Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.
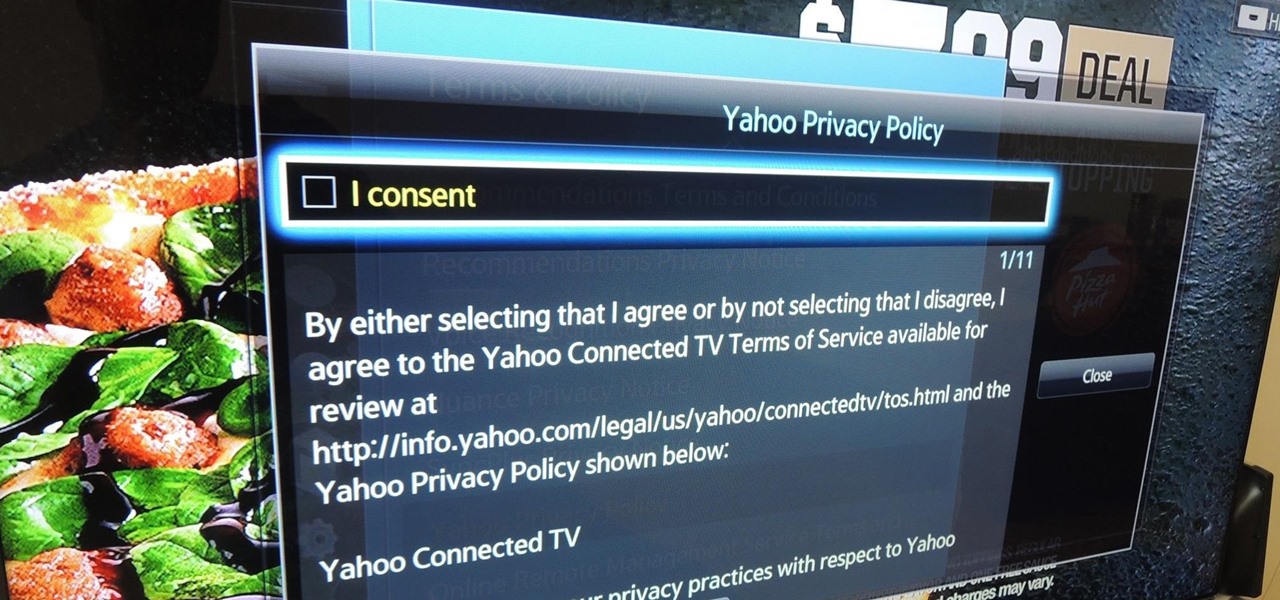
Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to place targeted and interactive ads on your screen.
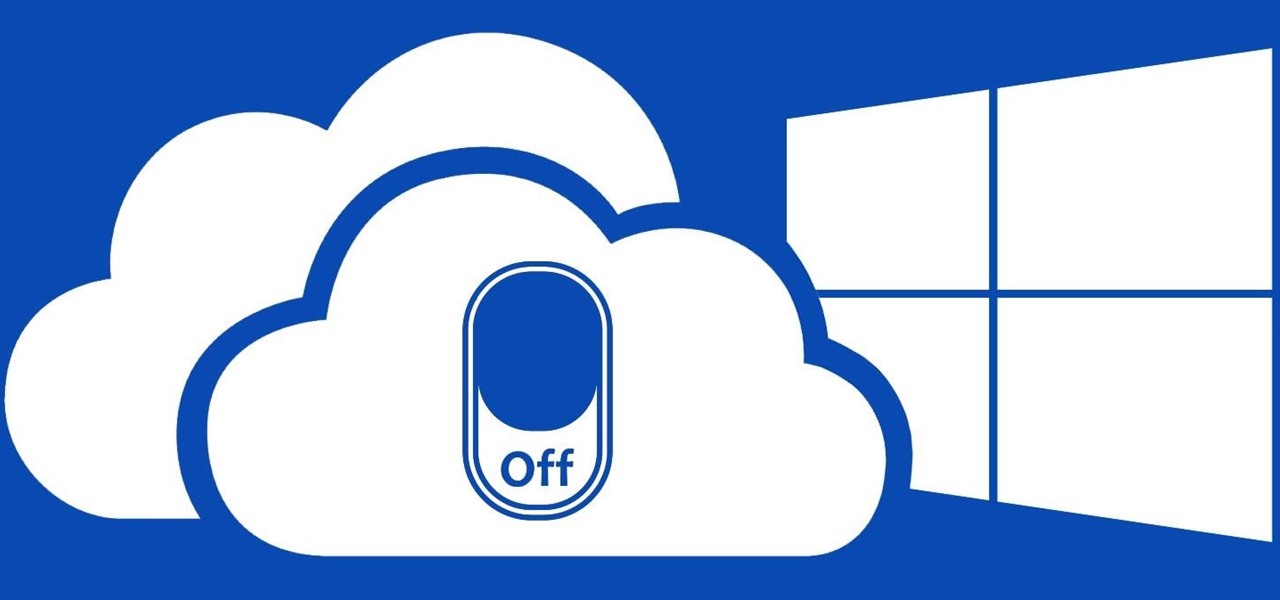
OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Check out this video to see how to collect blood with the BD Vacutainer Eclipse Blood Collection Needle.

