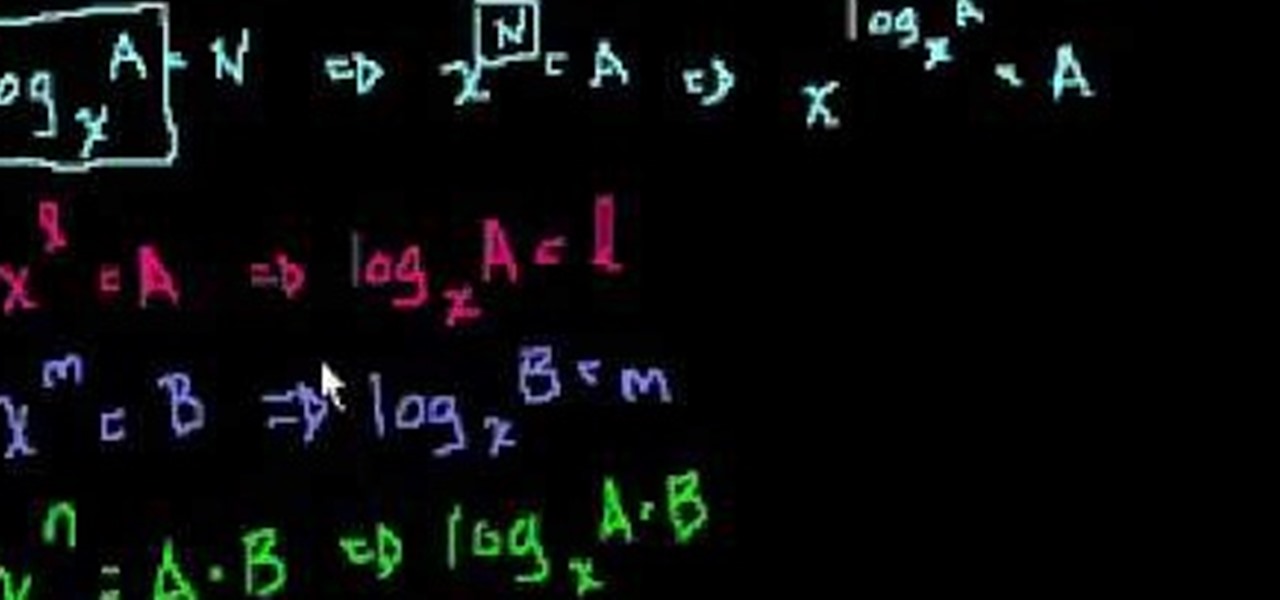Just a quick post. Xorg is the graphical server that handles the desktop environment you choose for your Linux box. A pretty big flaw was found in Xorg versions 1.11 and later that allows anyone to bypass the screen lock mechanism on xscreensaver, gscreensaver, and many others.
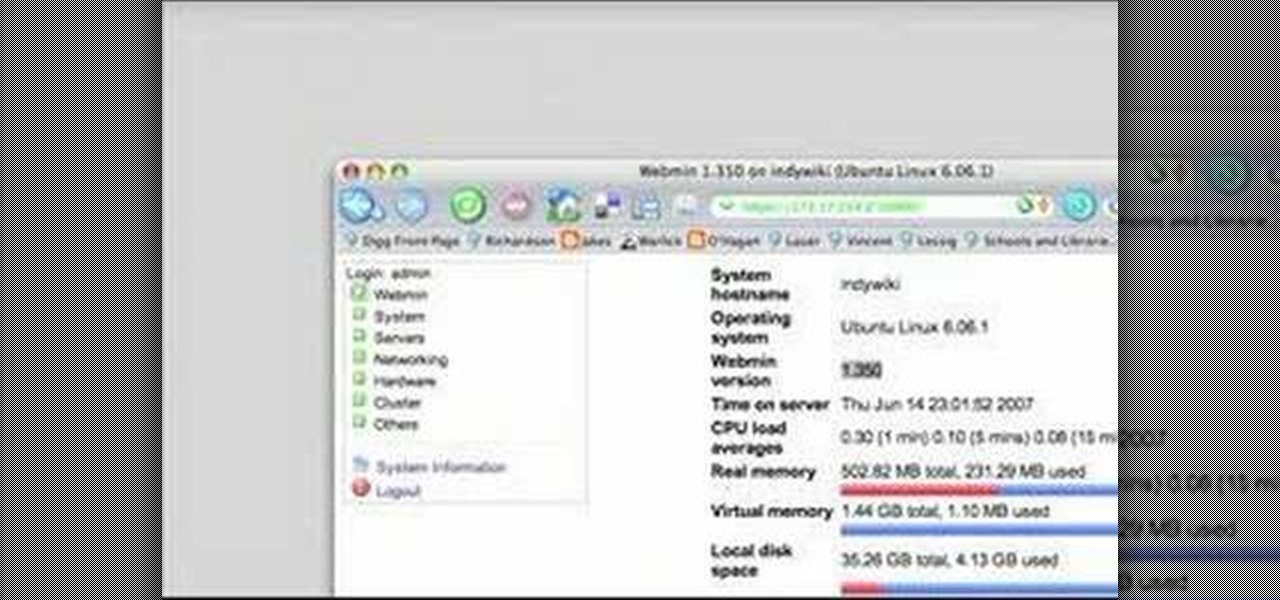
In this video you'll learn how to log in to Webmin, a web-based Unix administration interface, which will allow you to manage your serve with a web browser. Watch this video tutorial to learn how to control your server with a web browser and the Webmin interface.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?
