No need to figure out the 20th puzzle, entitled "The Origin of the Species", in Assassin's Creed 2. Here's the answers! Puzzle wheel: Start by turning the fifth ring right ten times, then turn the fourth ring left twice. Then rotate the third (and first) rings right twice, the second ring right five times and the first ring left three times. Image 1: Highlight the eye at the top of the painting. Code wheel puzzle: Ignore the numbers and focus on the Assassin motto: “Nothing is true, everythin...

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.
For those unwilling to wait until the Fall for the official release of Apple's latest Mac OS X, El Capitan, you can sign up for the public beta today and get it sometime this summer. If that's still not soon enough for you, there is a way to get it on your Mac right now.

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Editor's Note: The claims by Vani Hari which were originally detailed in the article below about azodicarbonamide were unscientific in nature. This article has been updated to reflect that and provide more scientific context on the issue.

The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

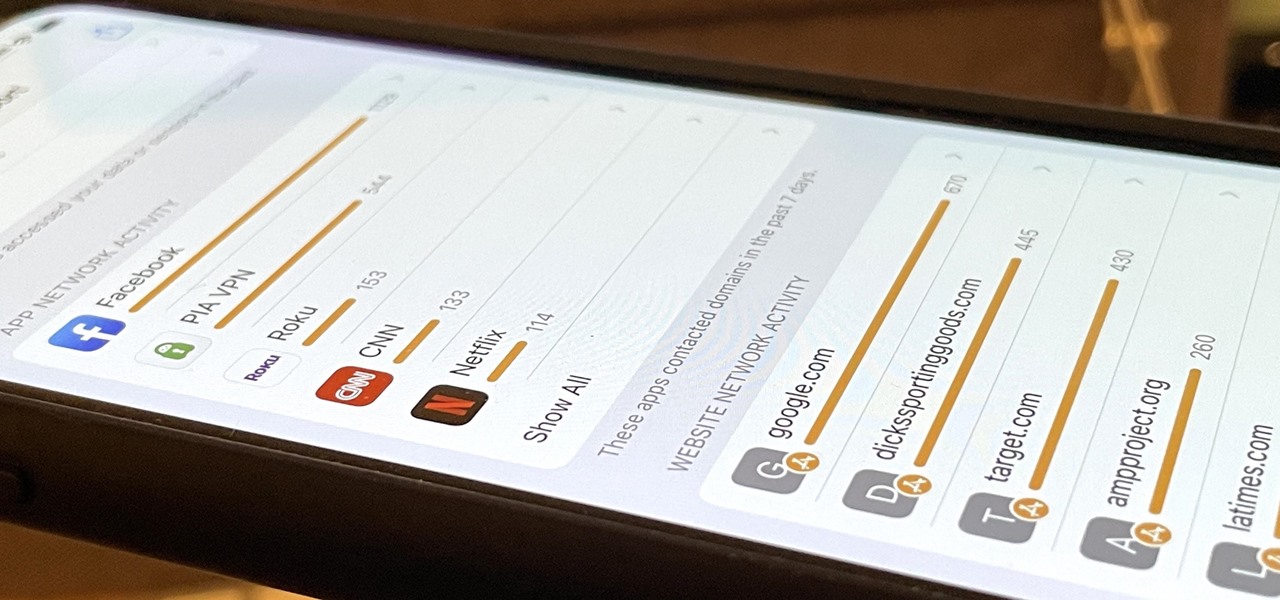
Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

