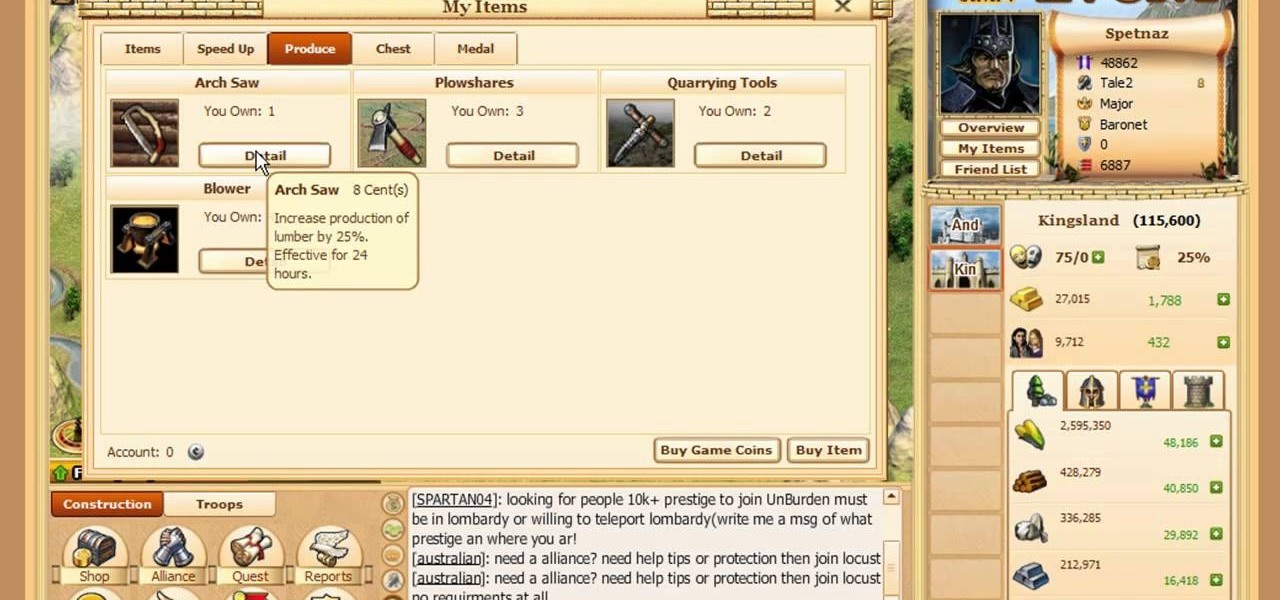
It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

After SquareTrade tested out the Samsung Galaxy S8 and found it to be the first phone to shatter on all sides after only one drop, it's nice to know we may have a solution for this $500 problem.

Even though HIV rates declined 18% between 2008 and 2014, 1.1 million people in the US are living with the infection. Part of that is because HIV is treatable, but not curable.

Rust protection doesn't have to cost a fortune. With a little zinc and some electricity, you can protect your precious metals from rust by galvanization. When you galvanize something, you're giving it a protective coating, and in this case, it's a zinc coating.

Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play Evony: Resource millionaire and beginner's protection. See exactly what the game Evony is!

In this clip, you'll learn how to unlock NAND and install a recovery menu on a rooted HTC Evo 4G. Whether you're the proud owner of an HTC Evo 4G Google Android smartphone or are merely considering picking one up, you're sure to be well served by this video tutorial. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

Have you ever wanted to transfer iTunes-purchased songs from your iTunes player into a different media player? Usually it's difficult to do because DRM music protection makes all of its songs .m4p files, whereas most music players only play mp3 files.

Learn how to wrap a textblock in this video tutorial. Wrapping the block allows you to protect the book's inner pages while you are working on the outside of the book. All you need to do is use some butcher paper, or any other kind of heavy duty paper you may have on hand. Lay the spine flush against one side of the paper. Open the front cover and fold the bottom sides into the book. Tape these ends together. Then, with the excess paper on the non-spine portion of the book, fold those ends in...

