Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

With a fresh infusion of $9.7 Million in funding on its ledger, enterprise augmented reality company Scope AR has now expanded the functionality of its WorkLink platform.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

On Wednesday, in addition to uploading another batch of videos from its L.E.A.P. conference to its YouTube channel, Magic Leap also launched a new video series for developers called Spacebar.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

This video was shot in de beautiful and modern city of Rotterdam, in the netherlands, starring the dutch break dancer Stefan Dirven accompained by the song "Freestyle - Crystal ball"

Augmented reality developers who have exhausted their treasure trove of video tutorials and panels from the recent Magic Leap developer conference can now shift their continuing education attention to Unity.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

Magic Leap's recent L.E.A.P. conference was free to all who registered in time, but if you weren't able to make the trip to Hollywood, the company just released video of some of the sessions that took place over the course of two days.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

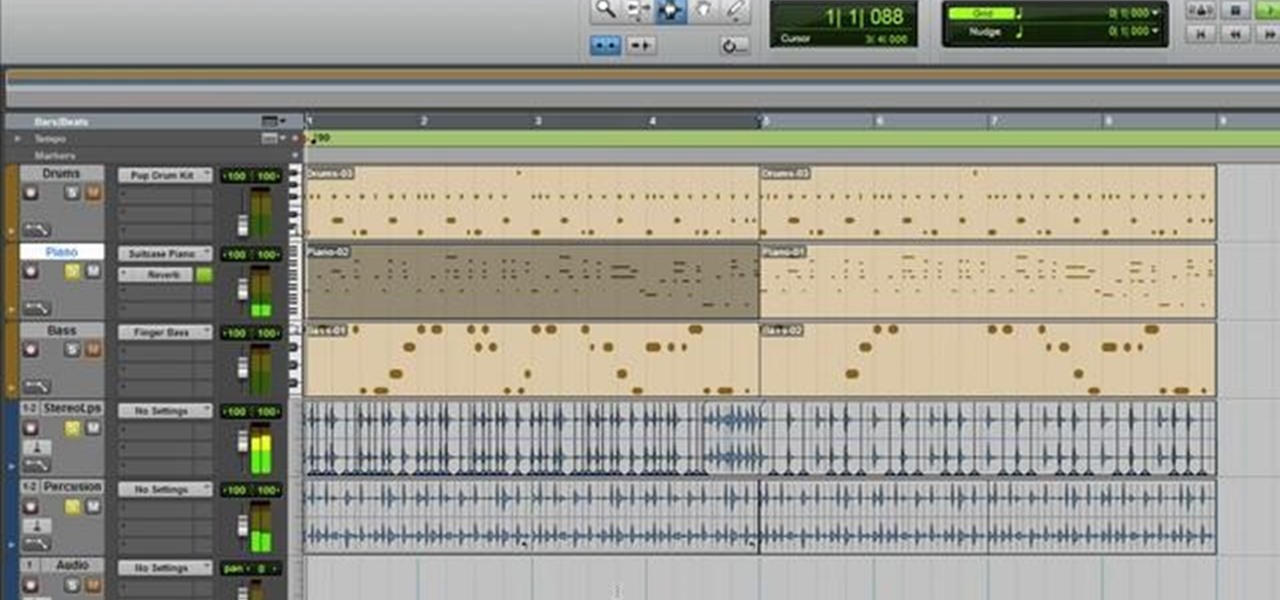
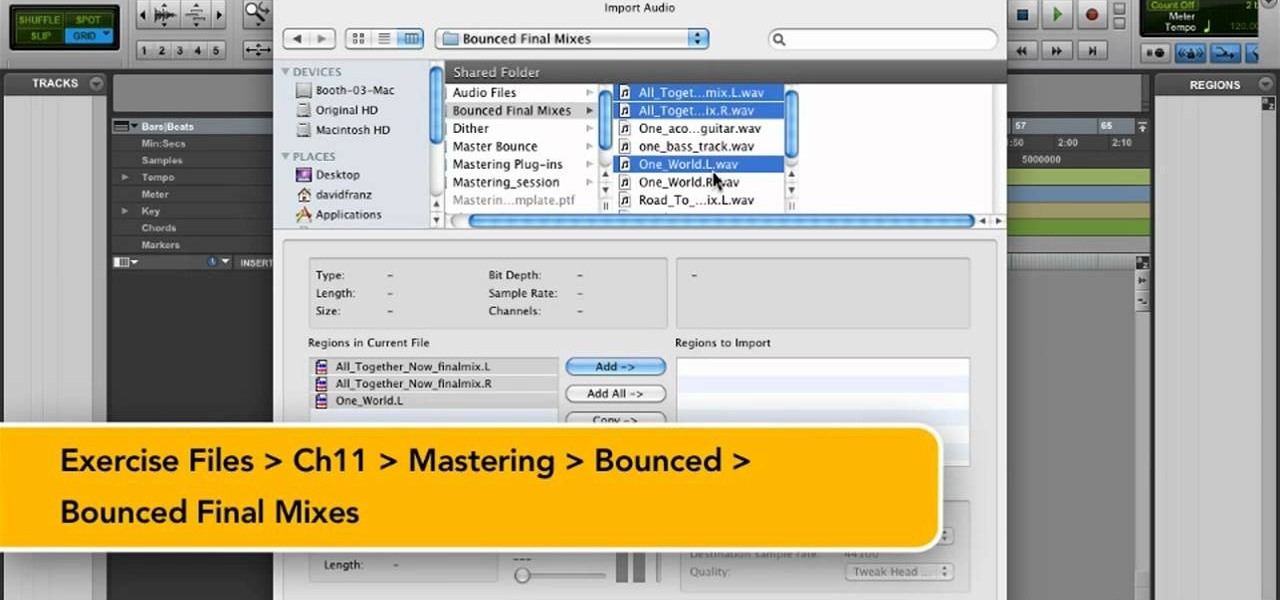
Before you can get started recording or mixing in Pro Tools 9, you'll need to create a new session for your project. This free video software tutorial from Lynda presents a complete and thorough overview of the process. Whether you're new to Pro Tools or just new to Pro Tools 9, Avid's first native, software-only version of their popular Pro Tools DAW, you're sure to find much of value in this brief video.

