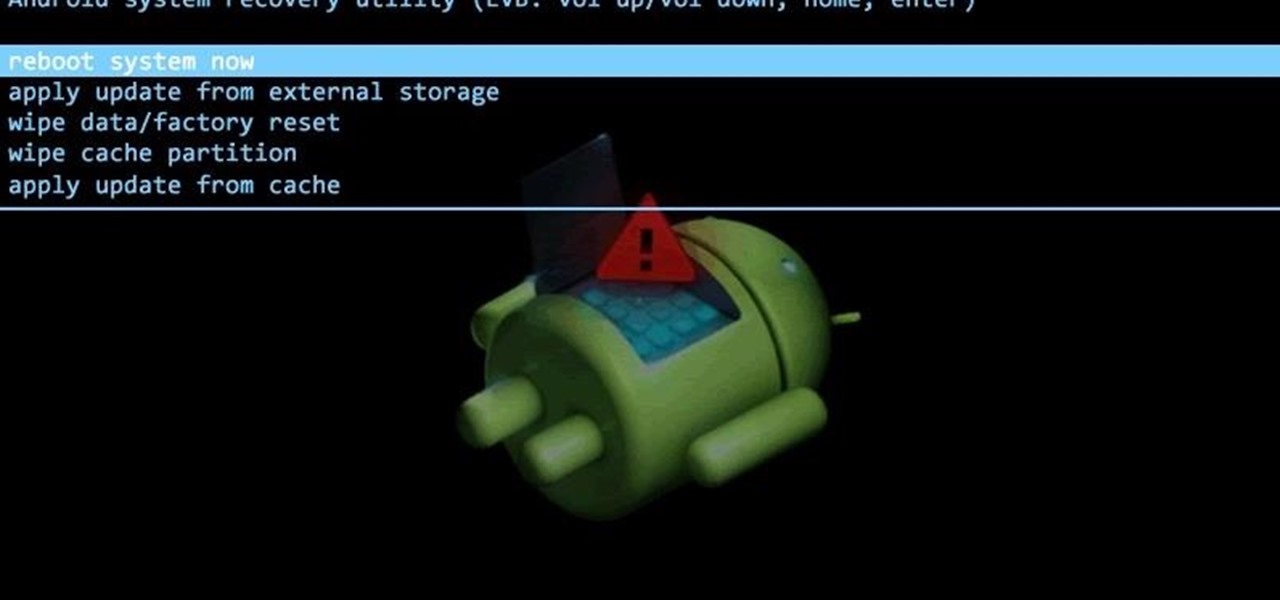
It is really quite easy to flash a custom recovery to your Nexus, and there are many excellent tutorials on how to do so (see the How-To below): The Easiest Way to Install a Custom Recovery on Your Nexus 7 Tablet « Nexus 7.

If you've ever wanted to scour the basement of a Hollywood hotel looking for evidence of a gruesome murder spree, this new AR experience might be the game for you.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