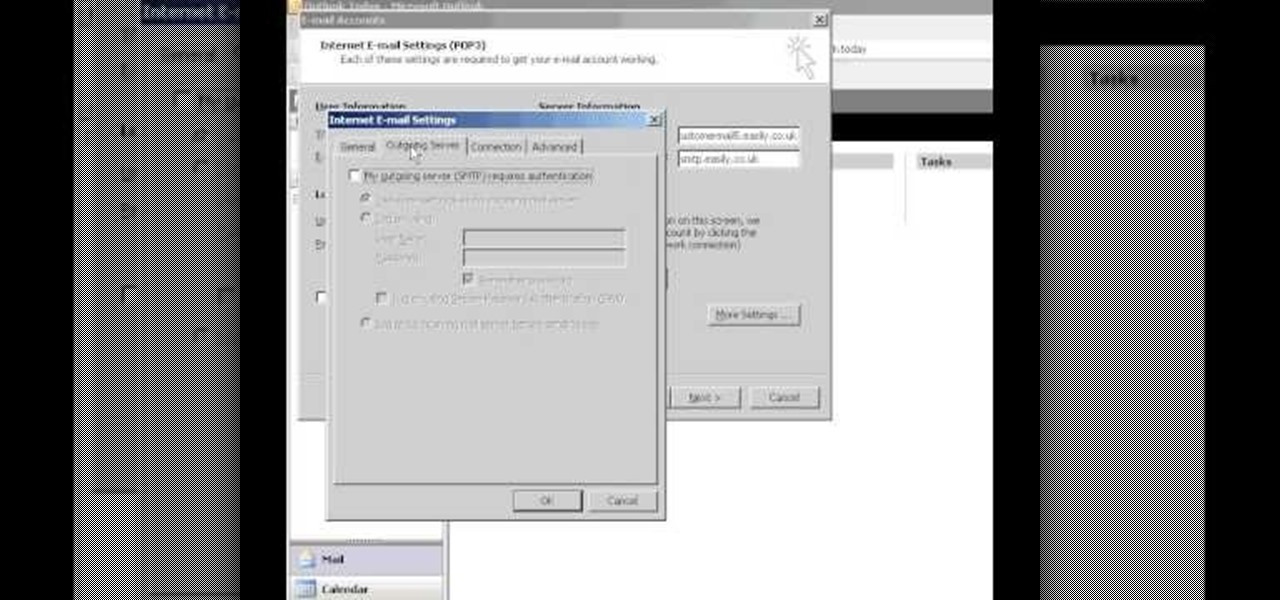
Easilycouk shows viewers how to set up an email account using MS Outlook. First, you should open up MS Outlook. Go to Tools and go to Email Accounts. Choose the option to add a new one. Click next and click the POP 3 option. Click next and Fill in your information such as name, the email address you are using and choose your log on information. Now, you need to fill in your Server information by copying and pasting your email into this. In the SMTP type smtp.easily. Go to internet email setti...

