Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EQ Series Telescope to ogle the universe.
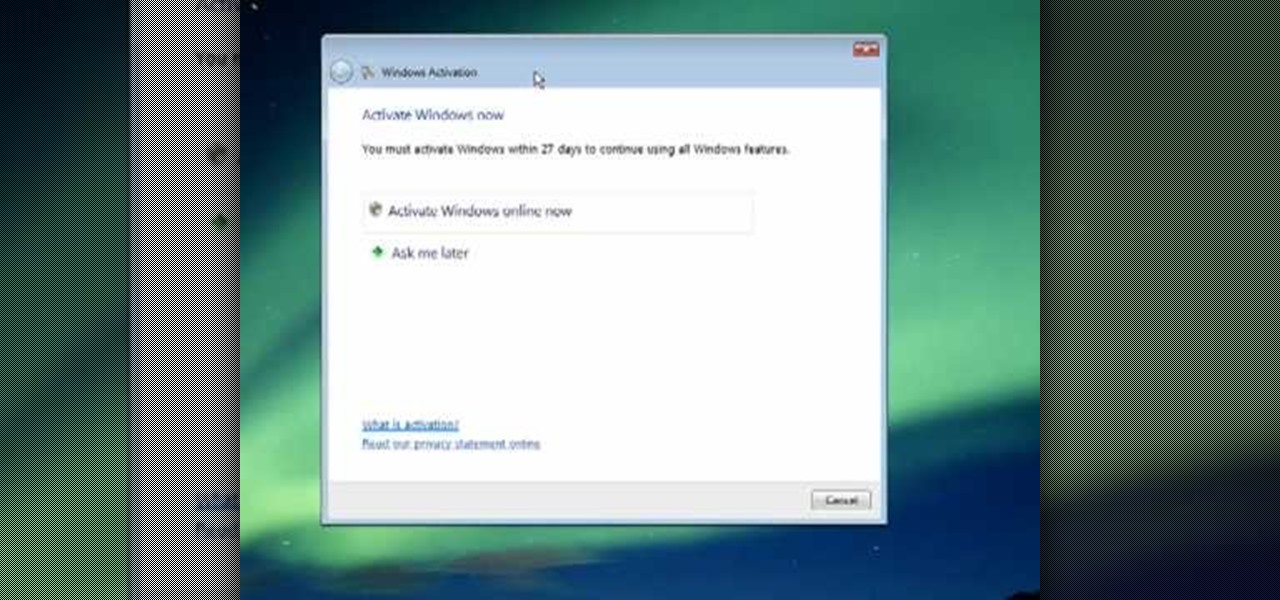
This video describes how to activate your new copy of windows. When you get a new computer or install a new copy of windows you have to activate it within 30 days. When you activate windows the activation process gathers information about your hardware and activates your copy of windows. You will click on the button that says activate windows online. It may take a few minutes and then it will be activated once it gathers all of the information from your computer. This is simply a method of pr...

Stock are very easy to make and even easier to remove the fat from. In this how to video Chef Paul talks about removing the fat from your cooking stock. Watch and learn how to make your broths just a little healthier by removing the fat that gathers at the top.

John Campbell, from azbushman, demonstrates how to make a quick bow and arrow in the wilderness by collecting natural materials and constructing them with cord. He starts by finding seep willow (also called coyote willow) that grows in clumps near rivers. He cuts ten willow sticks and ranges their lengths from about five feet down to about one foot, each a couple of inches shorter than the next.

The young lady in this video describes to the viewers how to make "Puffed Sleeves". You can use shirts, jackets, men's' shirts, ladies shirts, just about any shirt to make these on! She starts out with 2 ladies shirts, one oversized and one fitted. She also gathers scissors, thread, straight pins, a marking pencil, paper to trace the pattern on and paste. She then demonstrates how to cut the pattern by tracing the outline of the sleeve onto the paper, how to pin the shirts using the straight ...

