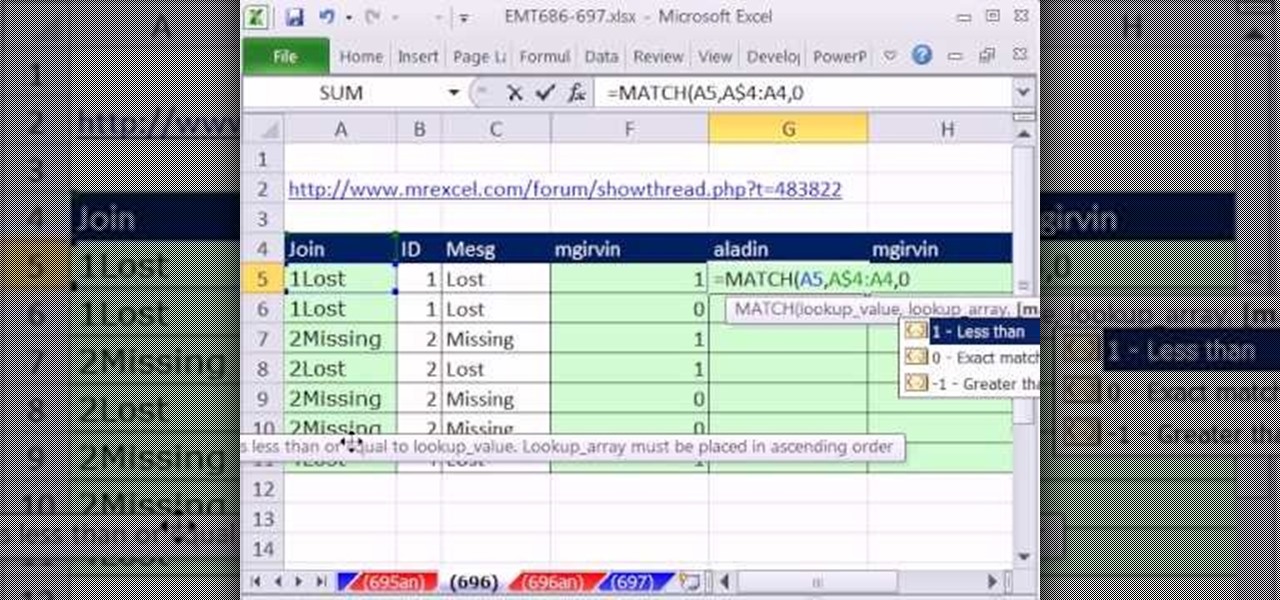
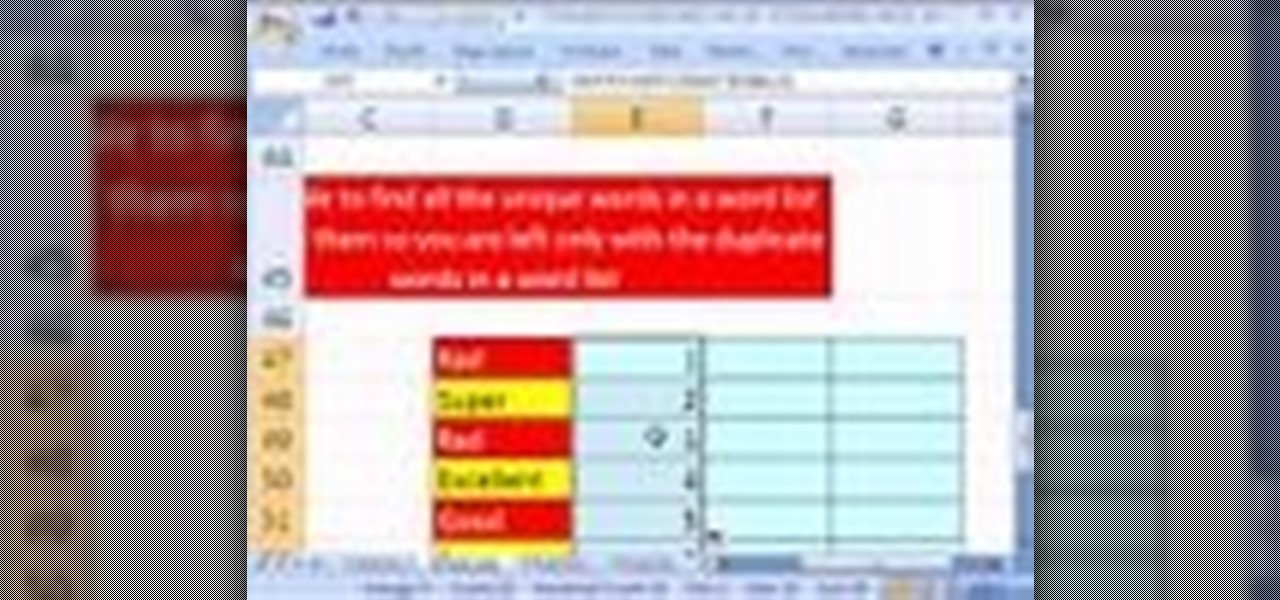
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 697th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a column of 1s and 0s (ones and zeroes) where 1 indicates the first occurrence and 0 indicates any remaining duplicates.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.
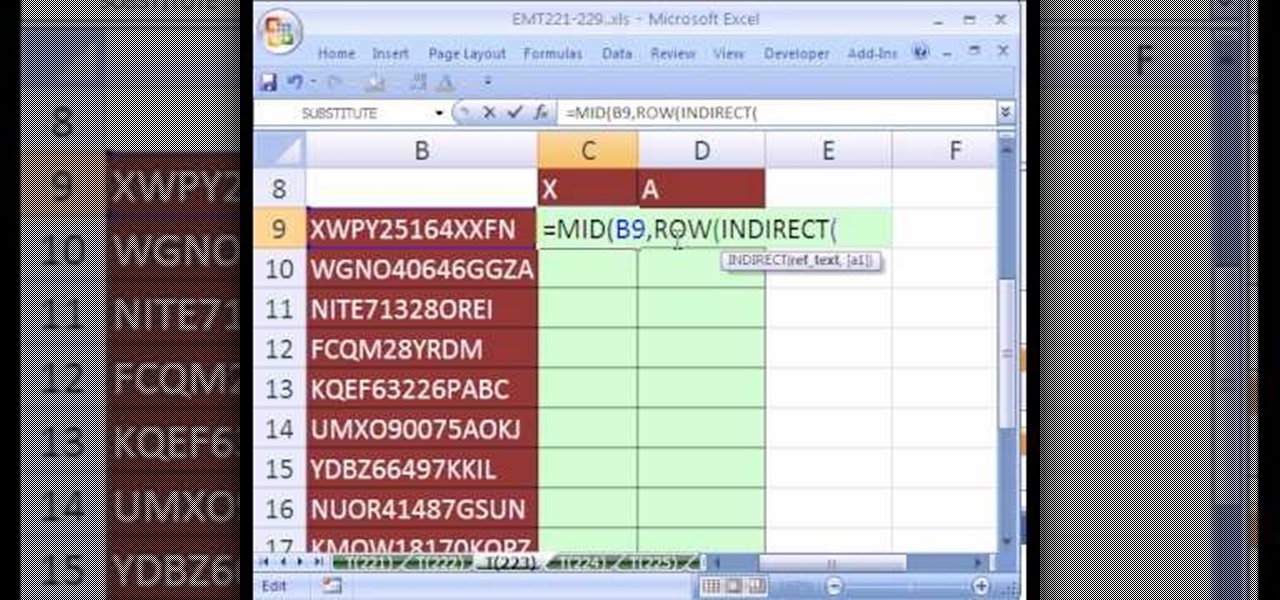
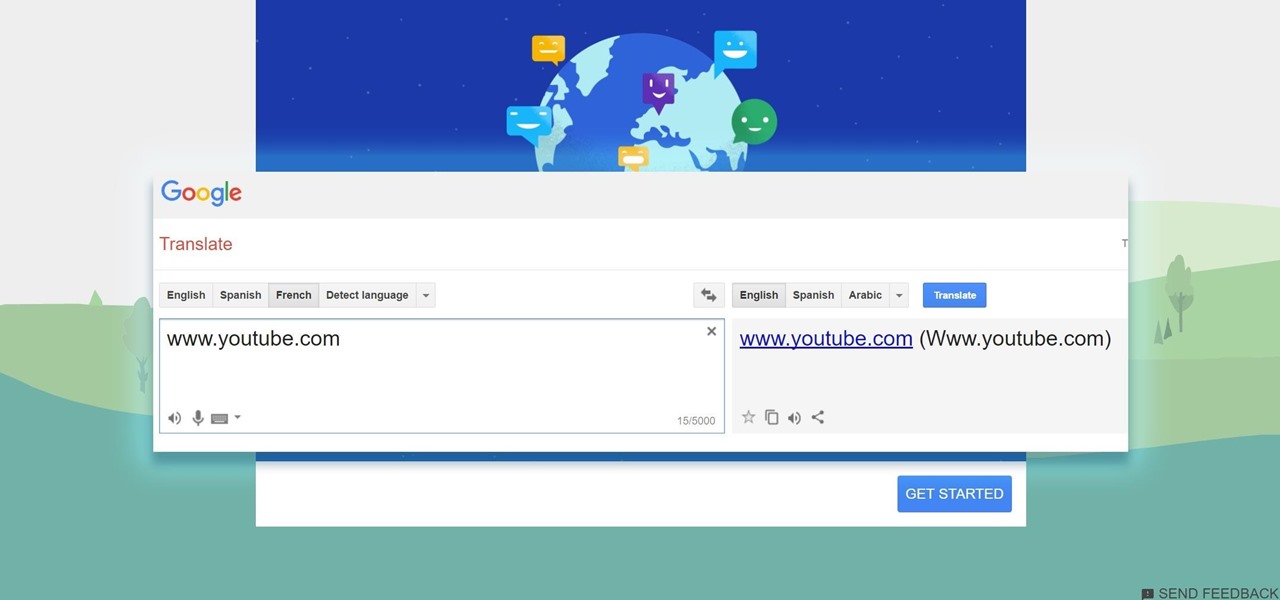
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 223rd installment in their series of digital spreadsheet magic tricks, you'll learn how to