Hot Posts


How To: Use John the Ripper in Metasploit to Quickly Crack Windows Hashes
There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

How To: An Exhaustive Guide to Building Mob Traps in Minecraft
Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

How To: Remove Annoying Contact Suggestions in Your iOS Share Sheet Completely or Temporarily
By default, your iPhone's share sheet will have a row of contacts iOS thinks you'll want to share the content with. Those suggestions are handy if you frequently share things with the same people, but they also clutter the share sheet, invade contacts' privacy in screenshots, and tell nosy people in eyeshot who you share with the most. Thankfully, you can remove or hide them whenever needed.

The Hacks of Mr. Robot: How to Hack Bluetooth
Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

How To: Hide Photos in the Gallery App on Your OnePlus Phone for Extra Privacy
Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.
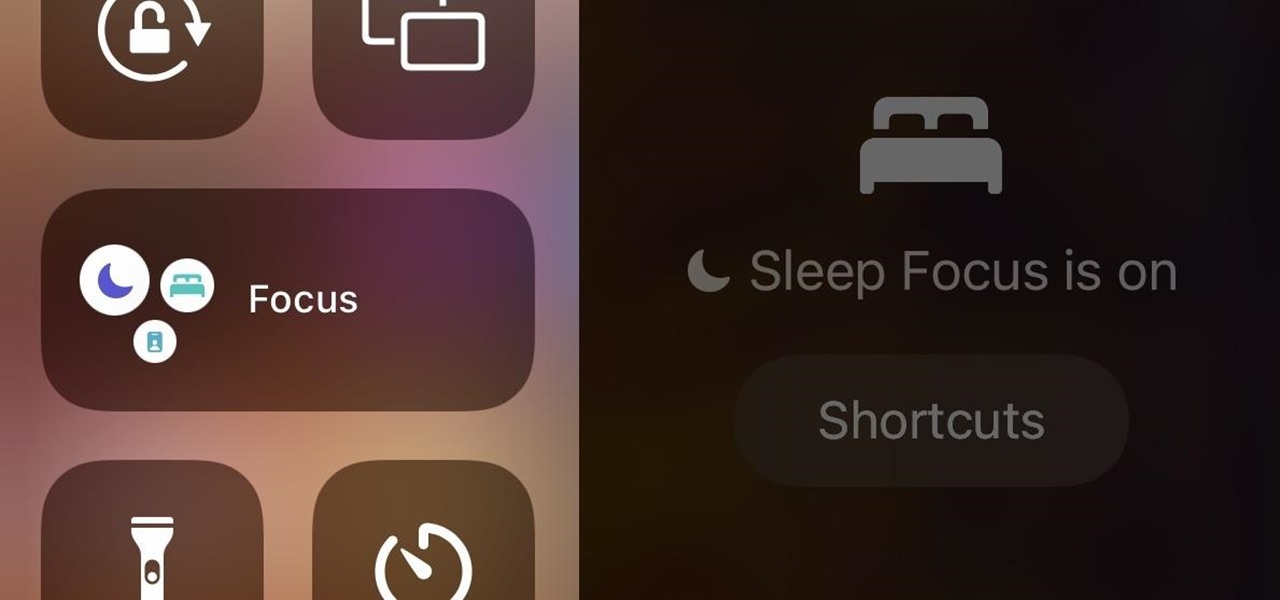
How To: Everything You Need to Know About Your iPhone's Focus Feature — From Creating and Editing Focuses to Automating Them
In iOS 15, Apple unveiled a new feature called Focus, an extension of Do Not Disturb that lets you focus on the one thing that's important at any particular moment. It does so by minimizing distractions from your iPhone and other Apple devices, but there's a lot you should know about setting up and using Focus on your iPhone or iPad before you dig in.

