If you are one of those individuals that are looking to enhance your Frisbee abilities, this video series is perfect for you. Steve Blank shows you how to do a variety of throws and catches. He shows you traditional Frisbee throws.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Blowing dust and fungal spores are creating a public health problem that could be just a slice of what's to come with climate change.

Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

Welcome back, my rookie hackers!

Though many students spend four years of high school learning a foreign language, most of us probably retained very little. Chalk it up to the carelessness of youth, but chances are you've since been in situations or places that left you wishing you paid more attention in class or had continued practicing long after you graduated.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

When Snap CEO Evan Spiegel pulled off the surprise debut of the augmented reality version of Spectacles last week, it was one of the biggest moments in the company's history.

Commenting on Facebook pictures is a commonality. But you may not want to share your private and personal pictures on Facebook. Maybe you just want a select few to comment on your photos. Fear no more, you can send your pics and get private comments using Google Photos.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

The more impressive demonstrations of the capabilities of augmented reality add another dimension to what we see in the real world.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

Adidas' new app All Day isn't going to be your average fitness app. Oh no, the company had the "versatile athlete" in mind when it came to creating the well-rounded program that not only encompasses fitness, but also provides nutrition plans, encourages a balanced mindset, and makes sure you get an adequate amount of rest.

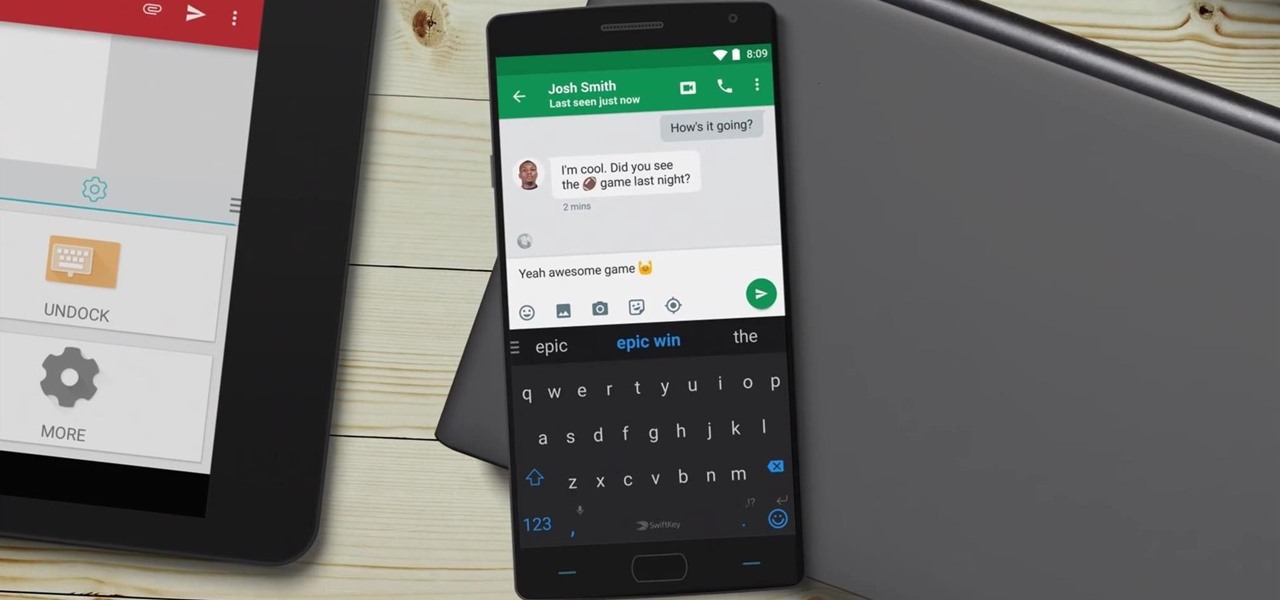
Microsoft announced Wednesday morning that it has entered into an agreement to acquire SwiftKey, makers of the SwiftKey predictive keyboard and its SDK that runs on over 300 million Android and iOS smartphones, for about $250 million.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

YouTube, the popular video streaming website owned by Google, announced on October 21st that it will be launching a new subscription service titled "YouTube Red" for $9.99 a month. Under the membership, subscribers will be able to watch videos without ads. Yup, all videos—from music to trailers to gaming and everything in-between—completely ad-free. Additionally, individuals can save videos to watch offline on their mobile devices as well as play videos in the background.

