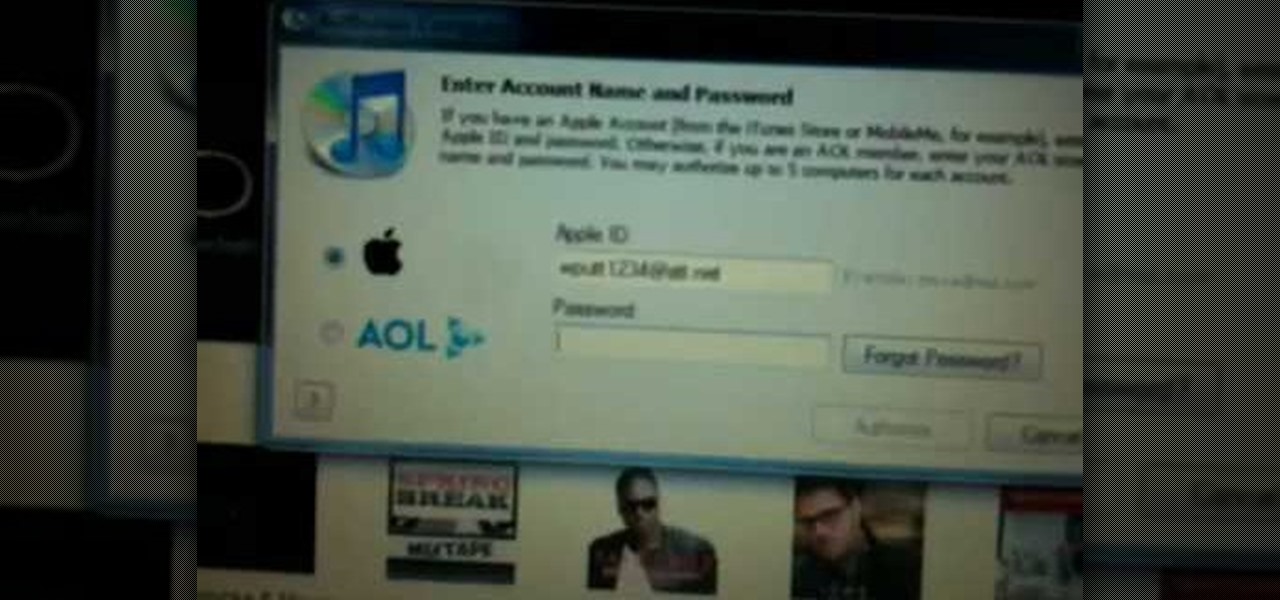
In this video from wadeputtii we learn how to authorize or de-authorize a computer on iTunes. Go to iTunes, sign into your account. Now click on Share and you will see Authorize Computer or Deauthorize Computer. If you want to authorize, click on that and enter your apple user email address and password. Then click authorize. If you have a new computer or you want to prevent someone else from using your account on your computer and you want to deauthorize your old computer, go to Share and De...
Authorization allows you to copy your music store purchases to other computers and burn them to CD and protects the artists. Each computer you use to play your purchase must be authorized using your music store account. You can authorize up to 5 computers; yours is automatically authorized.

You may not realize it but when you buy music or movies from iTunes, you have to authorize it to be used on a computer and you can only authorize five computers. It's pretty easy to buy and replace computers and if you don't de-authorize the old ones, one day you will download a song and it will tell you that you have reached your five computer limit. At that point, what do you do if you don't have any of those computers anymore? Now Apple has put a fix in iTunes itself. Go to the iTunes stor...
In late 2012, Instagram CEO Kevin Systrom made a sudden and controversial change to his social media service when he removed Twitter Card support.

A TFU was set up to review Navy service uniforms. This uniform is approved for E6 and below. It will replace the summer white and winter blue uniforms. This is how the female uniform should be worn.

Kelly Campbell explains the disarm while doing gun from behind defense. This time when an attacker is pushing you forward.hing gun from behind at a distance defense. Krav Maga is the same brand of self defense used by Matt Damon in the Jason Bourne movies.

Jarret Waldman explains a simple Krav Maga sweep technique

Krav Maga Worldwide Sherman Oaks Human Weapon Jarret Waldman teaching defense for gun to the head while kneeling executioner style.

A Krav Maga ground fighting technique for a quick release from the guard

Jarret Waldman explains why Imi the founder of Krav Maga uses a single handed defense instead two in other systems for gun from the front attack.

