Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

This five-part series on C# programming covers many things. First, you learn how to save to the Microsoft SQL Server. Then, you'll learn how to retrieve that data. You'll also learn how to navigate the DataSet, edit SQL data, and delete data. If you have Microsoft Visual Studio and SQL Server, give this lesson a try.

In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on a Microsoft SQL Server (or SQL Server Express.) See how easy it is to obtain a shell in a Microsoft SQL database with this how-to.
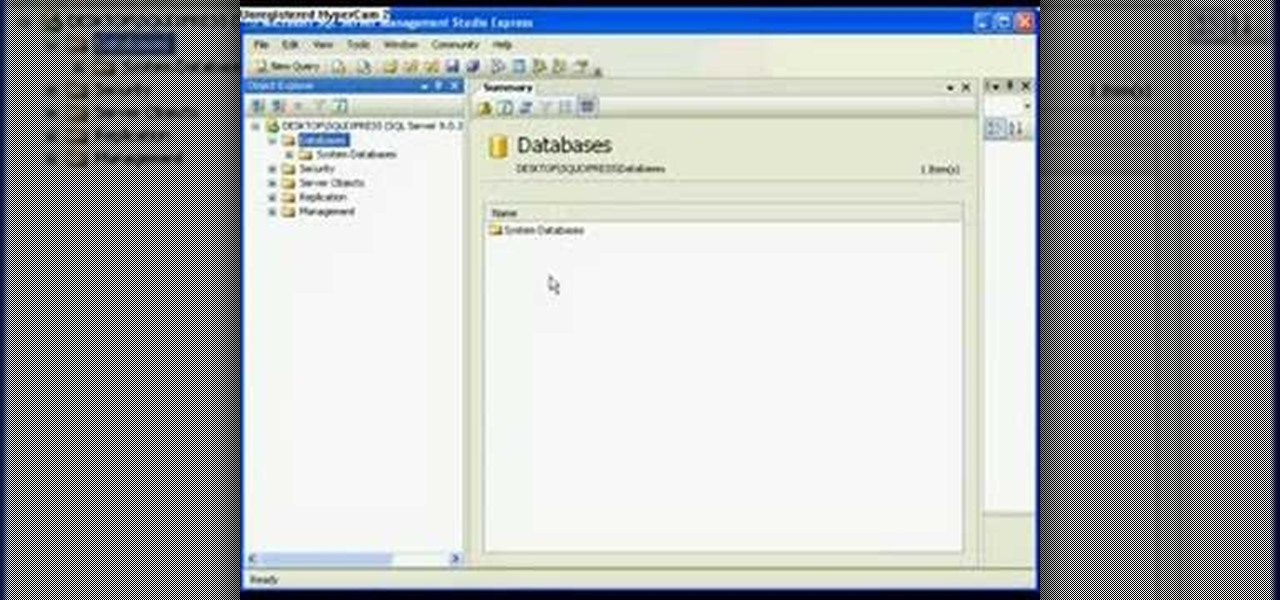
In this video tutorial, viewers learn how to detach and attach a database in SQL Server 2005. Microsoft SQL Server is a relational model database server. Begin by opening the Database and show all the tables. To detach the table, right-click the database and select Detach. Make sure that the database is not opened or it will not detach. To attach a database, right-click on Database and select Attach. Click on Add and find the table. Select the table and press OK. This video will benefit those...