count individual letters in a word. See how to count the occurrence of a given character in a text string.
This video will show you how to use the ‘find’ and ‘replace’ text buttons in Microsoft Word 2007. Microsoft Word 7 is slightly different from the Microsoft you might be used to but with these instruction you’ll have no problem finding the buttons.
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 32nd installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to use the MATCH & ROW functions to create a logical test to find the first occurrence of items in a list with duplicates.. Learn to love digital spreadsheets more perfectly with the tricks outlined in this free Microsoft Office how-to.
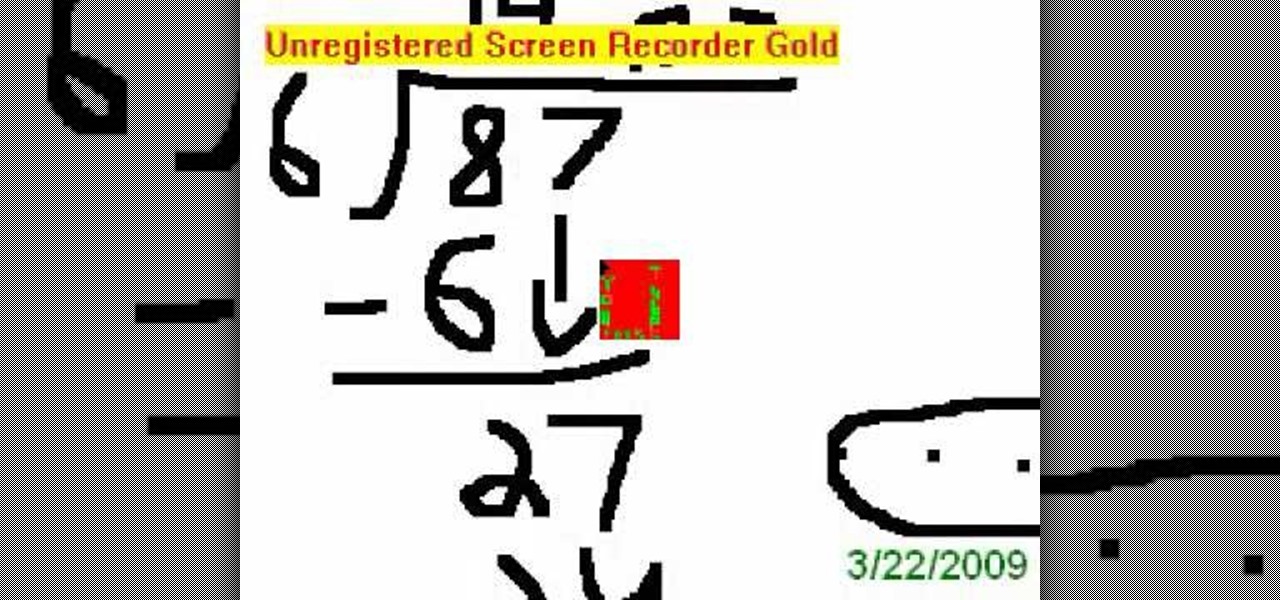
This video goes through the step by step process of doing long division with remainders. Multiple examples are used throughout the video to give the viewer a better idea of how to properly complete the difficult task. Perfect for anyone learning long division for the first time, or for anyone attempting to relearn long division after forgetting how to do the process (an all to common occurrence in a world with calculators on every cell phone).

