In this DIY fashion video, learn how to take an old fitted tshirt and add some flare! Add a sexy front-laced up section to your shirt to create a faux boddess. Spice up your closet for cheap with help from this clothing reconstruction video.

In this video, we learn how to reconstruct a t-shirt into an off the shoulder top. First, take a large shirt of your choice color and cut along the line on the shoulder, leaving a 1/4" seam allowance. Next, roll the hem and sew with a sewing machine. Next, cut a strap 4" wide and fold in half, then sew along the edge. After this, use a safety pin to pin one side to the shirt and then to the other side of the shirt. After these are secure, draw marks along the neck line of the shirt. Cut out t...

This week, the thread heads show us how to turn an old Jimi Hendrix t-shirt into an even cooler button-down shirt. Sweetness!

No money for a new dress? No problem! If you can afford a cheap pack of Hanes tee's from your local drugstore, then you can afford this look! And if you are on an even tighter budget, you can sneak into your boyfriend or brother's bedroom and "borrow" his!

Revamp your old tees with help this four-part tutorial! Take your older tees and reconstruct them to fit your style! In this video, learn different styles and tricks & tips to mold your old oversized tshirts into a new fashion piece!

Learn how to recycle and reconstruct your denim jeans: Craft side Look, Learn and Create with Stefanie Girard and Jean Therapy with Scathe G. Allison demonstrate how to recycle and reconstruct your denim jeans. You can make a bag out of your jeans by using the leg as the strap. Customize jeans by adding patches to the legs and ruffles to the bottom. All the projects use simple sewing machines and stitches and don't require extra tools. A skirt can also be made by sewing together 14 pairs of d...

This video shows us the method to reconstruct your t-shirt with a fringe design. You will need a long fitted t-shirt, scissors and a sewing machine which is optional. Cut off both sleeves of the t-shirt. Now cut the middle of the shirt on only one side. Cut off the collar. Hem both sides of the cut so that you have a clean finish. Now take the scissors and start cutting the fringes. Open the t-shirt so that all the fringes are even. Mark the length of the strips and start cutting. Once you ha...

This video fashion design lesson offers another great tip for recontructing a t-shirt. Revamping old pieces in your wardrobe is a sustainable and economical way to stay fashionable! Winter is so last season. Spring here we come....This week Threadbanger meets up with the Sistahs of Harlem for a long overdue T-shirt recon.

A cool t-shirt reconstruction lesson sent in to us by one of the loyal viewers of Thread Heads.

Iraq war reconstruction: $6 billion to $8 billion wasted, US official says - Open Channel. The official in charge of monitoring America’s $51 billion effort to reconstruct Iraq has estimated that $6 billion to $8 billion of that amount was lost to waste, fraud and abuse.

It's tough to figure out what a mummy would have looked like when he was alive; soft tissue of a human body decays, even in ice. But, Dutch brothers Adrie and Alfons Kennis took the challenge. Using techniques that belong to both science and art, they managed to reconstruct the face and body of Otzi the Iceman, a mummy who was found in the Italian Alps in 1991.

Want to add a few new pieces to your closet for summer but don't have the cash? Look no further than your "clothes junk drawer". Recycle your old oversized tshirt and reconstruct it into a sexy racerback tank top with help from this DIY fashion tutorial. Get the look you want for zero!

In this how-to video, you will learn how to maintain your recorder instrument. First, label your recorder with a permanent marker in case you leave it somewhere. This will allow someone to identify who it belongs to. First, use the cleaning rod and put a piece of cotton cloth on it. Push it through the opening of the recorder to get any spit and dirty out of the recorder. To clean the mouth piece, use an old tooth brush and scrub it. Once in a while, it is a good idea to wash the recorder in ...

Not sure what to do with all those oversized "night shirts"? Well, think twice before you throw them out. In this tutorial, learn how to reconstruct your oversized tees into a sexy rocker fitted halter top that ties in the back, quickly and with ease. This is a great way to add a couple new rockin' pieces to your closet by recyling your old t-shirts and not spending a dime!

Rob and Corinne invade the American Sewing Expo in Novi, Michigan and get a sweet tutorial for making a hoodie from the new winners of the Threadbanger/Janome Sewing Machine in this how-to video. About five minutes into this video, get together a t-shirt and a flannel; that's all you need to recycle some old clothes into a hoody. Watch this video fashion tutorial and learn how to reconstruct an old t-shirt and flannel into a new hoodie.

In this tutorial, learn how to reconstruct a men's dress shirt and make it into a cute mini dress! Recycle his old t-shirts and put them to some good use with help from these step-by-step instructions. With a little sewing knowledge and a couple hours of your time, you'll have a brand new dress to show off by the weekend!

We all have old tshirts lying around our house. Why spend the big bucks when you can reconstruct & recycle what you already have? In this DIY fashion tutorial, learn how to turn an old oversized t-shirt into a sexy cropped tank top! Perfect for summer!

Revamp an old t-shirt into a stylish halter top shape. This is an easy project, and with these tough economic times, you should probably be saving that money instead of going shopping. Check out this video fashion tutorial and learn how to reconstruct a t-shirt without any sewing.