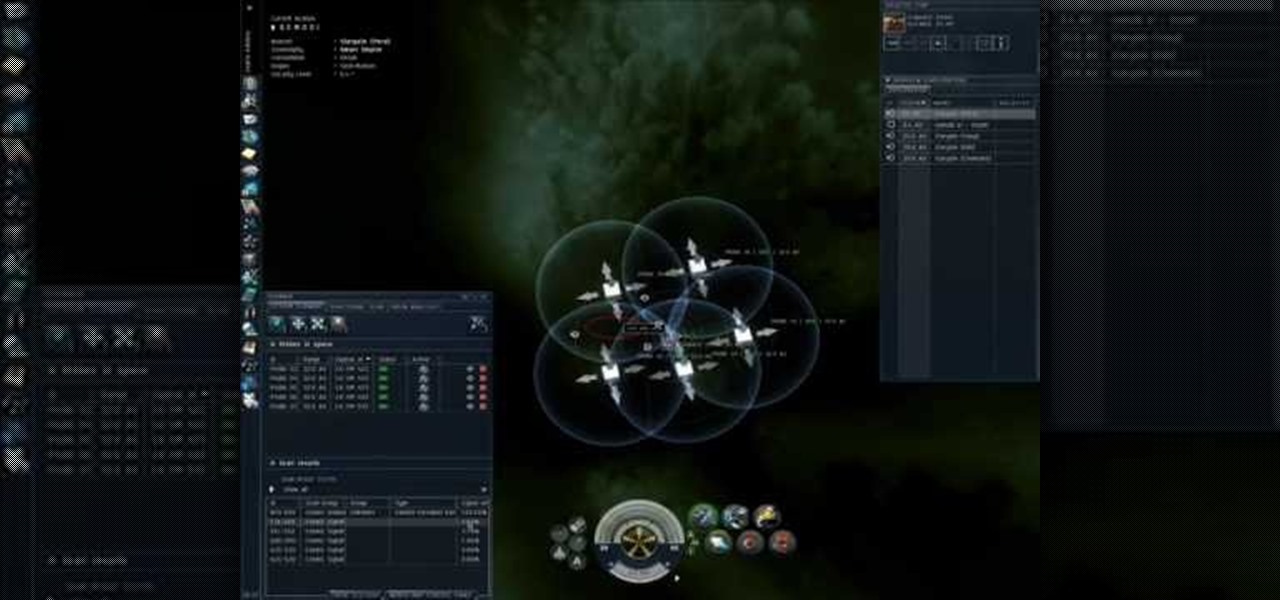
Avoid an ambush and detect what's available in a given star system! You'll need to learn how to use probes to scan the surrounding area if you want to do a lot of exploring in EVE Online. This video shows you how to set up your probes and execute the scanning function.
Our class had been assigned interviews with political representatives from different branches. In these interviews we asked questions that we had generated about their career position, advice to young activists, our government system, getting involved, and their opinion on certain laws. Here are the results from the two interviews that were done.

Ever wonder why Jupiter has those colored bands across its surface? Jupiter's enormous mass is made from an array of different liquids, and those fluids do not play well together because of their different makeup. All of the hydrogen- and helium-based fluids are thought not to be miscible, which means that they aren't homogeneous in nature, resulting in strikingly beautiful bands across the planet's surface. But what about viscosity and how that correlates to the development of planets? What ...

In this guitar lesson, Justin gives some tips on practicing and exploring the pentatonic scale. He gives some steps on how to add variation so it doesn't always sound like a scale.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

A new cross-licensing patent deal signed by Nokia and Chinese smartphone maker Xiaomi will bring increased collaboration between the two companies. One area of focus in which both Nokia and Xiaomi have already agreed to work together is augmented reality.

In a new update, the iPhone 16 lineup is finally getting Visual Intelligence, a feature that lets you instantly gather information about anything around you just by snapping a picture.

Virtual, mixed, and augmented reality all provide different but compellingly immersive experiences that draw us in through sight and sound. But what about our other senses? A few strange inventions are already exploring the possibilities.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.
24th Street Theatre Saturday Explorer Series 2012 Saturday Explorer Series 2012

Sometimes when you're camping it's necessary to pitch a little something called a tent after a long trek hiking and exploring the great outdoors. And when you're ready to call it a day, make sure you can do so peacefully without the fear that your tent contraption will fall down on you during the middle of the night.

Here's an approach to different concepts within liquid through one of the foundational concepts- the handflow. You can use the handflow as a gateway of learning many other liquid dance concepts. Note: Be sure to click on Chapter 2 (A continuation of using the handflow as a gateway to several liquid concepts) and Chapter 3 (Another section of exploring several liquid concepts through the handflow) to watch the full liquid dance tutorial.

Flickr is the most known and dependable photo sharing website to date, so if you haven't made an account yet, you better now, if you want to share your precious photos with family, friends, and even the whole world! Flickr allows you to store digital photographs online and share them with other people.

