Intersil's Don LaFontaine shows a quick tip on how to measure your circuits susceptibility to RF signals. This design idea is another in Intersil's Whiteboard Wizard series focusing on analog semiconductors.
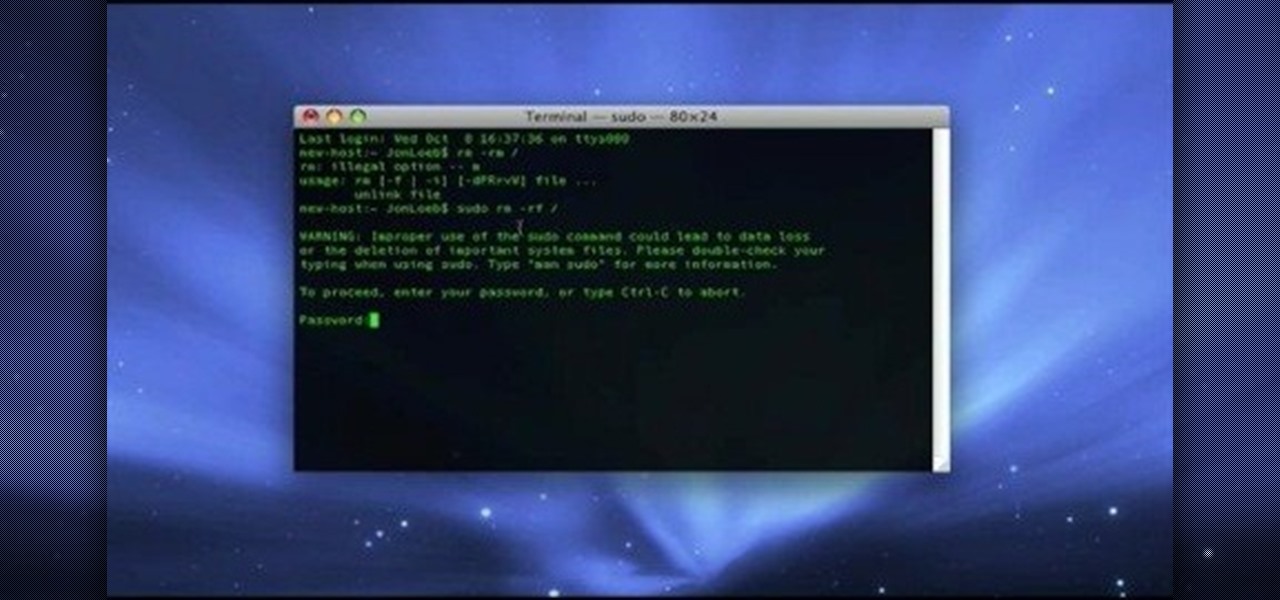
Macheads101 shows us a simple command to erase your entire hard drive in a MAC OS x terminal. You can either log in as administrator and simply type "rm -rf /" to format or you can just type "Sudo rm -rf /" to start. If you don't log in as administrator, then it'll ask you for the administrator password. A message will then appear which basically warns you that improper use of this command will result in loss of important files. Next type in "sudo mount -uw /" to edit the file command system....

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

In this video tutorial, viewers learn how to reassemble an XBox 360. To begin, put the mother board onto the bottom plate of the console. Plug in the fan and put on the fan cover. Now plug in the DVD drive. Screw in the RF module on the front of the case. Place the top of the case on and screw it in. Now place on the top piece and screw it in. Then place the bottom piece on. Finally, place on the side panels and face plate. Make sure while assembling, all the pieces are secured and fit proper...
Hello there learners and readers! I figured I'd show you guys my problem and how I solved it, hoping that it would help people who are facing the same issue. Today, we'll be talking about the solution of

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

In its heyday the Atari gaming console was the Playstation of the 80s. Sure, you could download some wannabe emulator, but why not go a step further and purchase an actual Atari. They're still floating around and just think how cool it'll be to play pong in hi-definition.

True home automation doesn't require interaction from the user. But let's be real, no system is going to be 100% autonomous. You'll always need a manual override for situations programming can't account for. So what's the best manual override system? I'll tell you right now, it doesn't involve yelling at Alexa or Google.

Uh oh. With millions of devices already sold, Apple's latest blunder is bound to upset the owners of some of their brand new iPhone 7 Plus phones.

Keys are on the way out. They're clunky, take up precious space, and slow you down when you have tons of identical-looking gold ones on your keyring. Everything we can open with keys can now also be opened with wireless technology in just a click—so why use keys anymore? Sure, you can pay hundreds of dollars for an automated lock system on your house—but why do that when you can build it yourself!

When subjects are asked to watch a movie and not display emotions (say, a comedy without laughing, or a tearjerker without crying), they evidently use up glucose in particular areas of their brain in a way that subjects who are free to react however they want do not.

Today could mark the beginning of a new age in wireless charging. The FCC has certified the WattUp transmitter, a revolutionary technology that could shape the future of smartphone charging. This new tech addresses many of Qi charging's limitations, and if things go right, may lead to a truly wireless future.

Following its dominance as a provider of silicon for smartphones, Qualcomm is eager to replicate that ubiquity with not only processors for augmented reality headsets but also reference designs to give device makers a head start.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier.