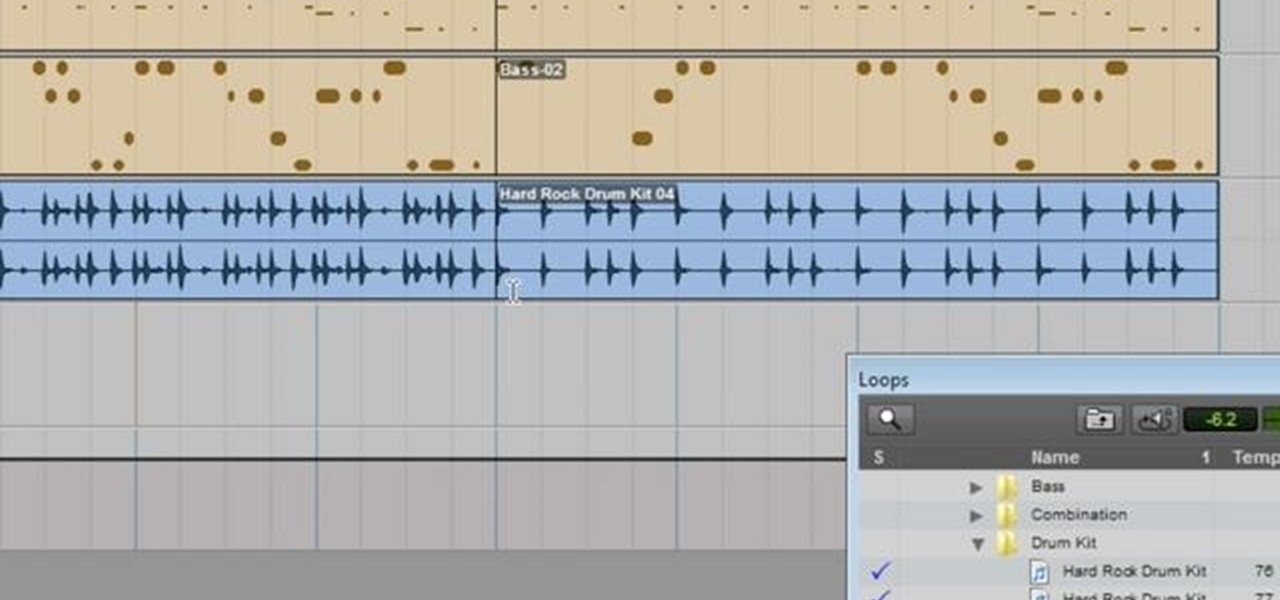
Pro Tools comes with an extensive library that you can use to add in your own loops to your session. This tutorial shows you how to find the loop library in Pro Tools SE and how to incorporate loops into your final session.