How To: Set Your Android to Atomic Time for a Perfectly Synced Clock
For most Android phones, the system clock is set using a protocol called NITZ, which relies on a connection with your carrier to ensure that the time stays in sync. The trouble here is that this feature won't work when you're outside of cellular range, and a lot of times, the carriers themselves have technical difficulties that can result in your phone's clock being minutes or even hours out of sync.

HowTo: Build a Vibrating Lock Pick With a Toothbrush
Unbeknownst to the general public, picking a lock can be a very easy process once you get the hang of it (yes, surprising AND frightening). A vibrating lock pick set takes the general ease of picking even further by speeding up the process. Now, with the help of Invent Geek, you can make your own DIY Vibrating lock pick for about a tenth of the price of a manufactured kit.

How To: Do the "Jack the bounty hunter" card trick
This card trick is called Jack the Bounty Hunter. After a series of cuts, placements, and sorting, Jack the Bounty Hunter ends up adjacent to a card the spectator picked earlier in the trick. Brief synopsis of the procedure (you need to see the video for the full explanation): First, you set a Jack aside. Then you make two piles of 15 cards and set them aside. The spectator gets a pile, and you get a pile. Cards are cut. The spectator picks a card from the remainder of the deck. The spectator...

Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 3 (Recovering Deleted Files)
Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

How To: Perform the Last 3 card trick
For this tutorial we are picking three Aces because they are the easiest to remember. Make 4 piles of cards. First pile is ten cards. Second pile is 15 cards. Third pile is 15 cards. The last pile will be 9. Take the Ace of Spades (the example card),put it on one pile and put any number of cards on top. Take the Ace of Hearts (another example card), put it on the second pile and put any number of cards on top. Take the last Ace put it on top and put the last pile on top of that one. Stack the...

How To: Open Any App Instantly from Your iPhone's Lock Screen
Widgets can display essential information from an app right on your iPhone's Lock Screen, but there's an even bigger reason you should be using them: fast access to your most-used apps.

How To: We Tested the Best Burner Phone Apps for iPhone & Android — Here's Our Top 4
A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

How To: Download Any TikTok Video on Your Phone — Even if They're Blocked from Saving
Many apps, including Facebook, Twitter, and Facebook, do not let you download videos, even if they are living on your own account. Saving these videos usually requires a third-party app or screen recorder, which is inconvenient and can result in loss of quality. However, TikTok, the newish popular short-form video platform, makes it easy to download videos — even if they're not yours.

How To: Log Wi-Fi Probe Requests from Smartphones & Laptops with Probemon
It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

How To: Use UFONet
With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

How To: Crack Password-Protected ZIP Files, PDFs & More with Zydra
Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

How To: 7 Ways to Bypass Android's Secured Lock Screen
If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

How To: Welcome to Math Craft World! (Bonus: How to Make Your Own Paper Polyhedra)
Welcome to Math Craft World! This community is dedicated to the exploration of mathematically inspired art and architecture through projects, community submissions, and inspirational posts related to the topic at hand. Every week, there will be approximately four posts according to the following schedule:

How To: Use Pupy, a Linux Remote Access Tool
In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.
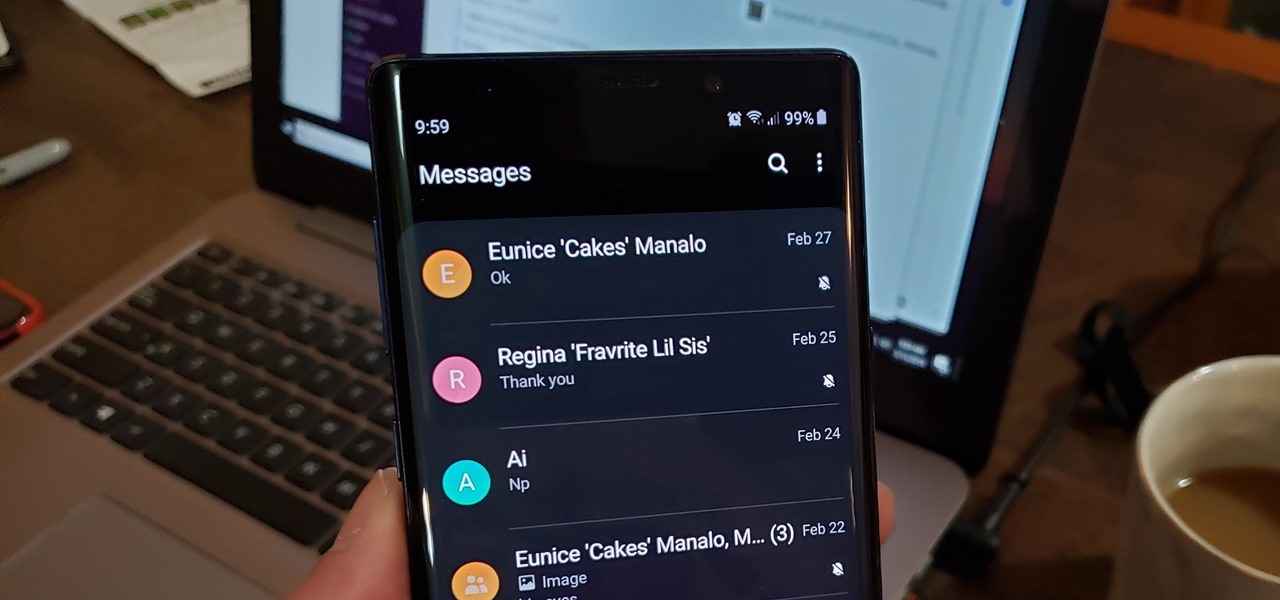
How To: Mute Conversations in Samsung Messages Without Blocking Contacts
Text conversations and group chats can sometimes devolve to random and nonsensical chatter that bombard you with annoying notifications. Naturally, this can get distracting and prevent you from focusing on more pressing matters. Fortunately, Samsung Messages has a feature built in to minimize distractions whenever conversations go out of hand.

How To: Remotely Silence Alarms, Messages, Calls, Notifications & Other Sounds on Your iPhone to Keep Others from Finding It
Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

Android Basics: How to Use the Share Menu
If you're entirely new to smartphones, Android's share menu can seem like a foreign concept at first glance. In reality, it's one of Android's most central and unique features, and with a little experience, it can make your smartphone a lot easier to use.

How To: Your Galaxy Has a Hidden Document Scanner Built in — Here's How It Works
Android's de facto document scanner is Google Drive, but it's far from the most intuitive method. With One UI 2, your Samsung Galaxy device now has a document scanner built-in, with the ability to automatically detect documents like letters, business cards, and notes that you can scan with just a tap.

Outlook 101: How to Protect Emails with Face ID or Touch ID Security on Your iPhone
Your email is just that — yours. You shouldn't have to worry about other people gaining access to it on your iPhone. Fortunately, Outlook agrees, and has included a way for you to protect your messages with one of two keys no one possesses but you — your face or fingerprint.

How To: Set Up Google Voice to Get Visual Voicemail on Your Unlocked Android Phone
Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices access to their visual voicemail apps. For that, there's Google Voice.

How To: Hide What You're Listening To on Spotify So Your Friends Don't Make Fun of You
There's nothing wrong with indulging in guilty pleasures on Spotify every once in a while — we all need a little Coldplay and Creed in our lives. The only problem is, all of your friends and family might be watching. Anyone that is following your Spotify account can potentially see what you're listening to, but there are several ways to hide this shameful and embarrassing activity from the world.

How To: Take Control of Sonos IoT Devices with Python
Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

How To: Make Delicious Thai Sticky Rice Without a Steamer or Rice Cooker
If you're a fan of Thai food, I'm sure you're familiar with sticky rice. There is something so special about its chewy texture and sweet flavor. If you have a desire to make it in your own kitchen but don't have the proper tools such as a traditional bamboo basket or stackable steamer, there are several other methods that work just as well. Once you try these alternative methods, I'm sure you'll be "sticking" to them for a while. What Makes Sticky Rice So Sticky?