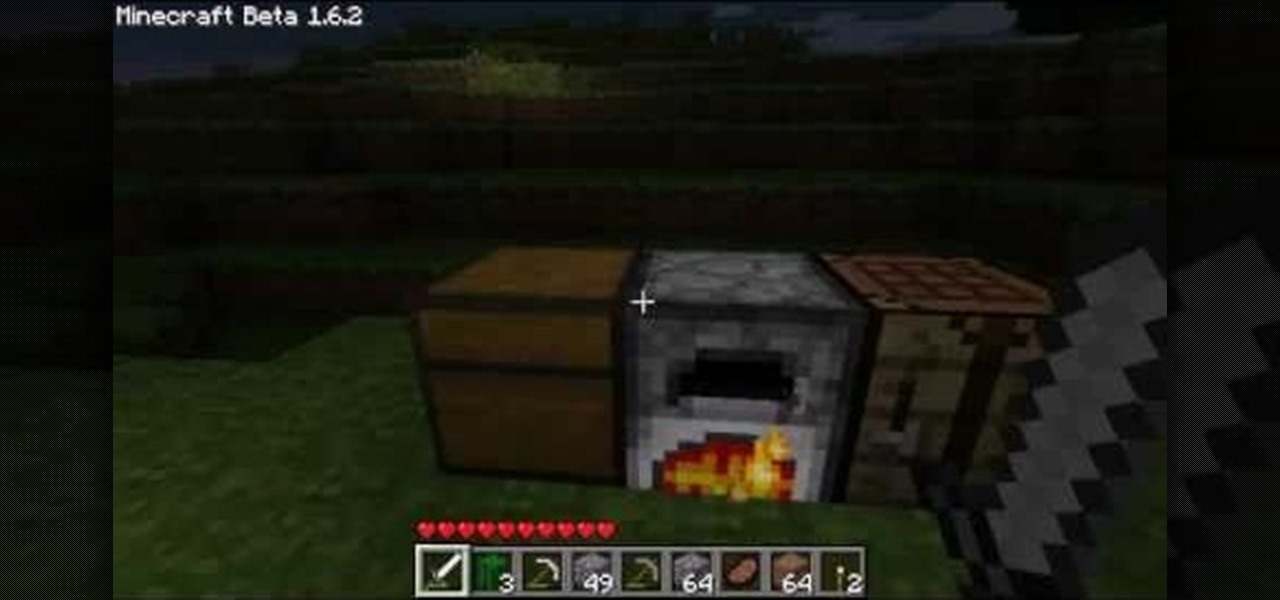
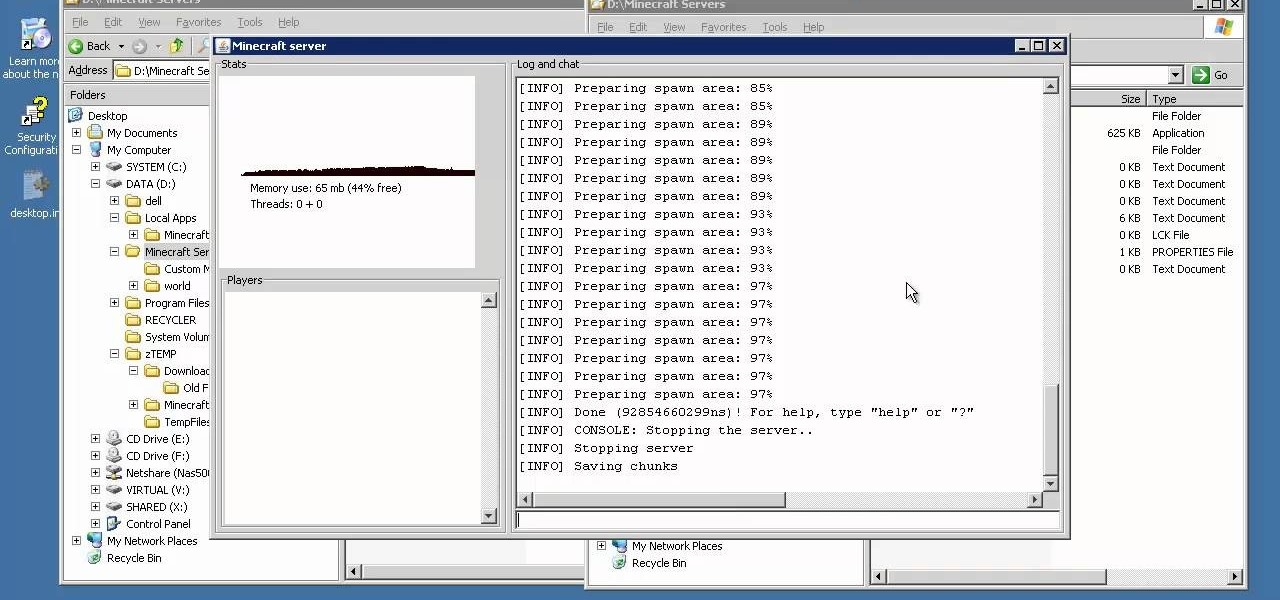
One awesome feature for Minecraft is the addition of the compass. It will always point you directly back to your spawn point in the game. This should help keep you from getting lost and losing your shelter or house while out exploring. In this video you will get a quick tutorial on how to build it using one red stone and four steel bars. Enjoy!