You can kill the x in Ubuntu with dontzap. Its really convenient if you like it. First thing you need to do is to download this package called dontzap. Now you can run the command sudo dontzap -d, it will disable that feature that Ubuntu uses and it will let you kill x by just pressing the ctrl + alt + backspace. It is really simple as that and there is no chance that you accidently pres the ctrl + alt + backspace and kill your x session. So after that you need to reboot your computer and you...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to session hijack with a pineapple.

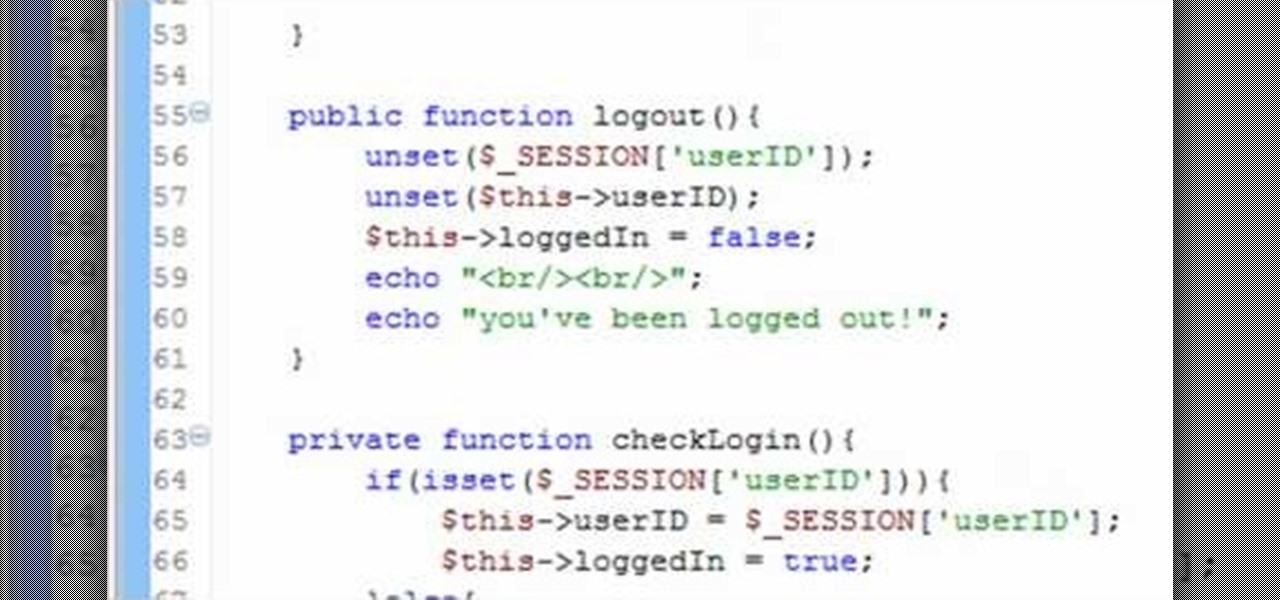
In this clip, you'll learn how to create a session class with PHP to track users on your website. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

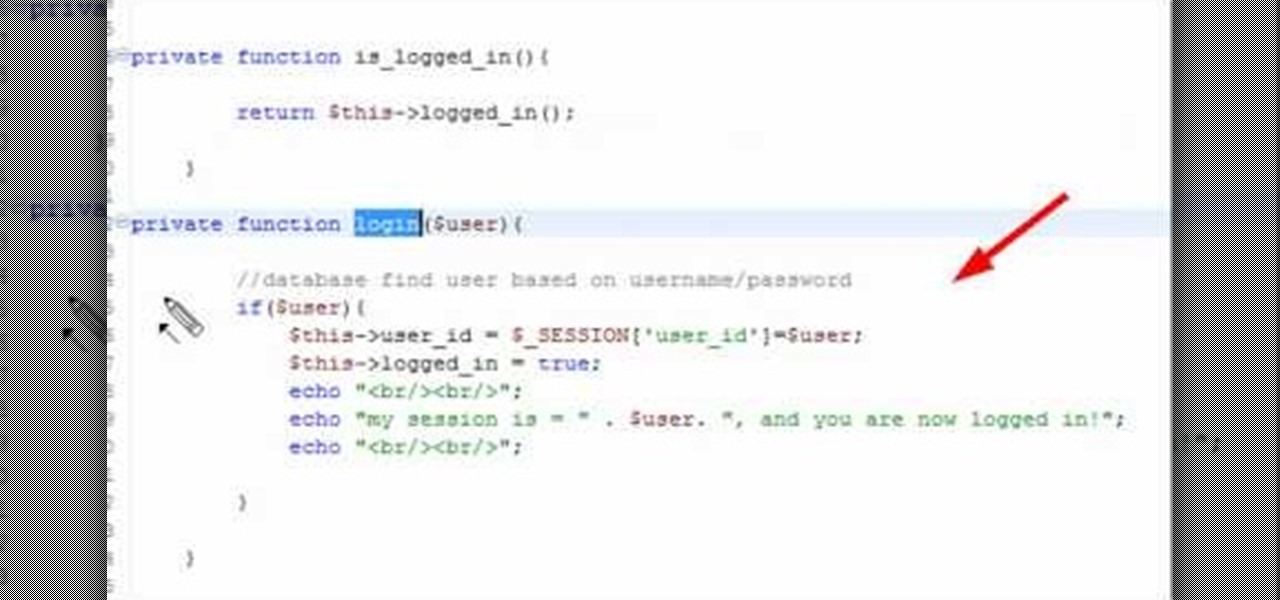
In this clip, you'll learn how to create a ogin (or log-in) session class with PHP. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