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

This tutorial shows you a few good tips on how you can manage your multiplayer Minecraft game. There's a special focus on how you can mine for diamonds and other rare commodities when you've logged on to a multiplayer server.

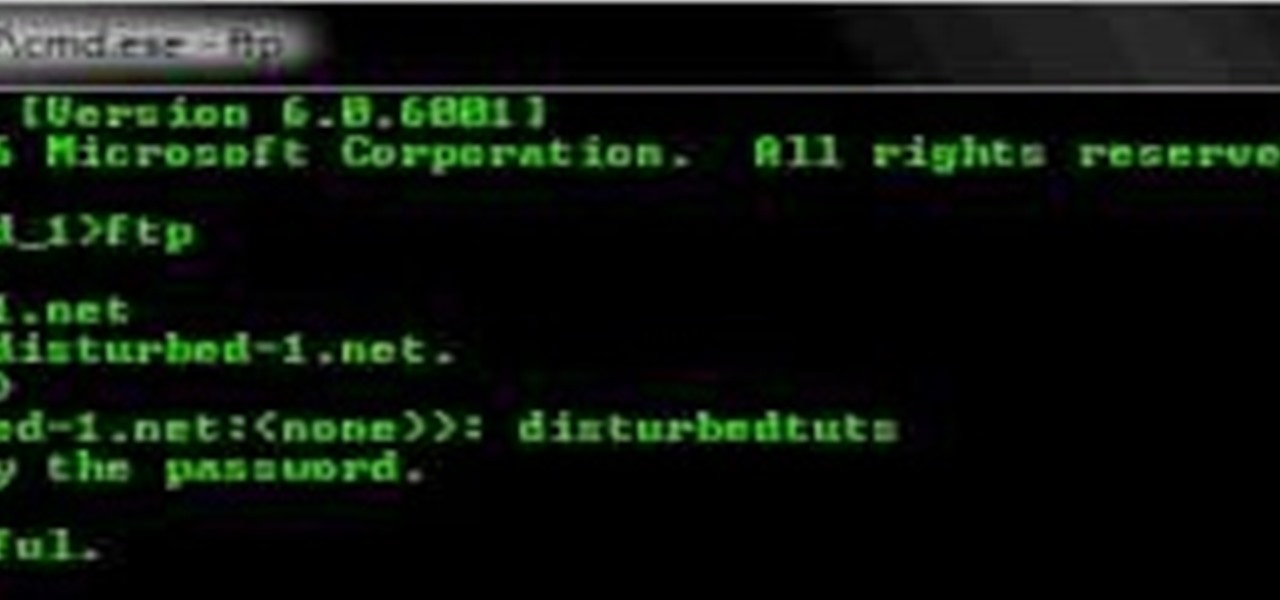
You can connect to an SSH server or connect to an FTP server from you windows computer. Open the run dialogue in your windows and type in cmd. Press OK to open the command prompt. Type in ftp command and press enter. This brings up the ftp prompt. Type o to connect to a server. Next type in the server name you want to connect to. Now you will need the authentication credentials to connect to the server. First enter the user name and then the password. Up on successful log in it shows the same...