Krav Maga Sherman Oaks Human Weapon Jarret Waldman teaching a choke from behind with a thin wire or rope defense.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

Despite how easy it looks in this video, finding and acquiring this rooftop wanted poster in Mafia II is not a simple task. But, if you're determined to get the wanted poster of drug trafficker Vladimir Semotan (aka Preacher), then follow along the best you can. Geoff and Jack from Achievement Hunter will show you the way to the roof of the Authorized Repair Shop to grab the poster, which will bring you one step closer to the Card Sharp achievement on the Xbox 360.

The ability to see the world around you and instantly share that "vision" is something that makes Google Glass great for everyday use. No reason to pull out your phone to show off the amazing sushi plate you were just served—look at it, give a couple of quick taps and voice commands, and boom, your social network is salivating in jealousy.

This is an electronic travel authorization system used to gain travel authorization to the United States. There are certain countries that fall under a visa waiver program, meaning that you do not need a visa to enter the US to visit. In that case you use the ESTA system. The countries that qualify in the VISA waiver program include Andora, Australia, Austria, Belgium, Brunei, The Czech Republic, Denmark, Estonia, Finland, France, Germany, Hungary, Iceland, Ireland, Italy, Japan, Latvia, Lich...

When it comes to Hi-Fi music streaming services, Jay-Z's Tidal is one of your only choices. But as you can imagine, true High Fidelity audio requires faster download speeds than your average music service. So the question becomes, how do you listen to Hi-Fi tracks on Tidal when a speedy internet connection isn't available? Offline music is the answer.

I am a graphic designer, so I have to collect massive pics from webpages to provide me with inspiration. But sometimes I need to use them everywhere, even if I've no access to computers or laptops, so I have to resort to mobile devices.

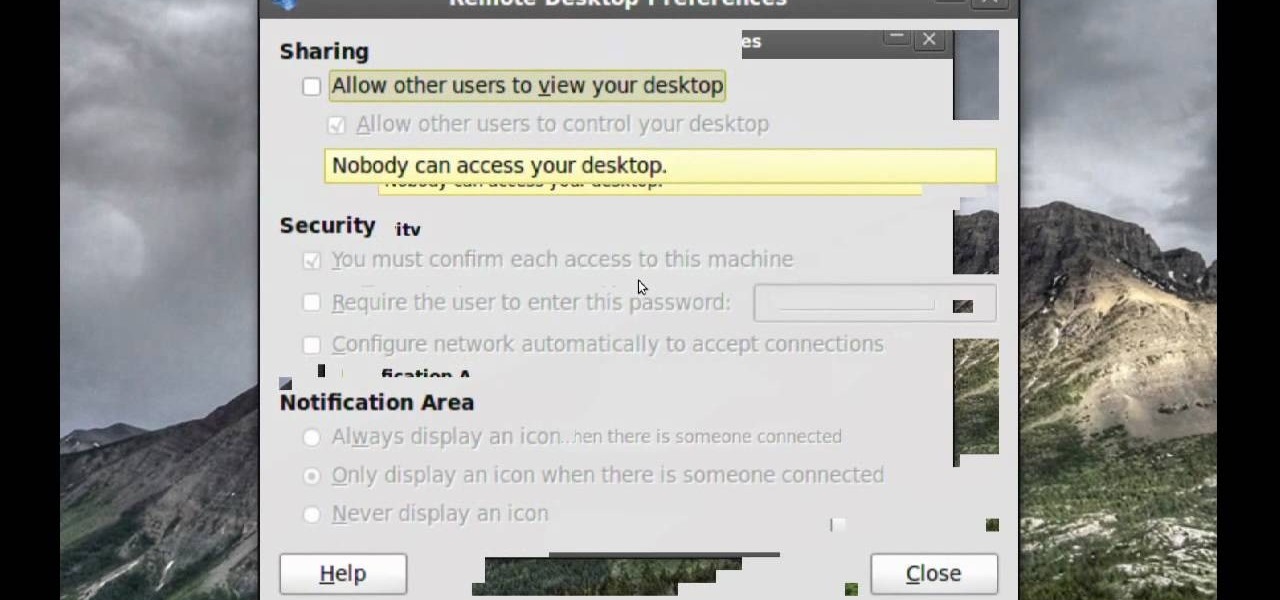
Remote assistance is a feature that, as its name suggests allows a user to remotely control another computer. The user can then use the remote computer in the same way as if the user is physically present there. Most modern operating systems support this feature.