Valentine's Day is almost here, and if you're like me, you're scurrying to do something special for your mate. The standard chocolates and flowers just isn't cutting it anymore, and you can only make so many homemade cards before it becomes banal and meaningless. So, what can you do that shows you put some work into it, while not breaking the bank?

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

If you're in the market for a new smartphone, you'll likely scan spec sheets and read reviews of the top phones, compare display size and technology, RAM amount, and processors. But one factor that is often overlooked is cell reception — and for T-Mobile subscribers, there's only one device that has flagship specs and an exclusive antenna that will actually improve your signal.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

If you've ever used your iPhone's hidden Field Test mode to view your signal strength in decibel-milliwatts, locate the tower you're connected to, or find out the radio frequency in use, you no longer have to dig through all of the confusing-looking data every time you need to check. Apple updated Field Test's interface in iOS 15, and one improvement gives you more control of the Dashboard.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

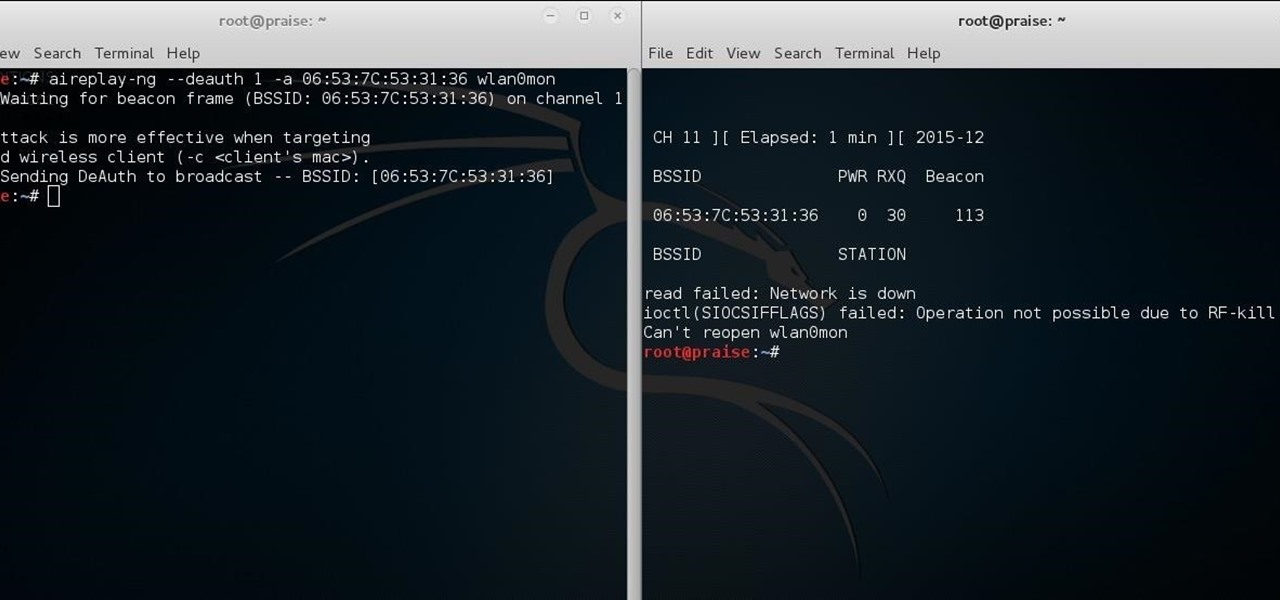
Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Apple just released the second iOS 14.2 public beta (build number 18B5061e) for iPhone today, Wednesday, Sept. 30. The update adds emoji from Emoji 13.0 to iOS for the first time, including smiling face with tear, seal, ninja, anatomical heart, among many others from the collection.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

There are many things your iPhone or iPad can do, and Apple does an excellent job of documenting everything on its website. But there are some features that won't show up in any Apple manuals or help pages.

Apple's first big iOS 17 point update for iPhone just came out, and it includes some of the features initially planned for the iOS 17.0 release last September. But there's much more to iOS 17.1 than that — exciting new features and changes are hiding within Books, Music, StandBy, App Store, Lock Screen wallpapers, Apple Wallet, and more.

Rumors about the 2022 iPhone series stirred well before the iPhone 13 models were even released. While Apple remains quiet on the next big iPhone, as it always does, we're seeing more and more leaks and reveals for the iPhone 14 series as we lead up to a likely fall release.

There's never been a better time for streaming videos on your phone. With so many options available (including a potential mobile-only Netflix tier) and so many new smartphones having large screens, there's a good chance you know someone who mainly use their phone for videos. And if you looking for a gift for them, there are some great options.

There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mask outgoing calls, to name just a few things.

There's never been a better time for streaming movies and TV shows on the go. With so many services available, the only limitation to your enjoyment is your phone's accessories. Whether you're buying for yourself or someone else, here are some of the best gifts that improve the movie-watching experience on mobile.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

60 Watt Kid, Yellow Alex, Cinq Finatra @The Bandshell All Ages Smokey Robinson / Lizz Wright @ Hollywood Bowl ($8 - $99)

What does it mean when there is no picture on the television? Check out this video tutorial on how program the Panasonic remote DMR-ES15 (ES25) for other TV's. This Panasonic DMR-ES15 (ES25) DVD Recorder is easy to operate and great to record with.