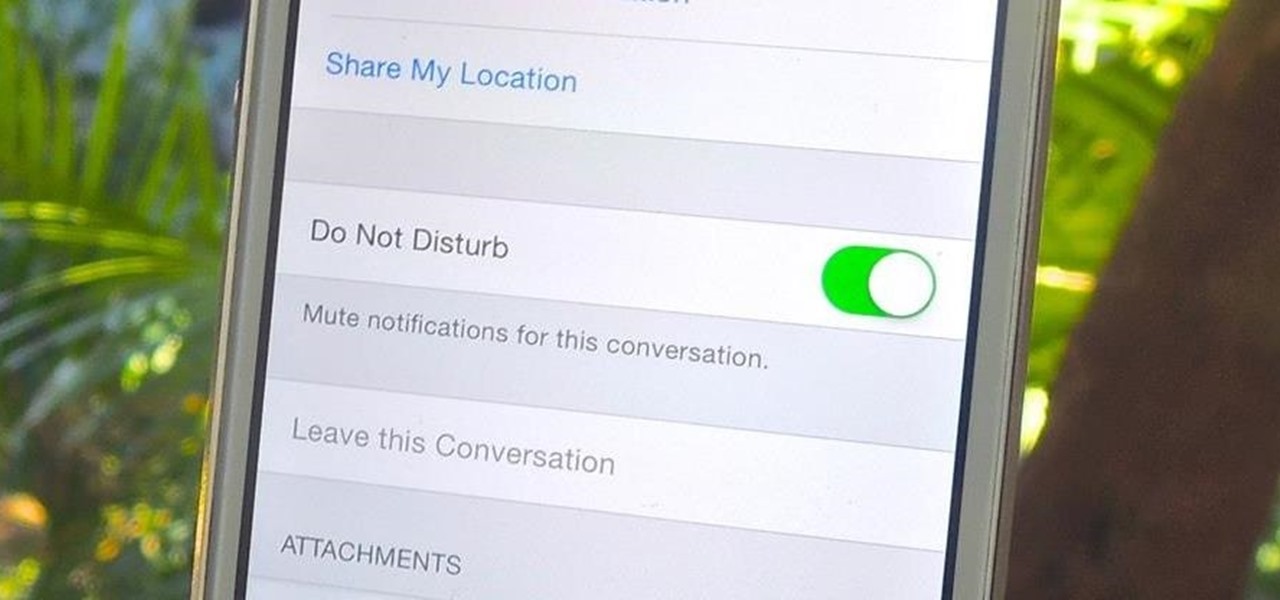
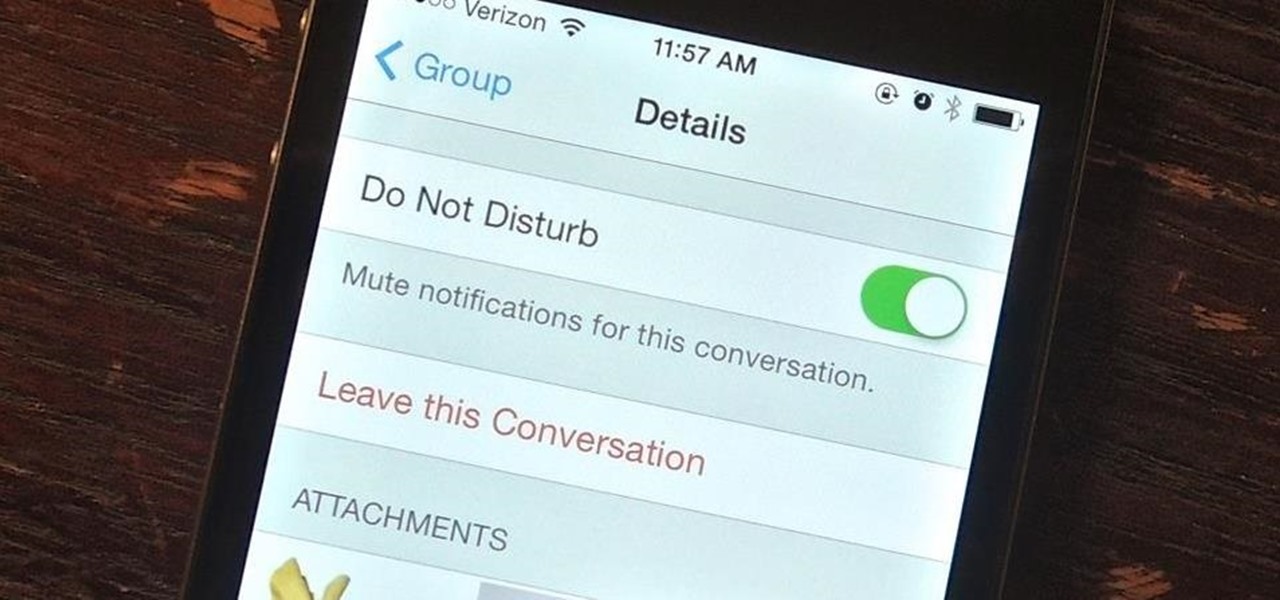
As hilarious and fun as group messages can be on your iPad or iPhone, they can also be equally annoying. You may not necessarily want to leave a group message thread, but you don't want to be bothered by notification after notification as participants in the conversation continue to send out rapid-fire texts. Thankfully, one of iOS 8's new features now makes it extremely easy to mute notifications from specified conversation threads, single or group.

