Apple recently scored a patent (number 9,488,488) to create augmented reality maps, hinting at possible AR integration into the iOS Maps application for iPhone. Does this mean we'll be seeing super visionary projections of places in the app in the near future? Maybe.

Kentucky Sen. Rand Paul will accept a speaking slot at the Republican National Convention in Tampa later this month, along with Jeb Bush, Rick Santorum and Oklahoma Governor Mary Fallin, according to a senior GOP official. » Rand Paul Granted Speaking Slot At GOP Convention.

November 11th isn't just Veterans Day— it's Origami Day in Japan, where they celebrate the traditional art of paper folding. November 11th is also the last day of World Origami Days, a 2-1/2 week celebration held internationally.

This tutorial will show you how to make origami cranes, one of the most popular and elegant origami shapes. The folds are a little complicated for beginners to learn, but once you've completed one, the next will be much easier. An ancient Japanese legend says that if you fold 1000 cranes, your wish will be granted. Why not try it, and see if it's true?

Electrical sockets are often taken for granted. It's not until one of them breaks or stops working and our laptops won't turn on that we truly have a crisis (mostly over lost internet time).

These days you can get a car tailored with special gangster rims, headlights, and sound systems, but one of the features of a standard car we all take for granted is power windows. Before those, all we had were frustrating crank-up windows that always got stuck if we didn't add enough elbow grease.

Dear the future Mrs. Brand: Can we be you? You're hot, one of the boys, can rock an olie like no one's business on the skateboard, are a ginormously popular pop star, and you're super funny and intelligent.

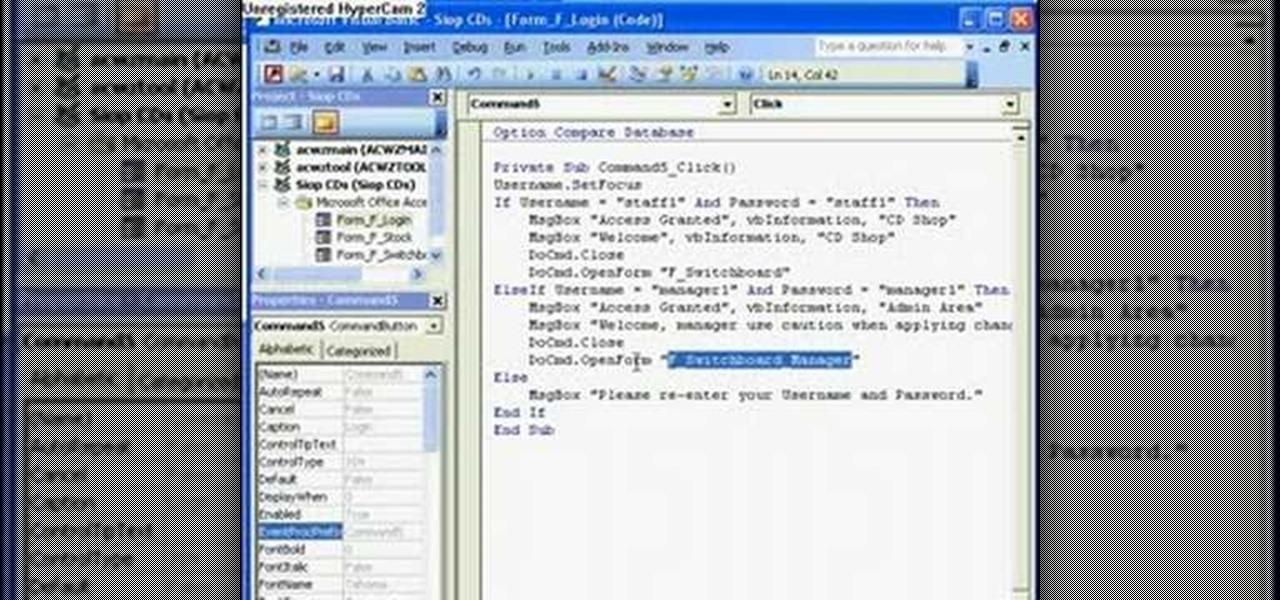
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about creating a multi-user login form to password protect different areas of your database.