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

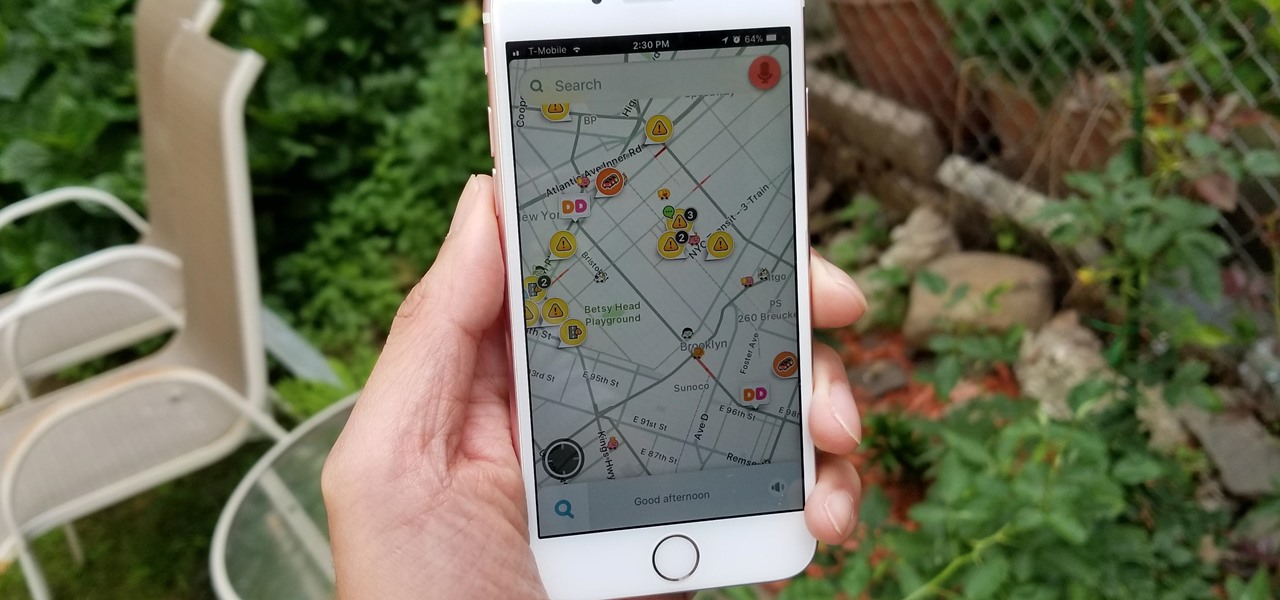
Some of the things that make Waze such a great navigation app are also its biggest downsides. Real-time data shows where individual users are, and the app automatically gathers traffic info that other drivers may encounter. These elements ensure that road conditions are as up-to-date as possible so that everyone gets to their destination safely, but it's certainly not ideal if you're a privacy-minded user.

It's always tempting to grab yesterday's shirt and toss it on in a fit of laziness, but before you do and venture outside, it's probably wise to freshen it up a bit first. The most obvious way to do that is with some Febreze, but if you don't have any around, your liquor cabinet will do the trick.

With Chromecast-capable applications slowly seeping into the market, it's difficult to find useful ones that we might use on a daily basis.

Jim McKelvey is going to show you how to blow glass. One of the secrets to making really nice glass is making really even gathers. So, if you're a beginning student, there are some tricks that you can use to learn how to gather correctly. That's just part of what will be covered on this series about beginning glass blowing.

The Pixel 3 has an indisputably great camera, but a software update coming soon is going to make it even better. Google will be adding a "Night Sight" shooting mode that's so good with low-light situations that you'll have to see it to believe it.

Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify.

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

Samsung put some of the industry's most advanced camera tech in the Galaxy S20 series. However, their image processing still lags behind the Google Camera app found on Pixel phones, so the end result is good but not great. Luckily, you can install a mod to pair that beastly hardware with arguably the best camera software.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Google is widely renowned for its mastery in using data to tailor specific search results and ads. Their Android and iOS search apps put this ability to use in finding the most relevant pages for your query, and their desktop site is the most-used search engine on the web as a result of it.

