
TypoGuy Explaining Anonymity: Who Is Anonymous?
Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.


Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.
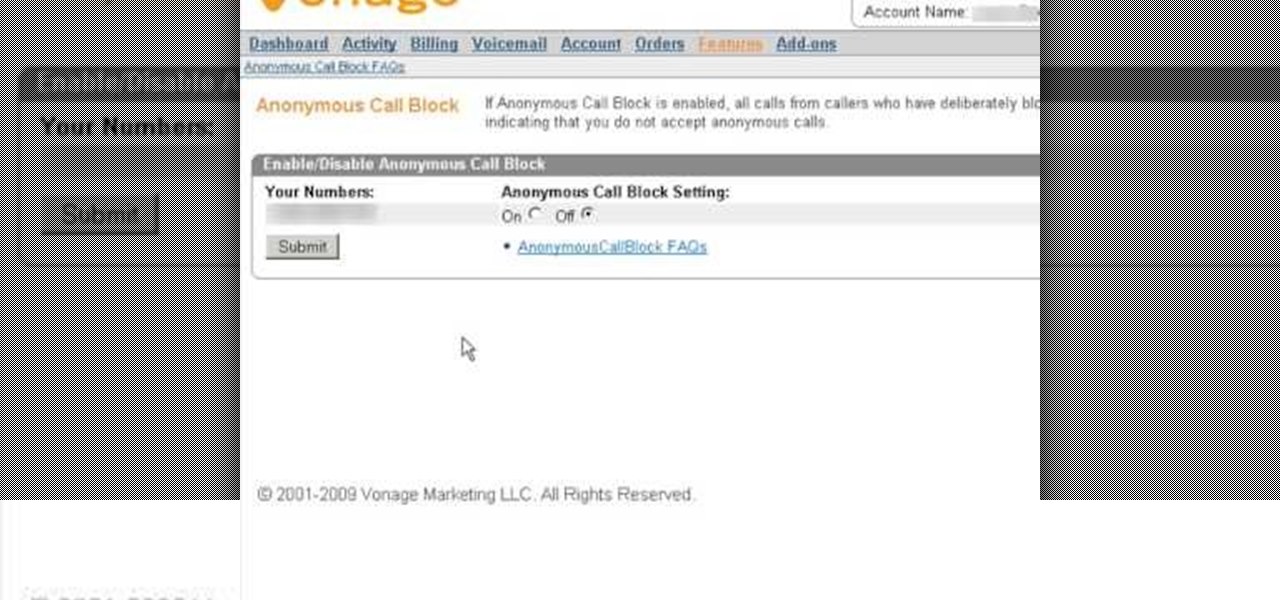
If you are looking for a way to prevent telemarketers and nothing else is working, consider signing up for Vonage's call blocking feature. In this tutorial, brought to you straight from the professionals at Vonage, learn how to set your phone to block any incoming call without a number attached to it.

If you've ever participated in a Anonymous protest against scientology or celebrated Guy Fawkes day, you probably know that drinking through a Guy Fawkes mask is tough, especially if you're keeping your identity a secret. Watch this video to hear an Anonymous member explain how to drink water without compromising your anonymity.

The computer represents a whole new frontier in prank technology, and if you've aren't computer pranking people you need to get with the times. Watch this video to learn how to send anonymous emails, make crank calls online, even send people a message saying they're about to be murdered!

Watch this video to learn how to shoot anonymous interviews for documentaries. Matt explains how to maintain anonymity using the proper lighting and audio effects.