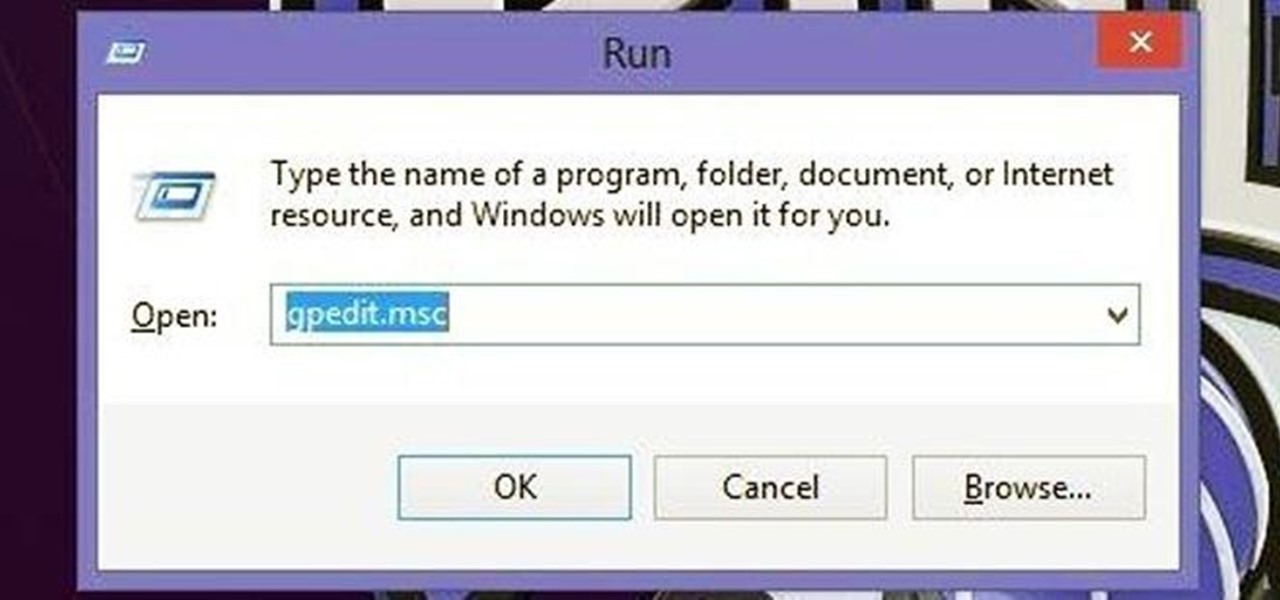
How to format a USB thumb drive to NTFS in Windows XP Go to my computer, click to the USB flash drive properties, in that click on Hardware, click on SanDisk Cruzer USB device, and then to its properties, then click to policies, in that click on the optimize for performance button, click ok. Again click ok on the properties icon.

