Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

In case you didn't already know, augmented reality is here. It's no longer just an idea in a cyberpunk novel. And while augmented reality has been around for a long time, the actual technology is finally catching up to the idea.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

If you're a regular Null Byte reader, you probably know your fair share of programming languages and have at least some experience with web or app development. But it's possible to apply your hard-earned coding and tech talents to other closely-related fields as well.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

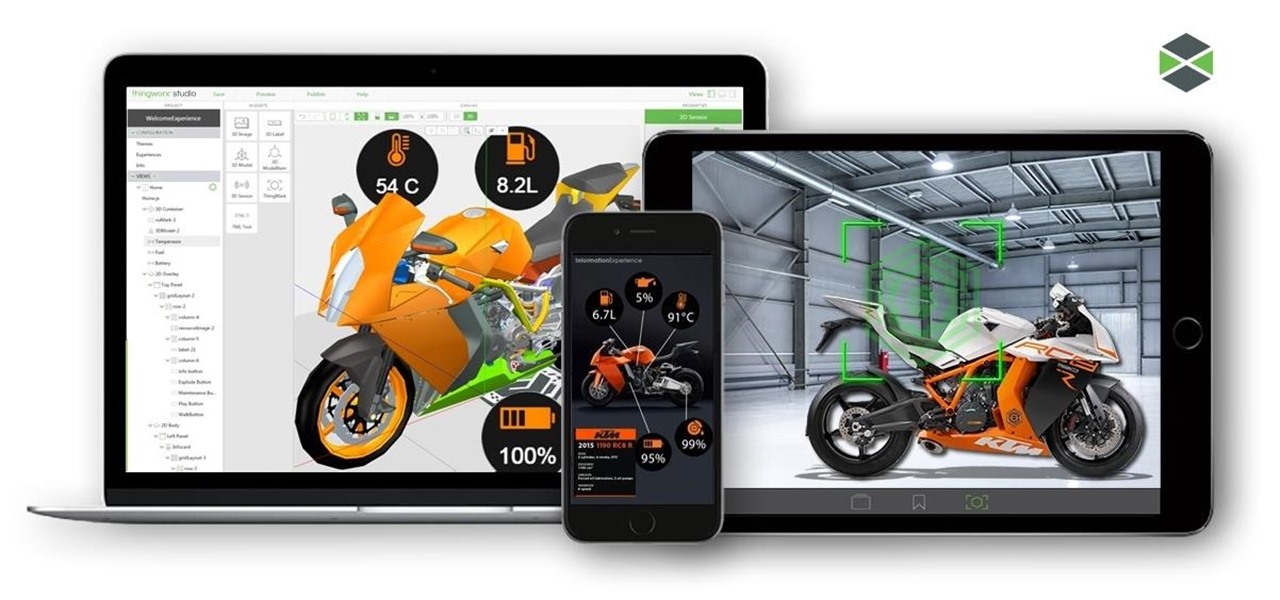
The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

A partnership between augmented reality company Zappar and IoT services provider EVRYTHNG will bring AR experiences to consumers while supplying market data to brands.

Independent game developer PlayFusion announced today a partnership with NEXON Korea Corporation, resulting in a Series A preferred share round to fund development of their entertainment platform. PlayFusion's platform applies augmented reality, Internet of Things (IoT), and audio recognition to Lightseekers, an original property that combines mobile gaming with smart action figures, trading card games, and other media.

These days, everything is connected. No, really — we mean everything. Your phone, your smart speaker, and even appliances like stoves and refrigerators can be connected and communicate with one another. Welcome to the Internet of Things, the start of our interconnected future. It's projected by 2027 that there will be more than 41 million internet-connected devices in use around the world.

If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more polished than the prototype we saw in January.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Welcome to the maiden voyage of our new Market Reality column. Each Friday, NextReality will give you a roundup of news briefs from the financial end of the augmented and mixed reality industry. We'll cover funding news, market analysis, and more.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

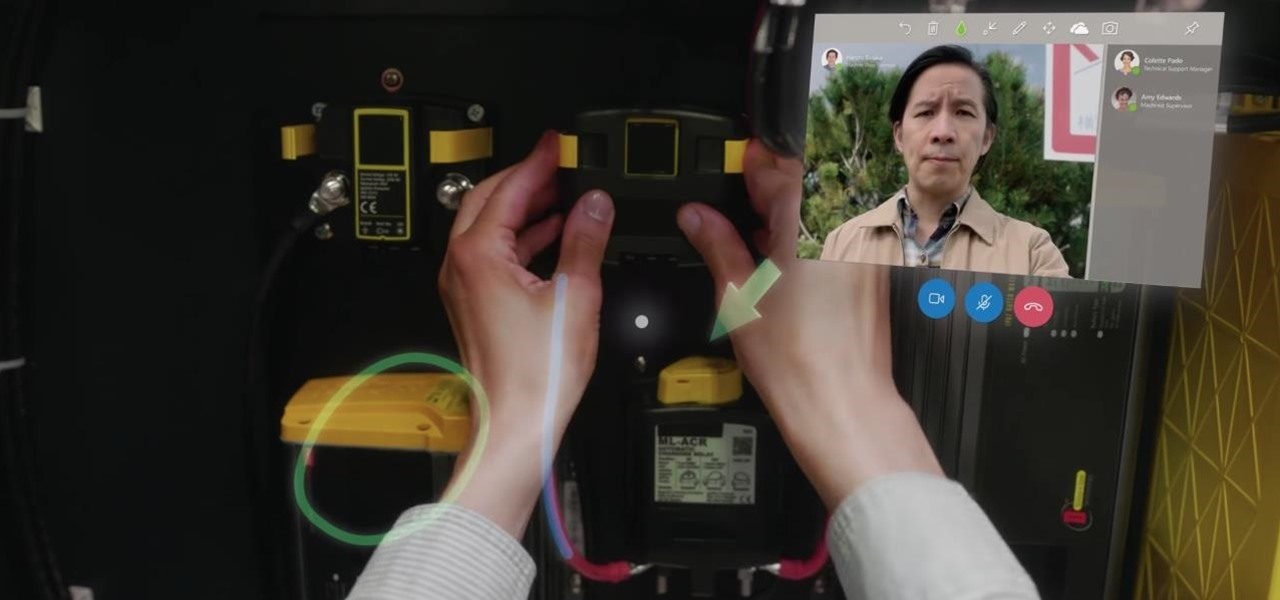
Late last year, two surgeons from the Instituto de Ortopedia e Traumatologia de Jaraguá do Sul in Brazil started using a combination of 3D printing and the Microsoft HoloLens to help plan spinal surgeries. And now, with the rest of their team, they've successfully performed a surgical procedure on their first international patient using their 3D impression planning and augmented reality process.