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...
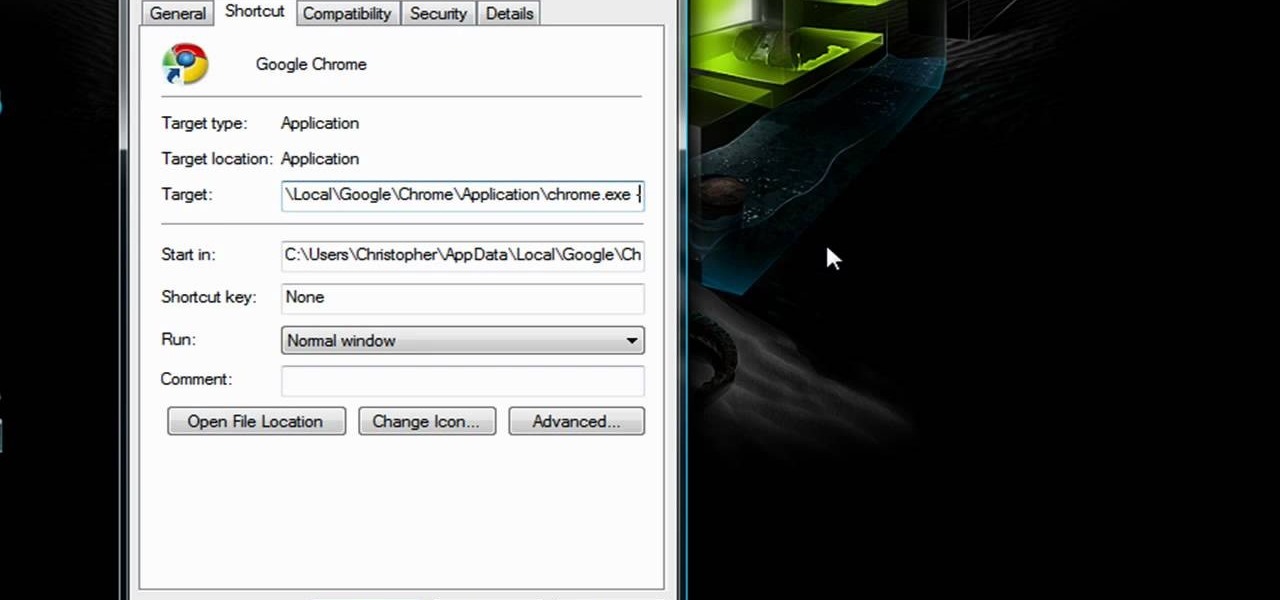
Did you know that Google Chrome has a feature called Incognito Mode that allows you to browse the web without having your history recorded or any cookies downloaded? It's perfect for shared computers, but by default you have to turn it on every time you open the browser. Watch this video to learn how to make Google Chrome default to Incognito Mode, removing one step between you and anonymous browsing.
The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