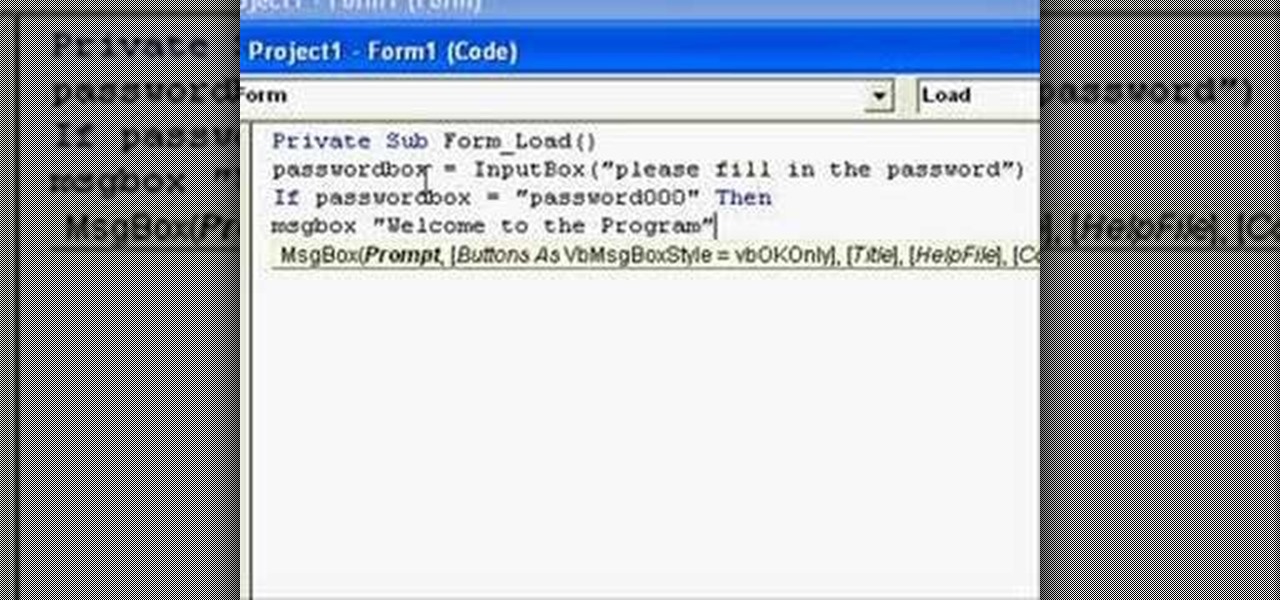
In this clip, you'll learn how to implement password protection in a VB 6 application. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Visual Basic programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

See how to enable Layer 7 DoS and brute-force protection within DoS within BIG-IP ASM. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

The free version of DVD Fab allows you not only to rip DVD's to your computer, but it also removes any regional or right protection from the DVD as it's ripping. Then you can use VLC to play back the DVD's.

A short tutorial on How to enable hotlink protection on cPanel. This video is provided to you by Scandicsoft.

In this tutorial, we learn how to get free virus protection with Avira. To do this, first go to Free AV, and download the software. After you install everything, open the program up. Next, you will want to scan your computer for any viruses that may be present already. It may take a while to scan your entire computer, but it will search all of your different files. If something comes up, you can choose how to deal with it and get rid of the virus if you wish. This is also great for any emails...

In this how to video, you will learn how to remove 3M paint protection film, also known as a clear bra. This is used for protecting the front of a vehicle. To remove it, you will need to use a heat gun on the film so that it will peel off. This takes a while to remove, so be patient. The film itself is very useful, as it protects from rock chips and bugs while driving. Note that it is a lot easier to take off during the summer time since the car exterior is already hot. You should not worry a...

