Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

One of my favorite things is finding an easy way to make what is normally a complex dish. Case in point: pasta sauce. Usually its depth of flavor is the result of fresh herbs, shallots, tomatoes, seasonings, olive oil, and a touch of dairy being cooked and added in stages. Long simmering mellows out each component's inherent character and turns pasta sauce into something that is far greater than the sum of its parts.

In case you haven't heard, chia seeds are off of the novelty plant grower and in your supermarket. Why? Because they're a nutrient-dense food loaded with calcium and fiber (18% and 42% respectively of your RDA per one ounce of seeds). There are even some preliminary studies that show chia might be useful in combating diabetes.

If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Can you cook a steak or salmon filet that's straight out of the freezer and get good results? Ordinarily, I would say no. Usually your steak ends up a sad grey mass fit only for the family dog and the fish is burned on the outside with an icy, undercooked center.

If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.

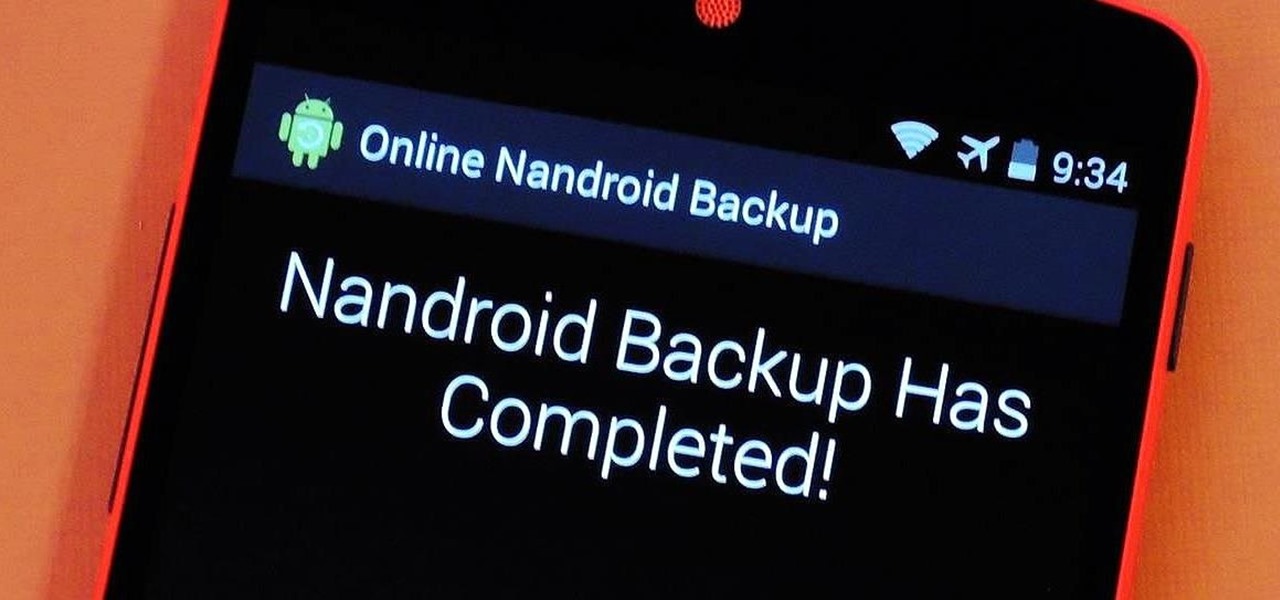
If you have a custom recovery installed on your Android device, the first thing you should have done as soon as you finished installing it was to create a Nandroid backup. But if you didn't, I'm not here to judge—I'm here to show you a much easier way.

Certain ingredients that a professional chef might work with in a restaurant-style setting may seem bizarre, dangerous, and even downright scary to a home cook, and for good reason.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

Brining is magic. All you have to do is make a mild saline solution, toss in your protein of choice, let it soak, and cook. You end up with incredibly tender, flavorful meat or tofu for very little effort. So why aren't more of us doing it?

Safari has some cool new features in iOS 8, but the app that seems to have gotten the biggest update so far is Messages. A lot of the new Messages features were discussed during Apple's developers conference, but we found many others and picked out our favorite hidden ones below.