Just because the internet renders you virtually anonymous does not mean social customs should be ignored. Just like in the outside world, there is etiquette that should be obeyed if you want to be treated as a friend rather than an annoyance online. In this how to video, Proper Ollie teaches you how you can have proper internet etiquette in social networking forums.
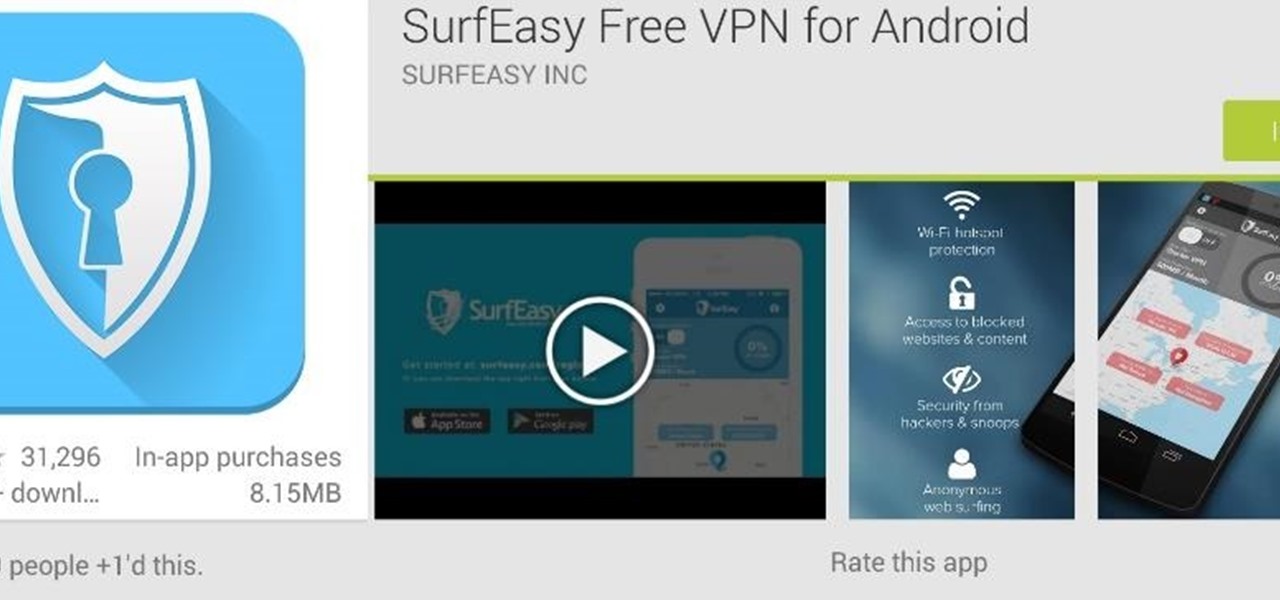
When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.
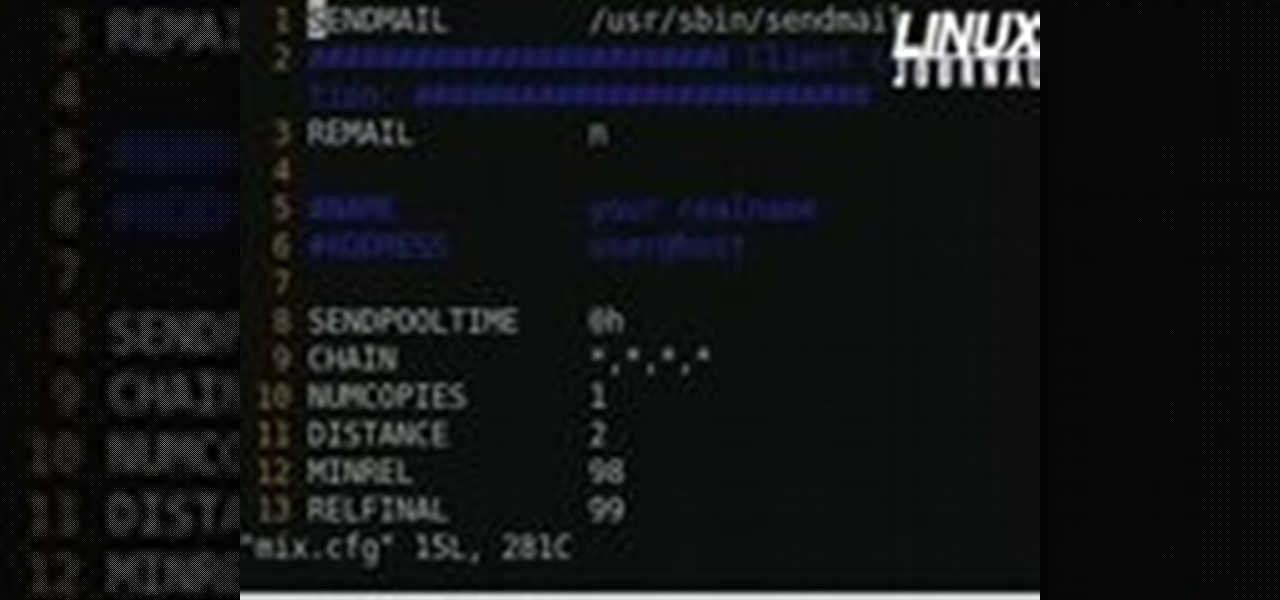
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.
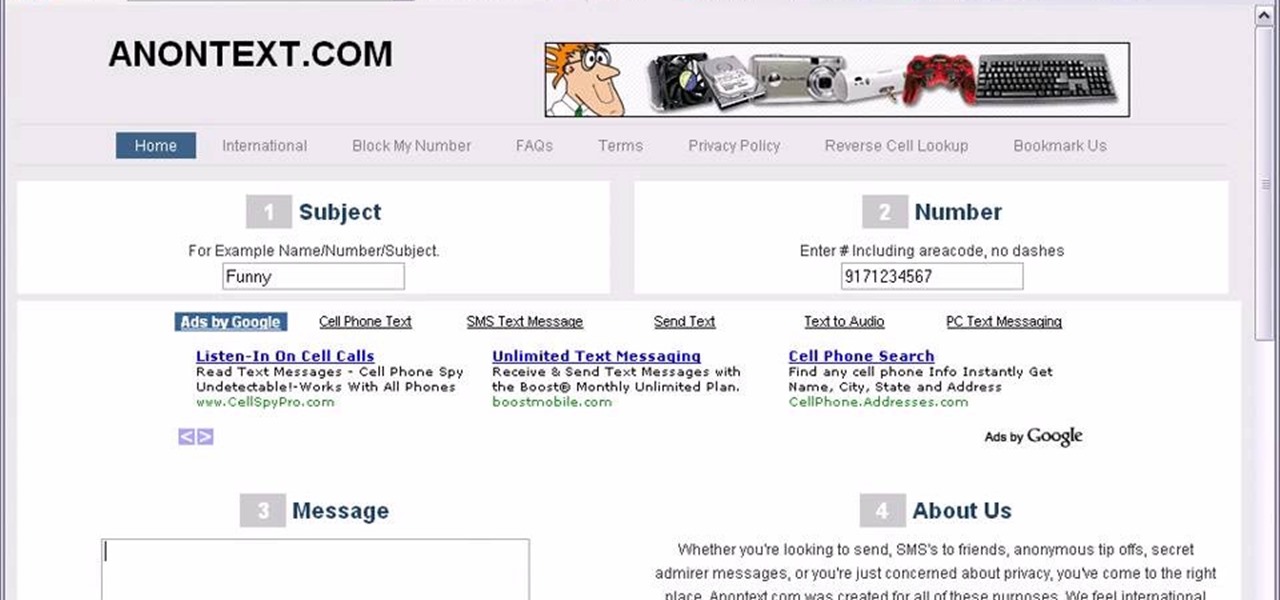
Want to send text messages, but don't want your recipient to know they're from you? You can use a website called AnonText.com, which lets you send anonymized text messages to any cell phone number. Use your computer, or, if you have a smartphone (like an iPhone, Droid HTC Evo), then you can navigate to the website using your phone's browser capabilities.

