How To: Find and Favorite Songs That Now Playing Identified on Your Pixel
Your Pixel's Now Playing song discovery tool received a few updates in Android 12, and the feature is finally comparable to other music recognition services.

Your Pixel's Now Playing song discovery tool received a few updates in Android 12, and the feature is finally comparable to other music recognition services.
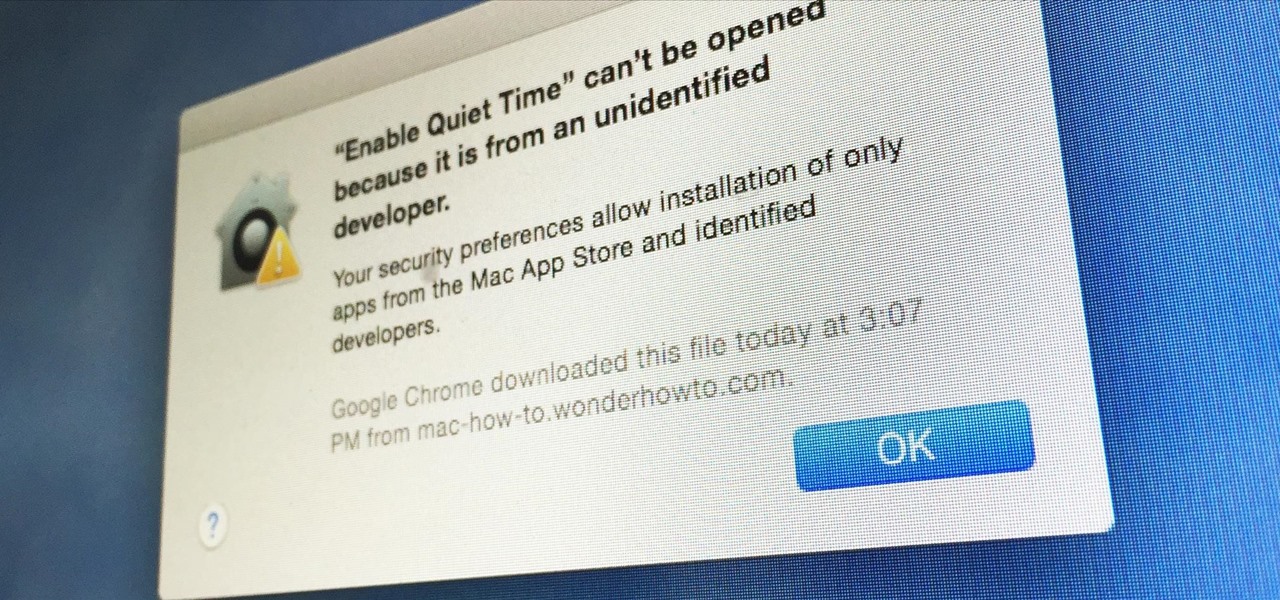
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it.

Check out this video if you are interested in learning how to Jailbreak AND Unlock the iPhone - Firmware 3.0.1 (August 2009).

In this lock picking tutorial video series, I explain and demonstrate how to pick warded locks. Warded locks can be identified by the unique keyway they have. Warded locks use a very simple design. This allows the lock to be inexpensive and minimizes jamming from dirt and grime. Use these lock picking videos to learn how to pick a warded lock.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Chinese chess is the world’s most popular board game. Chinese chess, also known as xiangqi, has been played throughout East Asia for over 1000 years. The playing pieces have traditionally been identified using Chinese characters, so only those who could read Chinese characters could play. Now, Chinese chess is available in a set in which the pieces are identified by symbols on one side and Chinese characters on the reverse side so that anyone can enjoy this challenging strategy game.

This video illustrates the quick and easy method to Identify and control garden pests on grapes and roses . The process is comprised of the following steps:Step 1:Garden pests are quite common in grapes and roses.Step 2: To identify these gardener needs to keep a very sharp eyes on the plants every day. Negligence may lead to disaster of the entire crop.Step 3:Garden pests can be commonly seen on the leaves on inner side or on the shoots of the plant.Step 4:Randomly select the plant and check...

