When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

See how to remove Personal Antivirus from your Windows PC. The Personal Antivirus malicious software is a tricky malware to remove. This is the easiest way to remove Personal Antivirus from your home computer, so watch and get rid of it!

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

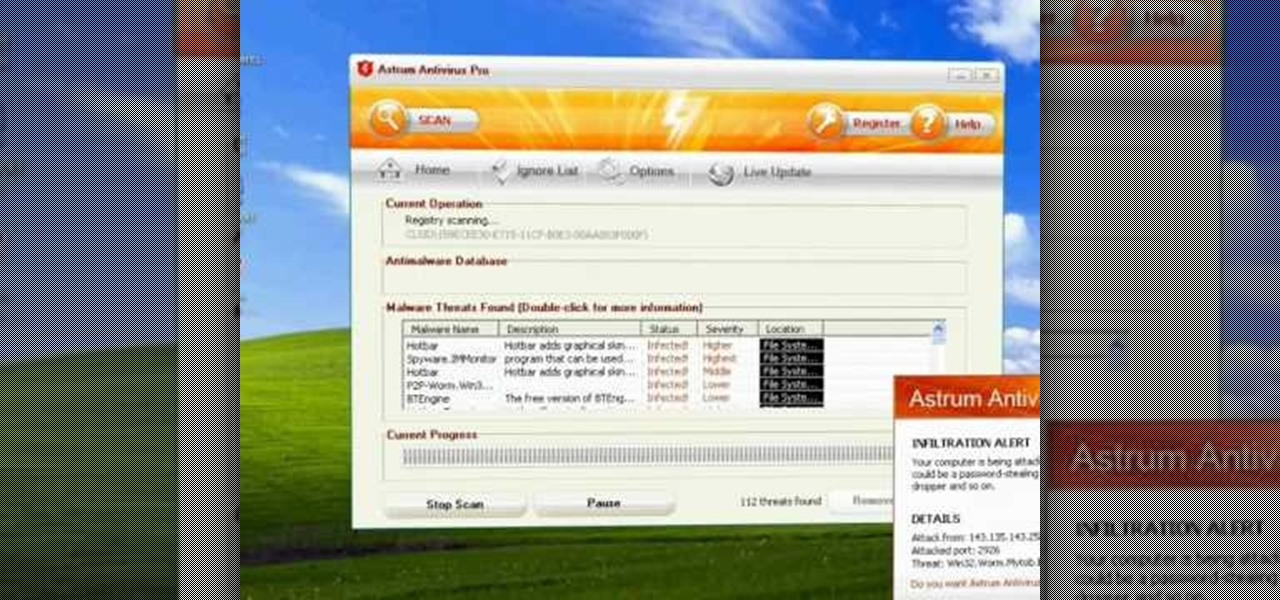
Astrum Antivirus Pro is a rogue anti-spyware application and a clone of VirusTrigger and Antivirus Trigger. Astrum Antivirus Pro is often downloaded and installed by a Trojan or through browser security holes. Astrum Antivirus Pro may generate large numbers of popup adverts. Astrum Antivirus Pro will also display notifications of imaginary security risks in its attempts to get the user to purchase the full version. Astrum Antivirus Pro may run a fake system scanner and then display fake syste...

Antivirus software is needed to prevent junk from the internet effecting your machine. Norton Antivirus comes equip with almost all new Windows machines but can bog down your system. This video will demonstrate exactly how to uninstall any version of Norton Antivirus.

New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software.

AntiVirus Live is a fake antivirus software which comes onto your system and asks you to buy it. It doesn't provide any security to the computer. Here is the procedure to remove it: (1) disable the proxy server for your LAN in Internet Explorer. 2) download the process explorer from ms technet. 3) locate and kill the sysguard.exe. 4) finally remove AntiVirus Live. After following all these steps reboot the computer. Protection against future intrusion is mentioned. You should be aware of the ...