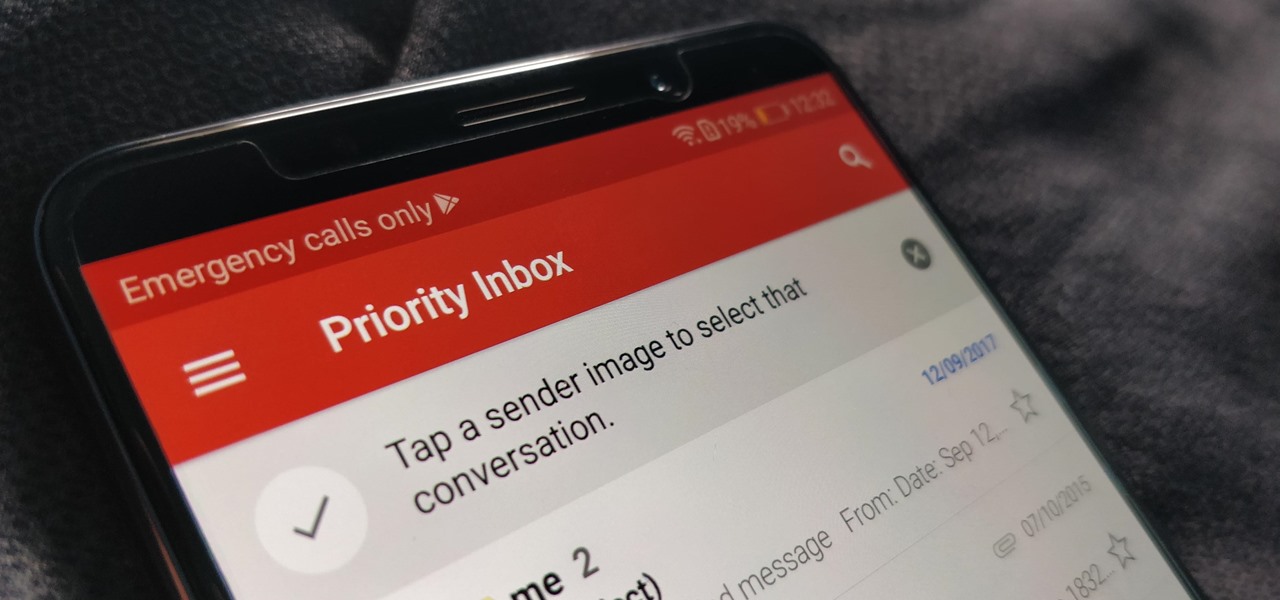
On average, an office worker receives 121 emails a day. Many of these emails are trivial and don't require immediate attention. While Gmail's automatic spam filters catch plenty of irrelevant emails, some still make their way into your inbox. Fortunately, Gmail's tools aren't limited to just spam filters.