At some point in Fallout: New Vegas on the Xbox 360, you'll eventually find yourself in Hidden Valley, the secret location of the Brotherhood of Steel. After exploring their bunker, you may find yourself meeting with Knight Torres, the Quartermaster for the Brotherhood of Steel. She will tell you that she is missing a Laser Pistol from her last shipment and wants you to go look for it. Well, not just any old Laser Pistol will do, apparently— she wants something very specific. In this video, y...

In this video, we learn how to do a touchdown raiz freerun trick. First, you will start off by running into a raiz move. This move is where you will lean onto one arm and then come down onto it and swing your feet around in front of you. This will look like a one handed cartwheel where you twist while you are in the air. Practice doing this at different angles to help better prepare yourself for doing this trick. When you have it mastered, you will be ready to do these more often and work out...

Here we learn how to insert secret symbols from your keyboard onto Facebook or any other regular program. This only works on PCs, sorry Mac users! By holding down the alt key and pressing numbers on the keypad from 1-9 and beyond, we discover there are many different symbols that pop up. There are smiley faces, arrows, numbers, punctuation marks, and various other random symbols. Exploring these on your own is simple and will show you everything there is to choose from. You can get creative w...

The Wedge ROP is a render output driver, which can be used to change variables on the fly while rendering. This can be very useful when simulating, in that you can test out different parameters to see the different results. It's a relatively new feature in Houdini 9.5.

In this software tutorial you will learn how to create an island terrain in Unity 3D game engine. PART 1 covers creating a new project and exploring the interface.

If you are looking for a low impact exercise with tremendous benefits, consider exploring yoga. This pose, called Janu Sirasanasa, or Head to Knee pose, will stretch and strengthen your back, legs, core and internal organs. Practicing yoga can also bring calm and clarity to the mind.

Start playing one of the most popular browser based science fiction games DarkOrbit! This tutorial gets you started, showing you how to create an account and choose your faction (Mars, Venus or Earth). Then the basic system is demonstrated, so you can start exploring space!

Expand your belly dancing horizons by exploring the world of Saidi style belly dancing! The Saidi style of Egyptian belly dancing often incorporates a cane in many of the dance moves. Practice dancing with a cane in Saidi belly dancing with help from an expert: Sahira began her career as a Middle Eastern dancer in Houston, Texas under the direction of Thalia and Shakira Masood-Ali. Get advice & more belly dancing lessons by searching Wonder How To!

What's new in Minecraft 1.6.? Maps and Trap Doors are brand new additions to the game. This video will explain what they are, how to build them, and how to use them. Learn while exploring the newest version of Minecraft beta.

if you've already seen this video and you are playing Minecraft on your own server, you're ready to start playing on custom maps. You can download maps here. Custom maps make playing Minecraft even more fun. Enjoying exploring these new worlds!

Here's a handy guide to unlocking all of the alternate costumes available from the Krypt in Mortal Kombat 9, on the Playstation 3 and Xbox 360 consoles. Expand your Mortal Kombat wardrobe by exploring the Krypt and purchasing the alternative costumes for your favorite characters.

Don't be just another red shirt! Here's a detailed tutorial showing you how to engage in ground combat when exploring a planet. Make sure you've equipped the right weapons and know how to use their expose and exploit functions!

Check out this instructional science video that demonstrates how to perform the experiment "Dye Detective." From the Oregon Museum of Science and Industry's teacher curriculum, "No Hassle Messy Science with a Wow", this is an activity exploring ink colors. Learn how to perform the Dye Detective experiment by following the simple step by step instructions outlined in this science tutorial video!