In this tutorial, we learn how to properly fit a blazer or suit jacket. First, try the blazer on and make sure it is not too baggy or too tight. You want the buttons to be able to close and you want the sleeves to be long enough to reach your wrists. If you need to get it altered to be shorter, mark where it should be, then bring it to a tailor to get altered. You wan to make sure the inside lining of the jacket is sewed on properly and that the shoulders are not too pointy or high. Once you ...

Build a fire with a Duraflame firestarter. This video is going to show you how to do this. Crystal Whole from Duraflame is demonstrating the process in this video. First get your chimney cleaned and inspected. Keep all inflammable material at least 3 feet away from the hearth. Use dry wood that has been seasoned for at least six months. Or you can use stax logs in lieu of wood. Three stax logs are sufficient to keep the fire burning all evening. Open the flue of the chimney, put two stax logs...

In this tutorial, we learn how to check the brake pads on a 2008 Kawasaki Ninja 250. First, check the thickness of the brake pads on the car to see if they are thick enough. The rear pad is surrounded by a gold piece called the "shoe" and the rotor. The front pad has to be inspected by laying on your back and looking for the pad to see how thick it is. If the thickness is not enough, you need to replace it as soon as possible. Make sure the brake pads are up to the standards of the owner's ma...

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Six people have died from fungal infections in Pittsburgh hospitals since 2014—that fact is indisputable. The rest of the situation is much vaguer. A lawsuit has been filed against the hospitals on behalf of some of the deceased patients, alleging that moldy hospital linens are to blame. While the lawyers argue over who's at fault, let's look at how this could have happened.
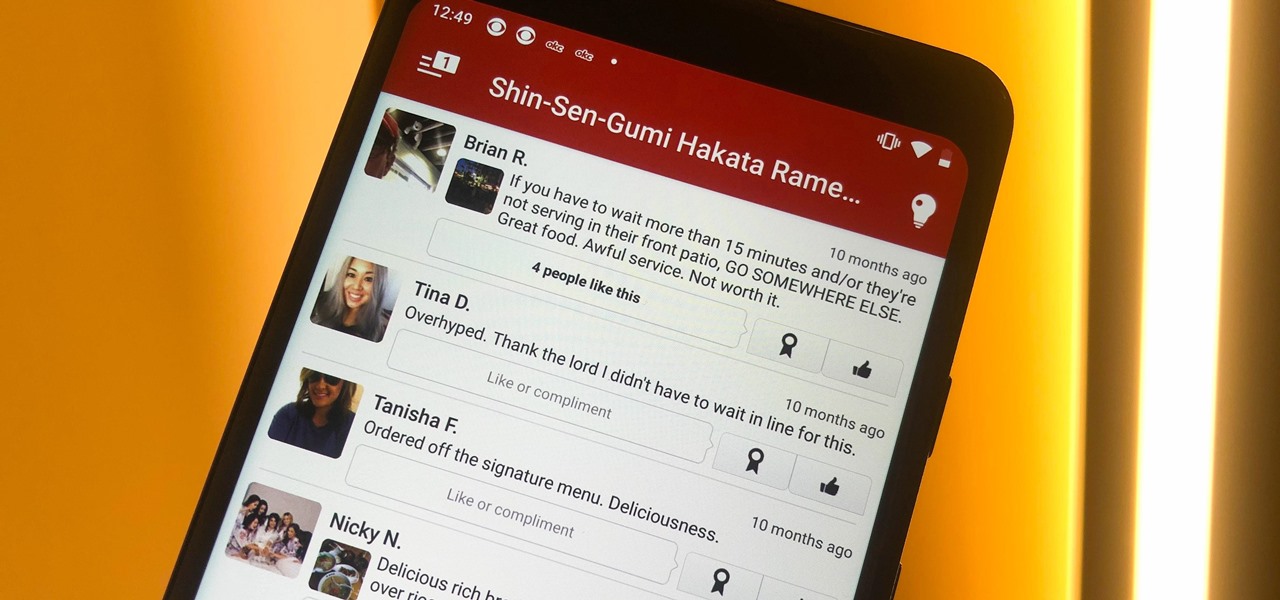
Yelp reviews are great for getting a feel for how a business operates, but they can't always be trusted, and they don't always get to the point fast enough. That's where "Tips" come in, and you can view and make them whether you're on an iPhone or Android phone.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Citrus greening disease — caused by a bacteria spread by psyllid insects — is threatening to wipe out Florida's citrus crop. Researchers have identified a small protein found in a second bacteria living in the insects that helps bacteria causing citrus greening disease survive and spread. They believe the discovery could result in a spray that could potentially help save the trees from the bacterial invasion.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Introduction So, today and yesterday I was playing with TNT (as we all do at one point or another) and was curious about a few things. From this curiosity, I went onto discover some of the science behind some things you may or may not have known.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Make sure your next apartment rental goes smoothly by properly checking the property before signing a contract. This way you will avoid unexpected disappointments or problems that you were not aware off. Moving is hard enough, give yourself all the advantage you can by going in prepared.
Soon, Americans may find every private email they write could be opened, copied and inspected by government snoopers. The latest cyber security bill – called CISPA – has passed the House of Representatives, coming a step closer to becoming law. President Barack Obama has threatened to veto the act, if it goes through in the Senate. He cited civil liberty concerns as the reason for his threat. CISPA has raised a massive outcry with internet users and freedom activists, who say it’s a hard hit ...

Announcement #1: Holiday season is here! Every Wizard101 account that logs in between December 21, 2010 and January 1, 2011 will receive a silent nightcap, which is different for both boys and girls! Merry Christmas and a Happy New Year!
International Pet Travel: Taking Your Pet Animal to a Foreign Country If you are taking a pet to another country (permanently or for a visit), contact that country's consulate or embassy for information about any requirements that you must meet. A list of consulates can be found at Foreign Consular Offices in the United States