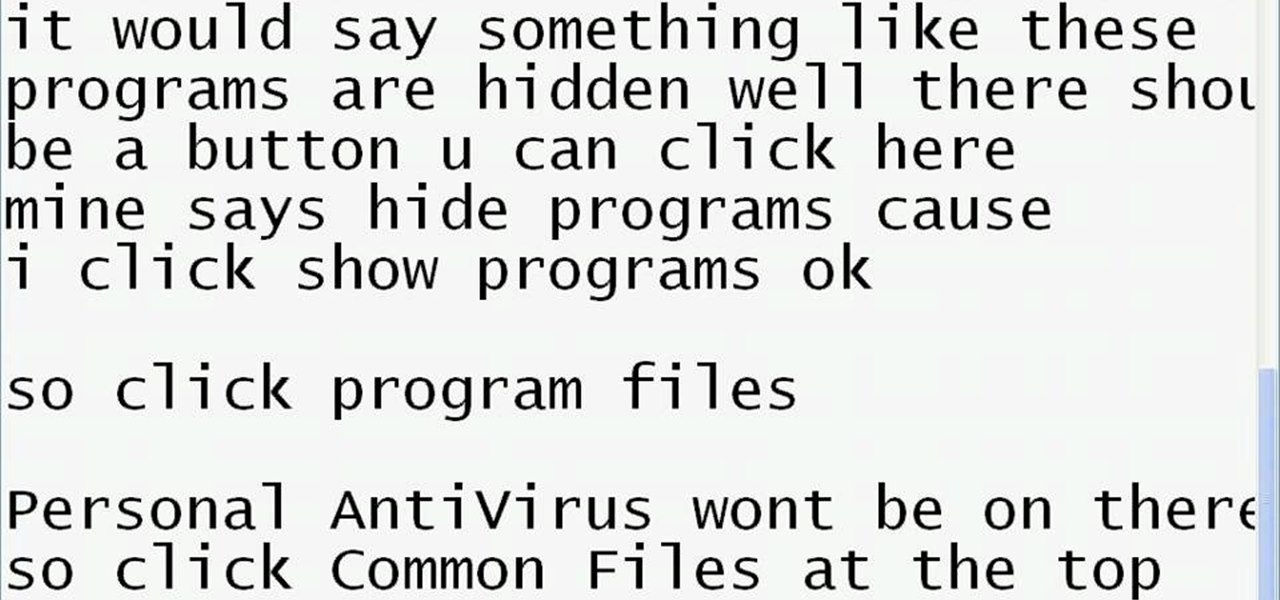
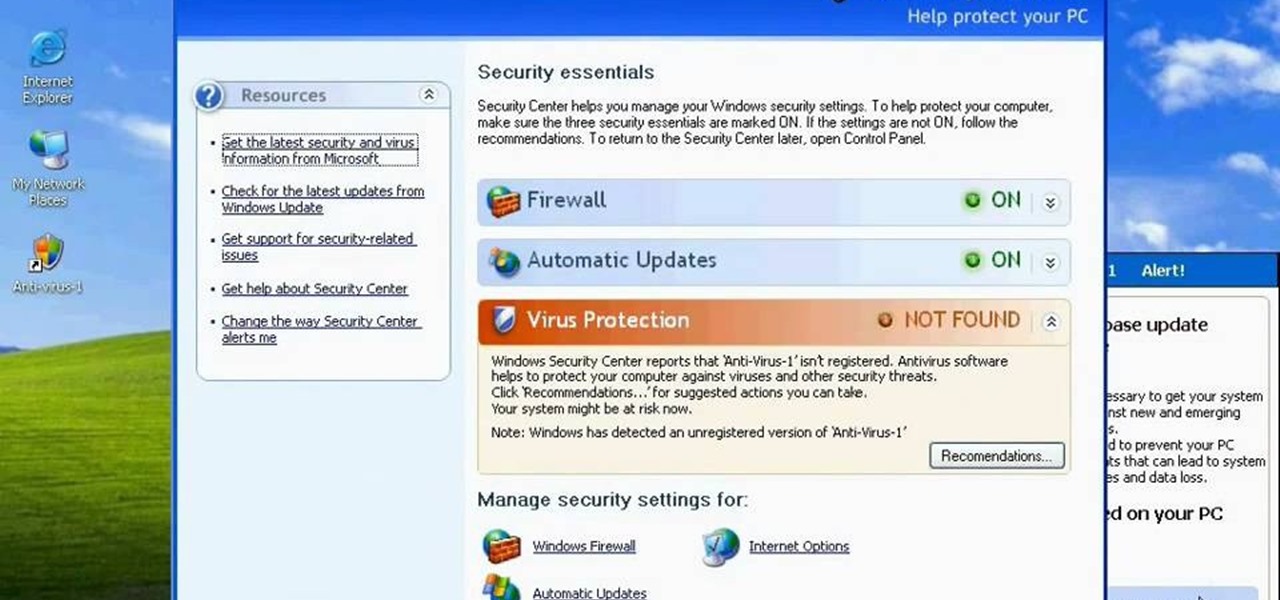
Having problems with your anti-virus software on Windows? Learn how to remove the fake virus protector Personal Antivirus! Personal Anti-Virus is NOT a legitimate anit-virus software and will use spyware to steal info from your computer. Personal Anti-Virus is hard to get rid of and is totally annoying. To get rid of it, you don't have to download anything.