Group messages make for some hilarious conversations with your friends, and are also a great way to update multiple people without sending individual text messages. But as awesome as they can be, they can also be as equally annoying.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

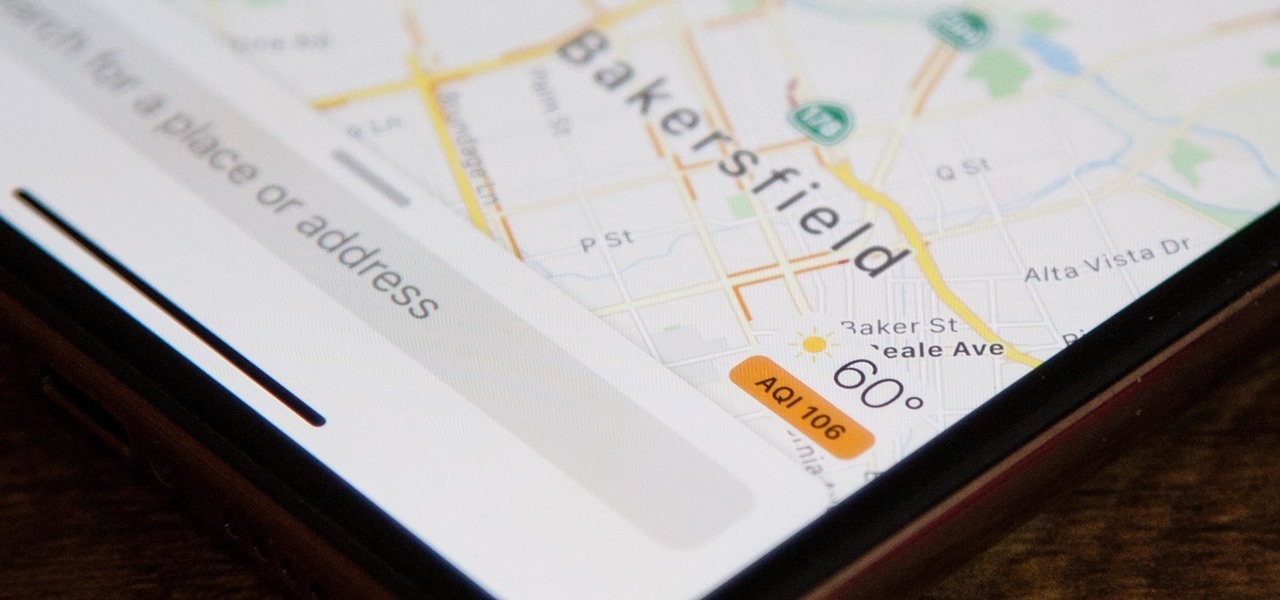
While the United States, in general, doesn't have the worst overall pollution, the air quality can drastically change from one day to the next. If you're particularly sensitive to pollutants in the air, there are apps that show how clean or polluted the air is in your area, as well as in cities you plan on traveling to, but Apple's making those apps less relevant with a new feature in Apple Maps.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.

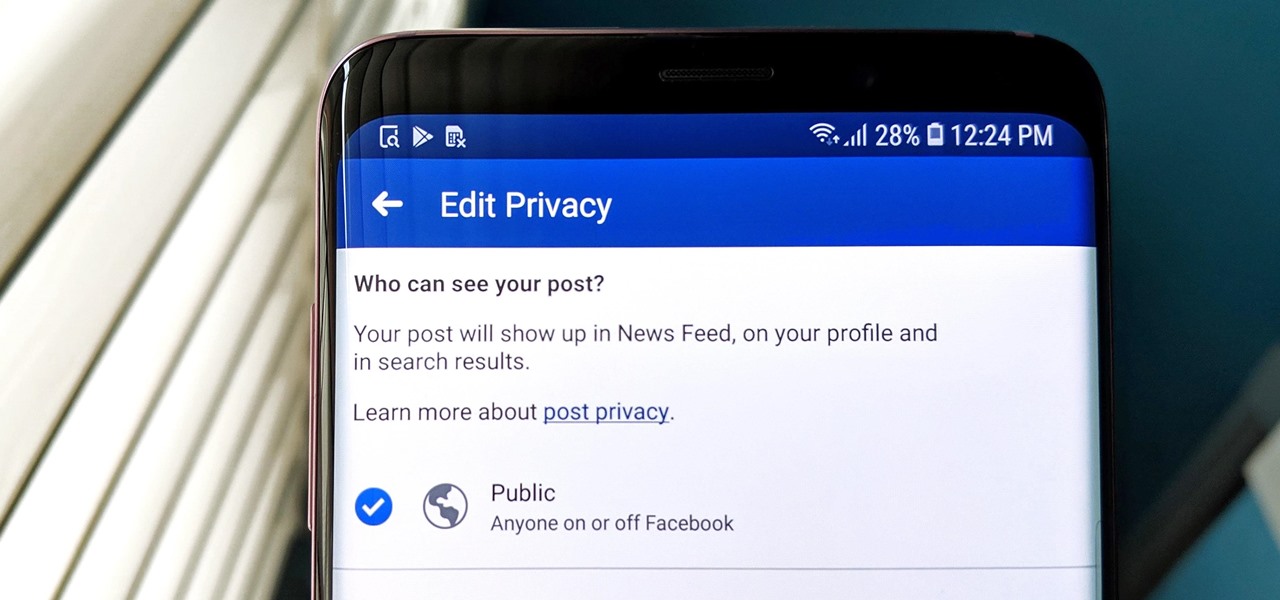
Facebook has grown into one of the central hubs of the internet where ideas are shared with others. But with the rise of brand development, individuals and companies need to get their messages out beyond their group of Facebook friends so it can be seen by more of the world.