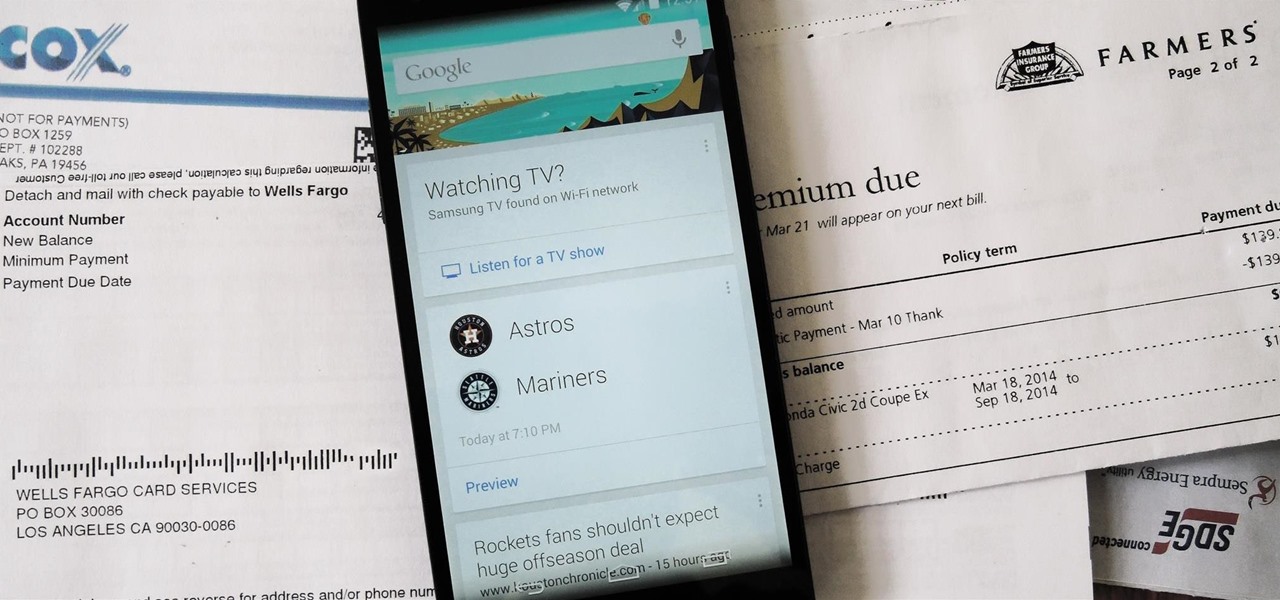
With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

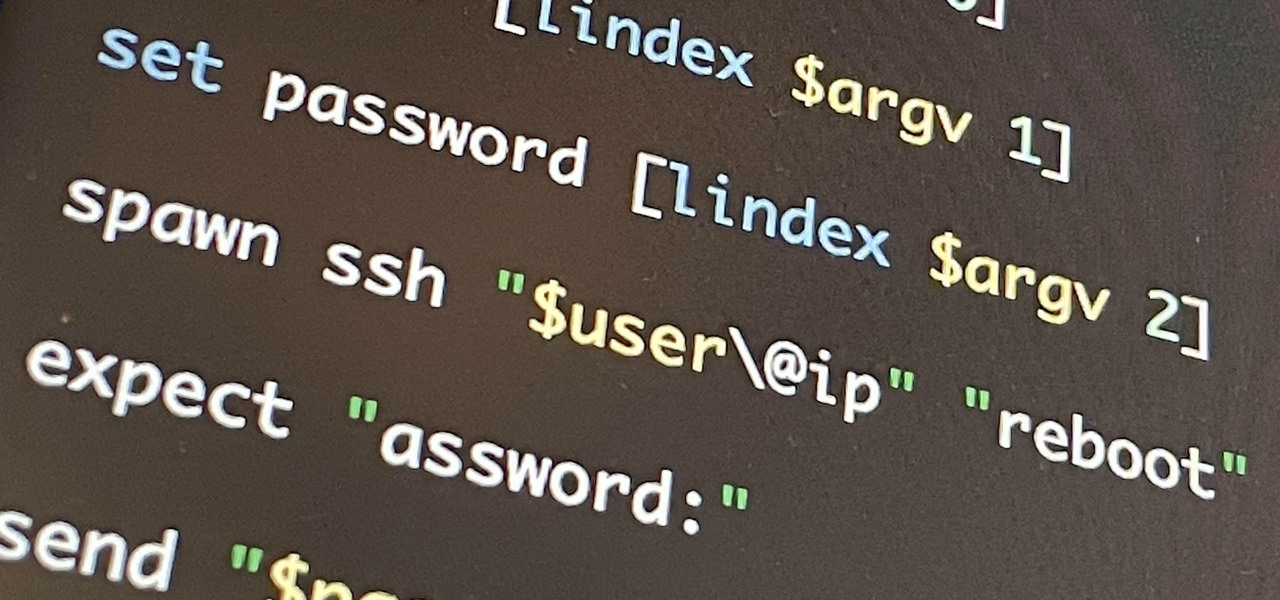
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate delivering an SSH payload with an "expect" script.