How To: The Simple Trick to Stop Your iPhone from Automatically Going to Sleep
You're halfway through reading an article on your iPhone, when the display just turns off. Frustrated, you open the article again, only for the display to go black again. You shouldn't have to keeping touching the screen to keep your iPhone from going to sleep. Luckily, you can delay or even stop your iPhone from doing so with just a few taps.

Decoding Produce Stickers: The Hidden Meaning Behind Fruit & Vegetable Labels
Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...
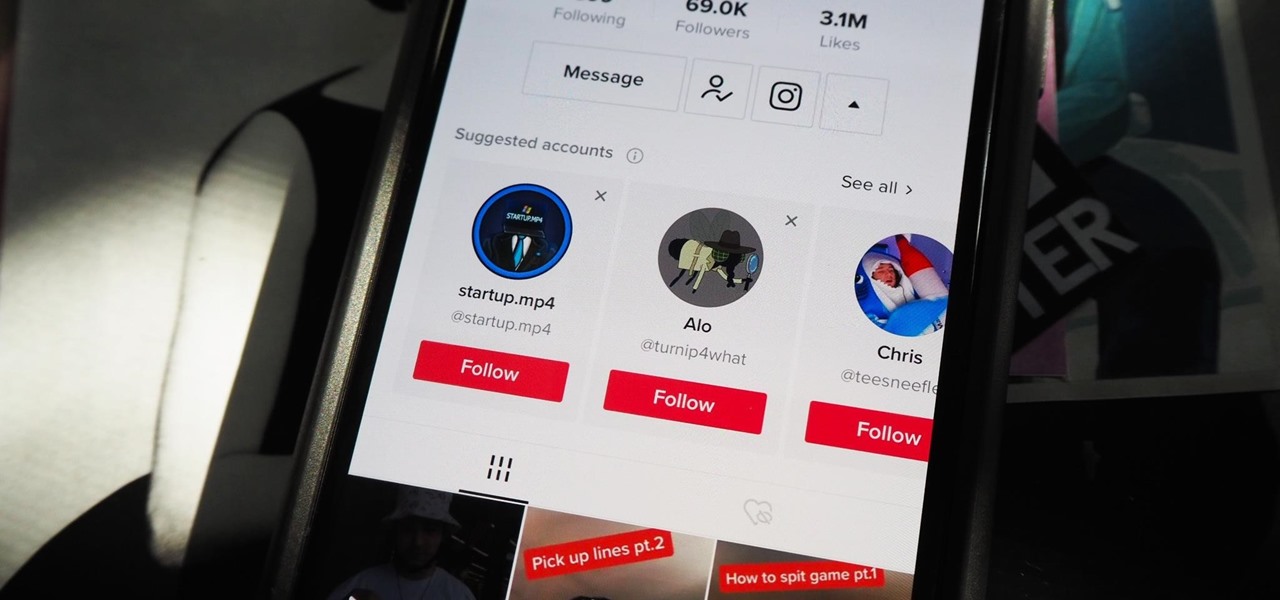
How To: Stop Your TikTok Account from Being Suggested to Contacts, Facebook Friends & Other Users You May Know
Your TikTok videos might be interesting, creative, fun, and appealing, but that doesn't necessarily mean you want the entire world to see them. While you're fine with strangers watching your videos, you may not want your close friends, family, and coworkers to see the kinds of mischief you're up to.

How To: 9 Ways to Earn Google Play Store Credit and Discounts for Apps, Games, In-App Items, Movies, and More
There's more than one way to get free credits and discounts in the Google Play Store for apps, games, books, movies, in-app items, and other Play Store content. You may know a few of them — but some of these may surprise you.