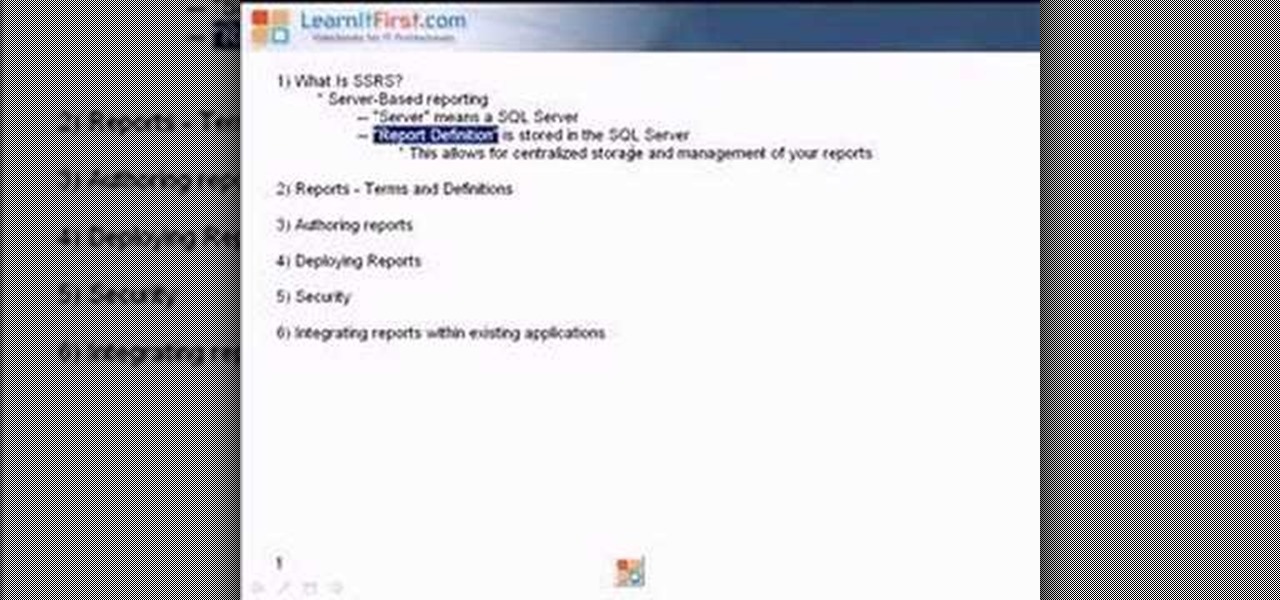
This video talks about what SQL Server Reporting Services (SSRS) is and designed for the absolute beginner - someone who wants a high-level overview of Reporting Services.

SQL Server Reporting Services allows you to design and deploy nicely formatted and interactive reports representative of your data. Suitable for print or online distribution, these reports and it allows you to get professional results very quickly. This video demonstrates how to set up Reporting Services and the Business Intelligence Development Studio to build reports using the wizards and design. Use SQL Server Reporting Services.

Watch this demonstration on Spotlight on SQL Server Enterprise by Quest Software. Spotlight on SQL Server Enterprise is a part of the Quest Management Suite for SQL Server as well as standalone offering. This demonstration shows the use of Spotlight on SQL Server Enterprise within the Management Suite

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to do is to monitor a remote MySQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to monitor a given MySQL database remotely via DreamCoder for MySQL, take a look!

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

If you're new to DreamCoder for PostgreSQL, one of the first things you may want to know how to accomplish is to connect to a remote PostgreSQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a connection between a given PostgreSQL database and the DreamCoder for PostgreSQL, take a look!

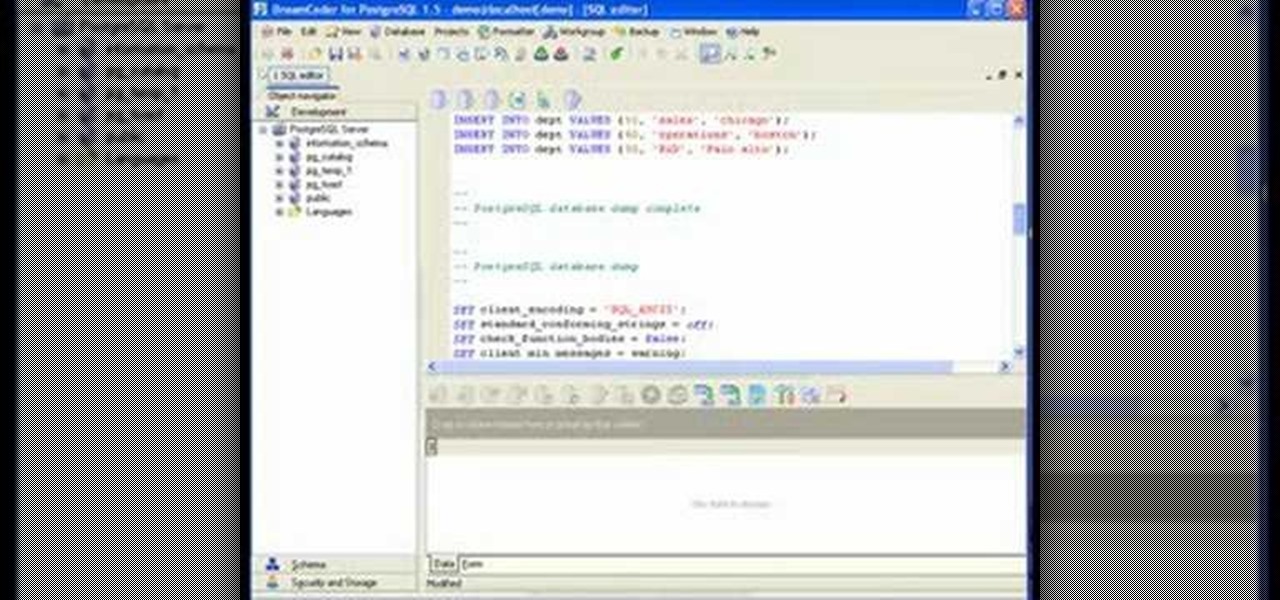
If you're new to DreamCoder for PostgreSQL, one of the very first features you should acquaint yourself with is the export data process, which will permit you to backup your PostgreSQL databases with ease. For step by step instructions, consult this how-to.

Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

Remote Server is a very handy tool for users wishing to utilize OnTime Windows and OnTime VS.Net without having direct access to SQL Server. This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers Remote Server in detail and how to set it up. Take a look.

A Membership Provider allows a web application to store and retrieve membership data for a user, and the standard ASP.NET Membership Provider uses pre-defined SQL Server tables. In this video tutorial, Chris Pels shows how to create a custom membership provider that uses custom SQL Server tables separate from the pre-defined tables used by the standard provider. The principles covered in the video will apply to creating custom membership providers using other databases such as Access or Oracl...

Welcome to the first coding tutorial on SQL here on Null Byte. Typo:

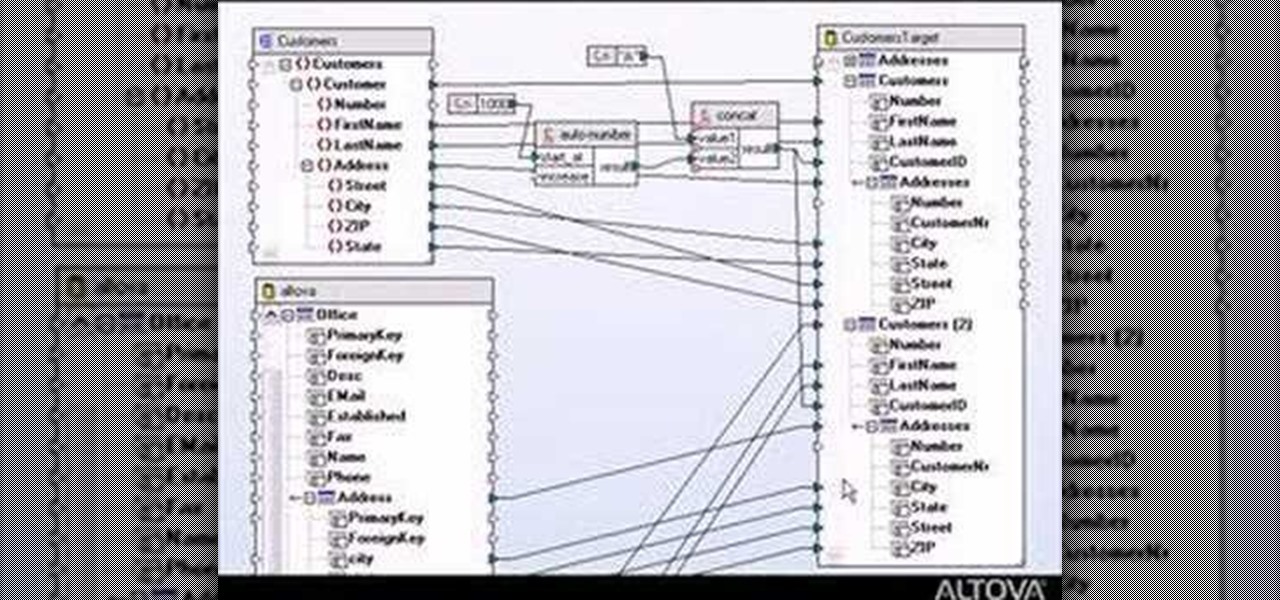
Designing a data mapping project in MapForce? The output functions in MapForce let you preview textual or XML output, save it to disk, or look at SQL statements for database output before committing them to the database server. Learn how in this tutorial.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