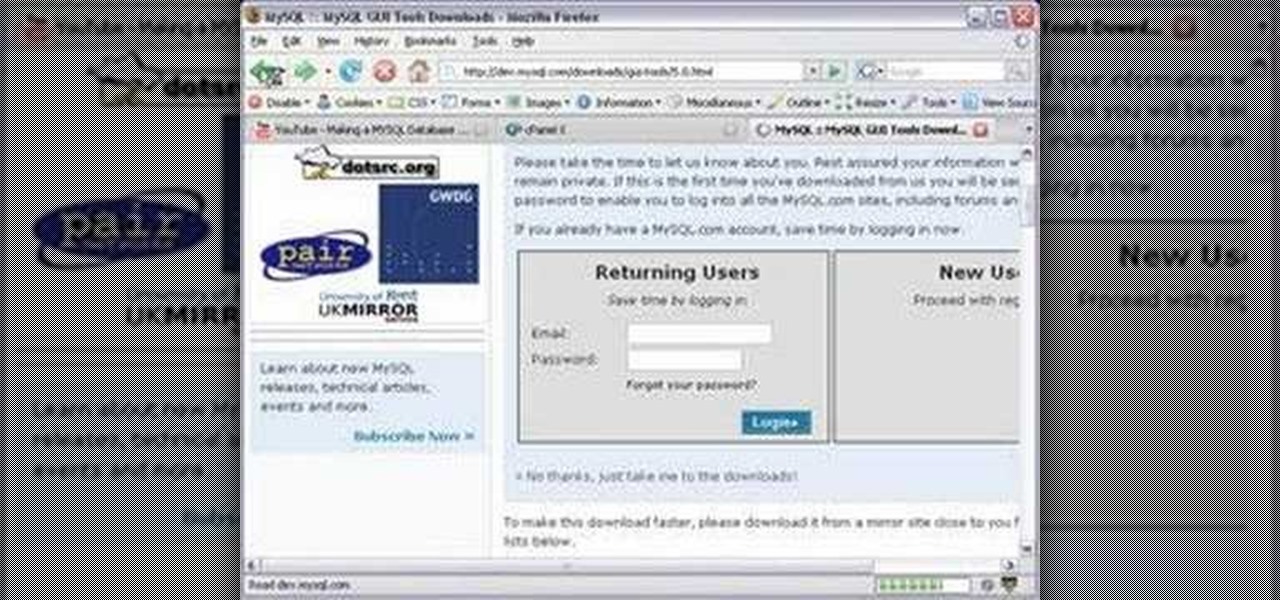
In this tutorial we show you where to download MySQL Query Browser and how to access and edit your databases. MySQL Query Browser is an easy way to access database information remotely from your desktop without having to log in to your server. Learn where to get MySQL Query Browser, and how to use it to access and edit your databases.