Crakintosh.tk shows viewers how to easily SSH into their iPhone of iPod Touch with an easy method! First, you will need Cydia. Open up the program then go to Manage and click Packages. You will need to click Authorize SSH and Install this. Wait for this to download. Next, go to WinSCP to SSH into your device. The password will be Root and the login Alpine. Once you do this, you can now view all of your files and really do what you want with them. You have now just SSH'd into your device. This...

ClosetFool shows you how to disable UAC in Windows 7 and Vista. UAC is there to protect your computer by asking if you authorized the program to run or make changes. However, it can become annoying constantly having to click "continue" in the dialog box when trying to run programs. To disable it, first click the start button. Type UAC into the search box. The search should return with one selection. Click on it, and select whichever setting you like. In this video, ClosetFool set it to "never...

For those worried that a lustful gaze at a new app on their iPhone X will authorize its purchase, we have great news for you.

It really is a pain getting an Apple device fixed ... What's a gal to do when there's jelly stuck in your Macbook Pro fan and no Apple Store in sight? (Yes, this actually happened to me. Stop laughing.)

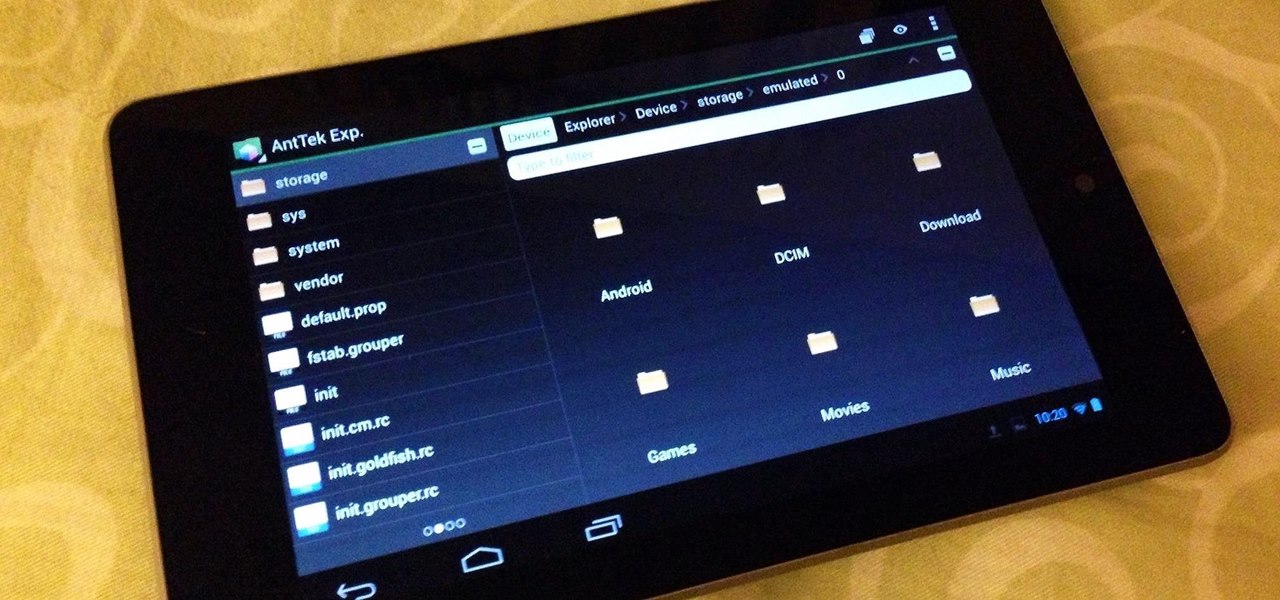
If you're always on the go, the Nexus 7 is a godsend for having everything you need at the tip of your fingers—music, videos, text documents, photos, and more. Unfortunately, as good as that is, it also means one hell of a messy tablet.

Apple released the third public beta for iOS 13.5 today, Wednesday, May 6. This latest public beta update comes exactly one week after Apple released iOS 13.5 public beta 2, which, among other things, introduced Apple and Google's joint COVID-19 exposure notification API. Public beta 3 updates that settings page to show a more detailed "Exposure Logging" option instead.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

It's been a rough week for Instagram. First they came out with a new terms of service that suggested the right to let companies use people's photos for advertisements without the user's permission. Then everyone started freaking out and debating whether or not to leave the online photo-sharing and social networking service. Now, they've changed the controversial wording saying that the selling of user photos "is not true and it is our mistake that this language is confusing".