Can't wait until you get home to get onto MySpace? This video gives step by step instructions on how to try and unblock MySpace while you are at school or on a server that does not allow access to the site. This video does not have narration, but has written instructions on how to get around blocked sites with out using a proxy server. However, you have to have access to the system 32 files for this tutorial to work, and accessing these files does go against a lot of network policies.

Some governments and organizations employ proxy servers to filter web content, permitting access to some web sites while blocking others. Here are several ways to get around these censorship policies. This is employed in China with YouTube and many other voices of anti-goverment ideas.

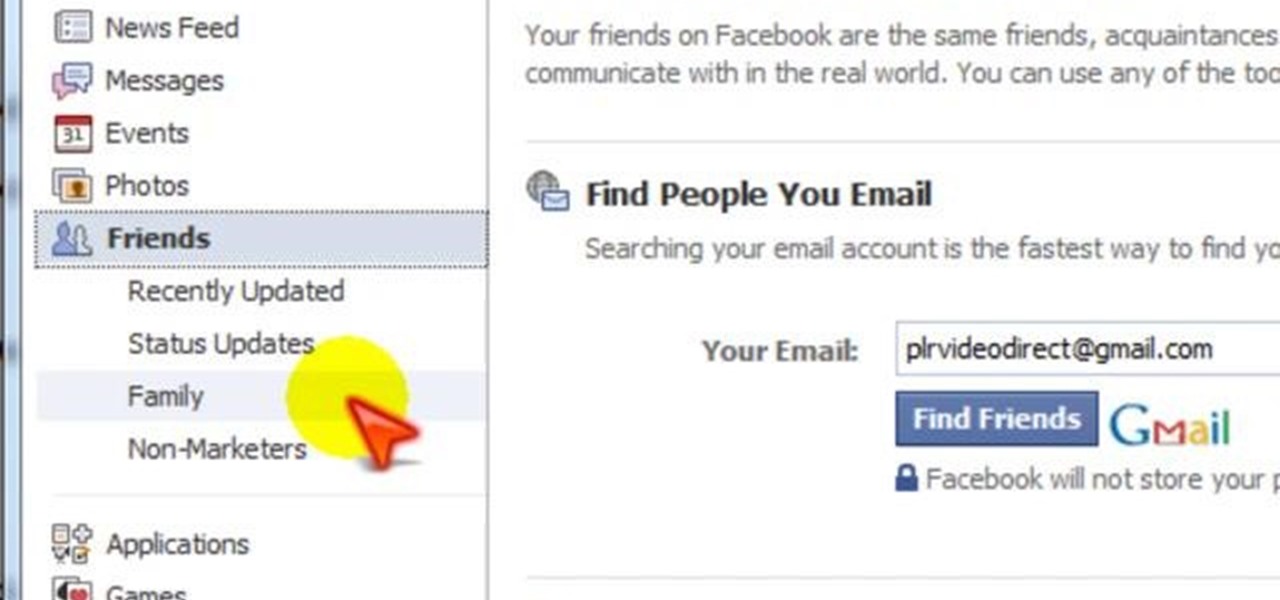
In this tutorial, learn all about Facebook's biggest issue these days: privacy. Check out this clip for a walk through of Facebook's privacy policy and learn how to create friend lists to keep your information safe and to yourself. Don't let your details get in the wrong hands, organize your account and be smart.