See how simple it is to create data-driven web sites using ASP.NET 2.0, Visual Web Developer 2005 Express Edition, and SQL Server 2005 Express Edition. Watch this video tutorial to learn how to create a database, add its data, and display that data on a web page.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

MySQL is a multithreaded, multi-user SQL database management system which has over 10 million installations. It runs as a server providing multi-user access to databases. It is by far the most popular and common database used in web applications throughout the world, and almost all hosting companies provide it free of charge to their users. MySQL AB makes MySQL Server available as free software under the GNU General Public License (GPL). For this tutorial we are going to download and install ...

Hello NullByte! This will be my first How To series.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

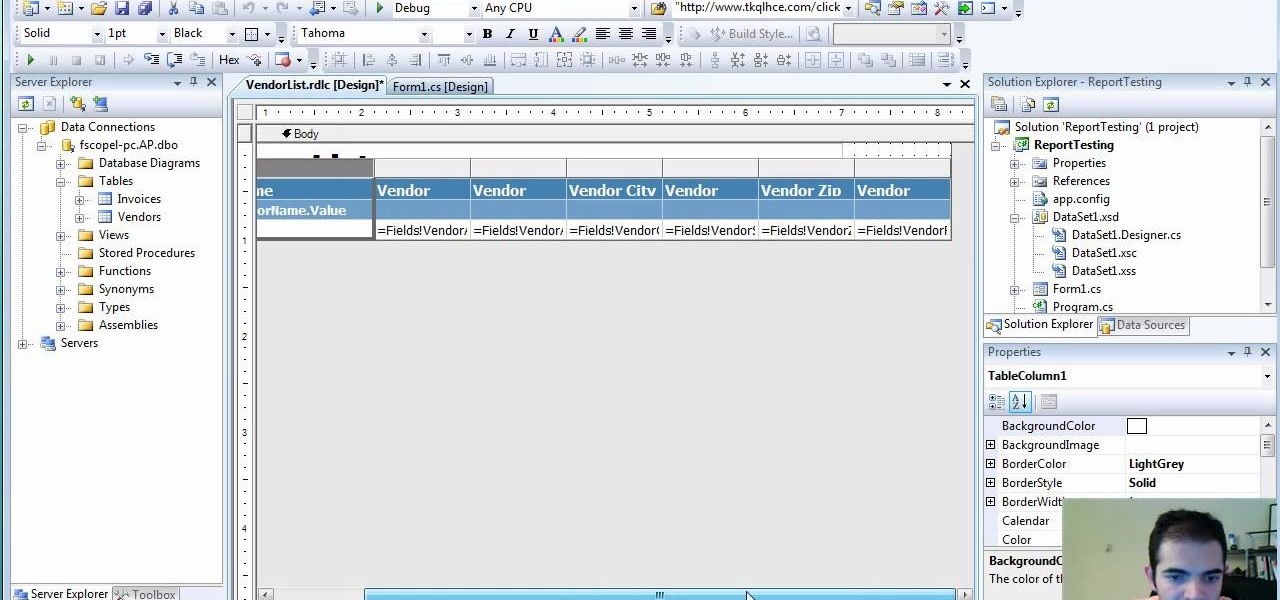
If you're not sure about creating reports in Visual Studio, this two-part video will cover the entire process. This assumes that you already know a few things in Microsoft Visual Studio and the C# programming language. So, if you're not a beginner and still need help to create reports from data in the SQL Server, this is how you do it. Also, learn a quick and easy way to pass parameters to reports in C#.

In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Join Patrick Hynds as he demonstrates how to set up the SQL Membership Provider to add Forms authentication to your ASP.NET 2.0 Web site, in this video tutorial. There are a few tips and tricks involved, such as using the aspnet_regsql.exe utility, which are covered in the video.

