For design embroidery software Embird. Want to know how to remove pesky underlying stitches using the Mask Tool? Rosanne demonstrates in this tutorial using the pull tool, as well. Remove underlying stitches in Embird.

You can't accurately draw a human face - heck, any part of a human body - without knowing about how the underlying bones and muscles contribute to structure. And while disecting is by far the best thing you can do to improve your knowledge in these two fields, we don't all have the ability to do such things. So this video is the next best alternative.

Just because it's called palm reading doesn't mean it's only "palm" reading. Palmistry involves more than mere palms — it looks at all parts of the grasping side of the hand, including the fingers. And in this two-part video from Jim Winter, a professional palmist, tarot reader, face reader and graphologist, you will learn the secret, underlying meaning behind a person's fingers. Knowing the digits is just as important as knowing the sweaty palm.
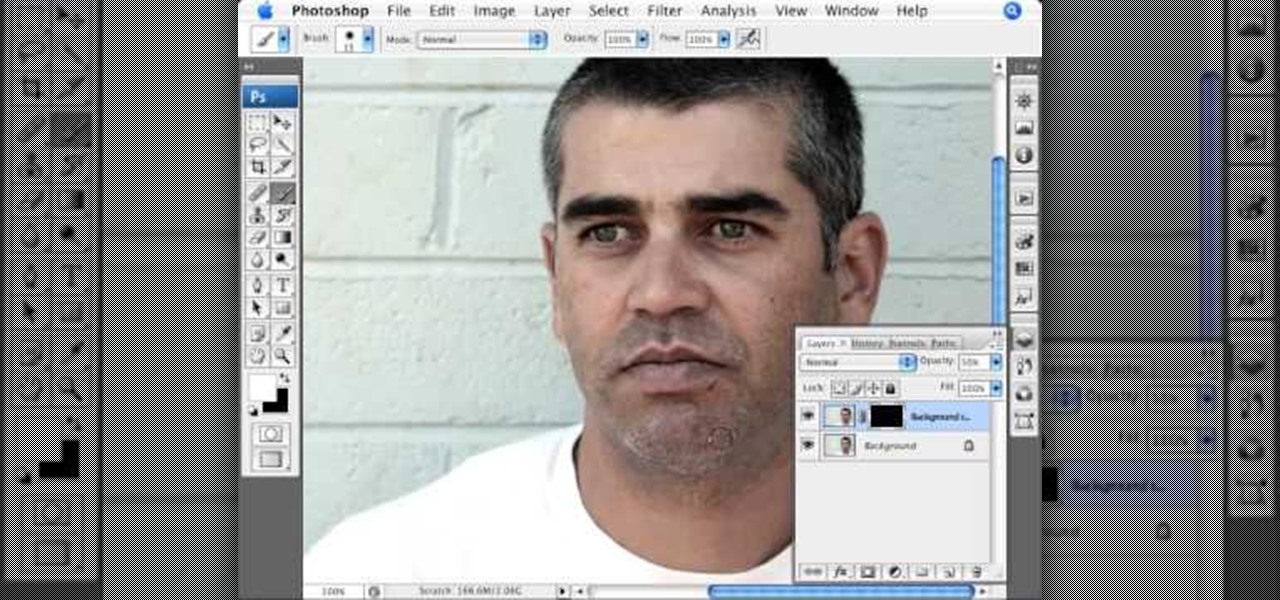
This video, produced by Photoshop Universe, teaches how to reduce beard stubble or 5 o'clock shadows from male pictures. We are shown how to use the dust and scratches filter, layer mask, as well as the advanced layer style command "blend if" on the underlying layer helps us to make this possible. The first step is to duplicate the layer and then select filter, noise, and dust and scratches. The second step is to apply some dust and scratches to the beard selection. Finally we blur the layer ...

