To go Open Source or go proprietary? There is a common conception that open-source is unsafe and insecure and therefore companies should rather go for proprietary solutions. They think that because software is termed "open-source", that the world can see the vulnerabilities of the software and might exploit it, and less informed people tend to think that open-source software can be modified while it is running.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Learning all of the patterns of the pentatonic is important, but if you're stuck to just playing them in their box shaped patterns, you can really find yourself getting stale and insecure in your playing. So break out of the box with this video! Learn how to connect your pentatonic patterns up and down the neck with ease and add an extra breath of life to your improvisations!
In this video, you will learn the steps to take to enable JavaScript in Microsoft's Internet Explorer (IE) web browser. Although JavaScript support is typically enabled by default in most modern browsers and many web applications depend on JavaScript being enabled to function properly, some persons and organizations may occasionally disable JavaScript to negate the effects of annoying or insecure implementation of JavaScripts on some web pages (such as pop-ups, hidden tracking links, unwanted...

In this tutorial, we learn how to meet more women & blast away your insecurities forever. Although you may be insecure, you need to get past this and act like you are confident. Don't worry about being attractive and do things that feel right to you. When you stop caring about looking perfect, the girls will start to notice you more. Dress the way that you feel comfortable in and you will exude confidence to the women around you. Women like to be around guys that are confident and that can ta...

Learn how to play "Your Biggest Fan" by Nevershoutnever, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

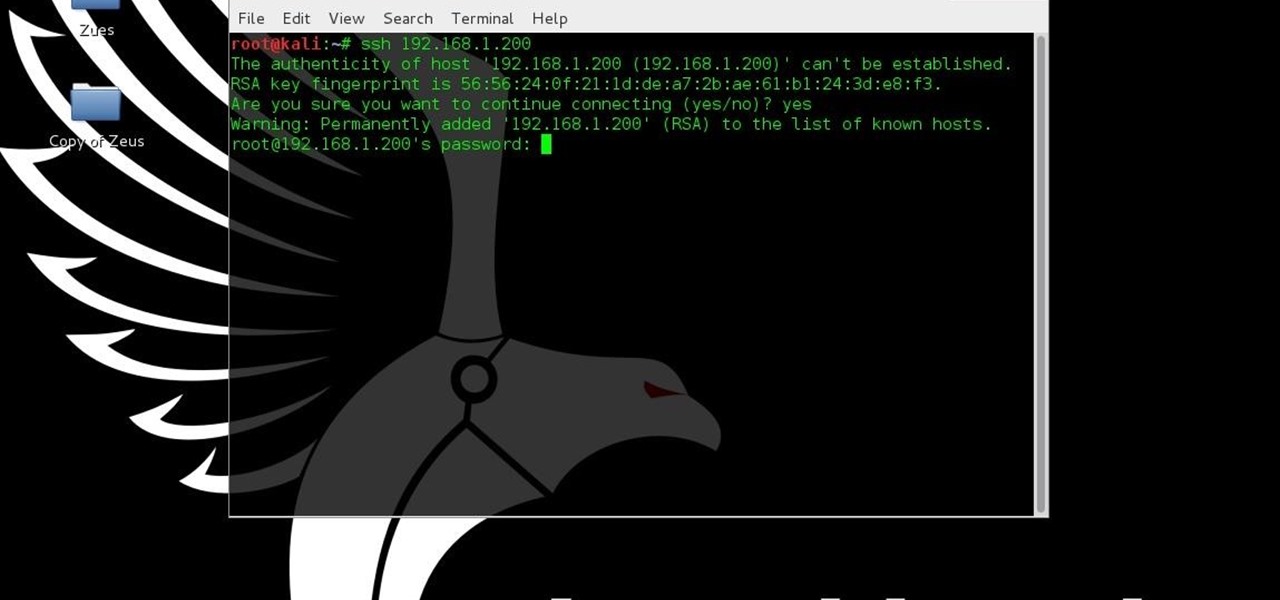
Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

Sony's Xperia Z, which has generated quite a deal of excitement since its launch at the CES in Las Vegas last month, is already sold out in France with its expected U.S. release to be sometime in March. It's 5-inch, 1080p display puts it up there with some of the best smartphones in the market. It runs on Jelly Bean 4.1.2 and comes with expandable storage. Also, the Z comes with an incredible 13MP rear camera with the capability to dish out 9MP photos at 14fps, shooting roughly 999 stills in ...

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Many people suffer from camera-shyness, or a reluctance to have their pictures taken. The reasons vary; some people are generally insecure about their appearance, others feel that their pictures don't match the way they want to be shown. Carson Kressley, from Queer Eye for the Straight Guy and How to Look Good Naked, offers the following advice: relax! Tight smiles, defensive body language, and insincere emotions can easily ruin a picture. Try to be spontaneous: if you want to smile, look at ...

No matter who you are, a little self-confidence can go a long way toward making your dreams come true.

Once you unlock your bootloader and root, you're left with one more hurdle to overcome, and that's getting S-Off.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

I am writing this to first pregnant moms. I am 25 weeks along and I have some advice as to getting through an uncomfortable pregnancy.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

If mainstream media has taught us anything, it's that being beautiful can get you ahead in life. The notion isn't necessarily correct, but it's what the general consensus accepts and it seems to hold quite a bit of weight (no pun intended) in the western world.

The Samsung Galaxy Tab 2 (7.0) 4G LTE on Verizon has only been released for a couple months now with good reviews. It comes with dual cameras, memory expansion, and very quick 4G LTE speeds, without needing a contract. While most users are satisfied with the tablet as is, there are others that prefer rooting the tablet in order to install their own custom ROM. Now you can do it with the Samsung Galaxy Tab 2.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

To quote MKBHD, cheap phones are getting good. Each year we are seeing manufacturers start to offer more for much less. This not only translates to cheaper flagship phones, but better budget phones. The latest example of this is the Alcatel 3V, which is redefining what you can get at $150.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Preserving battery life has become one of the biggest problems for the average user. Whether you're on Android or iPhone, your battery is probably a massive concern. While there are a ton of battery-saving tips out there, they mainly rely on you manually performing actions yourself. This isn't the case if you use IFTTT to take care of your battery automatically.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.