How To: Unlock Facial Detection & Recognition on the Inexpensive ESP32-Based Wi-Fi Spy Camera
If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

How To: The Best Way to Send High-Quality Videos from Android to iPhone
Being an Android user and having friends who are in the Apple ecosystem does not need to be a pain. You can easily send high-quality videos to iPhone users, so don't feel handicapped without access to iMessage. Sending high-resolution videos to iOS users is easy with this fast video-sharing method.

Tutorial: DNS Spoofing
Greetings my fellow hackers.

How To: Use Your iPhone or Apple Watch as a Remote Control for Your iPad Using This Hidden Built-in Feature
There's a hidden feature on iOS that will turn your iPhone or Apple Watch into a remote control for your nearby iPad or other Apple devices — and it's nowhere near as complicated as Switch Control.

How To: Hack Apache Tomcat via Malicious WAR File Upload
Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

How To: 15 Ways Apple Messages Makes Texting and iMessage Even Better on iOS 18, iPadOS 18, and macOS 15
Apple's Messages app already has a ton of great features, from audio message transcriptions to message editing and screen effect triggers. But there are some important new changes to go along with the newest software updates for iPhone, iPad, and Mac that make Messages even better.
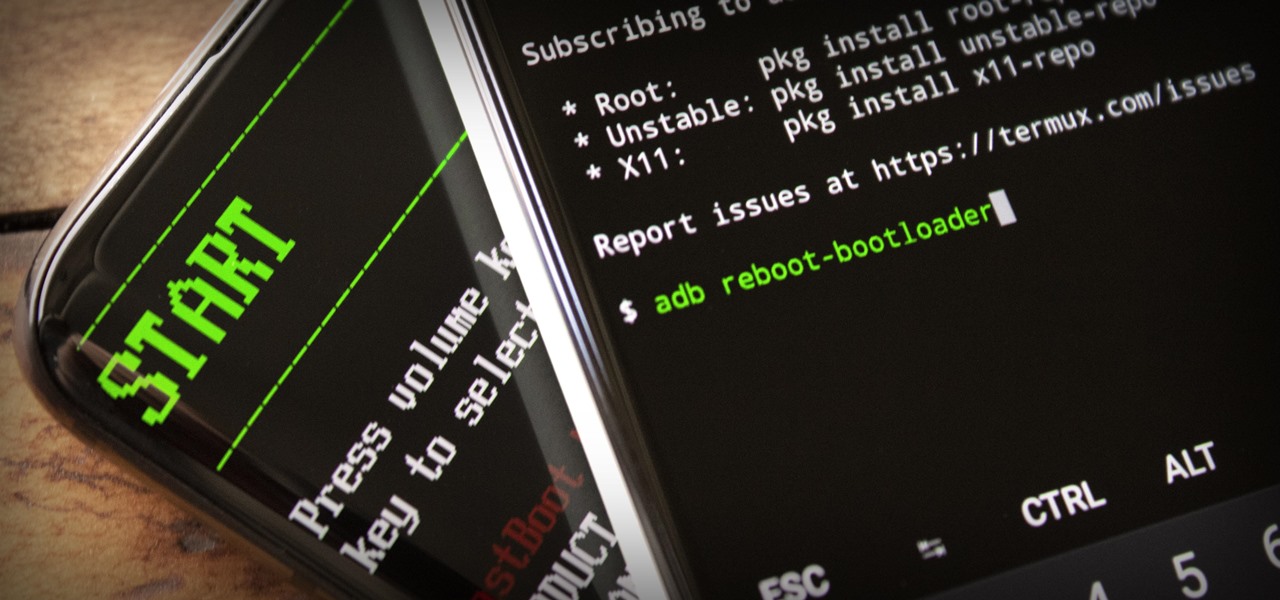
How To: Send ADB & Fastboot Commands from One Android Phone to Another
ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone.