The Moto X introduced tons of cool features that have slowly been ported over to other phones, like Peek notifications and always listening "OK, Google" detection. Another such feature allows you to twist your wrist to bring up the camera app from any screen—even with the display turned off.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

It's one hell of a device, but the Samsung Galaxy S5 is still susceptible to the many hazards that other smartphones are prone to: theft, cracked screens, poor battery life, and particularly, overheating.

When I first started cooking, there were a few steps I always skipped in recipes. I never added zest to anything because it seemed like too much trouble, I rarely separated wet and dry ingredients in baking recipes because I was lazy, and I never let meat rest after it was done.

If you drop your smartphone in water, take it apart as much as you can and place it in rice. It's been the most recommended method of cell phone rescue since the days of clamshells. In fact, it's usually the only thing recommended when searching for "how to save your wet phone." Turns out, we've been wrong all along.

I used a plastic water filter for years. Who wouldn't? It cuts down on buying bottled water, which, as it turns out, is pretty much the same as unfiltered tap water. Plus, bottled water is terrible for the environment and your wallet, too. Water that costs only pennies a day and actually was purified as opposed to just saying it was? That's a no-brainer.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Food is a necessity, sure, but every now and then it's so satisfying to eat something because it is fun and delicious. While eating a whole tub of homemade ice cream might satisfy your need for gluttony, there's a way to take it even further—make your dinnerware edible.

In today's dog-eat-dog world, every minute matters. Whether you're in school or working for the Man, a huge amount of your day is consumed by tasks, assignments, and other kinds of work. Then there's the time you spend playing video games, watching TV, or screwing around on your Samsung Galaxy S3.

While we've already covered several good ways to tame the itch of a mosquito bite, you're much better off preventing them from biting in the first place than dealing with the itchy aftermath.

We've all been there. Stranded in a large lot or parking garage, braving the rows upon rows of identical cars in an endless concrete landscape because, for the very life of us, we can't remember where we stashed the very ride that brought us there.

There's nothing better than real, homemade tomato sauce, but to really develop the flavors, it usually has to simmer for a few hours. And while it's totally worth doing if you have the time, some nights it's just not an option. That's where the pre-made stuff comes in. Jarred pasta sauce certainly doesn't taste the same, but it's really easy to dress up when you need something quick. If you don't want anyone to know your "secret recipe," here are 10 ways to make store-bought spaghetti or mari...

Nintendo fans rejoice! Not only can you play classic NES games on your iPad or iPhone without jailbreaking, you can play Game Boy Advance and Game Boy Color games. And that's not it. Now, thanks to @angelXwind, we can add Nintendo DS to our list of non-jailbreak emulators for iOS 7.

The Problem If you are working on a car restoration project, then you are going to faced with rust damage. This problem can’t be overlooked, as the entire project depends on repairing and eliminating rust. This would be like laying down new carpet to a house that was flooded, without cleaning the mess and making necessary repairs before laying the carpet down. The problem will still be there and the new carpet will be ruined.

Android developer Roman Nurik, famous for his open-source DashClock widget, recently released his latest creation, Muzei Live Wallpaper. Now, live wallpapers (LWPs) may not seem like a huge deal as far as mods go, but they're a great way to add flair to your device—and Muzei adds it in spades.

Valentine's Day is a day for love, but it also just happens to be the time when every flower shop in town hikes up their prices. Chocolates are still relatively cheap, but I never understood why you have to give the gift of bigger love handles when something more creative gets the job done at a much cheaper price.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Not having power can make everyday tasks really difficult if you're unprepared. You have to find new ways to do things like cook dinner and charge your devices, and if it happens during the winter, you also have to figure out how to heat your home.

Smartphone users these days can get bombarded with texts and emails every hour. Online retailers sending you coupons to get you to buy stuff. Girlfriends asking where you are. Service providers reminding you to pay your bills on time.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

Some women see Halloween as a once-a-year opportunity to dress in something skimpy without dealing with as much scrutiny as usual. That can be fun, but not everyone is comfortable enough wearing so little, and the costumes are so boring and repetitive. Some of us just don't feel like freezing.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

While Siri has never been my favorite, after using her in the new iOS 7, I have definitely become a fan. If you want to know why, check out the newest cool features that Siri has to offer!

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.