How to identify insects in your gardenCarol Sutherland explains us in this video of how to identify insects in your garden. She is an extension entomologist and she explains her view on the insects here. To be known is that some insects are damaging, some others we want to be aware of and some are necessary in your garden. Here during the garden season you get to see insects on trees as they form a familiar habitat. Mostly on the split ends and the broken ends the insects gets invaded. She sh...
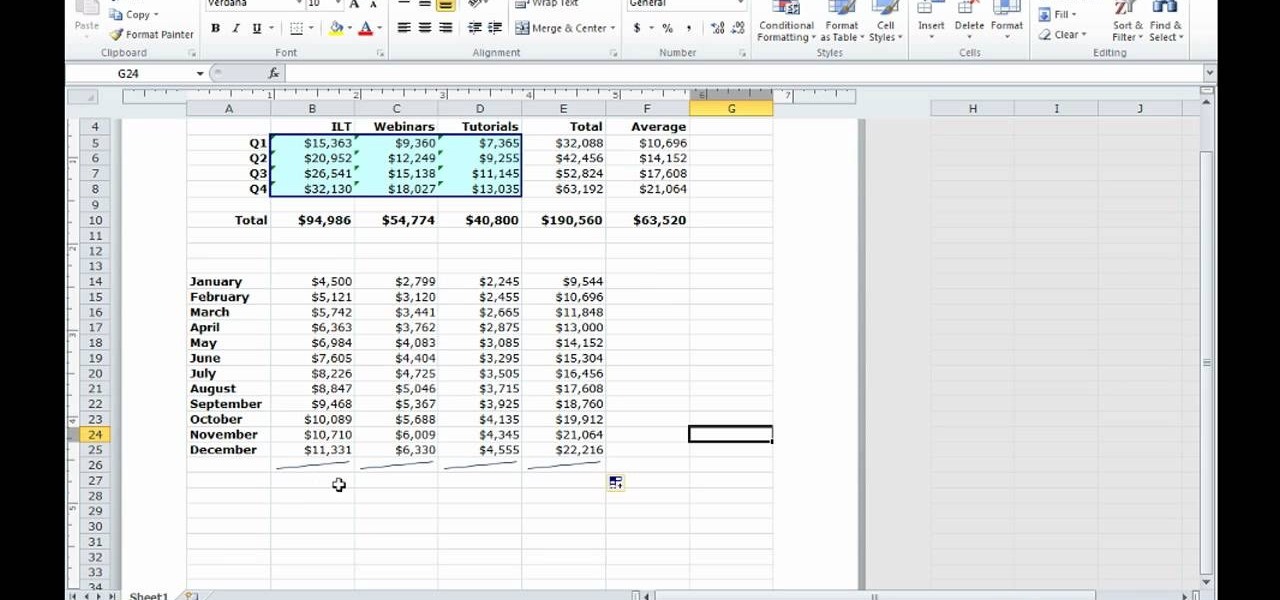
There is a new function in MS Excel 2010 called ‘Sparkline’ which helps you quickly find trends associated with a set of data. To create Sparkline, you can go to ‘Insert’ tab and then select ‘Sparkline’ section and then select the graph type. After you enter the data range and location range, the Sparkline will show up indicating the trend based on the data range you identified earlier. You can change the types and styles of your Sparkline easily. As the video demonstrates, whenever you use E...

This video describes problems with fruit trees and how to deal with them. One problem is Chlorosis, identified by yellowing leaves with green veins between the sections of the leaf. This is caused by a micronutrient deficiency (usually iron) that results when the tree roots are unable to absorb all the nutrients from the soil. This problem can be temporarily treated with a foliar spray of iron. Another problem is pruning wounds with decay that results when trees are not pruned correctly. They...

Master Gardener Rosamarie Maddox asks John White, Doña Ana County Extension Agent, about problems facing her pecans, grapevines, and native shrubs. An unidentified insect found on her pecan tree is identified by John White as a Twice Stabbed Ladybug. This ladybug is a useful insect that often over-winters on the tree and helps takes care of the aphid problems faced by pecans. Pink fuzzy coating on pecan nuts is also brought up. The coating is normal for pecan and contains bitter tannin. Too m...