Cooking chicken tonight for dinner? It may be a dinnertime staple in your home, but you're probably used to store-bought chickens that you store in the freezer. Well, sometimes the best tasting poultry comes from the chickens with their heads still attached… well, at least before you behead it. We're talking fresh meat here, not Kentucky Fried Chicken.

Learn how to play "If I Were A Boy" by Beyoncé Knowles, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Your precious dog can't be a dog without its freedom, and the number one way to make a dog feel its freedom is by giving it unrestricted access to your landscape, meaning— a doggy door. Granted, your pet can't go roaming all across the county, but a dog door is a surefire way to make your canine feel at home.

Make a wish! I wish... I knew how to fold a falling star out of origami. Well, now your wish is granted! This is an easy and fun tutorial that shows you how to fold a five pointed shooting star from origami paper!

Prized by crafty elementary and middle schoolers, the origami flapping bird, or crane, is a relatively simple origami project to complete but requires a bit of origami folding experience beforehand to do well.

inDesign has some hidden special effects that will make your type on a path much more compelling. Granted Type on a Path is not a new concept and has been around in Illustrator for years. However, no other application out there can handle Type on a Path as well as InDesign CS2.

In this next tutorial, you'll be finding out how to perform a terminal double hack in the game. This is pretty difficult to achieve, but will give youa shot at double credits.

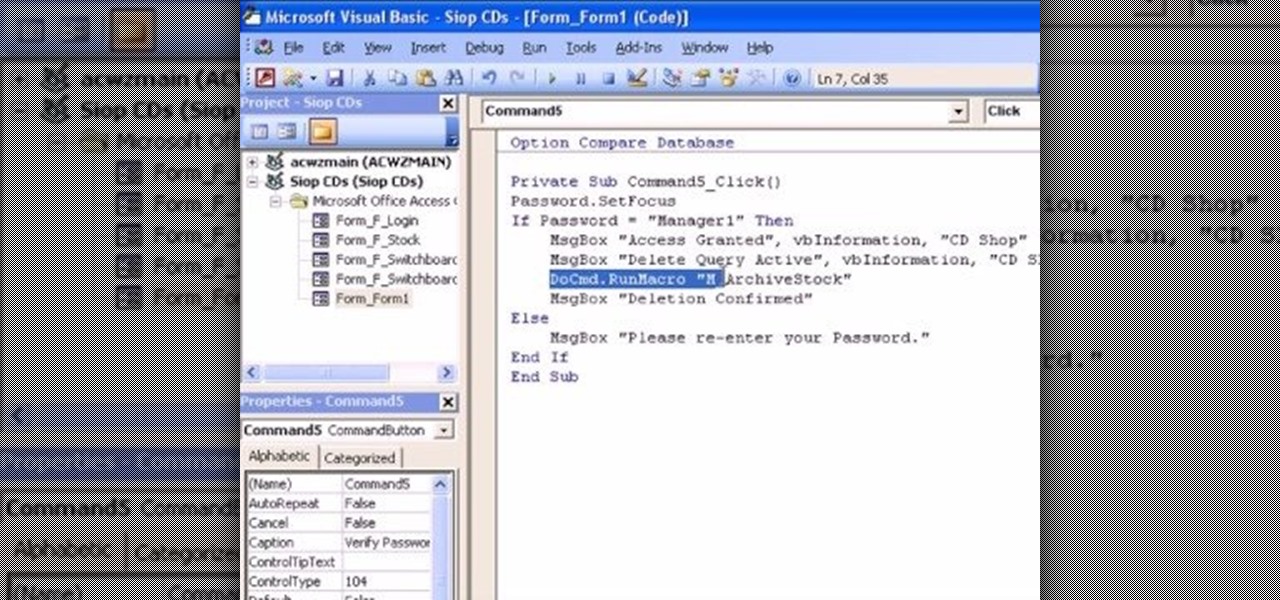
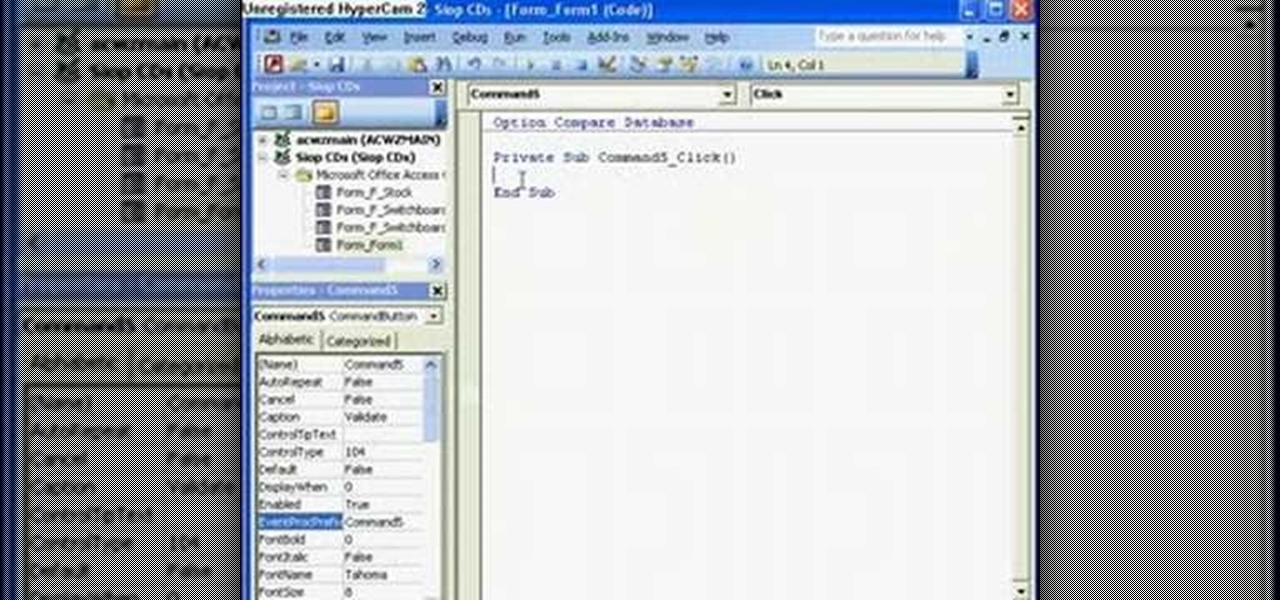
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn how to force a password to be entered in order to run a query.

