The pegged bowline, as demonstrated in this how-to video, is similar to a bowline on a bighte knot. Using pegs to construct knots is well documented. Simply tie the bowline as usual in the bight of the rope then peg the running end to the standing part. Watch this video knot-tying tutorial and learn how to tied a pegged bowline knot.

This video teaches viewers on how to inspect a motorcycle for damage after an accident as well as documenting it. The most important thing you need to do after an accident is to document all parts of the damage by taking photos of the damaged parts. Start by verifying the VIN number or Vehicle Identification Number and take a picture of it, take a photo of it. After that, get a photograph of the mileage on the dash area of the motorcycle. If there is other important information that needs to ...

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

This is an Electronics video tutorial where you will learn how to manually adjust the zoom position on the Nikon SB-900 with the diffuse dome attached. This is called the dome trick. It is not documented in the SB-900 user’s manual. The manual states when the diffuse dome is attached to the flash head, it gives a fixed zoom position of 14mm. However, if you attach the diffuse dome upside down, you can adjust the zoom position manually. The video then demonstrates changing of zoom position aft...

This video is about combining Microsoft Project 2010 and SharePoint 2010. This combination helps project teams to collaborate and share project information. Information can be displayed on a dashboard. We will also discuss various levels of project management such as starting the project, planning, tracking and reporting on the projects progress.

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.

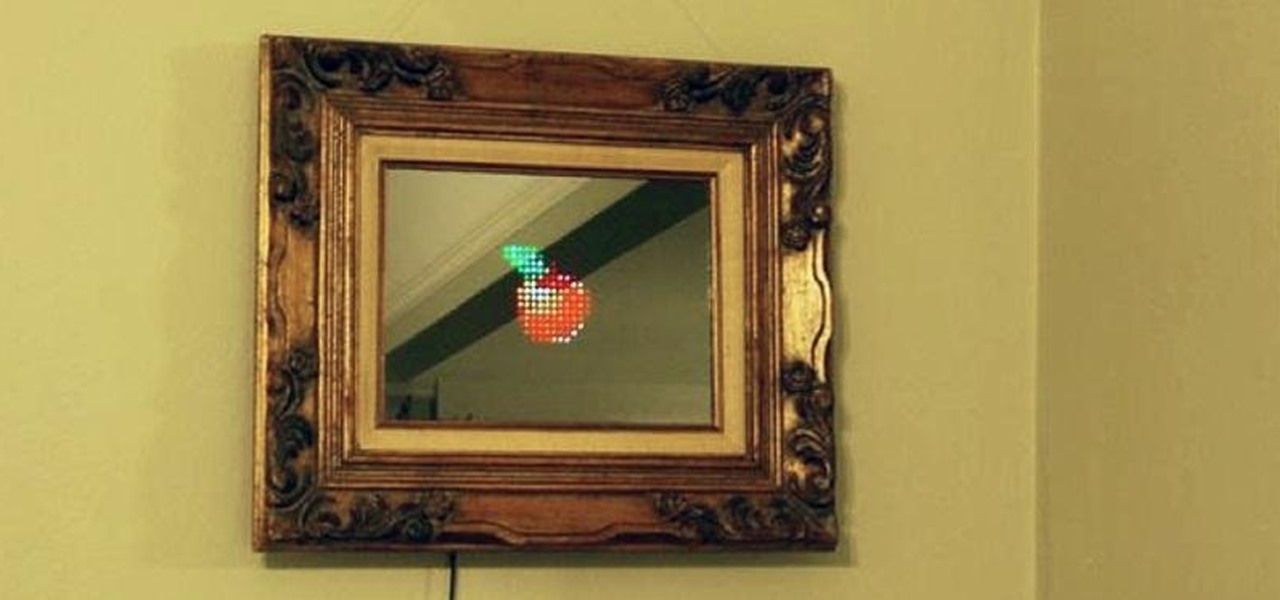
Fool your friends, scare your cat, play a game while also admiring your physique! This "magic" mirror lets you do all that and more by letting you display words, pictures, videos, and even some games—all controllable through a mobile phone.

Here's an awesome weekend project that could leave you with a fearsome "Ping Pong Ball Mauler" capable of firing hundreds of balls a minute at your unsuspecting neighbors. Christian Reed built it out of a poly drum and a homemade pneumatic device. He turned a standard shop vacuum into a high volume, low pressure system that allows his contraption to continually fire a constant stream of ping pong balls at a rate of hundreds of balls a minute. Best of all, all of the parts he used can be bough...

Over the past two years, Apple's Worldwide Developers Conference (WWDC) has become a showcase for new ARKit capabilities. This year, it could offer more information related to Apple's long rumored augmented reality wearable.

