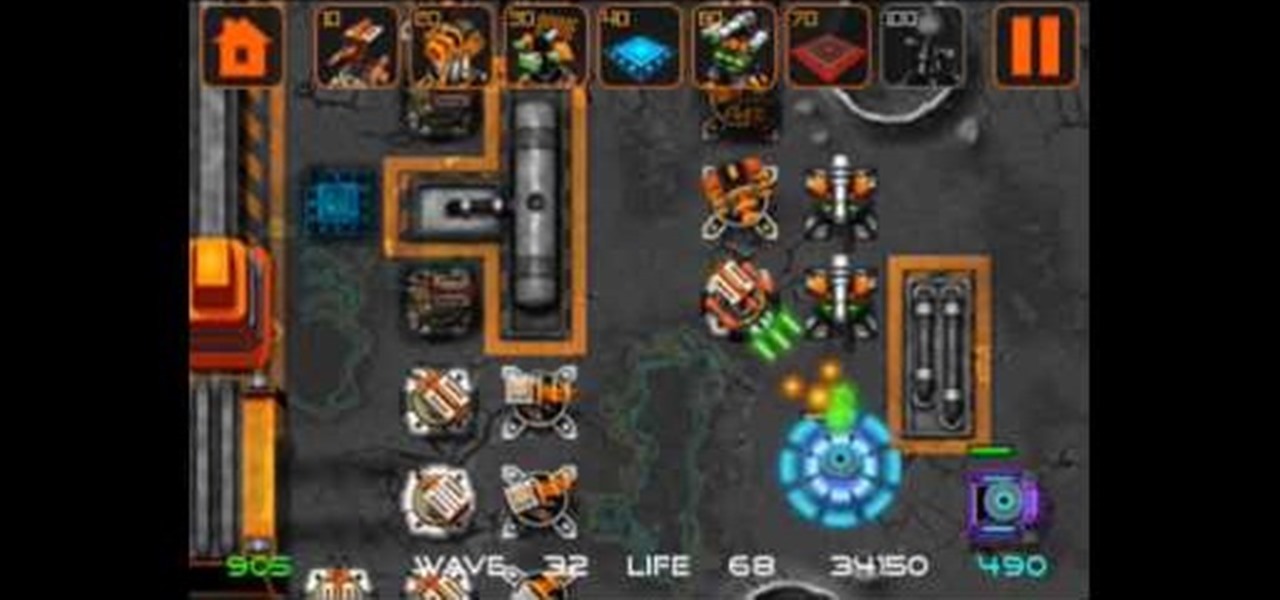
Need a new iPhone app? Check out Comets and Craters, a new iPhone tower defense strategy game. These ten video tutorials cover all of the gameplay troubles you may have. Steve explains the features and gameplay to help you get the most out of playing Comets and Craters on your Apple iPhone. For those more seasoned Tower Defense players, the video's also provide some insight regarding scoring, upgrades, plus Tower and Enemy capabilities.

Augmented reality allows for all kinds of experiences to happen just about anywhere, and that creates some incredible potential for entertainment. While games like Pokémon GO take you out into the world, one crowd-funded game wants to keep you inside—to scare the crap out of you in your own home.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

Guys, this has got to stop. It's not funny anymore. I'll defer to one of my all-time favorite people when it comes to my feelings on this unsavory subject:

This is a tale about microbes, a man who became a hermit, and the parchment that carries both of their stories.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the app where the story will be posted. Instead, you need a suite of apps that can turn your story into something special.

Alex Lewis imagines what the world would look like infiltrated by video game characters in his digital montage series “Video Games vs. Real Life”. (P.S. If you like what you see, check out Lewis' t-shirt designs at Threadless).

Digital distribution games are already firmly established on the PC, and they've infiltrated every present and next-gen console to some degree. Whether you like to play DOS, AAA, PC or indie games, there's a way to purchase most of them without leaving the comfort and warmth of your couch or desk.

Note: Little Brother is available as a free ebook download. Warnings

The agents of empire do not always arrive with warning. When you are besieged, surrounded, and infiltrated, imagination is often your best weapon against the oppressors. If all you have at hand is some duct tape and a disposable camera, fear not, you have the makings of a powerful taser!

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

