While not specifically an augmented reality conference, IFA 2017 packed a plethora of presentations with AR themes, including devices with AR features from Sony and Motorola, a smartphone-based AR headset from Lenovo, and a new processor from Huawei that will facilitate AR experiences.

Now that Microsoft has squarely focused on the enterprise market with the HoloLens 2, it appears Lenovo is content to play follow-the-leader with its new augmented reality headset.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

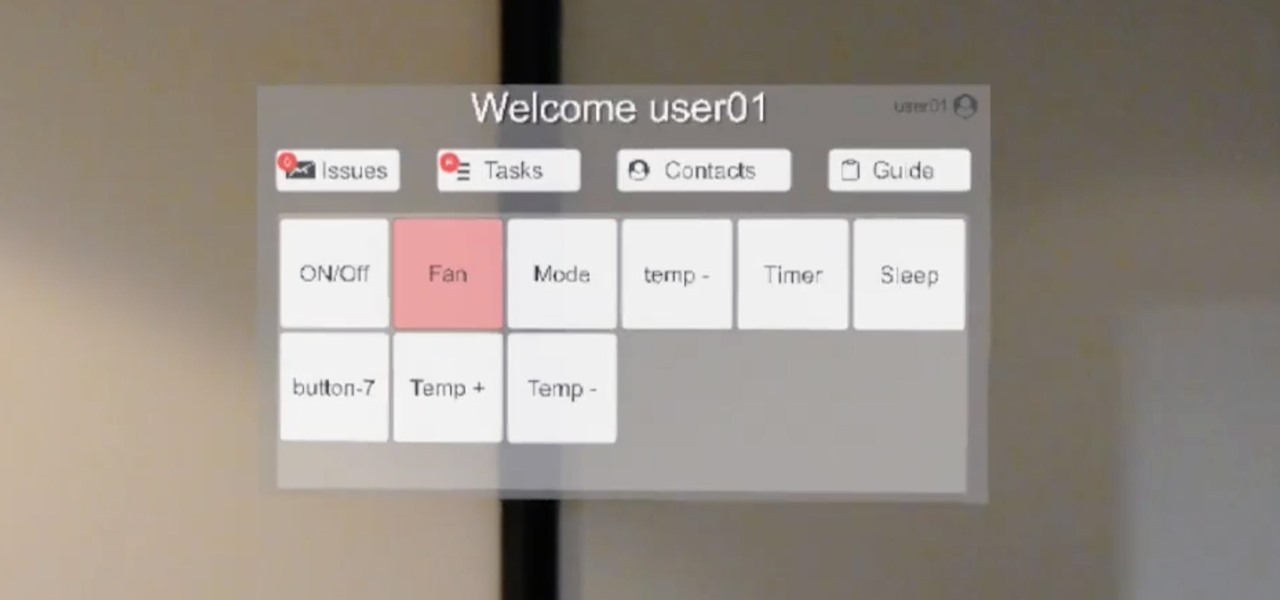
Empea Berlin, a Germany-based company specializing in augmented, mixed, and virtual reality software, released a Facebook video a few months back showing off their experiments in smart home technology. Using a Raspberry Pi and a HoloLens unit, they were able to make a virtual remote control for an air conditioning unit. The remote is complete with various modes, temperature controls, timers, and other features. There have been no updates on this project since they first showed it off, but hop...

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Location services provider Mapbox is expanding the reach of its augmented reality development capabilities to include apps for automobiles as well as smartphone navigation.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR and MR, and these are some of the faces behind them.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Microsoft's Monday keynote introduced the fourth generation of the company's Kinect sensor during Build 2018 in Seattle.

Up until now, experiencing augmented reality through Vuzix's next-generation Blade 3000 smartglasses would have required a trip to a tech conference where the company has an exhibition booth.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Mixed reality developer Arvizio has updated its MR Studio software suite to integrate processing of 3D light detection and ranging (LiDAR) point clouds.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

On Monday, at its annual Build developer conference, Microsoft revealed two new apps for the HoloLens apps.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

The augmented reality industry has a bright future built on innovation and growth, but that doesn't mean we can't look back at the close of the year to see what the industry has accomplished from a business perspective.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.