In this video tutorial, viewers learn how to repair the write protect on an SD card. An SD card is a non-volatile memory card format that is used in portable devices. If the write protect on a SD card is broken, the user cannot record any files onto the card. To fix this, viewers will need a small piece of scotch tape. Put the tape on the notch of the SD card. Do not cover the metal tabs at the back. This video will benefit those viewers who have a SD card and would like to repair the write p...

This Spirituality video clip will show you how to wrap a Wiccan cinnamon stick bundle for protection. You need some cinnamon sticks, scissors and ribbon. Cut a very long piece of ribbon, lay it down on a table, place the cinnamon sticks on the ribbon, tie a basic knot flip it over and tie another knot. With one end of the ribbon, go over and in between the sticks and with the other end, go under and in between the sticks. Now put one more knot in between the sticks. One more time go under or ...

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll learn how to get started using Symantec's Endpoint Protection Small Business Edition on your Microsoft Windows PC. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

Gutter protection comes in many different forms for your home, and to find the best gutter guard, Ask the Builder host, Tim Carter, prepares to test several different models on his house.

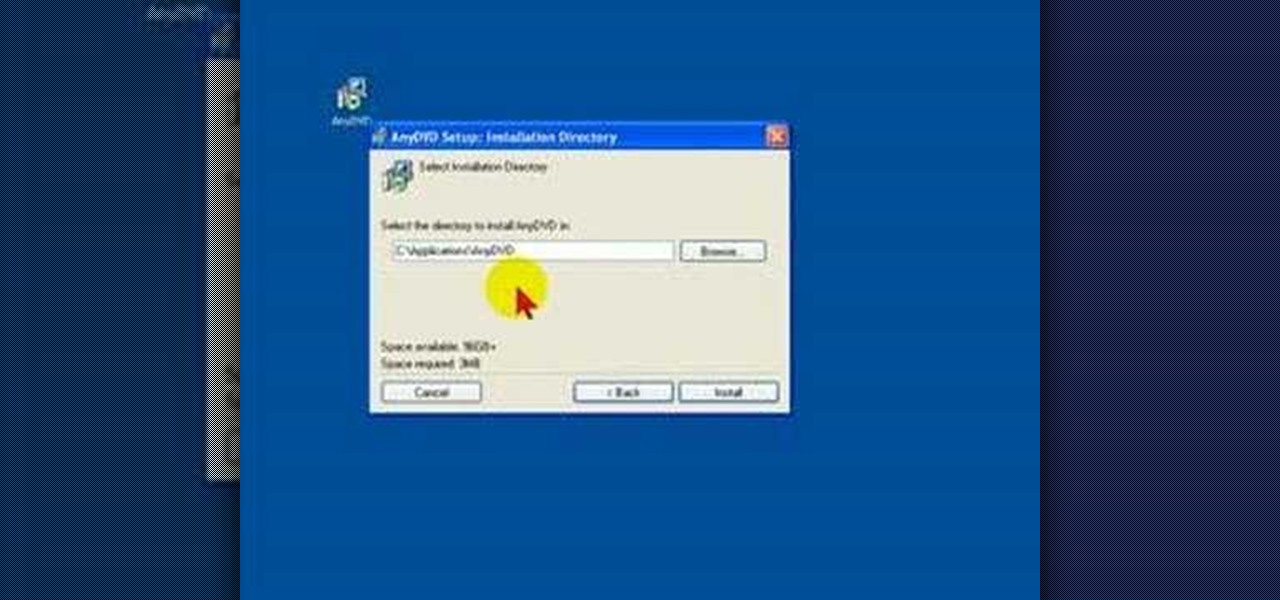
Slysoft AnyDVD is a program that you can install on your PC to bypass the copy protection, and in this screencast tutorial, we show you how to install and configure it correctly.

Helpful tips on how best to use a game camera for property protection.