Have you been holding onto something for way too long? Been biting your tongue around your boss or teachers? Vent some of that frustration by sending an anonymous email or text. All you need to do is get online and type in all those nasty things you've been dying to say. This video will show you how to text and email anonymously.
As Eric Hughes writes in his "A Cypherpunk's Manifesto," privacy, otherwise known as the power to selectively reveal oneself to the world, is necessary for a free and open society. One way to protect your privacy is through anonymous browsing. In this tutorial,

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)

Hotels are anonymous and while this is a great thing, you should also be careful about the nameless folks who've used your room before you. Follow this tutorial to make the most of your hotel and ensure a great vacation experience.
Log in to your LinkedIn profile, and you'll immediately be prompted to check out who's peeked at your profile. With one click, you can discover how many recruiters, companies, and random people have viewed your online resume.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.
As Eric Hughes writes in his "A Cypherpunk's Manifesto," privacy, otherwise known as the power to selectively reveal oneself to the world, is necessary for a free and open society. One way to protect your privacy is through anonymous browsing. In this tutorial, you'll learn how to use the freeunblockme.com tutorial to surf the web anonymously.
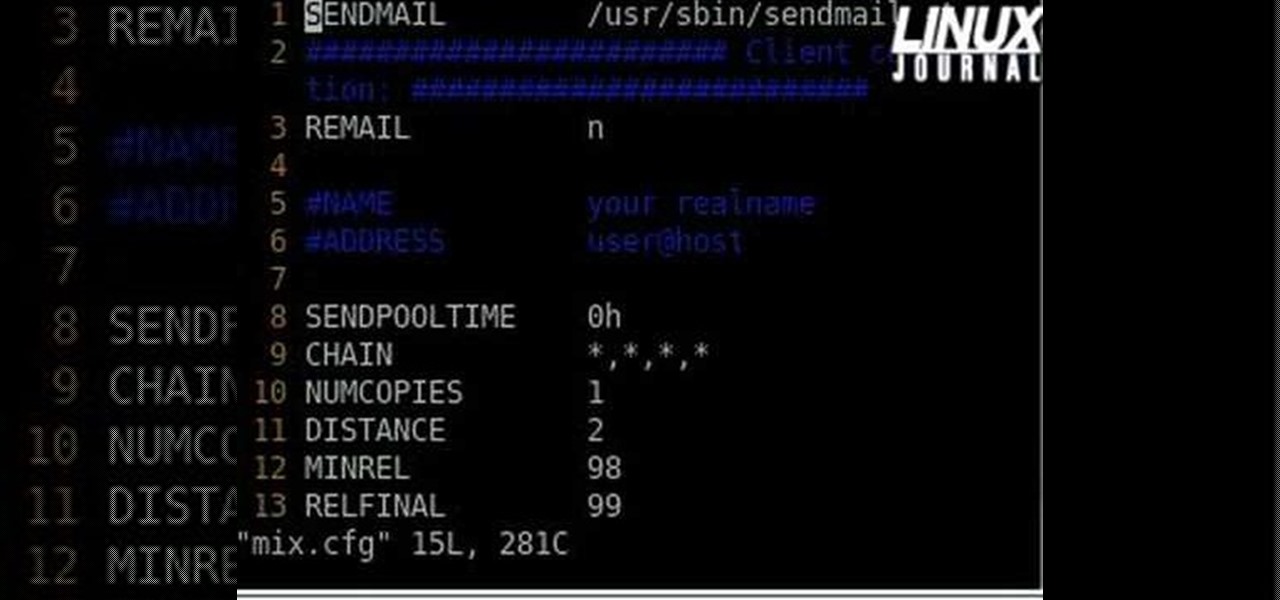
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