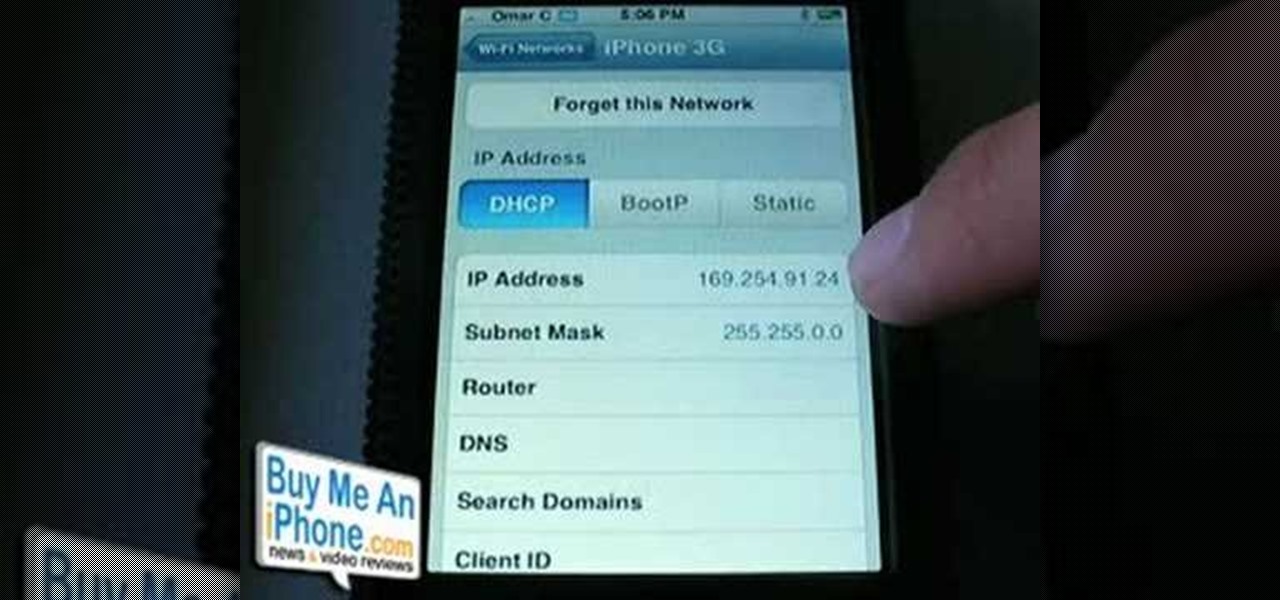
This is a video demonstration on how to tether your iPhone 3G to a Mac laptop to use the 3G network for surfing the web on the laptop. This is against AT&T's policy so try at your own risk. This is in place of the NetShare app that keeps getting removed by Apple or ATT. This let's you connect your computer to the 3G wireless network by using a proxy on your jailbroken iPhone.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

Learn how to configure the features in F5's FirePass v7 SSL VPN Endpoint Security. Peter Silva shows some of the new Endpoint Security features in the recent FirePass v7 release. Watch how to create policies, enforce host checks and other protective measures for your Remote Access deployments. For more information, and to get started configuring your own installation of FirePass v7, take a look.

Take a folder and organize documents based on the actions required. Actions:

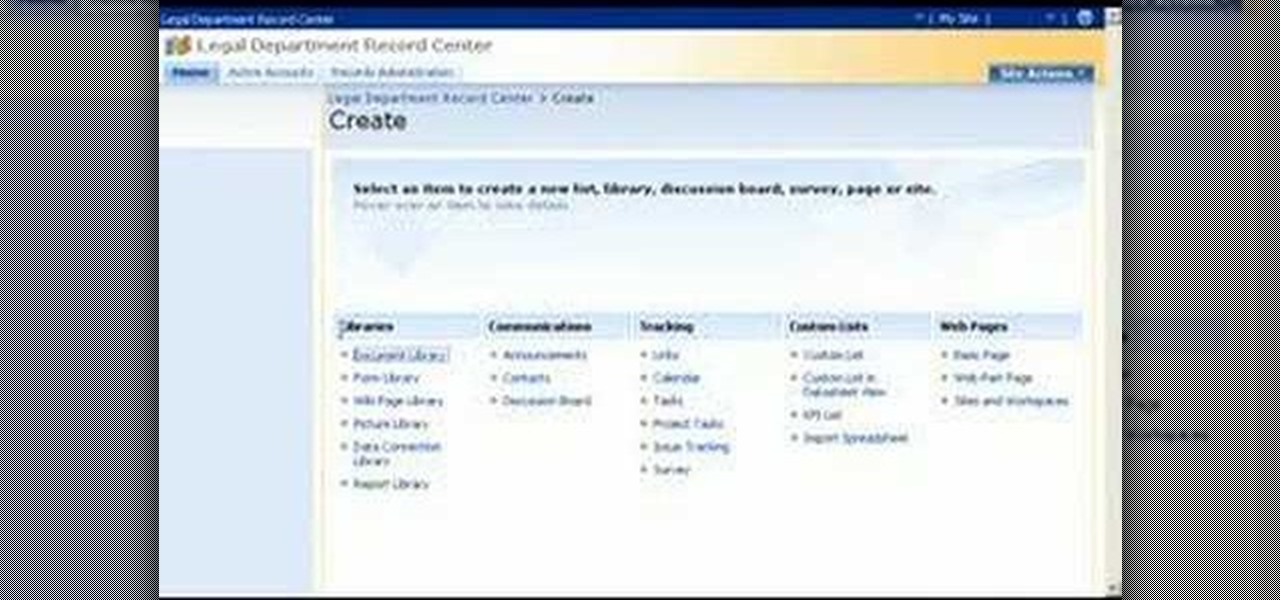
Check out this tutorial and see how to add a library to an existing Record Center site, apply policies to the library, and configure the Records Center site so that submitted documents are routed to the right library.