James Marey teaches how to test whether your Anti virus is still working perfectly. First right-click anywhere on your desktop, go to 'New' and select 'Text Document' to open a new document. Now find some text containing a virus from the internet or you copy the text from the video. After entering the text, go to file and save the document. Now if your anti virus is working perfectly it will pop out a virus threat indicating the file you just saved. Finally select the appropriate option to re...

Having problems with your anti-virus software on Windows? Check out this video tutorial to learn how to remove AntiVirus Pro from your computer. AntiVirus Pro is a rogue and fake scanner program that could destroy your Windows computer... see how to remove personal antivirus!

AVG Free from Grisoft provides you with basic antivirus and antispyware protection for Windows and is available to download for free. The only trick is finding it on the AVG website. In this video tutorial, you'll learn how to find and install AVG on your own Windows PC. Take a look!

In this tutorial, we learn how to remove pop up screens when Avira Antivirus updates. First, locate the installation folder for Avira, this should be in your computer programs. After this, locate the file "avnotify.exe". Next, right click this and go to the preferences option. Now, go to security, then edit, then click on the system option. Click "deny" on all the boxes in the bottom section, then save these. Now, the next time your Avira updates, you will not get a pop up box that tells you ...

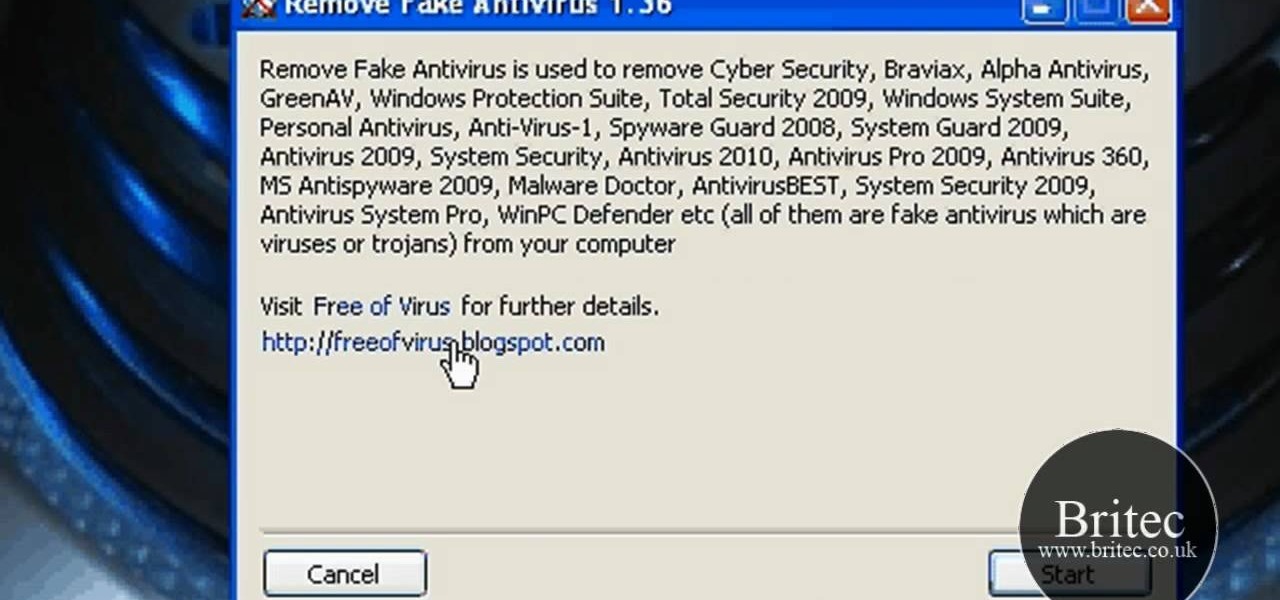
So-called "anti-virus" program doing more harm than good? In this clip, you'll learn how to uninstall fake anti-virus and anti-spyware software from your computer. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

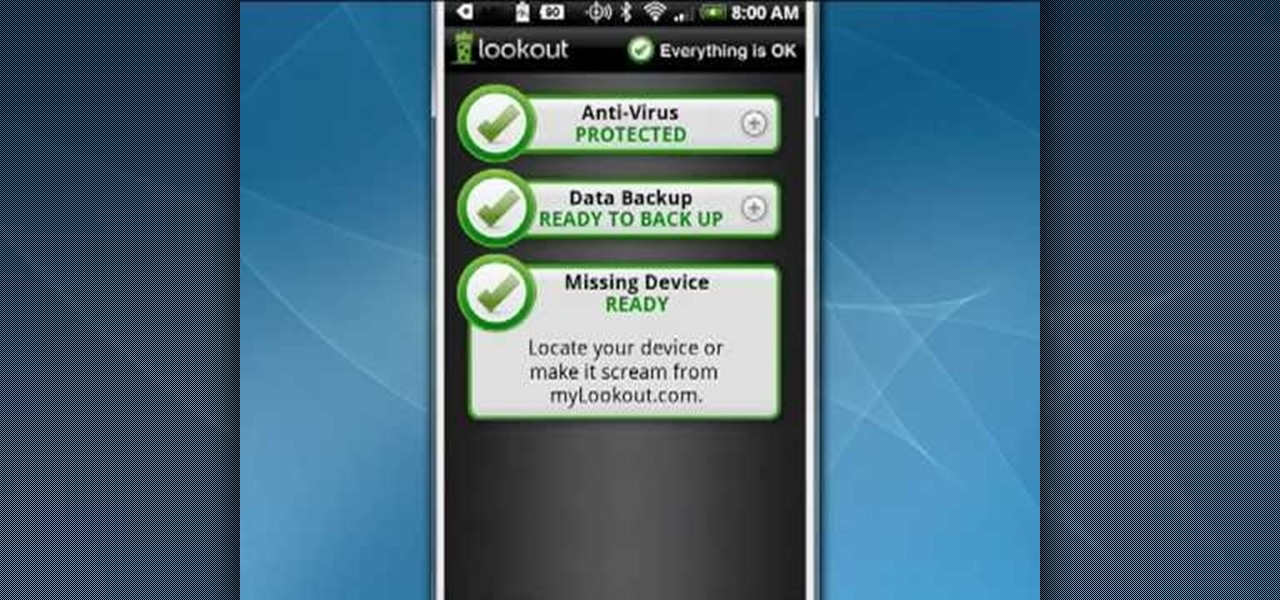
Your Android phone is a computer not unlike a laptop or desktop PC and it shares the same vulnerabilities. This clip presents a quick overview of how to safeguard against viruses and data loss. With the Lookout app, it's easy! So easy, in fact, that this video guide can present a complete overview of the process in about two minutes. For more information, including step-by-step instructions on how to adjust your own Facebook tagging settings, take a look.