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create cloud over a sea in Photoshop.
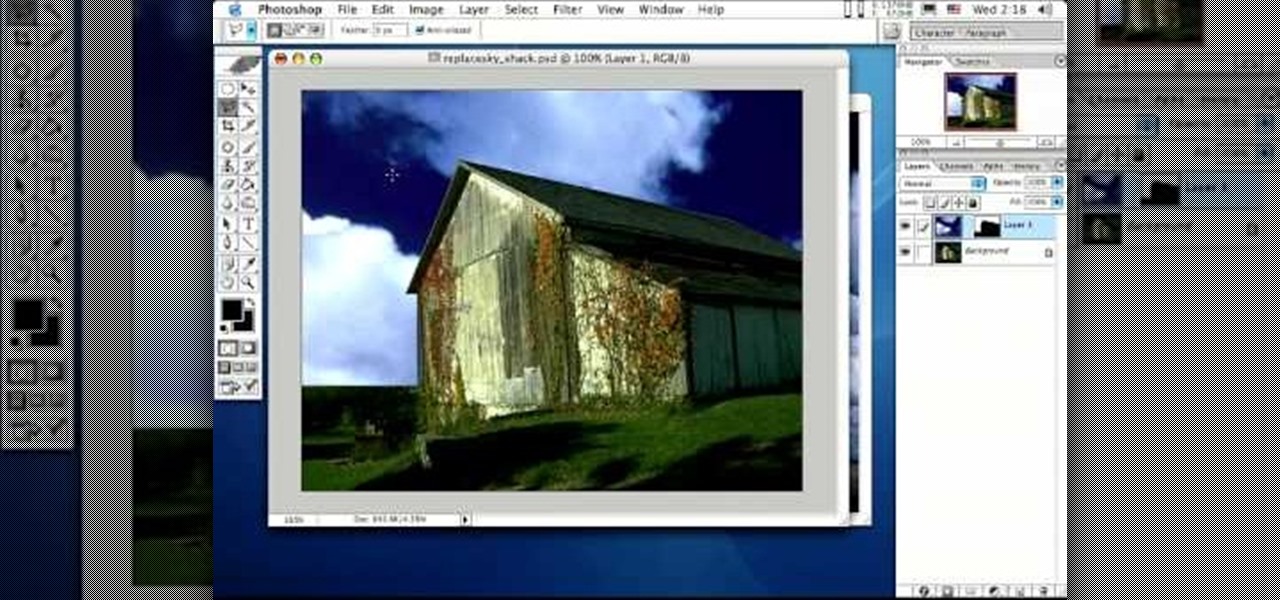
Photoshop is the perfect program to use when you want to make adjustments to photos you have taken. You can really make a sky pop in any of your pictures by using Photoshop to manipulate the color by following this tutorial.

This video tutorial offers an introduction to the terminal for those making a switch from Windows to Mac OS X, one of the most powerful (yet cryptic) of OS X, which will allow you to interact with OS X's underlying UNIX layer. If you'd like to get acquainted with the terminal, simply press play!

In order to begin, you will need the following: Three hair tiesBobby pinsHair spray or spray gelRat tail combHair net

GAF roofing has a four nail pattern. The shingles come in 2 sizes: English and metric. In this video we will be using English sizes. Place the shingles in a row by row pattern. You may move left to right or right to left but never move up the roof. You may have the shingle hanging over the roof by 1/4 in. Install the leak barrier in high wind areas. Place the second shingle next to the first. Five inches of the underlying shingle should be exposed. Use a whole shingle for the first course. Th...

The Artful Paper Doll demonstrates how to make a Marie Antoinette inspired matchbox. Trace the matchbox template onto a piece of decorative paper. Score the template on the creases and then cut the template out of the decorative paper. Fold the creases up. Affix the creases into a square basket shape with dabs of glue to hold the flaps closed. Fold and glue the ends of the box sleeve together. Slide the basket into the sleeve to form the matchbox. Embellish the box as desired. The box can be ...

Before meeting with an architect, you may want to review this video tutorial which outlines what you ought to consider when meeting with an architect that will be helping you renovate your home. Homeowners should visit places and take down notes and photos of what designs they appreciate so that they can bring it to the architect. This will help you to train your senses and language to describe what you like and dislike in terms of style. You should also bring magazine clippings or books of s...

Learn how to combine images with a mask in Adobe Photoshop by opening the same raw file twice and applying separate exposures. This technique is used to perhaps mask out the sky or the windows. Using the negative exposure making the initially over exposed sky black and the dark parts white which is what the mask feature operates on. Then the designer selects cuts out the sky in the mask layer and makes it invisible so that the second layer or underlying picture shows through.

Constipation affects almost everyone at some time. Follow these tips to help prevent it. This how to video lends helpful advice on preventing constipation (and possibly resulting hemmeroids).

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Many injuries do not require an ambulance, but they must be referred to medical aid for further treatment. This first aid how-to video will show you how to identify wounds that require further treatment. Underlying and dirty wounds, foreign objects, and stitches are all injuries that require a patient to go to a doctor or hospital.