They say a picture is worth a thousand words, but augmented reality is giving the United States Holocaust Memorial Museum the ability to add a few more poignant real words to its exhibits.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

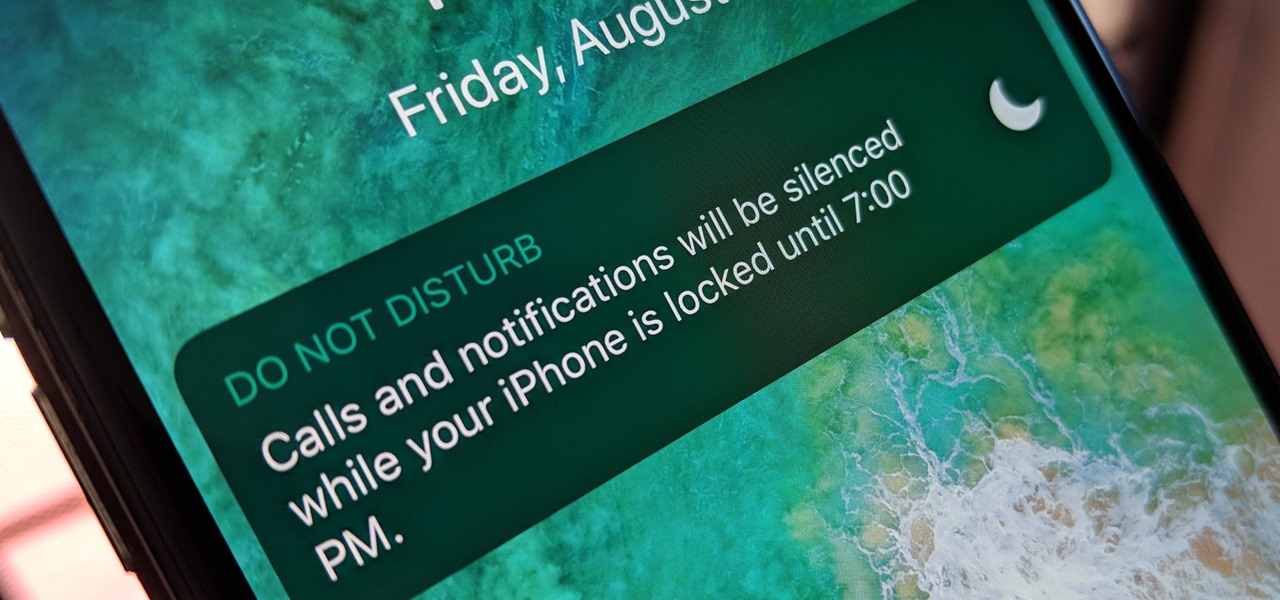
Included with iOS 12 is an easier-to-use Do Not Disturb mode. Not only is there a new Bedtime Mode that makes waking up less annoying, but also new ways to quickly launch the DND temporarily. One example is having the ability to set Do Not Disturb based on a time of day — specifically, morning or evening.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

When it comes to augmented reality smartglasses, for now, it's still a mostly enterprise world, since the form and function of most are more acceptable on a job site versus your local cafe, and the still high price tags are far more palatable to major companies rather than individuals.

Jay-Z's Tidal streaming service provides Hi-Fi music to a mainstream audience. Even better, Tidal can do this without blowing out your eardrums, because it's easy to enable volume normalization so that one track isn't louder than the next.

The standing desk movement has gained momentum over the past few years as research has pointed to the detrimental health effects of sitting at a desk all day.