While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stellar call quality.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

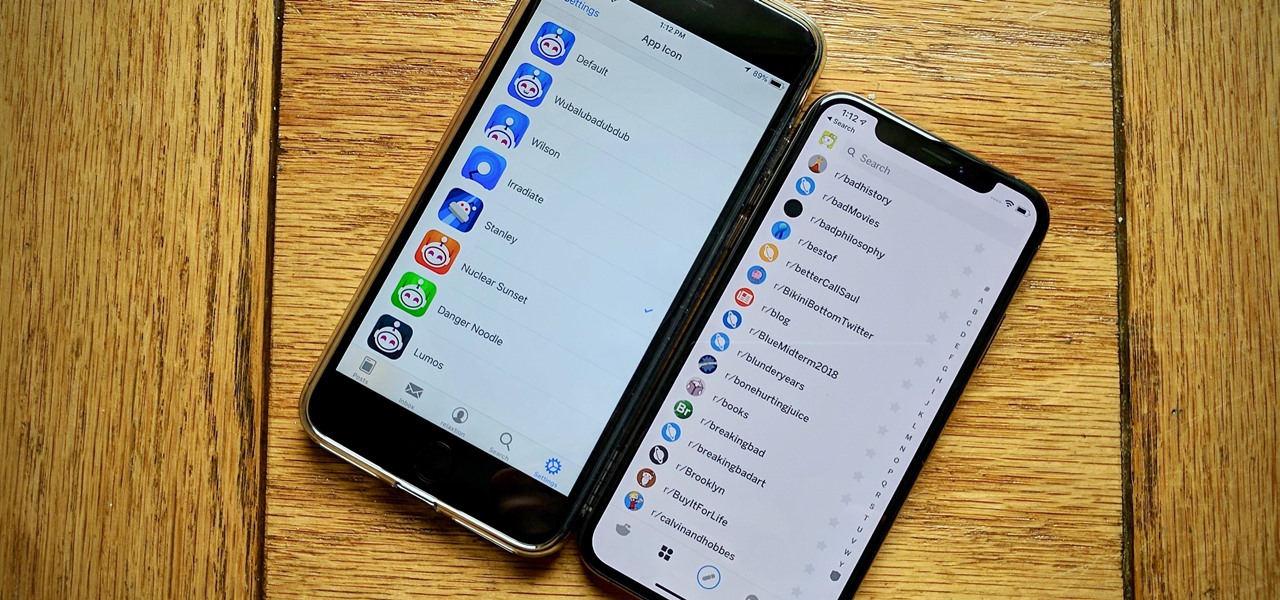
These days, using Reddit on your iPhone is just as good, if not better, than Redditing on a desktop browser. While there's an official Reddit app for iOS, there are plenty of third-party clients that have similar features as well as custom perks to enhance the experience. But figuring out which Reddit client is best for your daily use can be a lot of work — work that we can make easier on you.

This tutorial is for all fitted fanatics like me out there. I’ve been wearing fitted caps and snapbacks since I was in elementary school, and it has become a part of who I am. However, I also know that fitted caps and snapbacks are expensive, especially those from brand name companies such as New Era. That is why it is important to me to make sure that my hats remain wearable and stylish as long as possible. The following are some steps I take to make sure that my hats don’t become too dirty,...

What does one do with one hundred and one bottles of beer after taking them down and passing them around? Why, one gathers a couple of friends and plays Nikolai Andreyevich Rimsky-Korsakov's "Flight of the Bumblebee" on them, of course! As one commenter puts it, "The Greek system has been exonerated!"

The essential ingredient for this magical prank is RainX anti-fog car windshield spray. It's designed to repel the raindrops from a car's windshield.

A small group of students studying Game development at Stockholm University just released their first game.

Last week, I demonstrated how to go a little deeper into your Google+ profiles, photos, and introduced cross-posting. This week, I'm highlighting a bunch of different unofficial resources that have sprung up that will help improve your Google+ experience, and give you the latest updates on Google+ Photos.