Windows has its own built-in antivirus program called Windows Defender, which kinda sounds like a sweet arcade game, but it actually does a pretty good job of protecting your Windows PC from spyware and malware.

http://www.enigmasoftware.com/support... Having problems with your anti-virus software on Windows?

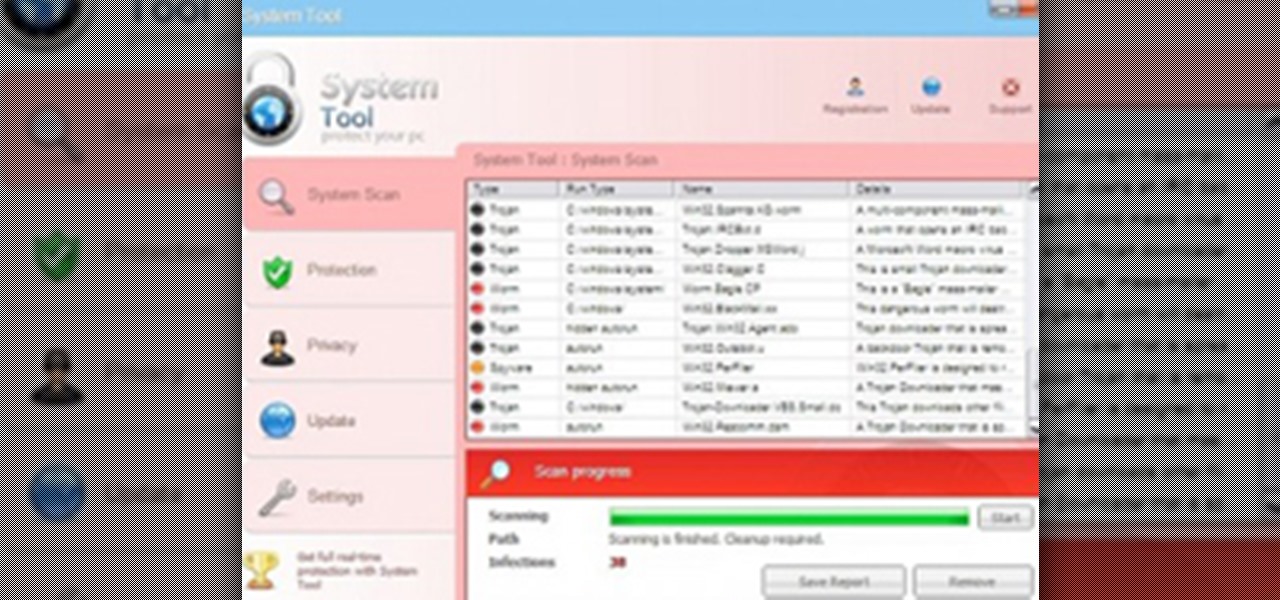
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

Having problems with your anti-virus software on Windows? Learn how to delete the fake virus software Personal Antivirus! Personal Anti-Virus is NOT a legitimate anit-virus software and will use spyware to steal info from your computer.

If you've ever seen something called ThinkPoint Antivirus on your computer, you have gotten one ofhte most widespread and infectious fake antivirus malware programs out there. To get it off your PC, follow the instructions below, or watch this video for an alternate method if this one doesn't work.

MS Removal Tool is the latest in the long line of malware programs that pose as official antivirus software and actually put virus and other tracking software on your computer. This video will show you how to remove MS Removal Tool from your computer and get it working good again.