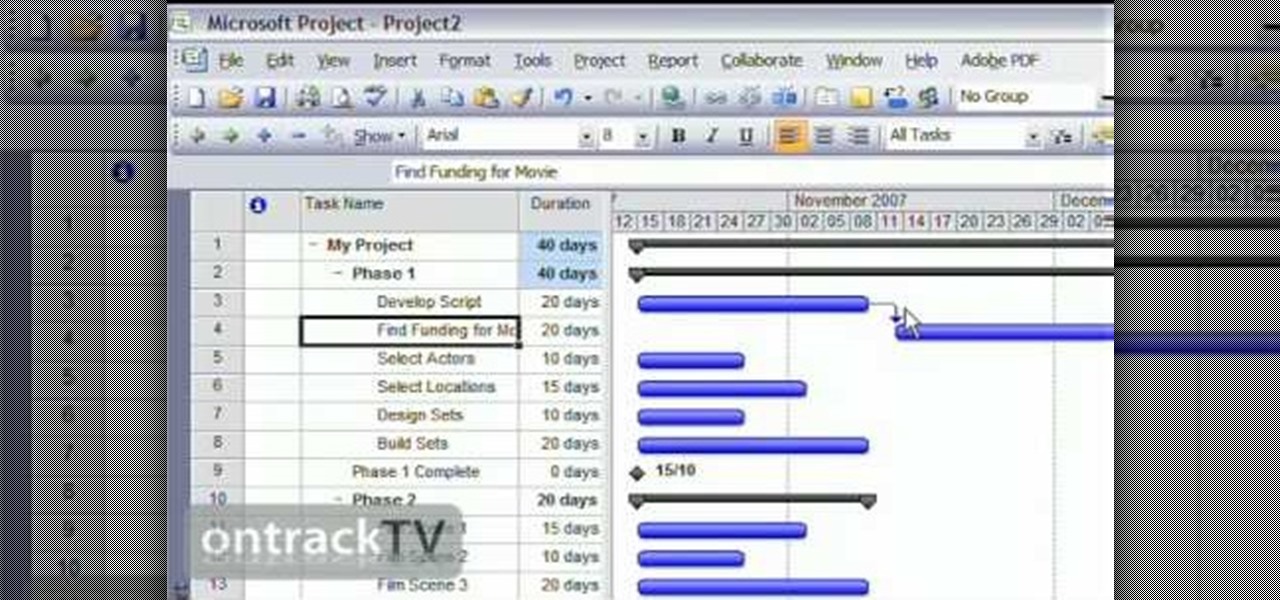
In this Software video tutorial you will learn how to link tasks in Microsoft Project 2007. There are four ways to link a task. Finish to start is the default, then you have start to start, finish to finish and start to finish. Here you will see how to link up two tasks and what is the dependency between them. There are various methods of creating dependency between two tasks. One method is to select the two tasks and click on the ‚Äòlink tasks‚Äô button on the tool bar or you can go to the ‚...

Compulsive gambling is a recognized addiction, just like alcoholism or chemical dependency. Follow these steps to see if you might fit the profile. Recognize the signs of compulsive gambling with this guide from Howcast.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

In this series, we are going to get you to the edge of building your own cloud-based, cross-platform augmented reality app for iPhone, Android, HoloLens, and Meta 2, among other devices. Once we get the necessary software installed, we will walk through the process of setting up an Azure account and creating blob storage.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that don't quite understand what's going on.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

The iPod changed the music and electronics industries when it was first introduced way back in 2001. It is credited with ushering in the age of "connected devices," and has held a huge market share of around 70% for years. At the height of its popularity, the iPod made up almost 50% of Apple's revenue. Now that the smartphones and tablets we use every day have the ability to store and play music, the iPod's glory days are over. Nevertheless, there are millions of people who still use them, an...

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

When you want a helpful task manager on your iPhone or iPad, any of the nine apps in this guide should be at the top of your list. But we'll review each app's features to help you determine which one might be best for your workflow.

In this online video you'll get tips for recognizing signs of drug & alcohol addiction from a former addict. John DePalma explains how drugs can affect the brain and the long-term affects of addiction on the body. He explains the symptoms of several types of drug use, from alcohol and marijuana, to harder drugs like cocaine, crystal meth and heroin, and warns of the dangers of abusing prescription drugs like pain killers and anti-anxiety drugs as well. He then explains how to approach an addi...

Horses penned together can easily become dependent, or buddy sour, and suffer from separation anxiety while being ridden individually or involved unaffiliated activities. Instead of letting the horses work themselves up into anxiety which may cause them to hurt themselves, get sick, or generally injure their health, cure the horses of their co-dependency. Learn how to cure a buddy sour horse by watching this video tutorial from expert horse trainer, John Lyons. Cure a buddy sour horse with se...

Want to travel light? With a little research – and a lot of editing – you can lose your luggage dependency one overstuffed bag at a time. Pack everything for your vacation into a carry-on.
With the increase in pollution levels, Union government has planned to put around 7 million electric vehicles on Indian roads by 2020. It is speculated that the sum of investment required to do so will be around Rs 22,500 crore as per the report submitted by Society of Indian Automobile Manufacturers (SIAM).

When you look up the word free in the dictionary, you'll find a lot of definitions, but in the days of digital dependency and a falling economy, free only means one thing—expensive stuff for nothing. And if you own a Windows computer, one of the best sites to get free software from is Giveaway of the Day.

I'm not going to lie. I was Catholic. But one of my reasons for my faithful departure was having to tell my innermost secrets— my sins— to a silhouetted figure behind a latticed screen. With the creepy enclosed booth structure and separation of sinner and confessor, its anonymity was clear, yet deceiving. You always knew the priest and he always knew you. If I wanted total privacy, was there really a need for this intermediary to God?
Recently, I decided to install Kali 2016 as dual boot on my laptop. Everything install perfectly up until the installer gave me the option to set up the package distribution mirror. No matter what setting I provided, no mirror would set up correctly. I was forced to continue the install without setting up the mirror. If you do not know what this means, I will explain it. Basically, you will not be able to update or install any tools onto your Kali distribution.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...