Snails and slugs can really be a problem sometimes if you are a gardener. They feed on plants and can be considered pests, sometimes even getting inside your house. They are identified by their tell-tale slime trails. A bad infestation can be very hard to deal with. However, specialized cleaners or fertilizers can help your garden snail-free.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

County expert John White determines how to solve some pesky plant problems for the area. The first problem - cutter bees on Crepe Myrtle - is an obvious one, with the deep curved "bites" showing on most of the leaves. He suggests using an insecticide but then points out the signs of a second problem - beetle damage. Crepe Myrtle is prone to beetle infestations and he advises to get out a flashlight and look for them at night when they are at their worst. A problem with heat scorching on Euony...

When you watch the news or a television show where someone doesn't want to be identified, it is common to see the face blurred out or obscured. In this Adobe Photoshop tutorial you will learn how to blur someone's face in an image and preserve or hide their identity. So if you are producing videos or podcasts or need to hide part of an image, this tutorial will show you how to do it in Photoshop.

Being identified as a tourist is generally not a good thing. Here’s how to blend in with the natives.

The video answers questions on whether containerized tomato plant need to be replanted, problems with yellow tips of an oleander and spots on a silver berry shrub. The tomato plant may be replanted in a bigger container and staked/caged to avoid wind damage. If planted in the ground, it is recommended to plant it at an angle, up to the first branches because tomato plants are able to set out adventitious roots. The yellow and brittle leaves of an oleander is also identified as the result of f...

This video shows how to use optimization methods in calculus. Optimization means finding the maximum or minimum values of a quantity or finding when the maximum or minimum occurs.What quantities are optimized in economics?we want to minimize costs or maximize revenue.First steps in any optimization problem1.Identify the quantity to be optimized i.e., read the problem exactly what is exactly maximized or minimized.2.Identified the feasible domain. This is important because the math we can opti...

Learn how to make a delicious Alaskan Sushi Roll with this easy to follow, step by step video. Starting with tasty sticky rice, bring out the various flavors of the different ingredients with an elegant design that anyone can do from the comfort of their own home. The upbeat music will keep anyone entertained as the focus is on the preparation with each ingredient identified as it placed in the assembly. This charming video will help anyone create a striking, tasty treat that's sure to impress!

There are a few differences between bed bugs and bat bugs. The first thing you want to do if you have a infestation is to have the bugs professionally identified because bed bugs and bat bugs look a lot a like. However, there are a few more things that can tell you which type of bug you have. For example, bat bugs like to infest your upper walls, ceiling junctions, and ceilings. Also, these bugs don't bite as much as a bed bug. The treatment for bed and bat bugs can be similar except for one ...
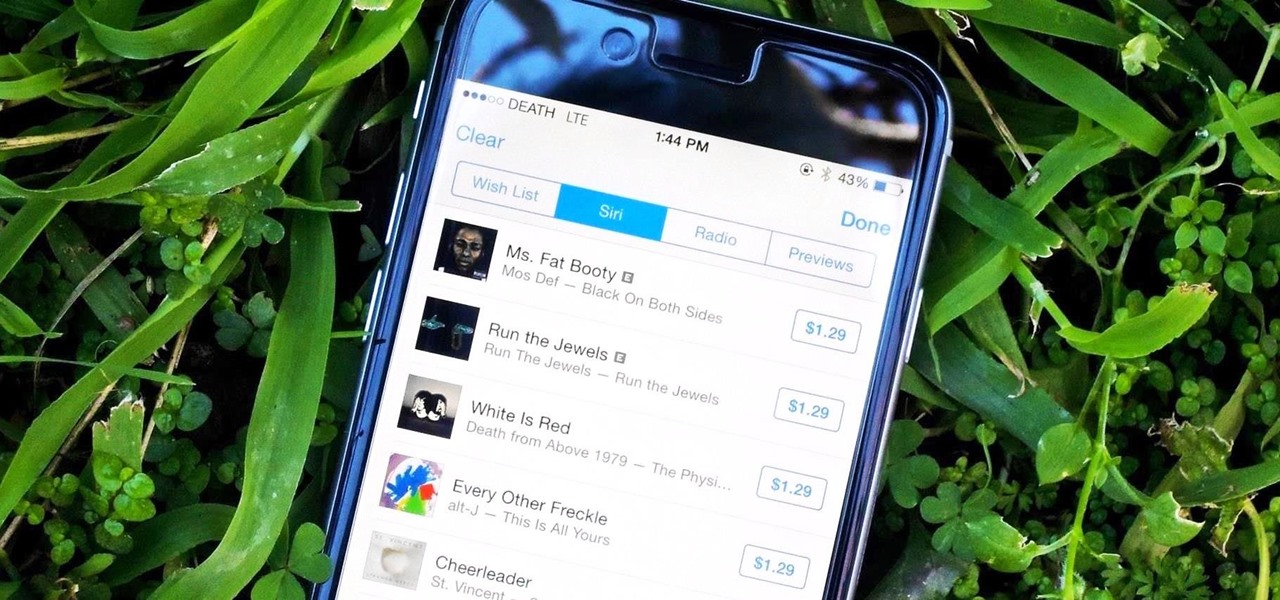
When you hear a song you like but can't quite catch enough of its lyrics, it can be nearly impossible to search for it online. That's where Shazam comes in. For the past decade, they've been making music easier for us to identify by analyzing a track's acoustic footprint, requiring only a few seconds of audio for accurate identification.