It's time to enjoy one of America's longest lasting favorite pastimes. No, not baseball—pranking our friends! With the internet currently overrun with countless pictures and memes of cats, there's no way for your feline-hating friends to surf the web without coming across a kitten or two. But things can get worse for them. Way worse...

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.
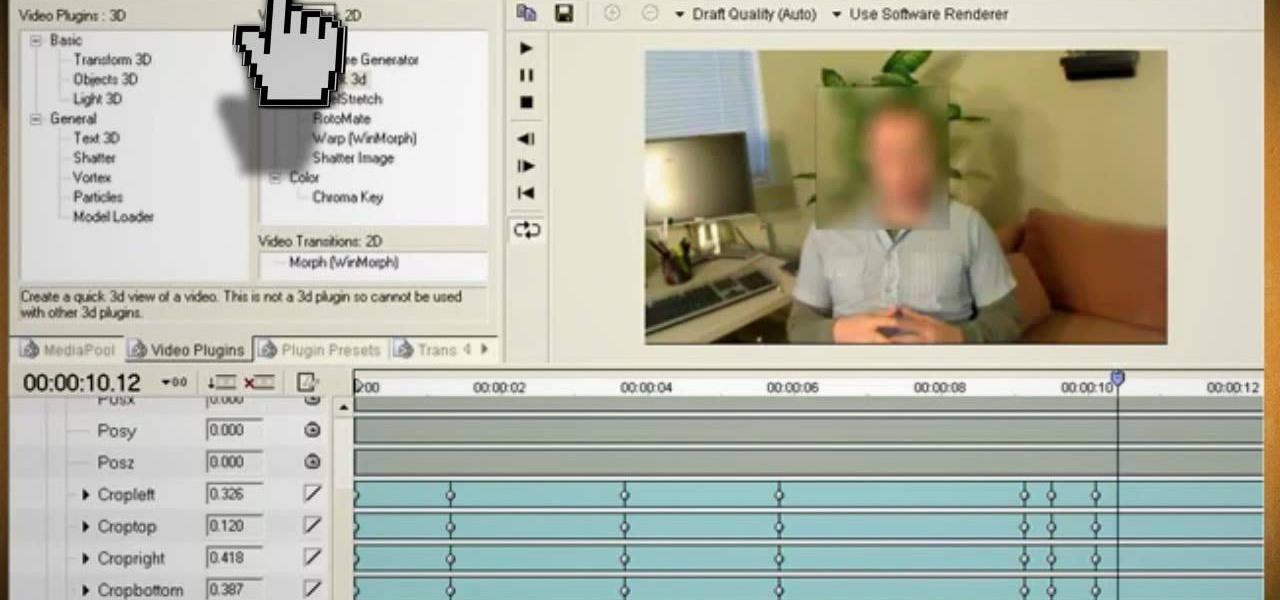
Watch this video and learn how to protect your identity on the internet. This clip will help you learn how to blur out your face and alter your voice when posting videos on the web, where your identity is an important secret. Stay anonymous while portraying your opinions. This software can also be used to avoid release issues with strangers in the backgrounds of your videos. Preventing passers by from having there picture posted with your opinions opening you up for legal action. This can als...