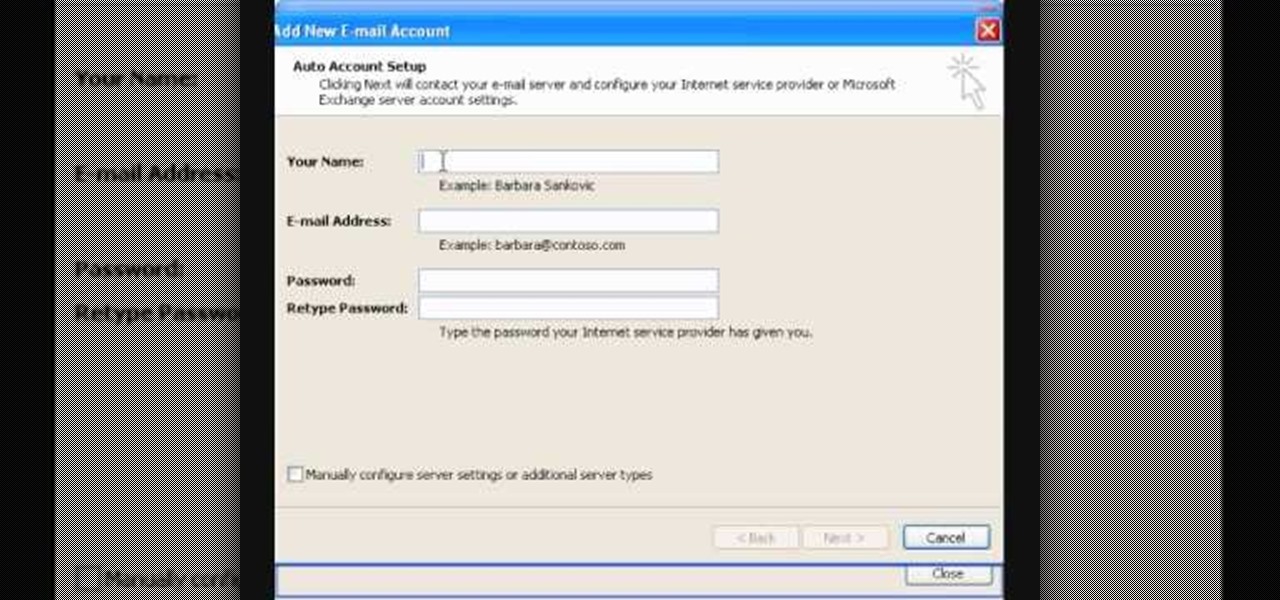
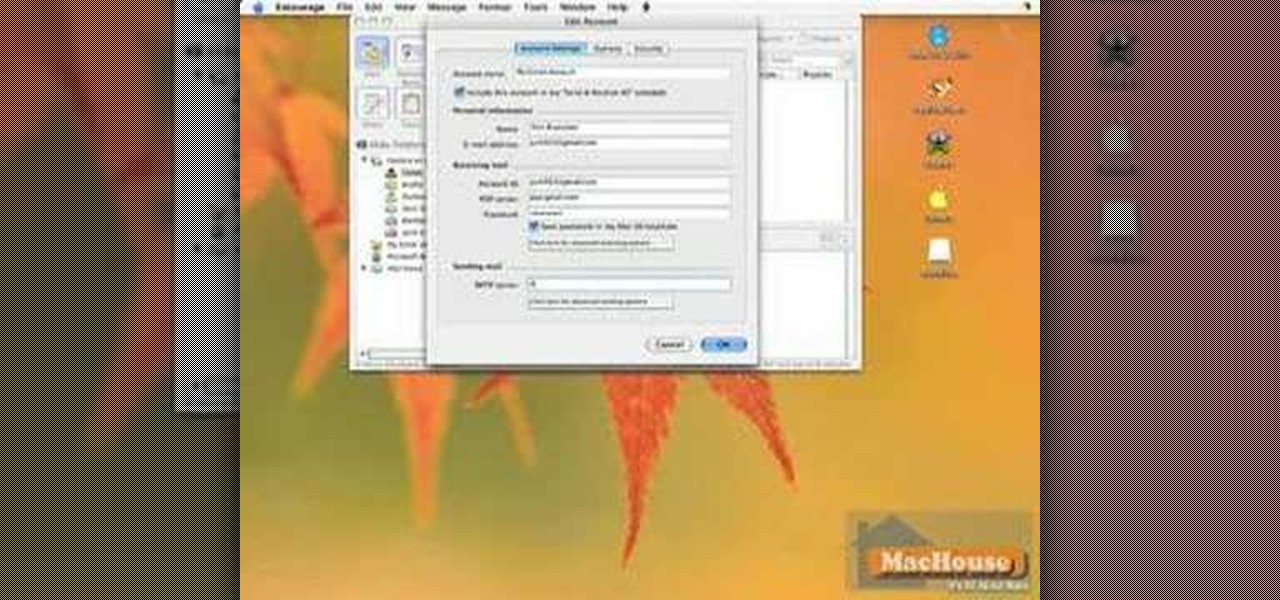
In this video tutorial, viewers learn how to setup Microsoft Outlook 2007. Begin by opening the Outlook Express 2007 program. Then click on Tools and select Account Settings. Under the Email tab, click on New. Now type in your name, email address and password. Then click on Next. Select Internet Email and click on Next. Now type in your user information, server information and log on information. Then click on More Settings and click on the Outgoing Server tab. Check the first box and then cl...

