Who wouldn't want to know if someone was trying to log onto their personal computer without their permission? Be it your annoying co-worker or your girlfriend, there are many cases where people may try to gain access to your desktop or laptop.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Protect your email account from would-be hackers and crackers with this free video tutorial from the folks at MacMost. If you have a Gmail, HotMail, Yahoo! Mail or other web-based email account, this video is much recommended. For more information, and to secure your own online free email account, watch this helpful guide.
Need to protect a section of your overall flash content (say movie or slideshow) from unauthorized access, learn how to do so in this video.

This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Check out this tutorial and learn how to encrypt Microsoft Office files to help prevent unauthorized people from opening a workbook, document, or presentation. Watch the video to see how easy it is to set a password to help you control who can open or modify the Office files you create.

A close look at an alternative adaptive method for playing nonlinear theremins (theremins whose notes are not evenly spaced) such as the Moog Etherwave Standard theremin.

In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.

This video tutorial from DrJailbreak presents how to download and install Androidlock on your iPhone and iPod Touch.Androidlock is a type of application that locks screen to prevent unauthorized access. You have to draw a specific pattern on the screen to unlock your device. It is advisable not to create too difficult Androidlock pattern because you can forget it.You also can turn off Androidlock if you open subsettings, select More and then Mobile Substrate Add-ons option.To get Androidlock,...

This video is an entertaining way of learning how to quantify how much time has elapsed from one point to another. It opens with a mischievous person using an unauthorized computer, claiming he had only been on for a shorter time than what was calculated by the owner. The video then instructs how to figure out such a calculation by creating a T-chart. One the left side of the T-chart, the previous time is shown, along with new times as each hour or minute is added. On the right, the desired t...

The key to repairing bad credit is to write a properly formatted letter of dispute to one or all of the credit bureaus and send them out via registered mail. Here's a step-by-step guide to writing a letter of dispute to get rid of those black marks off your credit report for good. Remember, it's your right to file a dispute.

When you are editing your documents, it is sometimes a good idea to protect areas of text, so they cannot be edited, just in case you make a mistake and edit the wrong part.

The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.

If you want to protect your word doc from other, you can give it a password. When anybody wants to open, it will ask a password. This way your valuable document will be secured from unauthorized access.

This video demonstrates the steps to restore your iPhone or iPod Touch to original factory settings. This is a way to undo or repair any damage to your phone caused by downloading unauthorized files or corrupt files. Be aware that this will delete all the files that are on your device including music, pictures, videos and contacts, so use this method when all others fail. First connect the device to a computer via USB and select the device in iTunes as shown. Go to the device's information pa...

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Recently, a user on Reddit complained that their Snapchat account had been temporarily banned because Snapchat noticed the user's account was going through a third-party service. In reality, the account in question was running on a jailbroken iPhone, and it was far from the first to be banned by the messaging app.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

The saga of augmented reality startup Meta appeared to be at end, but there are new developments unfolding in real time that may either sink Meta deeper into trouble, or provide a tenuous lifeline for the beleaguered augmented reality company.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

For those interested in jailbreaking their A4 Apple devices (iPhone 4, 3GS, and 4th Gen iPod touch), a new update has been released that makes things a little easier. Unlike the previous Redsn0w iOS 6 jailbreak, the newest version, 0.9.15b1, comes with full support of the Cydia App store.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Oh no... your precious iPhone is in shambles. Maybe you shattered your screen after a crazy night of celebrating, or maybe your two-year-old jabbed a toy into your iPhone's charging port, completely destroying it in the process. Now what? Do you take it to a repair shop, or go to an Apple Store to have it fixed? This brief article will help you weigh your options.

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

Apple has released the second beta for iOS version 11.2.5 for developers on Dec. 19. The update comes six days after the release of the first 11.2.5 beta which updated the Music app to include a persistent "play bar" at the bottom of the window, along with some bug fixes. Public beta testers received the update on Dec. 20.

Just nine days after the official release of iOS 11.2, Apple has released iOS 11.2.1. The update initially seems to have been seeded to only a handful of users and is intended to fix bugs in 11.2.

Any parent with a rambunctious child who may have at one point racked up a hefty bill on their Kindle or Android device can now breathe a sigh of relief. One, Jack Black has had it happen to him too, and two, Amazon will be refunding up to $70 million of in-app purchases made by children after downloading apps from the Amazon AppStore.

You no longer have to worry about repair technicians accessing the personal information on your iPhone when you send it in for repairs. With Apple's new security feature, you'll no longer have to erase your iPhone to ensure your photos, messages, accounts, and other private data remain for your eyes only.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Remember that scene in Tim Burton's Batman where the Joker and his goons defaced dozens of priceless works of art? A collective of digital artists have found a less criminal, more geeky way to do the same thing.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

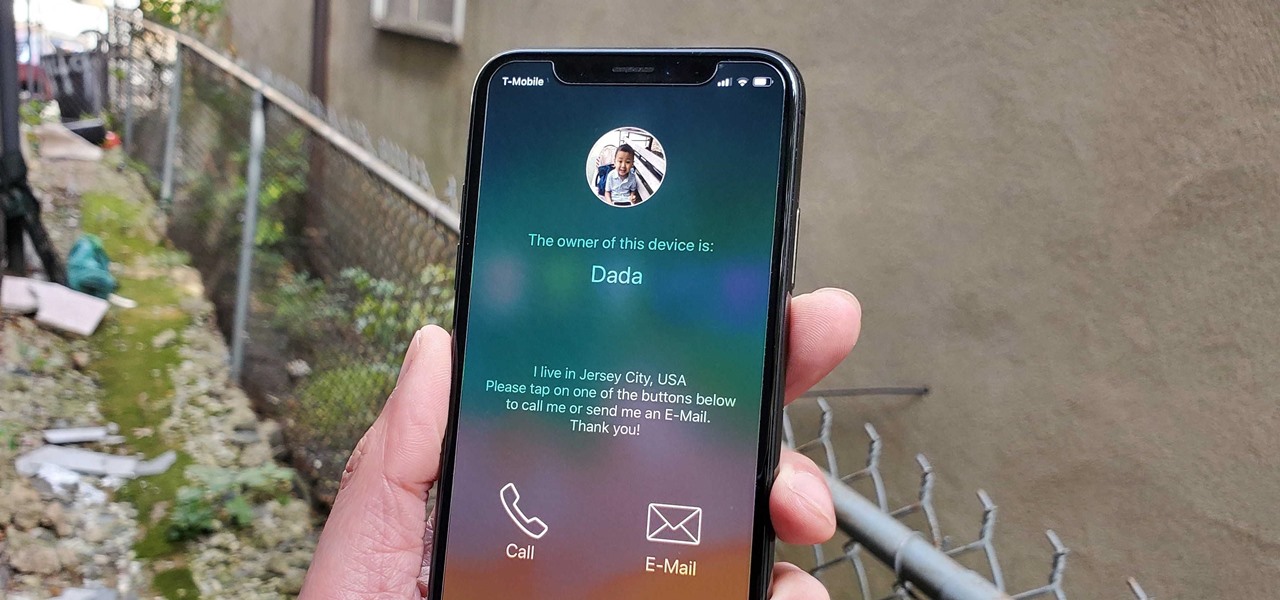
If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.