Wounds that involve underlying structures usually require immobilization. The purpose for immobilizing an injured victim is to provide support. This first aid how-to video demonstrates the proper technique for immobilizing someone who has serious wounds or injuries.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Before there was Gray's Anatomy, physicians and medical students used anatomical flap books to explore the inner workings of the human body—a scientific illustrated guide that takes its name from the moveable paper flaps that can be "dissected" to reveal hidden anatomy underneath. Similar to pop-up books, these instructional tools mimic the act of human dissection, allowing doctors and students to study the intricacies of the body normally concealed by flesh.

Have you ever bought a cork product? Cork liner? Cork coasters? Wine… with a cork? Well, did you ever wonder where it comes from? Watch this video demonstration and you'll find out how raw cork is extracted from the Cork Oak.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Montezuma's revenge, the runs, the trots, or just diarrhea — everyone gets it sooner or later. What exactly is diarrhea good for, if anything?

In response to the success of Apple Pay and an attempt to stave off the appealing Samsung Pay service, Google is completely revamping Android's mobile payments system. Instead of just using Google Wallet as an app to make payments with your phone, a new service called Android Pay, with an extensive underlying framework and API, will soon make its debut—and maybe even sooner than you'd think.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

It's truly amazing how far smartphone camera hardware has come in such a short period of time. It took roughly 5 years to advance the image processing capabilities from a pixelated mess to the crisp and clear photos we can take today. This reaches well beyond the megapixel spec race, since camera modules these days sport vastly improved optics, wider aperture, and even larger pixel sensors that capture more light.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Apple's first AR wearable might not arrive until 2022, but we may have an early preview of what it will be like to wear a pair of its smartglasses via iOS 14.

Waveguide manufacturer DigiLens has closed a $25 million Series C round of funding from automotive technology company Continental, which uses the technology in its heads up displays.

Microsoft, even being Apple's fierce competitor, is no stranger to producing iOS apps—in fact, they've made 94 of them. But their latest iOS app may be their silliest yet: a goofy photo editor named Sprinkles.

When eyesight deteriorates, either due to illness or advanced age, many people turn to audiobooks as an alternative to reading. With today's technology there is an abundance of services and devices one can use.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

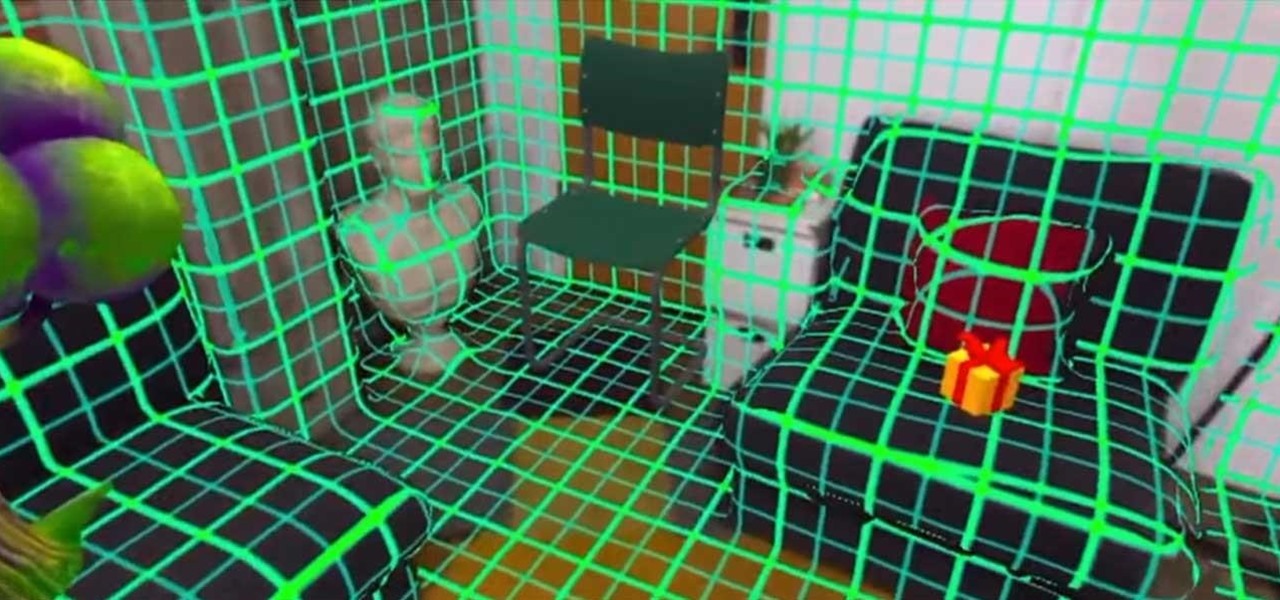
San Francisco-based 6D.ai is preparing to launch a beta of its AR cloud platform that's capable of constructing a real-time dense mesh from crowdsourced data for use in 3D mapping and multi-user AR experiences.