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

Dead Space. One of the best Xbox 360 games ever. And if you want to collect all of the logs in Dead Space, then Jack shows you where to find them. Watch all seven videos from Achievement Hunter to locate all of the hidden logs.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Log cabins are so beautiful they look straight out of a storybook. In this two part tutorial, starring Becky from Becky's Homestead, you will learn how to make your very own wooden home. It's easier than you think!

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

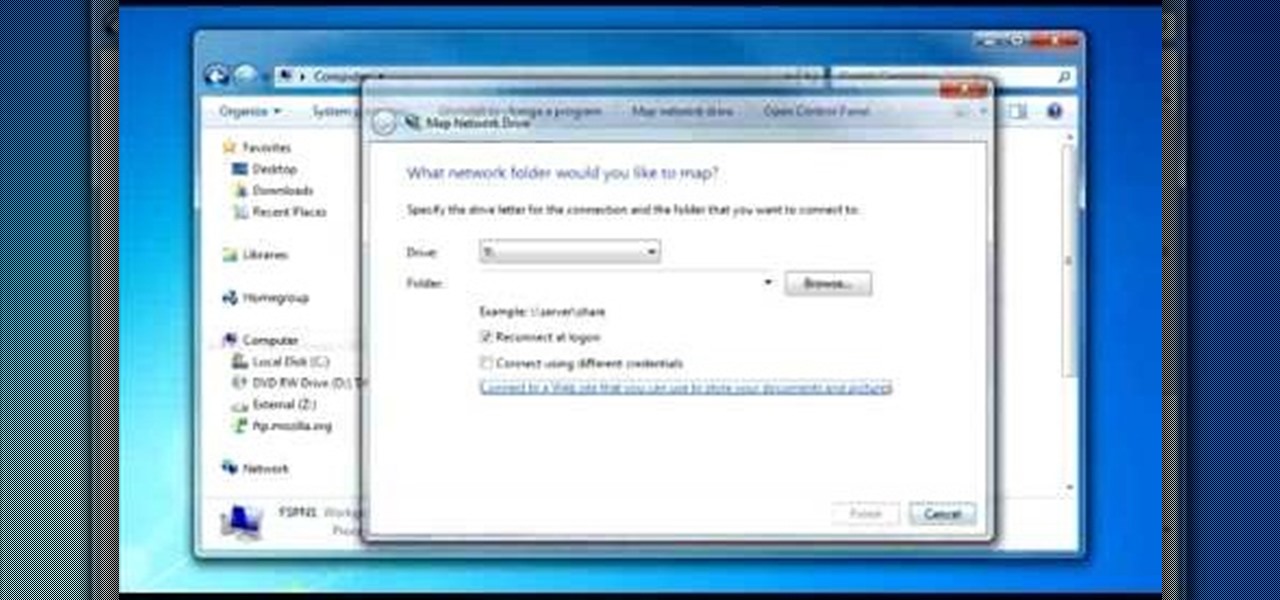
To do that click on tools in windows explorer and choose map network drive. Now click on "connect to a web site that you can use to store your documents and pictures" and then click on next and next. Now you have to type your internet or network address for example you type ftp://ftp.mozilla.org. This is a public server and it does not require a user name or password. Now click on next and there make sure you selected "log on anonymously" but if your server require a password then you have to...

If you loved the cedar log bench, try out your chainsaw skills on something for the inside of your home— a log coffee table. Using a chainsaw as your primary woodworking tool is dangerously unusual, but the results are well worth the risk! In this two-part video, learn the techniques to chainsawing your way to a beautiful log coffee table made from scraps. It's great for any outdoorsman's living room or den.