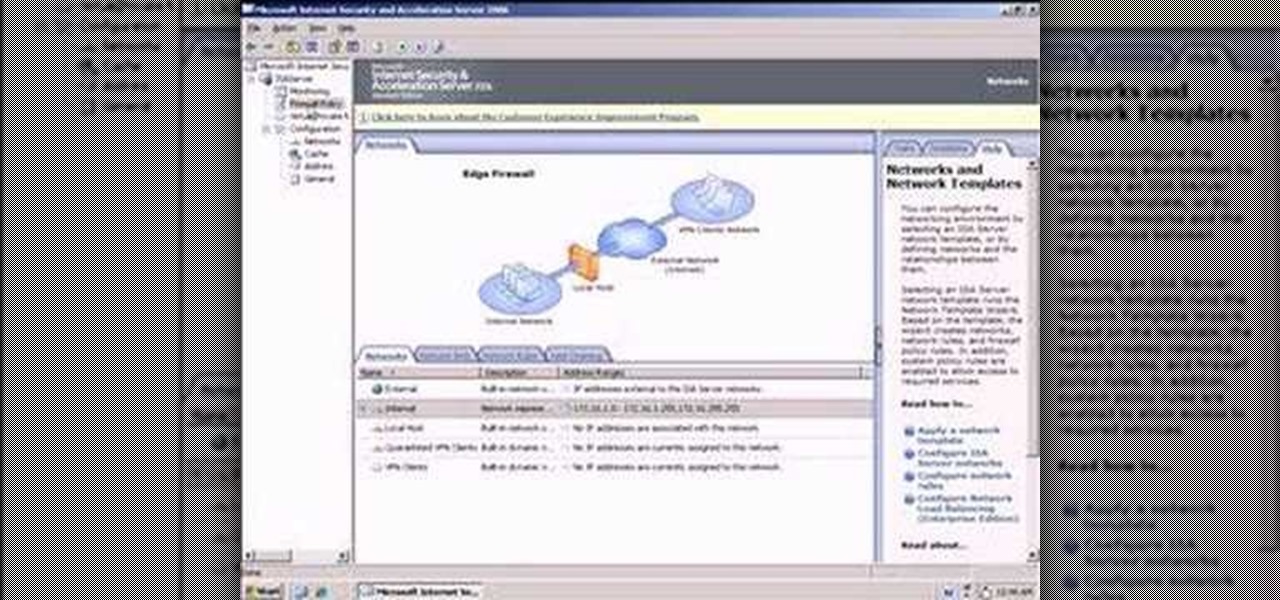
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

Bose Corp is the latest company trying to make another dollar off of you without your permission. Bose Connect, the companion app to the swag $350 Bose headphones, is not the Jane to your Jack that maybe we all hoped it to be.

BD Quikheel Safety Lancet The BD Quikheel Lancet is a safety-engineered product designed for heel sticks on infants and premature babies. It features a sweeping surgical blade that permanently retracts after creating an incision. Additionally, it offers a tapered window providing the healthcare worker with the ability to accurately position the lancet.