Arthur van Hoff, former CTO and co-founder of Jaunt, is taking his immersive content talents to Cupertino.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

We've all been there... admit it. You sent a couple messages, but your friend had the "Read Receipts" option turned off in WhatsApp, so after a few minutes, you start wondering if they're away from their phone right now or just flat-out ignoring you.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

There is a question that has haunted man since the dawn of time: What if you could combine your tablet and your smartphone? Historians around the world have documented wars on the subject, and philosophers and kings who dared ask the question went down in the annals of history.

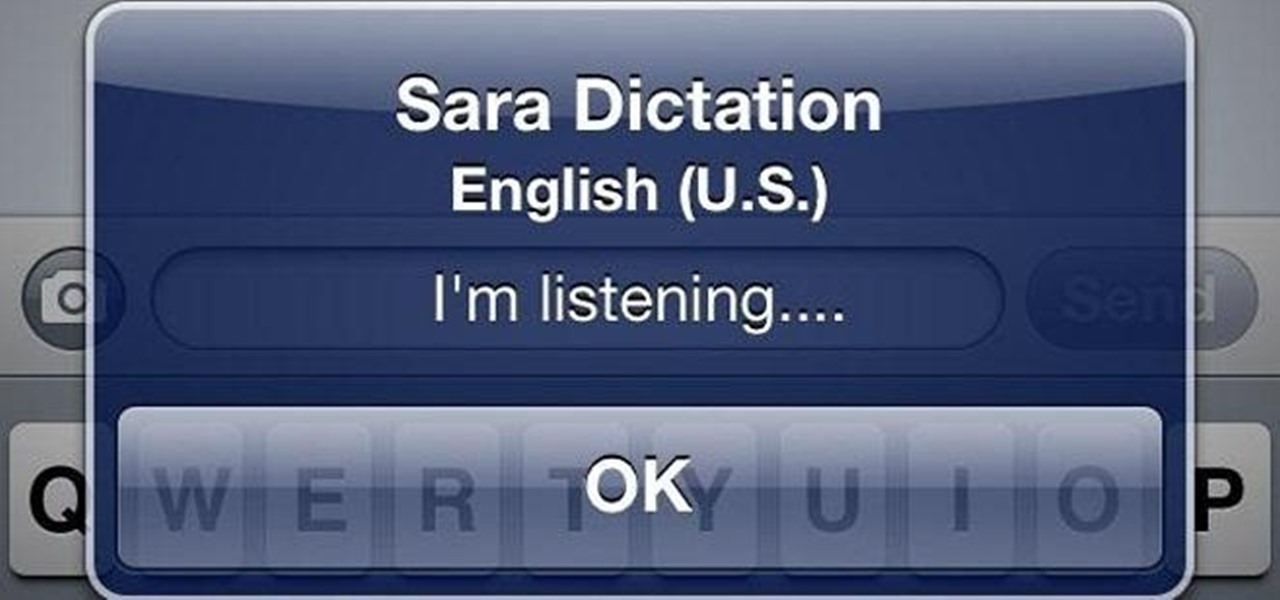
My obsession with Siri is well documented, and after I jailbroke my iPhone 4 recently, I thought I would finally be able to rekindle our imaginary love. But, when I downloaded the Siri Port, I found that the app was buggy and super slow.

By default, your Samsung Galaxy S III comes equipped with a few app shortcuts that are available from the lock screen. But what if you don't use those apps very much? Wouldn't you rather customize the lock screen icons on your S3 to your favorite and most used apps?

Everything is documented these days, thanks to the Internet and mobile devices. Most people who own a smartphone use it to take lots of pictures. If you're one of those people, an app called Scoopshot can help you turn some of those photos into extra cash. Scoopshots lets you post your pics so that news organizations can pay you to use them. Companies can also post tasks, so if someone is looking for a particular photo in your area, you can accept the task, go take the photo, and earn money f...

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Last week, iOS 12 developer beta 7 was quickly pulled upon release, due to complaints of poor performance and instability issues. While Apple tackled these bugs with the release of developer beta 8 two days later, testers are seeing beta 7 again in their Software Update settings. Why is beta 7 back, and, more importantly, is it safe to download?

Unsurprisingly, Google wants to be the caretaker for augmented reality on the web, and its latest move in this endeavor is a 3D model viewer prototype called Article that's designed to work across all web browsers.

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

Researchers have been studying the blood meals of flies to understand the flow of infectious pathogens in wild animals.

Some Montana inhabitants have been making impassioned pleas to legalize raw milk this week. The debate took place during a hearing on House Bill 325, which was held by the Senate Agriculture, Livestock, and Irrigation Committee on Tuesday, March 21.