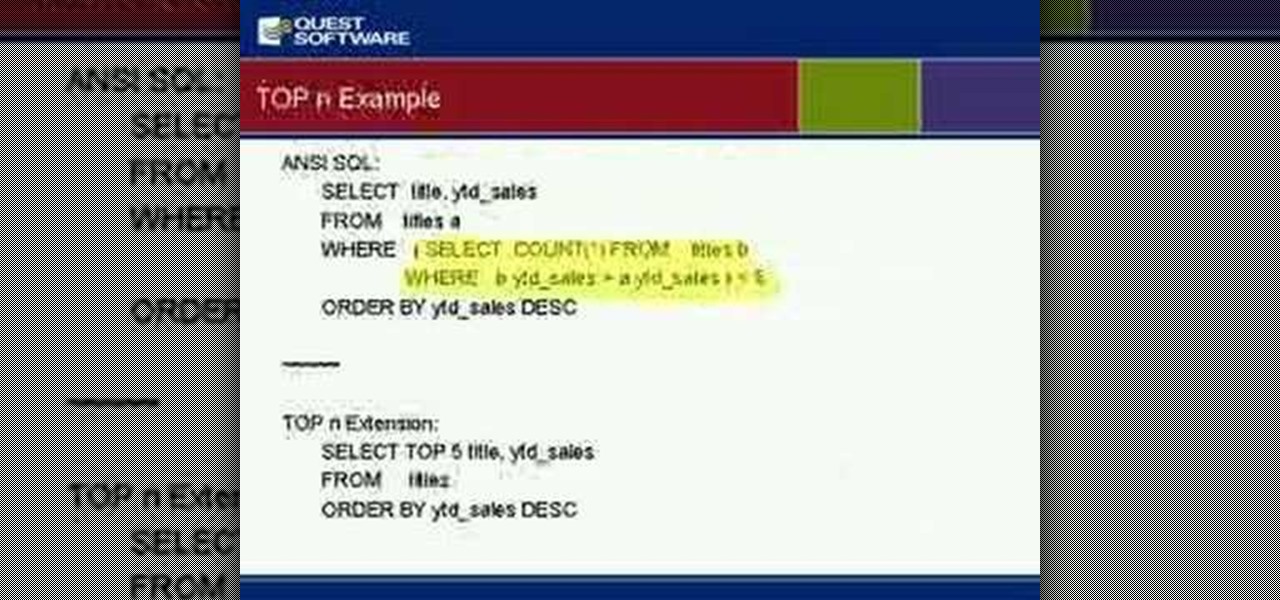
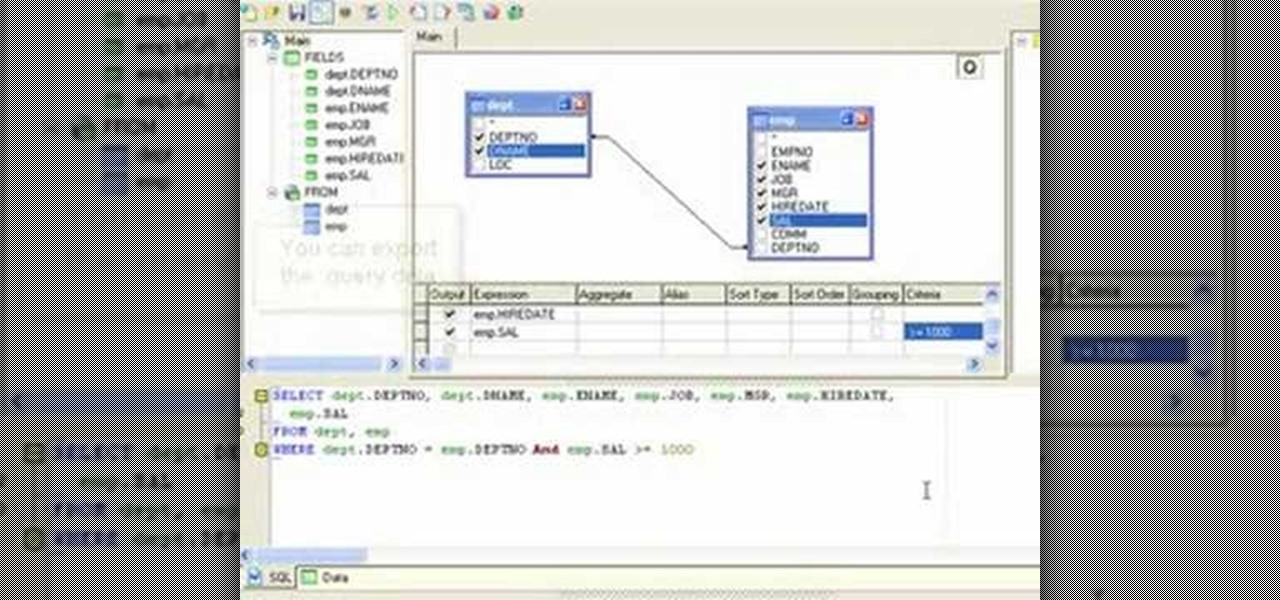
So many newbies to Transact-SQL have difficulties determing when to use a UNION or a JOIN to satisy their query. This video teaches you some guidelines to help you quickly and easily identify whether your query will likely need to become a JOIN or UNION. Disclaimer: these are just guidelines and they will not work in every situation but they are applicable for most SQL developers most of the time.