You can take an old, stainless steel refrigerator and turn it into a vertical smoker. Weld steel plates to make a fire box with a door and a removable ash tray, then reconstruct the frame to make yourself a new addition to your barbecue pit!

In this how to video, you will learn how to liquify an image using Photoshop. First, open the image in Photoshop. Next, go to filter and select liquify. Use the forward warp tool to press pieces of the photo. Use the reconstruct tool to bring the image back to the original state. The twirl clockwise tool can be used to twirl pieces in the photo. You can adjust the pressure to twirl more. The pucker tool can be used to push sections into the image. The bloat tool can be used to pinch sections ...

Reconstruct your T-shirts into more stylish attire with this video! The materials you'll need are a T-shirt, scissors, a ruler, and a pen or pencil. First cut off part of the sleeves (this part is optional.) The next thing is to cut the neck all the away around the front and back, cutting off the border. Now it's time to cut the bottom of the shirt right under the hem, underneath the stitching. Keep what you've cut to use for the ties for the shirt. (You can also use string or ribbon.) Measur...

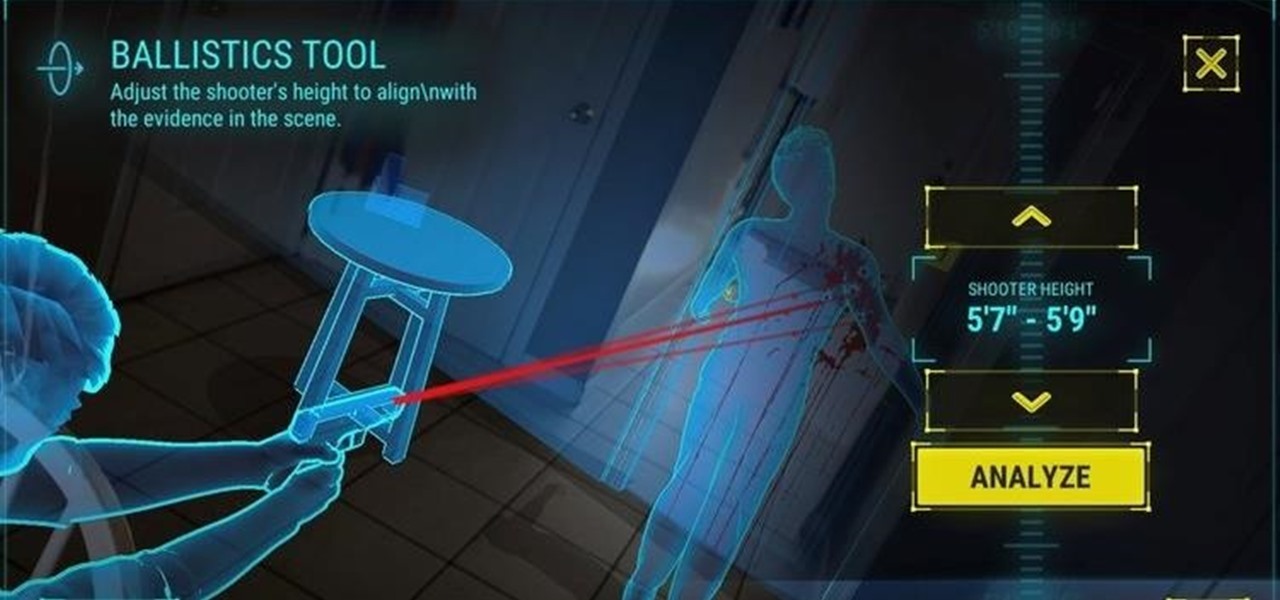
The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

Last week, I tried out StackAR, a puzzle app updated to support ARKit where the AR features felt mostly unnecessary.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

The evolution of our infection-fighting systems may have something to teach modern scientists. That's what a group from the University of Granada in Spain found when they studied a protein that's been around for over four billion years. Their work, by senior author José Sánchez-Ruiz and colleagues in the Department of Physical Chemistry, was published in the journal Cell Reports.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

With the release of Object Capture this fall, Apple is giving everyone with a Mac and a camera the means to create their own 3D objects.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Lidar, a technology first used by meteorologists and aerospace engineers and then adopted in self-driving vehicles, has slowly crept into consumer electronics over the last five years. If you have a Pro model iPhone or iPad, there's a good chance it has a lidar sensor, and you're likely using it whether you know it or not.

Inspired by the vast and exotic geography of Iceland, Canadian-Hungarian artist Eszter Burghardt uses food and wool to reconstruct her memory of the landscape. The series, "Edible Vistas and Wooly Sagas", is molded from "poppy seeds, coco powder, coffee, milk, and chocolate cake crumbs" and Icelandic wool—there are endless herds of native sheep wandering the countryside. She then captured the dioramas with a macro lens.

If you're not familiar with the animations of Jan Švankmajer, you're in for quite a trip. The Czech artist and filmmaker is known for his metaphorical, captivatingly surreal stop-motion and claymation films, and is God to many (including talents such as Tim Burton, Terry Gilliam and the Brothers Quay).

You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down the Internet? Could they even do it?