DOZ explains the setup for a tattoo session and steps you through it while he tattoo's his own upper right thigh.

The less time you spending futzing with your mouse, the more time you can spend making music. Learn how to save time in Reason 5 with a number of useful keyboard shorcuts. Whether you're new to Propellerhead's virtual music studio application, Reason, or their newer DAW app, Record, you're sure to find much to take away from this brief, official video software tutorial.

This tutorial covers several aspects of using Pro Tools. You'll learn not only how to record an audio track to include in your final project, but also how to record at a specific point and make use of cycle or loop recording.

Learn how to restore your lost data with Sony Vegas video editor. Whether you're completely new to Sony's popular nonlinear editor (NLE) or are a seasoned digital video professional simply looking to pick up a few new tips and tricks, you're sure to be well served by this free video software tutorial. For more information, including detailed, step-by-step instructions, take a look.

In need of a quick guide on how to master a finished mix within Pro Tools 9? This free video software tutorial from Lynda presents a complete and thorough overview of the process. Whether you're new to Pro Tools or just new to Pro Tools 9, Avid's first native, software-only version of their popular Pro Tools DAW, you're sure to find much of value in this brief view.

Want to close Firefox without losing all your tabs? Now you don't have to wait for it to crash. Watch this software tutorial video to learn how to turn on session restore. Turning on session restore will allow you to keep your tabs between Firefox sessions.

We had a blast during last week's social engineering calls. One of our attending social engineers was so clever that she convinced several people on Craigslist that lost items were hers, even if it seemed she couldn't be trusted. But females are better social engineers, naturally. Some say that females have a special knack for manipulating men, but I think that's preposterous. I can't see why that would be true in a million years (note my sarcasm).

Breads get made in loaves not because bakers find the shape aesthetically pleasing, but because it saves them lots of time, energy, and effort.

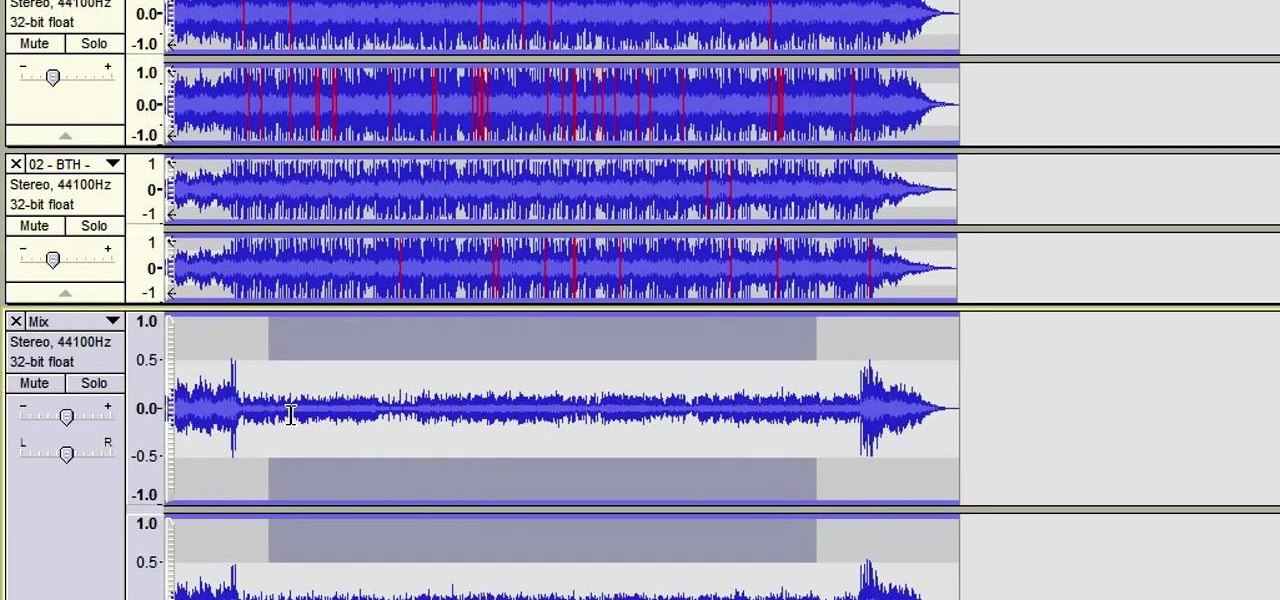
OK, your recording session is done and it went great! Well, except for the guitar. And bass. And drums. Oh, the trumpet was off. Tamborine was "meh", the harmonica was off key, the wood block was off time... you get it. The music was all wrong. BUT, the vocals were great. So, this tutorial shows you how to create an acapella track using the popular audio recording/editing software Audacity. This method is a little different than others out there on the web so check this one out and see how it...