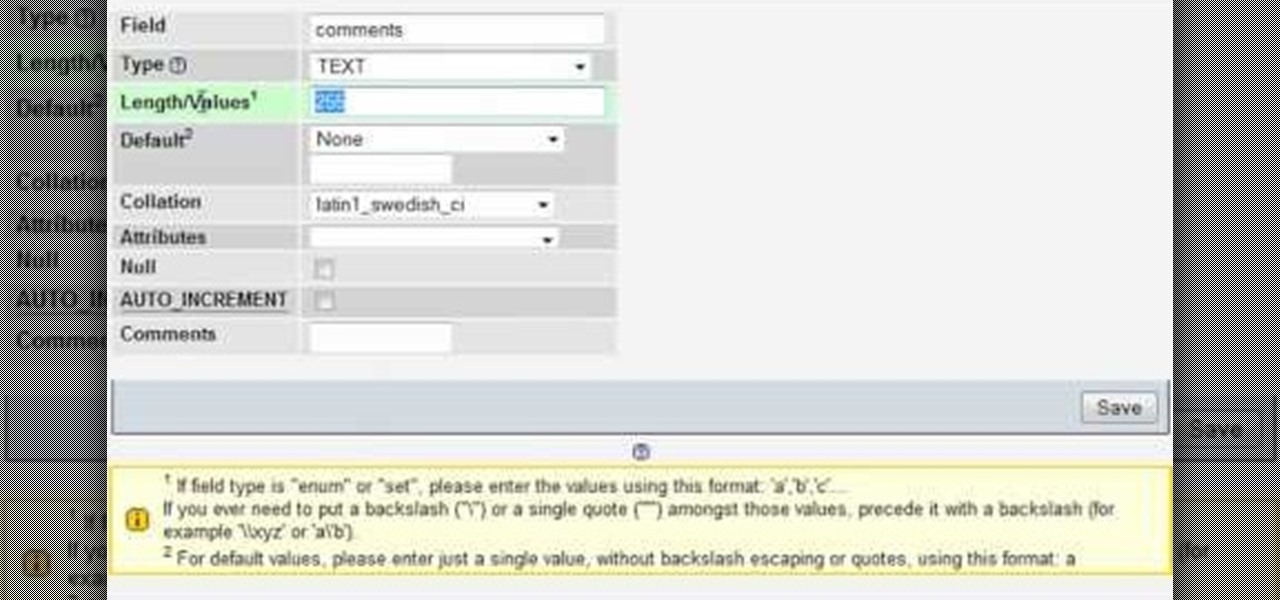
In this clip, you'll learn how to adjust database parameters using phpMyAdmin and order MySQL pages with SQL ORDER BY. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll learn about how to prevent SQL injection when writing code in PHP. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

If you're new to DreamCoder for MySQL, one of the things you may want to know how to do is write complex SQL queries. Happily, this tutorial will walk you, step by step, through the process. To learn how to use the DreamCoder Query Builder, press play!

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.