Check out this video tutorial to see how to use the BD Genie Safety Lancet blood sampler device. BD Genie Lancets are high quality, safety-engineered, single-use capillary blood sampling devices. They offer a permanently retractable blade or needle feature that minimizes the possibility of injury or reuse. BD offers a full range of blade depth and needle gauges for sufficient blood volume in multiple sample requirements. All Genie's can be used in conjunction with BD Microtainer Tubes.

Check out this video tutorial to see how to collect blood with the BD Vacutainer Safety-Lok Blood Collection Set.

For many busy people, time is of the essence, and for others, it's simply just being impatient. But no matter what your vice, having your computer start up as quickly as possible is usually a plus for anyone.

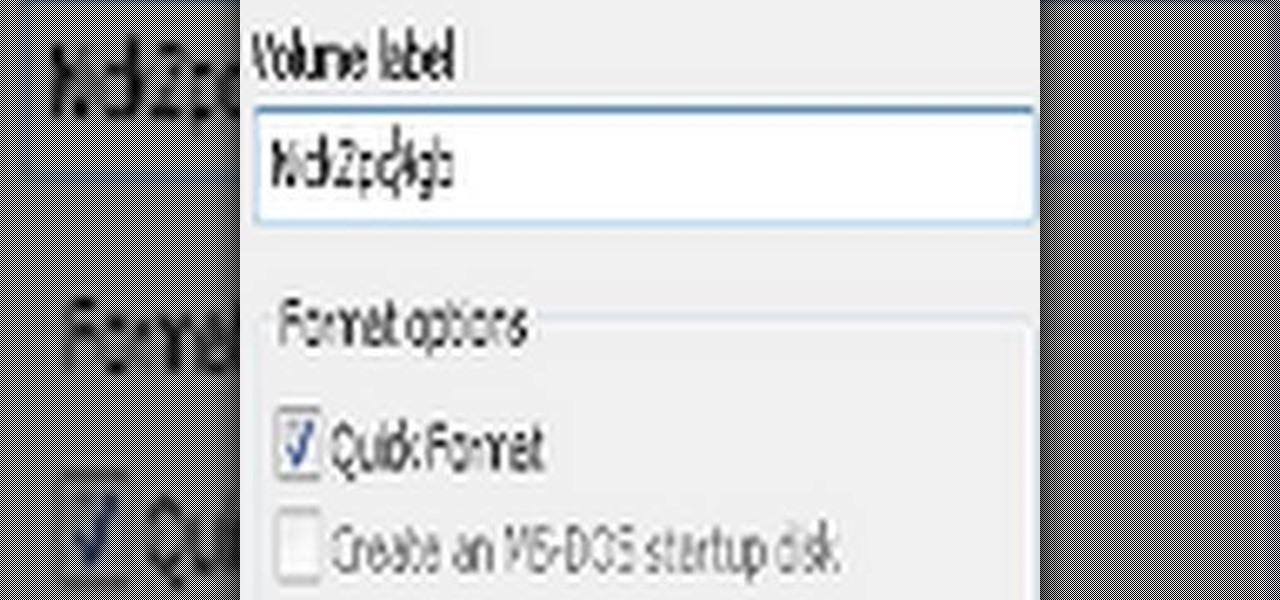
In this how to video, you will learn how to format a USB flash drive to NTFS. First, plug in the USB drive to your computer. Right click on My Computer and select properties. From here, go to the hardware tab and select device manager. Next, click and expand disk drives and right click your USB drive. Select properties and then click the policies tab. Choose optimize for performance and click okay. Edit the device manager and open My Computer. Next, right click the USB device on My Computer a...

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

In the business world, it's sometimes said that "where there's smoke, there's fire." At Snapchat parent company Snap, Inc., it appears the equivalent of smoke is executive turnover.

SNAP. That's the sound of your Samsung Galaxy S3's camera going off. Not that big of deal, unless you're trying to take some top secret pics or some candid shots of your friends. The shutter sound gives you away, and the next thing you know, you're deleting pictures. On most other smartphones, if the users turns the phone on silent or vibrate, the shutter sound is killed. If that doesn't do the trick, usually muting the shutter sound itself in the settings will do the trick. But for some of y...