If you're an Android user, you're very likely jealous of your iPhone friends who have access to the wide, wonderful world of augmented reality thanks to ARKit.

A top executive from Baidu's telematics division believes the company will become the word leader in driverless by 2020, according to a report in today's South China Morning Post.

BMW seeks to hire 2,000 engineers for its driverless program ahead of the launch of its iNext Level 3 model in 2021, a source close to the company told Driverless.

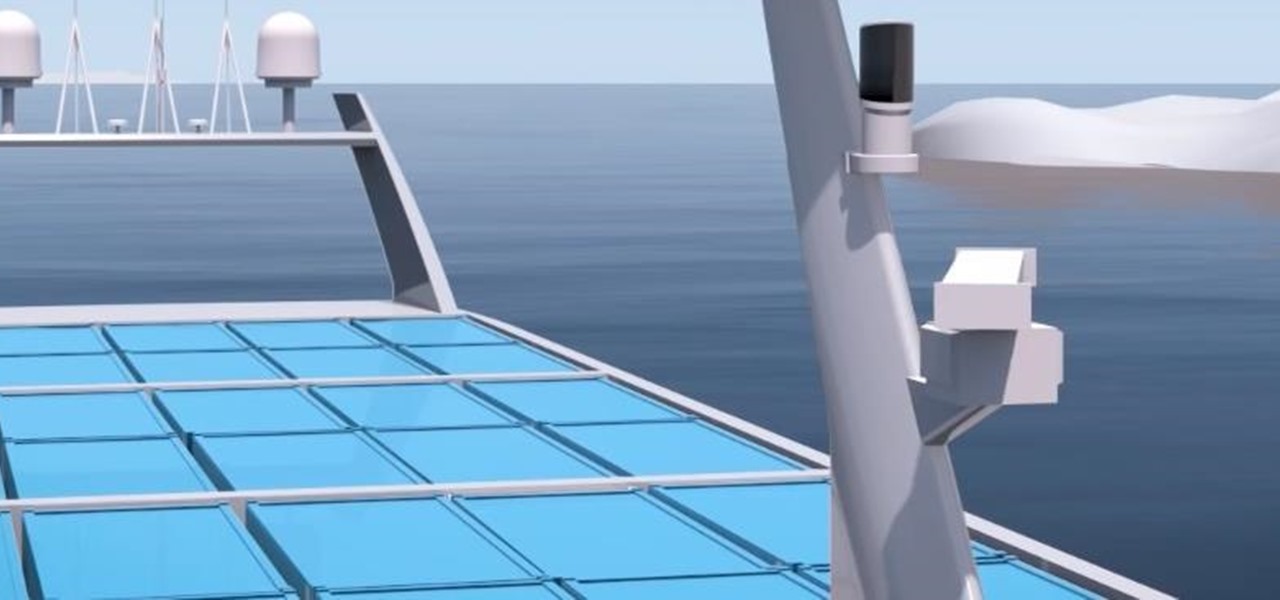
A Norwegian carrier's launch of a pilotless container ship next year could lead the way to a new era in sea transportation and shipping if successful.

Germany-based Pupil Labs has jumped into the UX and control deep-end with a range of products that allow the user to add eye tracking to not only their existing augmented and virtual reality head-mounted displays but computers as well. This type of technology can add a new depth to the way we control devices.

Waymo's transfer of its driverless car know-how to commercial trucks will likely pose few challenges for the self-driving unit of Alphabet, which owns Google.

With every flagship device they release, Samsung makes sure to add in at least a few little software goodies. Last year's Galaxy Note5 was no exception, because among other things, Samsung included a revamped version of their useful utility called Air Command that gave users quick access to tools and common functions with a small floating bubble.