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

After the lackluster update that was iOS 13.3.1, we beta testers were in need of some excitement. Thankfully, Apple delivered the goods with iOS 13.4 developer beta 1, introducing fun new features like fresh Memoji stickers and a new Mail toolbar. Of course, that update was for developers only, so we public testers are thrilled that Apple just released the first public beta today.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Replacing your iPhone fingerprint sensor has been one of Apple's most cruel tortures. It's a slow and painful process made worse last year when Error 53 messages started appearing on the phones of users who had tried to repair their sensors outside of Apple. The error rendered the phones essentially useless. Since then, Apple has provided fixes but is now finally making it much easier to replace your iPhone fingerprint sensor with the releasing of "Horizon Machines" to official repair locations.

Since the days of Friendster and MySpace, social media platforms have taken leaps forward, revolutionizing how we live our lives by changing the way we communicate with others. Not only has social media become a catalyst for major uprisings around the world, but on a personal level, it connects people together in ways that were unimaginable even 10 year ago—no one was taking pictures of their brunch to share with the world in 2004.

This video is provided by "Betty Sell" from AAA travels. In this video she tells about the international travel and also about the important documents to be carried while carrying out an international travel, that is the international driving permit, commonly called as an IDP. It's very important to carry an IDP while traveling overseas because an IDP acts as an important recognizable form of photo identification which helps us to communicate with foreign authorities. To get more information ...

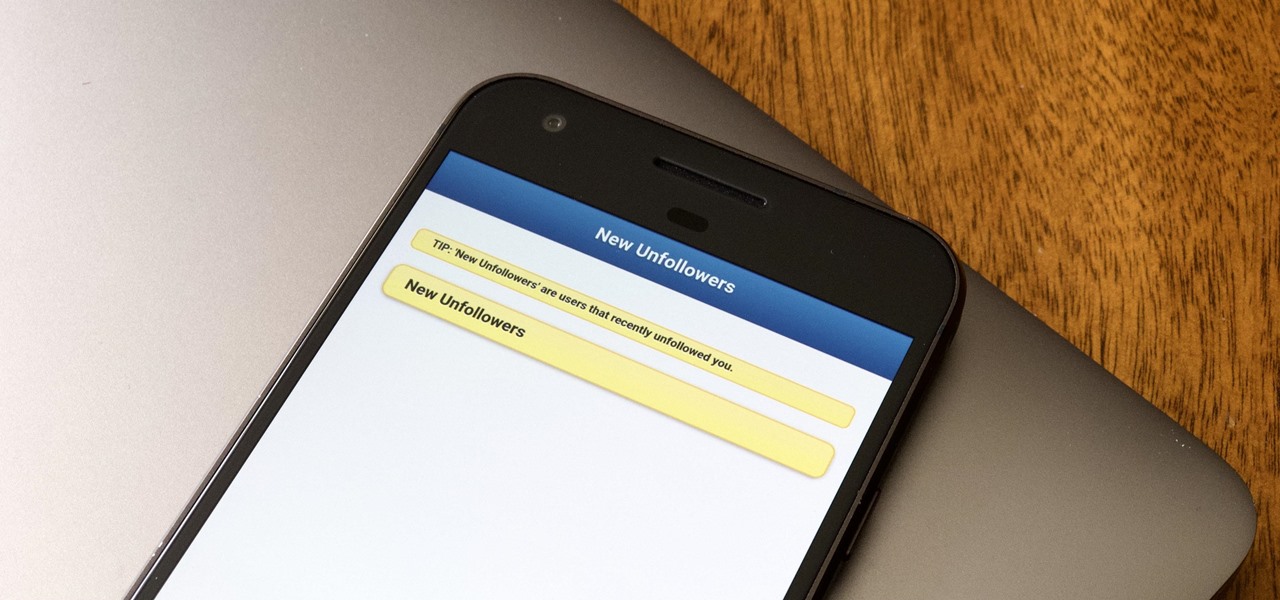
Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