For the normal woodworker at home, the table saw, router and lathe are the prime tools used for making fine furniture, but when you hit the outdoors, the backwoodsman's tool of trade is the chainsaw. Mastering furniture-making with a chainsaw is the key to being a great woodworker, and in this three-part video, you'll learn the techniques to chainsawing your way to a beautiful log bench.

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

This video tutorial is in the Computers & Programming category where you will learn how to set up an FTP connection using Firezilla. Open up your filezilla program. On the top left, click on the file menu button, and select 'site manager'. In the window that opens up, select 'new folder' and give it a name. Now create a site to store in this new folder. Click on 'new site' and name it. Now on the right hand side, enter the host and the port. The default port is 21. Under server type, select F...

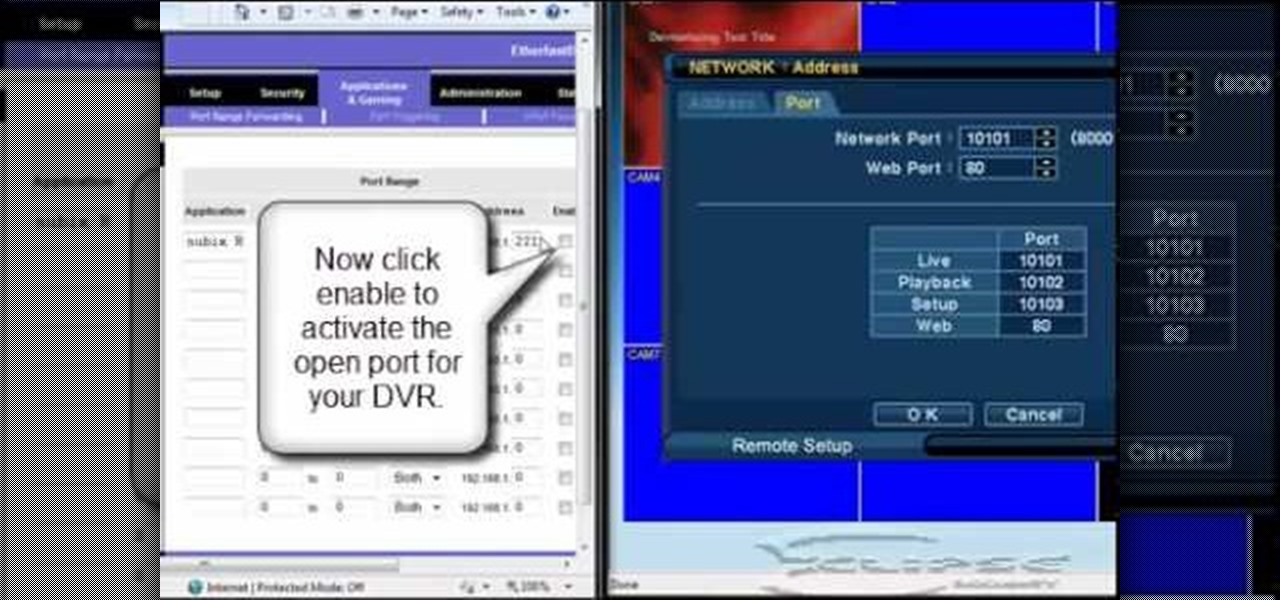
In this tutorial, we learn how to open ports on a Linksys router for your DVR. First, make sure your internet is connected and your DVR is connected to Linksys. Next, log into your Linksys router online and set up your DVR to the "DHCP" section. When you have the information from this, enter this information on your DVR so it has the correct server name. Make sure the IP and other information displayed on your Linksys page is the same as the setup on the DVR page. When finished, change your p...