The video shows how to effectively be aware and get rid of possible webworms or aphids on your mesquites so they won't get damaged later. Here, John White invited Annete Peterson to show how to do so. She starts by informing from what she saw that many mesquites from her neighborhood have deformed leaves and mainly several of them have stripped branches at the tips of the trees. He explains that one of the problems is a webworm on the leaf of the mesquite, and it eats the leaves of the plant ...

Circuit bending an audio device typically involves removing the rear panel of the device and connecting any two circuit locations with a "jumper" wire, sending current from one part of the circuit into another. Results are monitored through either the device's internal speaker or by connecting an amplifier to the speaker output. If an interesting effect is achieved, this connection would be marked for future reference or kept active by either soldering a new connection or bridging it with cro...
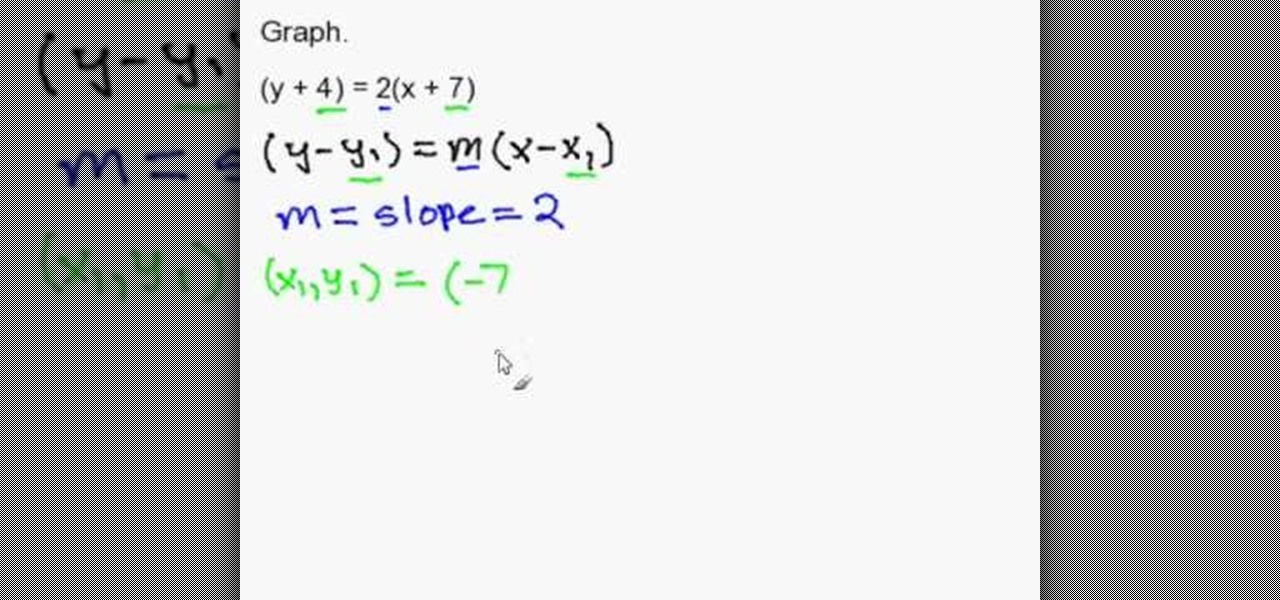
This video tells you how to draft an equation in point-slope form. Consider the equation (y+4) = 2(x+7) for example. The formula for the point-slope form is (y-y1) = m(x-x1). To plot the graph you have to identify m the slope, the x intercept x1 and the y intercept y1. In this equation the slope is 2 and (x1,y1). The x intercept according to the formula is -x1 but the given value is +7 so you have to figure out what will give you +7,only -(-7) can give you +7 so the point is -7 and now the y ...