The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about creating a login form and password protecting your database.

The CEC, Canada Experience Class, is a new program to help a person who has held residency in Canada gain permanent residency status. The program realizes that, by going to school or living in Canada while working, many people have the skills necessary to make the transition to live in Canada permanently. To qualify for CEC, you must be a temporary worker living in Canada for at least two years with two years of skilled working experience. A second way you can qualify is by being a foreign gr...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

When it comes to dressing up, don't take the shirt for granted. This tutorial fashion video will teach you to dress to kill by picking the right shirt.

If thinking about growing your own Bonsai, remember these are trees. Granted they're miniaturized and kept in small containers but they need to be kept outdoors. One wouldn't bring a Red Maple or Azalea inside, same here. They will require diligent care, they will need to be checked for over or under watering but need to remain outside most all of the year. If a tropical variety - a bright window or greenhouse would be perfect

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

With all the recent activity around augmented reality, the possibilities involving immersive computing and commerce are quickly becoming obvious, and digital payments giant PayPal has no plans to sit on the sidelines

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Make your gadgets magnetically controlled with everyday things. People often take for granted the common items and devices they use in everyday life. Looks can be deceiving. It's not what things appear to be, it's what they can become.

Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new "heads up" alerts, but you can still bring them back.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

The Google Now gesture included in the Google Now Launcher and on Nexus devices isn't something I regularly utilize, and you might not either. There is a way to disable it, which is a good idea if you were executing it accidentally, but what's even better than disabling it? Repurposing it!

After closing its office last year, enterprise AR company Daqri has moved on to the final stage of its lifecycle with the liquidation of its assets.

Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

Oftentimes, seemingly insignificant, nondescript features have the most impact on enhancing our Android's usability. A great example is Nougat's inclusion of customizable Quick Settings tiles, which adds greatly to the user experience by letting individuals tailor their expandable status bars to suit their unique needs.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

Despite its deliciousness, the pomegranate is one of the hardest fruits to eat. Once you cut it open, the seeds are stuck behind a bitter-tasting white membrane, and trying to pull them out with your fingers just results in a huge mess.

I'm sure that there are plenty of people out there who have no idea what a plague doctor is/was, so I'll start with an explanation.