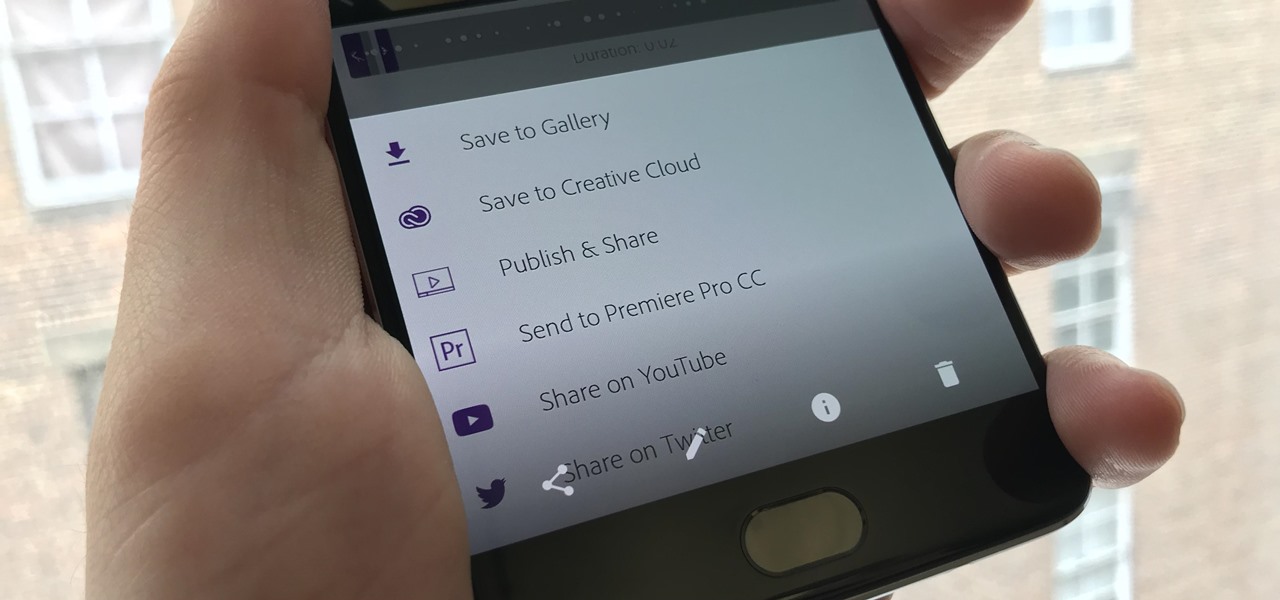
If you've taken the time to edit a video on your iPhone or Android phone, you probably have a purpose for it. Maybe you want to share it to YouTube in hopes of making the next viral sensation. Maybe you just want to save the video to your phone to show off to friends and family when you can.

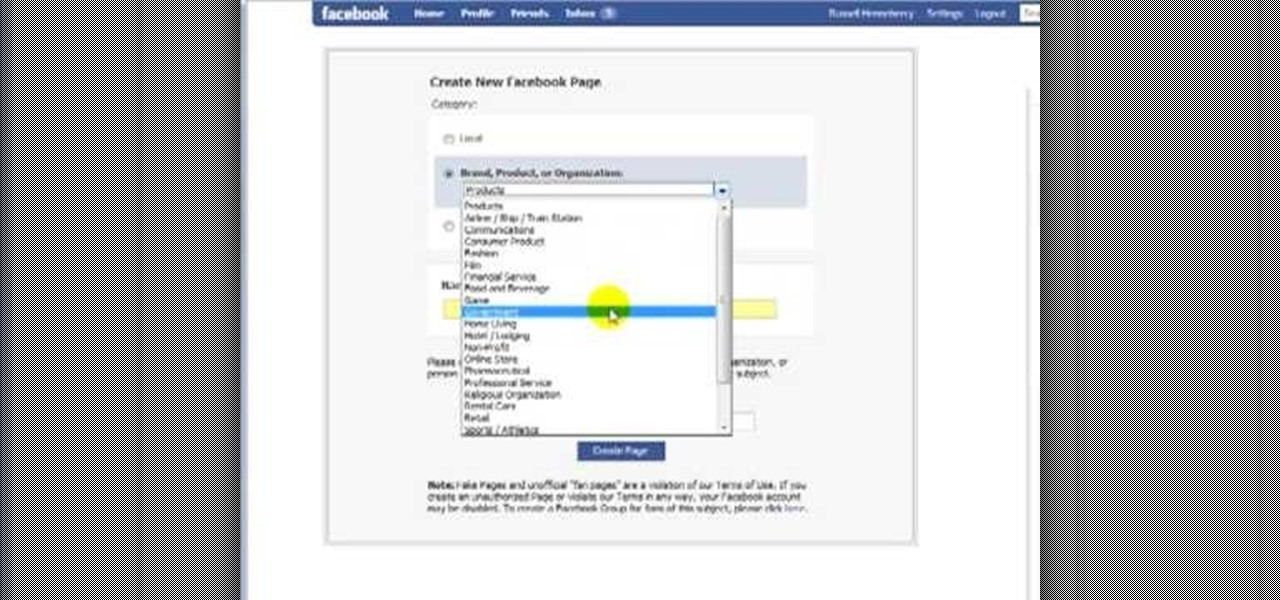
First, you must log on to your personal face book page or create one if you do not already have, but don't log in yet. Then at the bottom of the face book home page click the click here sign within the words to create a page for a celebrity, band, or business click here. Now that you are on this page log in. You will be able to select what you are. Enter name of your website, now select that you are authorize to create this page. You must then enter your electronic signature, which is the exa...