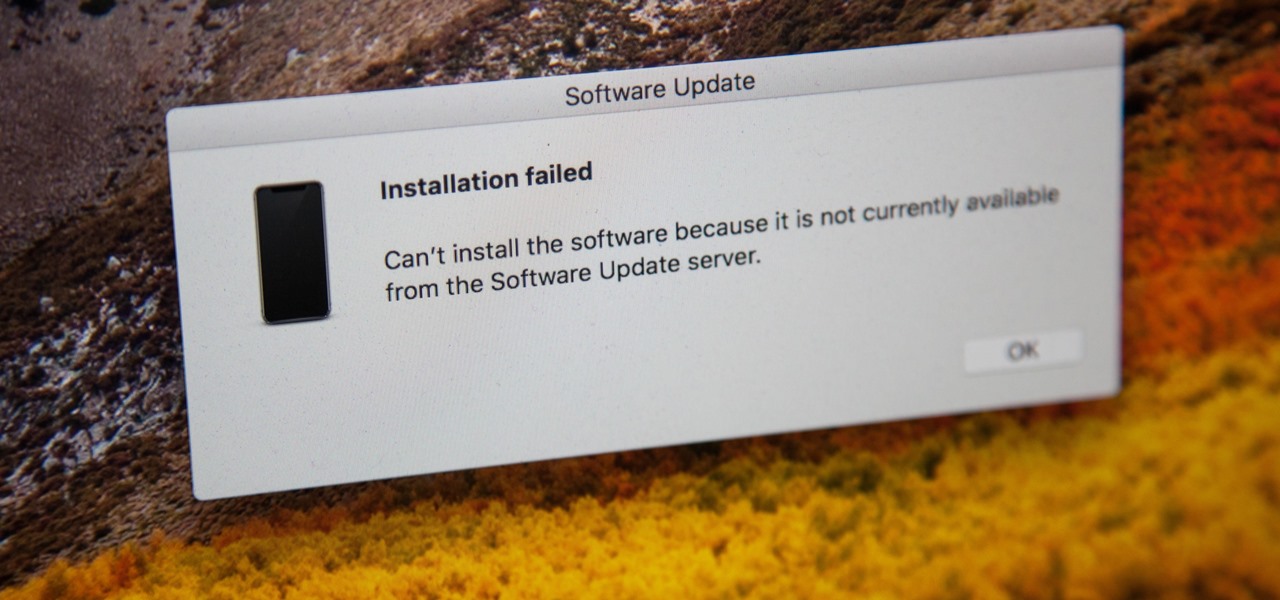
If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

One of the most significant changes in iOS 14 is something we've wanted for a very long time, and it will change the way you use your iPhone. Since the very first iPhone OS 1 (yes, before it was even "iOS"), we've been stuck with Apple Mail as the default emailing app. That all changes now.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Taking a cue from Apple and its Health app for iOS, Google has created a central hub to collect health and fitness data on your Android device. With it, you can share and sync health and fitness data, such as steps, heart rate, water intake, sleep quality, and calories burned, between different apps and devices and use your favorite app to view all the information.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

With the holidays right around the corner, it's easy to miss a big software update on your iPhone, and by that, I mean iOS 15.2, which was pushed out Monday, Dec. 13. There's a surprising amount of new features and changes in the updated firmware, and there are a few big ones you need to know about.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

Successfully Complete Your CNA Training Program You must finish your CNA (Certified Nurses Assistant) training program and must secure a CNA training certification in order for you to be qualified to apply for CNA state exam.

Before you start snapping away and submitting your photos, please take some time to read the official rules below!

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.
International Pet Travel: Taking Your Pet Animal to a Foreign Country If you are taking a pet to another country (permanently or for a visit), contact that country's consulate or embassy for information about any requirements that you must meet. A list of consulates can be found at Foreign Consular Offices in the United States

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

It's once again Monday, which means it's time to highlight some of the most recent community submissions posted to the Math Craft corkboard. Since two of these posts were on polyhedral versions of M.C. Escher's tessellations, I thought we'd take a look at building a simple tessellated cube based off of imitations of his imagery.

You've seen his explanation of a combination lock's inner workings. You'll never lose another game of Jenga, thanks to his winning wooden pistol. And nearly 4 million YouTube users have marveled at his wooden marble machine sculpture. He's Matthias Wandel, and he's accomplished what most only dream of—turning a hobby into a career. Matthias has been tinkering in woodworking since he was a child, with unrestricted access to his father's workshop, permitted to use power tools unsupervised from ...

Do you do last minute cramming before you go to the dentist? No, I don't mean reading up on orthodontia in hopes of having an intellectual conversation about crowns with your dentist (how you can talk at all with all those tools in your mouth is beyond me, though dentists always ridiculously try).

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

Photoshop. It’s like a mountain to climb. You can chug up to the top, working hard, never letting up, or you can just go part way up and scoot around the side of the mountain and still get to the other side. Not everyone needs to be a Photoshop guru, or ninja pixel punisher. There are a few things to know and be comfortable with in order to do lots of cool things. Here are some tips that will take you a little way up the mountain, somewhat in order of altitude.

My JO was watching The Simpsons on FOX the other day, like she wholeheartedly does every evening, and I joined her, much like I always do— though I must admit, I'm not as obsessed with the cartoon family as much as she is. Just like she isn't as obsessed with SCRABBLE as I am.

The game has undergone many transitions over the years, since its days as LEXIKO (1931) to its briefness as CRISS CROSS WORDS to its current and amalgamated, renowned brand of SCRABBLE. There has been many editions of the word board game along that historic metamorphosis, and SCRABBLE has even given in to pop culture, sports memorabilia, and fanaticism.