Log in to your account. Go to settings, then go to Forwarding and POP. Then, check in the box for enable POP for all mail. Next, save the changes. Then go back to the settings page and check the first box (to include the mail that has already been downloaded). Save your changes again. Next, select tools>account. In the box that pops up, select POP for the account type and hit OK. Name the account and fill in your email address and POP address. For the SMTP server, put in smtp.gmail.com. Then,...

In this video tutorial, viewers learn how to SSH into the iPhone or iPod Touch without any WI-FI connection. Users will need to download the Cyberduck application. Once downloaded and installed, open the program. At the top, change it from FTP to SFTP. The server is your IP address. The user name is "root" and the password is "alpine". Now click Connect. Click Allow on the pop up window. Type in the password once again and click log in. This video will benefit those viewers who have an iPod d...

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Learn how to make Yule log cake with expert Christmas recipe tips in this free holiday desserts recipe video series on making Yule log.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

See how to prove the log a + log b = log ab logarithmic property with this free video math lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll...

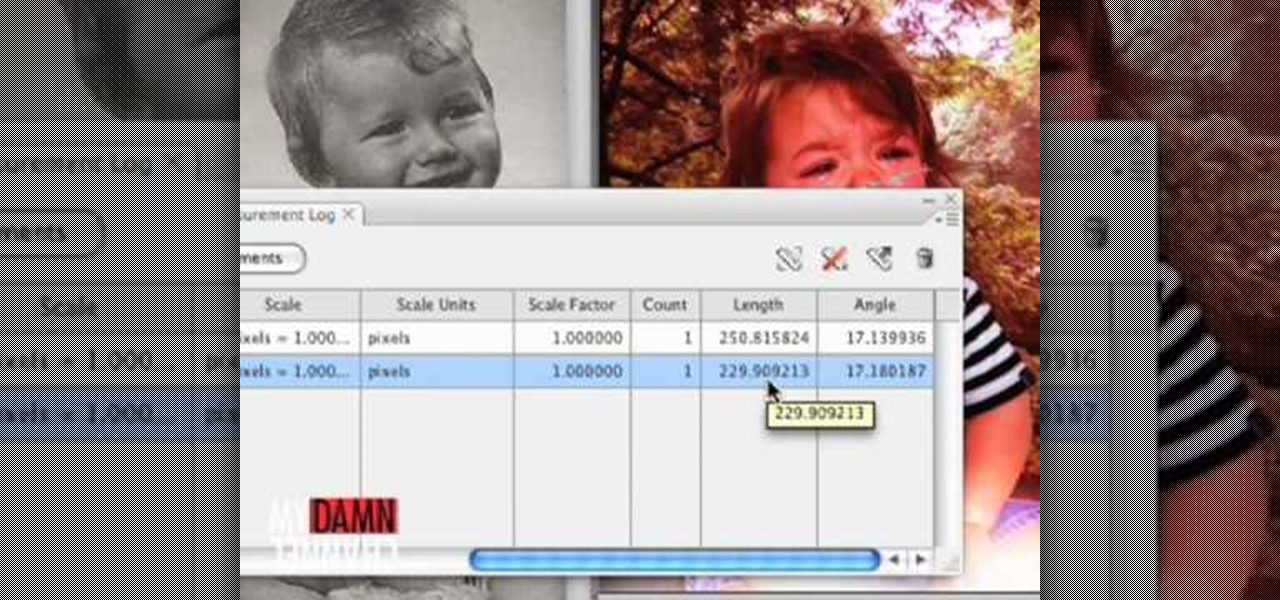
Donnie Hoyle sizes himself up against some old memories. Size yourself up too by learning how to not suck at Photoshop and use the measurement log. The measurement log in Photoshop allows you to click and drag from point to point and take the measurements of things. In this example, you learn to use the measurement log to compare similarities and differences in the faces of a dad and his son.

With a manual log splitter, splitting logs doesn't have to be such a chore. But a manual log splitter isn't ideal for every job. In this video, Tim Carter, of Ask the Builder, will teach youu about the manual log splitter and what sort of jobs you can use it for.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.