From a quick, passing glance at a photograph, you may not notice that Jon Almeda's impressive displays of ceramics mastery are actually the size of coins. It's well-documented how much tiny art is loved by WonderHowTo, but this petite pottery may take the cake as the most impressive display of craftsmanship.
Welcome back Hackers\Newbies!

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

We tend to assume that eating is mostly a physical act, but the mind has so much to do with the choices we make.

Any living creature will die if deprived of sleep for long enough. The longest documented occurrence of a person not fully sleeping and surviving is only 11 days. There is a rare disease where deep sleep is never achieved, affecting roughly 100 people worldwide. Patients usually only survive between 6 to 18 months after the onset of chronic insomnia, and only 3 to 9 months in a parasomnia state without any real REM sleep.

Mobile augmented reality pioneer Blippar has now completed its fall from hopeful AR startup to the immersive computing history books.

It seems that mobile app developers are constantly coming up with new ideas to apply augmented reality, with Apple's ARKit promising to increase adoption in apps exponentially.

A 'superbug' fungus is currently running riot in the hospitals of New York and New Jersey. This outbreak of Candida auris has contributed to 17 deaths in NYC, according to recent reports.

Guys, this has got to stop. It's not funny anymore. I'll defer to one of my all-time favorite people when it comes to my feelings on this unsavory subject:

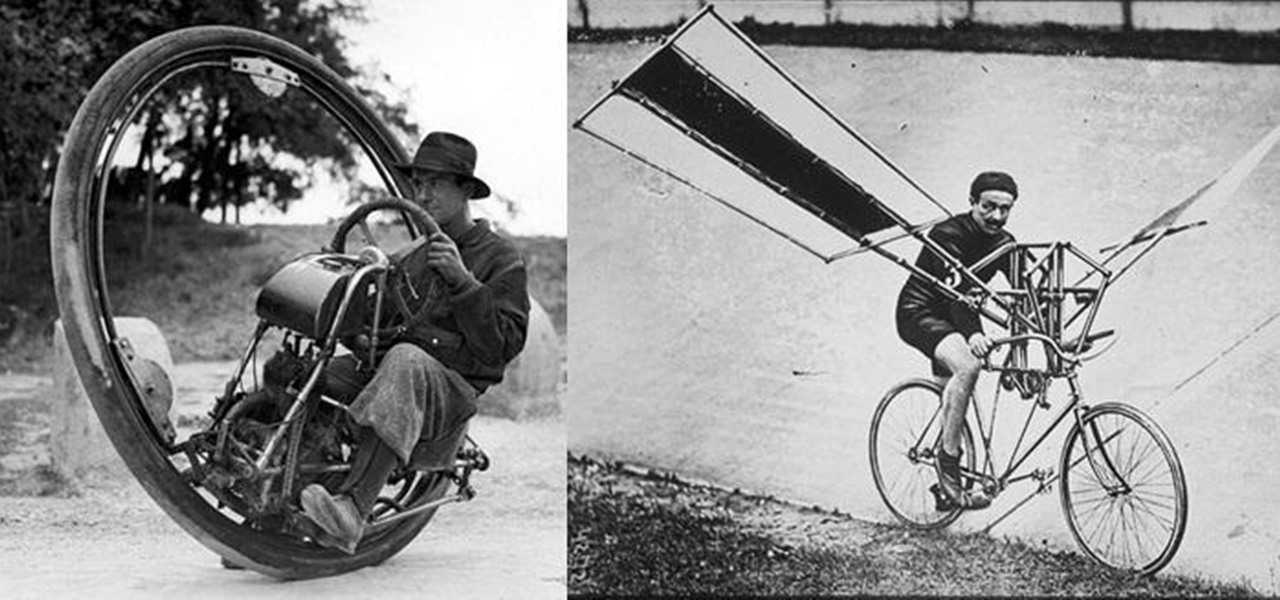
We don't spend much time thinking about bicycles today, do we? Sure, they're a "green" alternative to driving everywhere in cars, but the vast majority of America has dismissed them as simply being too much work, or more importantly—too slow. That wasn't always the case, though, I assure you!

If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

Colorectal cancer — cancer of the colon or rectum — is the third most commonly diagnosed cancer in the US. To reduce the chances of a diagnosis we are all urged to stop smoking, keep our weight down, decrease our intake of alcohol and red meat, keep active, and get screened for colon cancer. But, new research has found something that participates in the development of colorectal cancer that might not be as easy to control: A strep bacteria that promotes tumor growth.

A new study casts real suspicion on the possibility of life on Mars. Why? It seems the surface of the planet may be downright uninhabitable for microbial life as we know it.

While Lyme disease can be disabling, the wrong treatment for the infection can be fatal.

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.