A Facebook page formatted specifically for non-profits can be created in a matter of minutes with this video tutorial from John Haydon. The first step you need to take is to search for any page. In this tutorial, Haydon searches for the page "Facebook Pages/Public Profiles" to use as the example. On the bottom left (of any Facebook page), you will notice that there is a link for "Create a Page for My Business." Click on that link, which allows you to begin the page creation process. Non-profi...

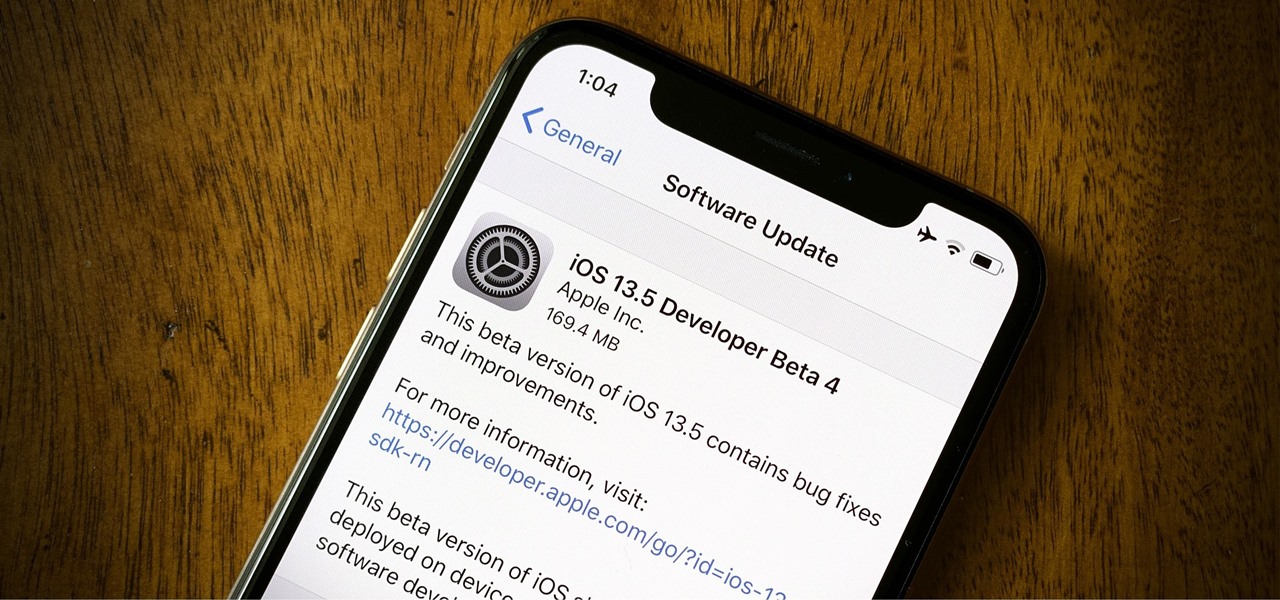
Apple released the fourth developer beta for iOS 13.5 today, Wednesday, May 6. This update comes one week after the release of iOS 13.5 dev beta 3, which introduced Apple and Google's joint COVID-19 exposure notification API to iOS for the first time. Apple updated that settings page to now include an "Exposure Logging" setting instead.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Flickr is the most known and dependable photo sharing website to date, so if you haven't made an account yet, you better now, if you want to share your precious photos with family, friends, and even the whole world! Flickr allows you to store digital photographs online and share them with other people.