An anonymous sushi chef explains how to make a Volcano Roll. First, he pats down a thin layer of rice over the sliced seaweed. Then, he spreads toasted sesame seeds all over the rice. A layer of salmon is then applied. He then spreads salmon eggs and scallions all over the salmon. Some tempura flakes go over the layer of salmon fish as well. He rolls the entire thing up very tightly to make sure it does not fall apart when eaten. He then deep-fries the entire roll and slices it into even piec...

In this video tutorial the maker of the video teaches us how to setup an account for a friend in order for that friend to be able to download whatever they would like from the Playstation store for absolutely free. The video is extremely detailed and even offers a word of caution as the maker begins the process of creating an account for an anonymous friend. This video is extremely informative and very quick to the point. Its not long and drug out and it is a useful video tutorial to watch. O...

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.
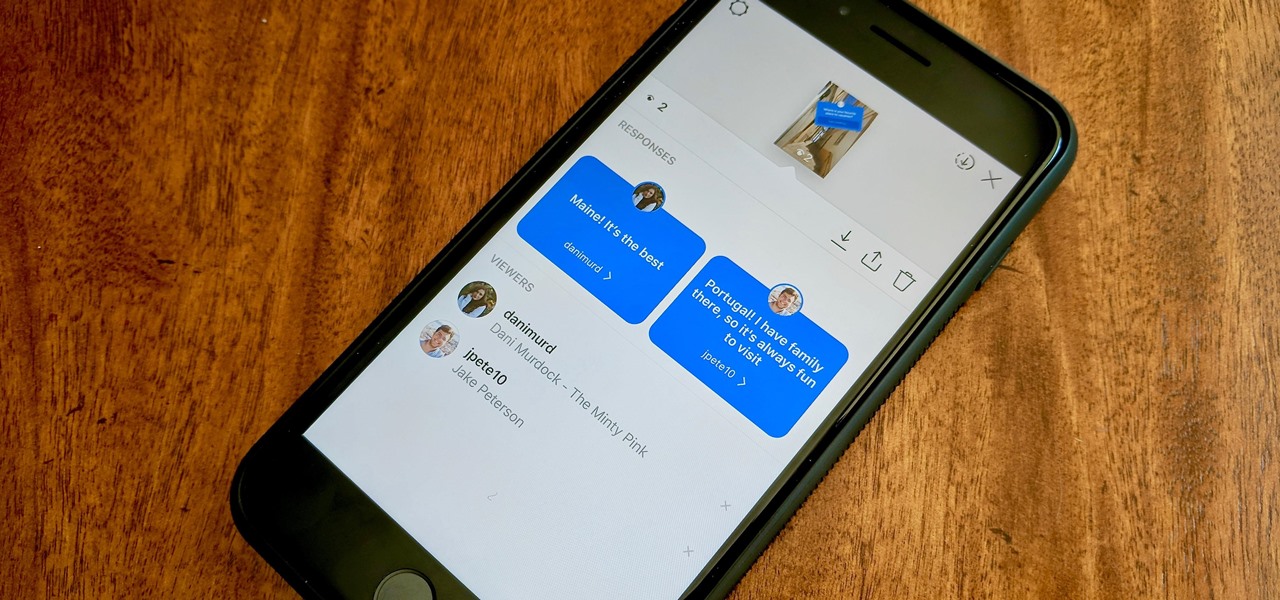
Users on Instagram have taken the app's new "Questions" sticker and run with it — it's tough to find a story in your feed that doesn't proudly sport "Ask me a question." However, it appears there's some confusion when it comes to the anonymity of your answers to these questions. News flash — your username is attached to every response.

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...