
News: First Look at the iPhone 6's Unbreakable Sapphire Crystal Display
It's increasingly difficult to keep any secrets at bay, and that has become especially true for Apple's upcoming iPhone 6.


It's increasingly difficult to keep any secrets at bay, and that has become especially true for Apple's upcoming iPhone 6.

You've been there. Those precarious few seconds between dropping your expensive smartphone right on its face and reaching down to survey the damage. Or maybe you got thrown in a pool while your device was in your pocket, or you dropped that sucker right into the toilet bowl. Heck, I've managed to accidentally wash two devices by leaving them in my pants pocket when throwing in a load of laundry.

Put the egg in a corner and your victim won't be able to smash it with the flat part of the frying pan, making it an unbreakable egg. This is a sensational trick, so see the full reveal of this bar trick.

Bet you can smash your finger with a can and have it not break? You can with this physics-based trick.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

Watch to learn how to perform a magic trick by squeezing an "unbreakable egg."

In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many password...
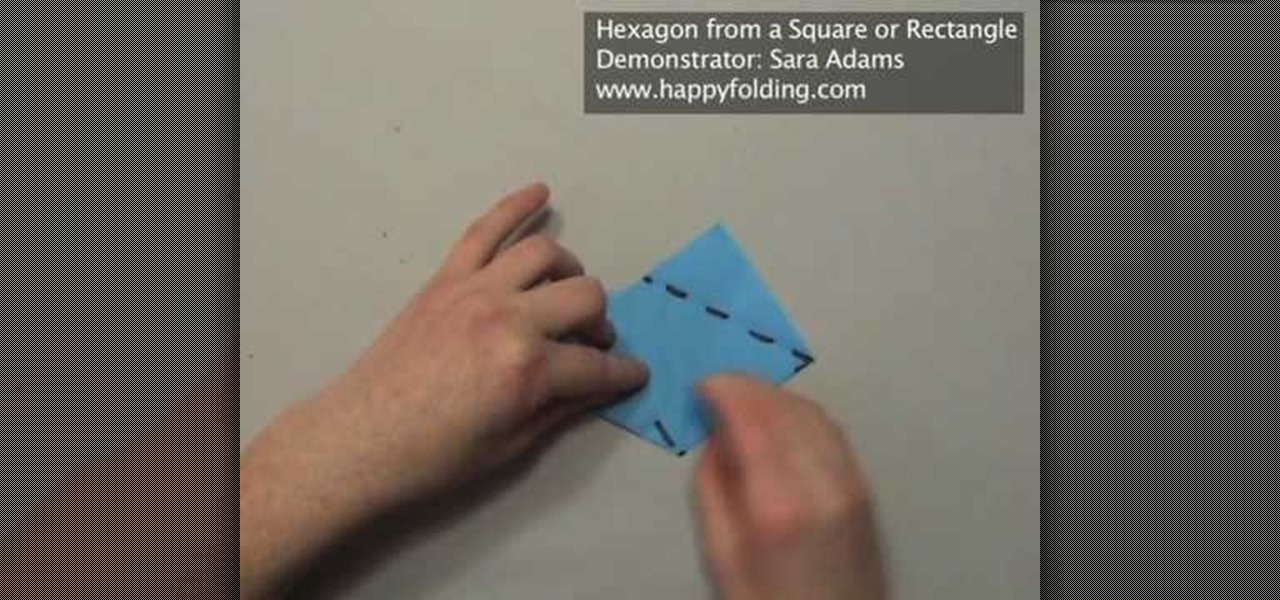
This video will surely perplex math teachers everywhere who have always made it an unbreakable rule that all rectangles are squares and that not all squares are rectangles, but neither squares nor rectangles are hexagons.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

Installing clean, reliable, inflation-proof solar power is easier than ever thanks to the invention of thin-film photovoltaic (PV) laminates that can be bonded directly onto metal roofing panels. Unlike crystalline PV material, there's no need for obtrusive racks and heavy, expensive glass. Instead, unbreakable thin-film PV is produced using amorphous silicon, encapsulated in Teflon and other polymers. Watch this video to learn how to install PV laminates on your own roof.

This video is demonstrating the technique of jala neti by Steve. It is a purification exercise. You will use the unbreakable neti pot in the bathroom to do jala neti. This pot's nozzle properly fit in the nose and the plastic body of the pot can be easily hold. For 200 ml of neti pot put 1/3 of teaspoonful of salt. Don't put more, or otherwise your nose will burn. Fill the water straight from the tap and shake the neti pot properly. Take the neti pot in the right hand if you want to put water...