Spyware can cause all sorts of problems for your computer. It sneaks its way onto your computer and then does its damage. You can remove spyware from AOL 9 by double clicking AOL spyware protection on your desktop. If you don't have that, you can search for spyware. Once you open the spyware protection, it will allow you to scan for spyware and display it on the screen so you can choose which software you want to block. This video will benefit those viewers who use AOL and would like to learn...

In this video tutorial, viewers learn how to set and encrypt the wireless password using WEP Apple Airport. Begin by opening the Apple Airport utility program. Then find the network's name and double-click on it. The Configure "Apple Airport Express" opens, click on the Airport tab. Then click on the Wireless Security button. Now click on the Wireless Security drop-down menu and select 128-bit. Click on the Set WEP Password button, type in the password and verify it. Finish by clicking on Upd...

In this video tutorial, viewers learn how to set and encrypt your Wi-Fi password using WPA on a Linskys router. Begin by opening your web browser and type in the address: Click Enter. Now type in your user name and password, and click OK. Then click on the Wireless tab and select Wireless Security. In the Security Mode drop-down menu, select WPA Pre-Shared Key and then type in a password under WPA Shared Key. Finish by clicking on Save Changes. This video will benefit th...

In this Computers & Programming video tutorial you will learn how to encrypt a D-Link router with WEP password protection. First you connect to your wireless network. Open your browser and type in http://192.168.0.1. Type in your base station username and password and press OK. Under the SETUP tab, select WIRELESS SETTINGS, scroll down to 'Wireless Security Mode' and select 'Enable WEP Wireless Security'. Scroll down to WEP. Under WEP Encryption pull down menu select 128Bit. Now create a pass...

In this video tutorial, viewers learn how to set and encrypt a NET-Gear router with WEP password protection. Begin by opening your web browser and go to the router website: Router Login.. When the Prompt window appears, type in your router user name and password, and click OK. In the sidebar, under Setup, click on Wireless Settings. Once again, type in your user name and password, and click OK. In the Security Options, check WEP (Wired Equivalent Privacy). Then select the Pass-phrase box, typ...

In this video tutorial, viewers learn how to set and encrypt their Wi-Fi password using WPA in Apple Airport. Begin by opening the Airport Admin Utility application from the CD. Then locate your the name of your network and double-click it or press the Configure button at the bottom right of the screen. Now enter your password and click OK. The network should be opened now. Then click on the Airport tab and click on Wireless Security. In the pull-down menu, select WPA2 Personal. Then click on...

In this tutorial, we learn how to set and encrypt a Wi-Fi password using WPA in Netgear. First, type "www.routerlogin.net" into your internet browser. Next, a pop-up window will appear, type your user name and password into this dialog box. A new window will pop up, click on the tab on the left hand side of the screen that says "wireless settings". Type in your user name and password once more, then find where it says "security settings", and click on the "WPA-PSK" radio button. Now, make a p...

Watch this video to learn how to encrypt Wi-Fi using WEP password on Linksys in 4 simple steps. Connect to your wireless network. Open your Web browser and type in the web address http://192.168.1.1. Press enter key. Type in the User Name for your network. Type in the Password, press OK button. Select the Wireless text tab, select the Wireless Security text item. Pull down and select the WEP menu item. Type in a good password. Click the Generate button. Click the Save Settings button. Encrypt...

What type of protection does Doug have in this scene from The Brady Bunch Movie?

Zero chance of your ride being jacked with this level of protection. You will need: a 100,000 volt tesla coil strapped to the roof of your vehicle. Created by tesla master, Peter Terren. Previously, Electrifying Transparent Tesla Coil (DIY!!)

A Self-Protection Guide 1) You can help protect yourself from violent crimes.

Hi again, Just wanted to share a neat little code that I found way back, when I was presented with a spreadsheet which was locked and asked to ''unlock'' it or do whatever it takes to enable the user to edit it's contents.

What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.