This introductory tutorial video offers instructions on how to get the most out of a Ouija board. Beginning with casting a circle, it covers the use of protective herbs and symbols, the importance of having water to offer to the spirits and a candle to focus energy, how to invoke a spirit or demon, some important questions that should be asked when a spirit answers the call, what types of questions are best, and how to correctly banish the spirit or demon at the end of the Ouija board session...

Are you a fan of Robert Johnson? If you are, you probably have a guitar, so grab it and learn this Robert Johnson tune. See how to play "Come On In My Kitchen" on your electric blues guitar.

If you're a beginning or intermediate ukulele player and you're looking for a way of taking your playing to the next level, you'll probably want to use some movable chord forms. These are particularly helpful if you already know the open chord forms or if you're having trouble learning a song you've heard on the radio or are at a ukulele jam session where people are playing in an unfamiliar key. For more details, and to get started learning intermediate movable chord forms on the ukulele, jus...

Urgot is a unique champion who can deal out high amounts of damage early in his game, and eventually evolves into a tank/assassin hybrid who can be sent after important enemy targets. Here's a guide for building and leveling Urgot to take advantage of his capabilities to help your whole team.

Galio's strength on the Fields of Justice comes from his ability to tank, though he can provide a bit of team support as well. This guide goes over his strengths, and gives good advice when it comes to making an optimum build for the Sentinel's Sorrow for your next League of Legends game.

Vladimir the Crimson Reaper makes a good champion when you want a tank/caster hybrid. When he casts, he draws on health. His health and ability points are also symbiotic, improving one as the other goes up. Here are few tips on runes, masteries and strategy to make Vladimir a terror in battle.

A brief neurologic examination includes six sections: 1) mental status exam, 2) testing cranial nerves, 3) sensation exam, 4) testing strength, 5) deep tendon reflexes exam, and 6) coordination exam. Eve Bargmann, M.D., shows doctors how to perform this neurological examination on a patient. You will need to do a full neuralgic exam (not in video) if any abnormalities are found. But this is just a brief screening exam during a general physical exam.

Eve Bargmann, M.D., will teach doctors in this video how to perform an examination of the patient's heart and blood vessels. As with any examination, you should start out with inspection. Start off with the jugular venous pulse, then examine the heart by palpation and auscultation with bell and diaphragm of the stethoscope, and lastly examine the blood vessels.

In this video, doctors can learn how to perform a full cardiac examination on a patient. The very first thing a doctor should do is visually inspect the patient, because there's a lot that can be gained by simply examining by eye. You'll want to carefully examine the respiratory pattern of the patient, the nature of their precordium, the anterior part of their chest over the heart. Feeling the pulse is also necessary when starting out this heart exam. To learn more, watch the full video.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Easttexas937 shows viewers how to properly use a Ouija board to get the best experience. First you will need a Ouija board and a pointer. If you want to make these two things, you should use lightweight glass and make sure you make the board properly. You have to have an open mind and good intentions when you go in to use the board. There also must be no secrets between the friends playing and you should not have a friend that is not trustworthy. This will keep evil spirits out. Always have m...

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.