The first thing that comes to mind when your car is stolen is: ####!! However, once calm, cover these bases when your car is stolen to notify relevant parties and help ensure vehicle recovery or replacement.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

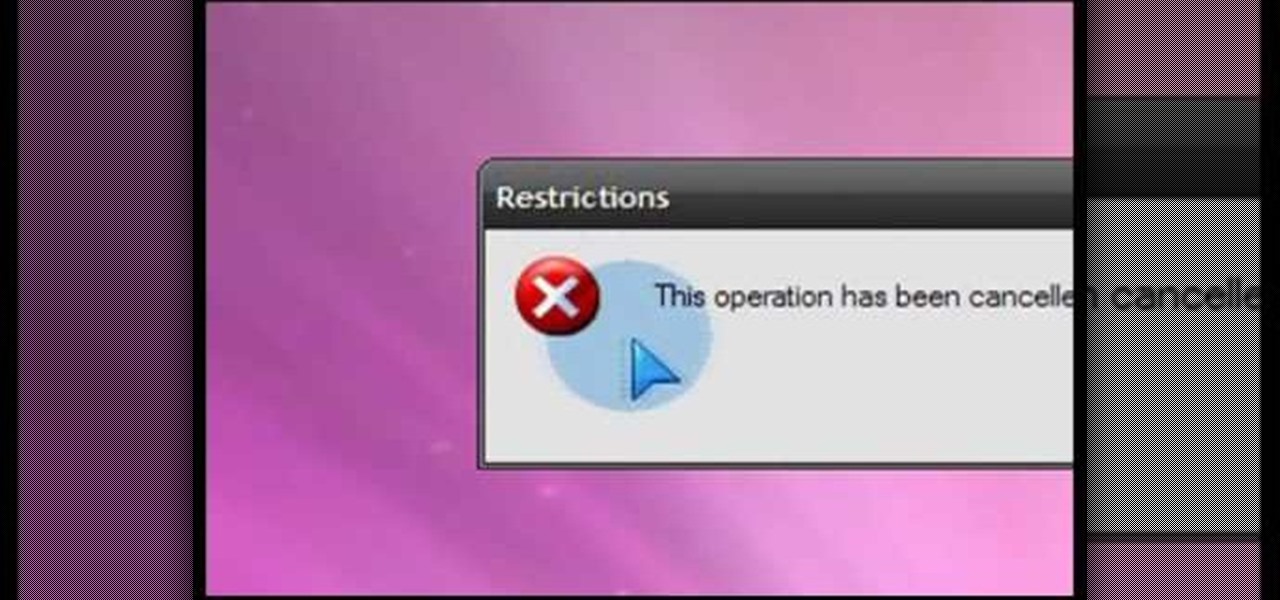
If you love computer pranks, this is one of the easiest ones to pull. This video will show you how to remove the Shut Down button from the start menu in Windows XP. Actually, it does't remove the shutdown button, it just disables it, giving the user a restriction message, stating "This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator."

If you are law enforcement or find yourself in an emergency situation you may need to know how to properly conduct surveillance in a rural area. You will have to gather information without being scene and will need different techniques when out in the wilderness.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

In this video tutorial viewers learn how to wear the National Working Uniform. This uniform has a strict policy and all must follow the uniform rules. The basic components of the uniform are: an eight point cap, blue cotton undershirt, shirt, trousers, belt with closed-faced buckle, black boot socks, blousing straps, black 9" steel-toed leather boots, embroider rank insignia and service & name tapes. This video is very detailed and clearly explains all the uniform expectations. This video wil...

Before lead was removed from gasoline, lead from car exhaust got into the air, was breathed in by kids, lowered their IQs, and increased crime rates (there is a very strong correlation between IQ and criminal behavior).

In this tutorial, we learn how to block a website using a Linksys Router. First, go to your web browser and type in "192.168.1.1" into the address bar. After this, you will need to enter in your username and password to the pop up window. From here, go to the tab that says "access restrictions" and look for where it says "policy name". Type in 'blocked website' to the bar and then click 'enable'. From here, go down to the bottom of the page and enter in the URL of the website you want to bloc...