The drum support rollers are usually in the same spot on every dryer, no matter the brand. They will be below the drum. In order to remove the rollers, you need to open the dryer's cabinet and remove the drum. Perhaps you will notice that the left roller is more worn out than the right one. This is a common occurrence, but you need to replace both at the same time. Be sure to remove the nut before you remove the roller. Don't use more than one drop of oil on the hub as too much oil will aid t...

While intestinal gas is a normal occurrence within the digestive process, it can also cause bloating, burping and flatulence. Follow these tips to remedy the problem.

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.

As summer heats up, new maps from the Centers for Disease Control and Prevention (CDC) gives us our best guess at where Zika-carrying mosquitoes could be hanging out this year in the US.

Although it is a rare and potentially frightening occurrence, knowing how to do a system restore in Windows XP is an important thing to know how to do. To get started with a system restore, select the Start menu in the lower right of your screen. Then select All Programs. Then from the All Program menu, select Accessories and then from Accessories, select System Tools. There are several items under System Tools, but you want to select System Restore. You will follow through the next few scree...

In this tutorial the author shows how to find out a Cool XP Easter Egg hidden in the XP which comes by downloading the latest update of widows update. The author now opens Internet Explorer and visits the windows site. Now he quits the explorer and holds down both the Control key and alt key and right clicks on the desktop seven times. Now keeping the control key pressed, he releases the alt key and right clicks the desktop and chooses the option 'Create ShortCut'. Now he releases all the key...

While the concepts of molecule interaction, zero force and energy states might be a little beyond an elementary school science fair's scope, the basic idea of water's capabilities and naturally prepared access to animals and insects that rely on it as a habitat is certainly worth the time. Learn how to duplicate this natural phenomenon in this free video clip series with our expert Scott Thompson as he demonstrates the occurrence of water skin or skin tension, and shows you and your children ...

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

Since its release into the arms of waiting developers, Apple's new ARKit is already making waves in the augmented reality scene. Only a week out and there are already a hefty number of videos appearing on the web showing off various demos with iPhones and iPads.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Need to break out of the restrictions your school or workplace have on internet browsing? Maybe you want to waste some time on YouTube, check out some gaming action on Twitch, or simply just browse Facebook or Twitter.

When you hear people say that Android is more flexible than iOS, it's because of things like Tasker. You can do virtually anything with the venerable automation tool, from saving battery life to controlling your smart home with your fingerprint. But before you get to that, you'll need a good understanding of all the basics.

When attending networking events, a LinkedIn exchange is a common occurrence. Equally common is the awkward fumbling dance with how to add each other. Fortunately, we have the solution: the ultimate way to add LinkedIn contacts.

Despite the relatively small size of Magic Leap's first annual L.E.A.P. conference, there was a lot to see and experience. Apparently missed by many was one of the best experiences I had at the event: Wingnut AR's unreleased Pest Control game.

Any living creature will die if deprived of sleep for long enough. The longest documented occurrence of a person not fully sleeping and surviving is only 11 days. There is a rare disease where deep sleep is never achieved, affecting roughly 100 people worldwide. Patients usually only survive between 6 to 18 months after the onset of chronic insomnia, and only 3 to 9 months in a parasomnia state without any real REM sleep.

A lot of people have problems with their cats urinating inside the house, leaving behind the retched odor of cat pee. Others get frustrated when feral or stray cats pee on their porch, patio, or anywhere else outside of their house, as it's not the most welcoming odor when guests arrive.

After a brief reprieve, Zika fear is back with a vengeance as the US mosquito population booms. And we're just now seeing the true impact of this devastating virus, as babies of mothers infected with the virus are being born.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

The first thing you'll always have to do before getting your customization game on with most phones is to unlock the bootloader. Doing so opens the true potential of the device, allowing you to root, install TWRP, Magisk, custom ROMs, and other mods. No matter your wants or needs, there's no way around it — the bootloader must be unlocked to modify the system.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

Bacteria, viruses and other germs sometimes set off the immune system to overreact, producing a severe condition called sepsis. Sepsis is so dangerous that it is the leading cause of death of children across the world, killing a million kids every year, mostly in developing countries. Probiotic bacteria might be able to prevent sepsis and infections, but no large research studies have been done to find out whether that actually works. Until now.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

The Massachusetts Department of Public Health (DPH) issued a health alert for a Boston mumps outbreak, on Monday, June 5th, to healthcare providers and local boards of health. There have been 12 reported cases of mumps during the recent outbreak. The affected residents' symptoms occurred between March 24th and May 31st, and 10 of the 12 had symptoms after May 9th. There have been 35 confirmed cases of mumps in 2017 in Massachusetts, and "nearly 300" suspected cases in the continuing outbreak.

The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a compromised immune system.

For many of us, pets are important family members. They give us loyalty, companionship, and comfort. Now, researchers have given us another reason to welcome them into the family: Babies from families with furry pets — the majority of which were dogs — had higher levels of two types of beneficial gut bacteria.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Over 6,500 waterfowl—mostly ducks—have died in Canyon County, Idaho, stricken by avian cholera. The outbreak started in February, and before it's over, it may not only be Idaho's largest outbreak, but one of the largest in the country.

Ecosystem changes caused by agricultural choices in Brazil are creating a dangerous microbe mix in exploding populations of vampire bats and feral pigs.

The pathogen referred to as a "nightmare bacteria" is quietly adapting and spreading faster than anticipated.

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.