In this sports video tutorial you will learn how to play golf with Goofy. Contrary to many beliefs, playing golf is not a waste of time. Out in the open green, happily the golfer chooses his club. A modern golfer comes with balanced and matched clubs. A tee is used to support the ball. The interlocking grip is extremely scientific and it gives the golfer a virtually unbreakable grip over the club. Learn it from an expert. Once the grip is mastered, the golfer is ready to hit the ball; which i...

To help keep sleepy binge-watchers from sleep-"watching," Netflix asks if you're still watching after a semi-short period of time. This means that it could be anywhere from 1 to 5 episodes that you slept through, which is better than 2 seasons, I guess—but it doesn't make it any easier to find out where you left off.

Copy and paste keyboard shortcuts are beautiful gifts from the gods, and any website that blocks such an offering can burn in hell. But really, Cmd+C and Cmd+V (Ctrl+C and Ctrl+V for Windows folks) are second nature to most of us, so it's very frustrating when sites like PayPal don't let us use them.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.
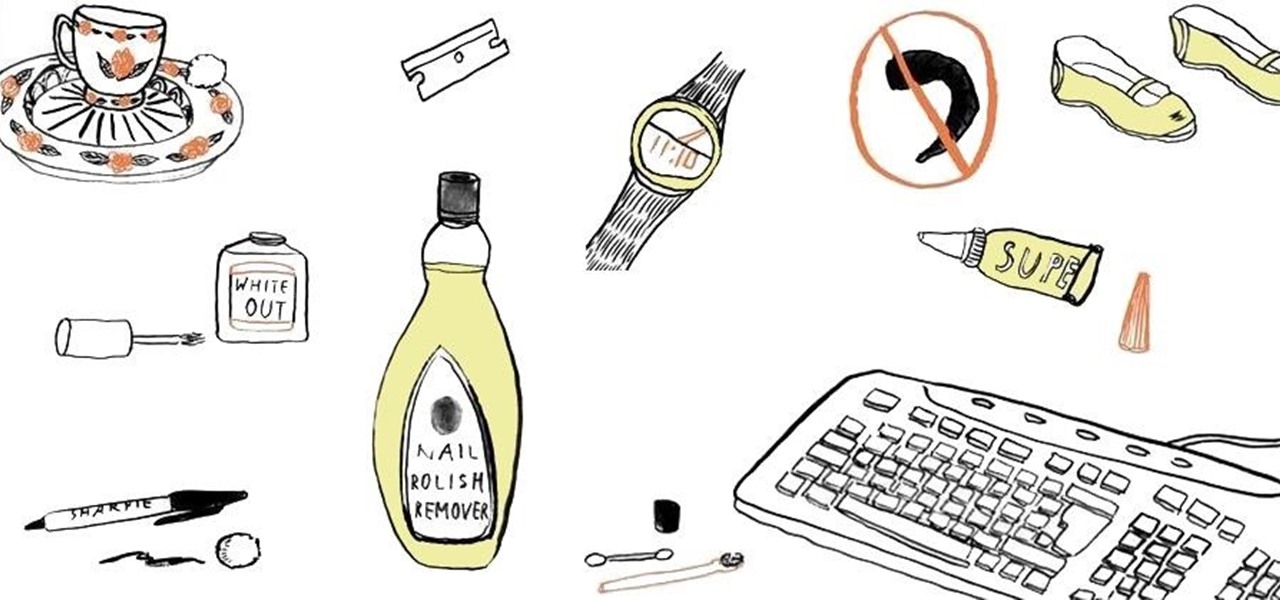
Acetone-based nail polish remover is great for removing nail polish, and it's also great for some DIY uses around the home. From eliminating scratches to fixing the consistency of correction fluid, its uses are varied but all effective. With nail polish remover, you can also clean your computer keyboard, get rid of ink stains, and even remove leeches from your skin. Talk about versatile!

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Look, tests are no fun, and doing poorly on them is rarely an option. Whether you're studious or a slacker, everyone needs a little boost now and again. While students have found ways to cheat as long as tests have existed, the invention of smartphones has greatly enhanced the potential to get ... creative.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Your smartphone stays with you everywhere you go, so it's only a matter of time before you spill coffee all over it or drop it on the ground. For some of you, it has already happened, perhaps even multiple times. That's why we thought it was important to find out which flagship phones are the most life-proof.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.