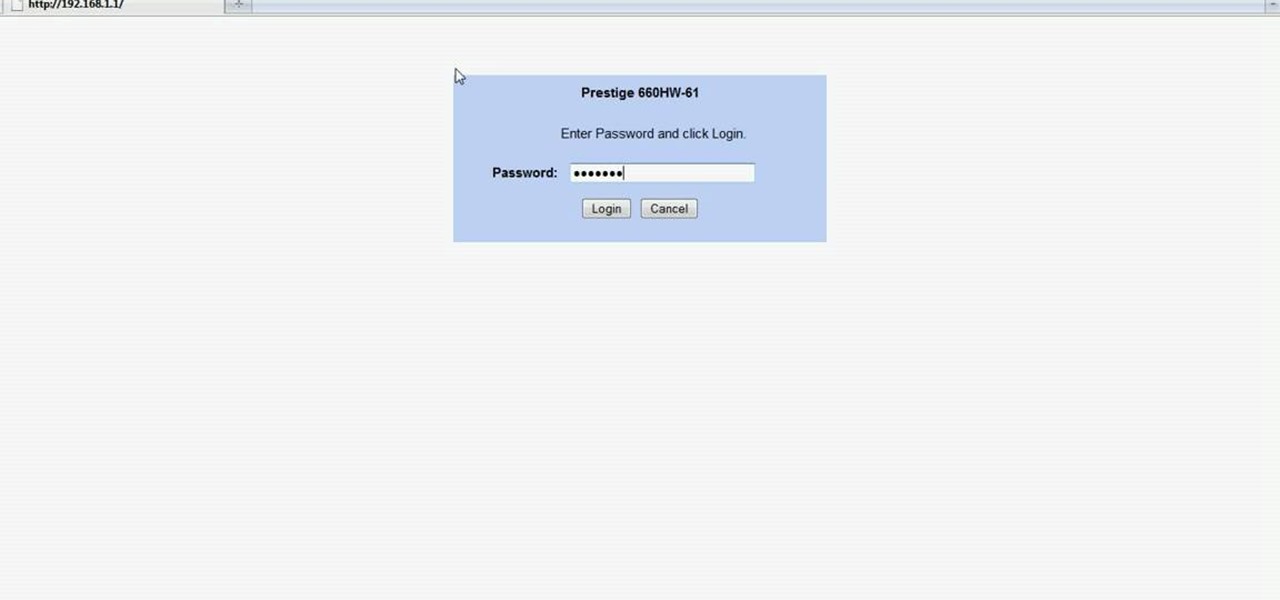
In this Computers & Programming video tutorial you will learn how to easily open your NAT on a ZyXel router. There are three steps involved in doing this. Open your web browser and type in the router IP address which is normally http://192.168.1.1. Then you will get the log in page. The password is either 1234 or admin. It will be written on the packaging of the router. On the next page click on UPNP, then check all three boxes and click 'apply'. Then you click on NAT and set the start and en...

In this video tutorial, viewers learn how to become a judge for the card game, Magic: The Gathering. The best way to join is to contact a level 2 judge. Judges must put rules in context. If confused or unsure, use online forums for a guide. Interact with the judge community. You don't have to be a certified judge to run a local event. The tournament policies and procedures can be found in the Universal Tournament Rules, Floor Rules or PCI Penalty guidelines. This video will benefit those view...

Although you may not agree with Sarah Palin's policies, there is one thing we all can agree on. Sarah Palin's hair looks great This tutorial teaches you how to do an "updo" Sarah Palin style. This is a quick and easy way to put your hair up without having to use any product, teasing or backcombing. Gather you hair into a pony tail, twist your hair, loop it upwards and clip it in place with a good size barette. Let the ends show at the top of your head. Then, gently loosen sections of your hai...

Check out this video tutorial to see how to tansfer blood specimens with the BD Blood Transfer Device.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Lately, the biggest news in driverless has been the raging lawsuit between two autonomous spearheads, Uber and Google's Waymo. A new bill back by General Motors, however, could take them both out of the race towards driverless.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.