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

In this video, we learn how to develop a competitive advantage. A competitive advantage answers the question "what are you best at." You just need to better than your competitors at what you do in delivering value to your customers. Think about why your customers buy products from you. If you have the competitive advantage clearly identified, it will get you the customers that you want and keep the customers that you have. Put the competitive advantage together by thinking about the company n...

The main complaint for this 1999 Jeep Cherokee, 4.0L, is that the Low Coolant Light keeps flashing on and that it keeps needing coolant. Nothing seems to be leaking on the ground, so where's the leak going? After doing the normal pressure test to spot the leak, and the combustion gas leak, and the overnight test, nothing seemed to work. The coolant leak could not be identified. So, it must be the cylinder head, right? But you need evidence of that first. Watch and learn how to prove your theo...

If you own a BMW E46, you may have run into a problem with the control arm bushing. This is a frequent problem when dealing with this car, but it can easily be identified. What happens when a control arm bushing fails, is that the actual wheel moves two inches back. This can be dangerous and can easily damage the car. So check out the tutorial above to identify control arm bushing failure in a BMW E46. Enjoy!

In this tutorial, Scott Atkinson shows us how to identify different types of bulbs. Common types of bulbs are: tulip, daffodil and lily. These are most easily identified but there are many that appear in flowers. A core looks similar to a bulb but it is a solid tissue and doesn't have an leaves, just a hard core with a protective covering. There is also tubers which are what potatoes and other foods grow from. These cause eyes to form and create different types of things to grow. You will now...

With rainfall comes unwanted plant growth in the form of weeds. Here's how to identify and control them. First is Nutsage which has a glossy green leaf, triangular stem and the rhizome sends up new plants whenever you cut away at it. Next is jungle rice which is an aquatic weed, from areas where there is a lot of moisture. It can be identified by it red/purple chevrons. Use herbicide to take them out before they get too large. Next is pigweeds, to get rid of it you can use weed killer or a ho...

This video is one in a series of videos dealing with conic sections, in mathematics. This particular video deals with hyperbolas. The teacher, Robert Ahdoot, gives an example of a hyperbola, during which he emphasizes some key points. A hyperbola is identified by an equation containing x squared and y squared, with a minus sign between them. If x is larger, the hyperbola will open to the sides, and if y is larger it will open up and down. He creates hyperbolas, demonstrating where to make asy...

Richpin's Auto Repair shows you how to properly identify the rear axle of a Jeep Grand Cherokee. This information will allow you to obtain the correct information for replacing this specific automobile part. The video will show you where you need to look beneath the vehicle to find out which style of rear axle your Jeep Grand Cherokee has. You'll be shown where to clean the dirt off of a specific area of the axle to obtain this important information. In this particular case, the rear end axle...

In this video, Chopping It Up, we see how some men camping and scouting in the remote central Brazilian jungle hack their way through the thick brush with machetes. We watch as they clear a path to the top of a mountain. It's a lot of work! We're told how they identified a route where the need for hacking would be minimized, on an old trail. The problem, however, is the sunlight on an old trail causes it to get choked up with vines and other thick growth. To clear the path with the machetes, ...
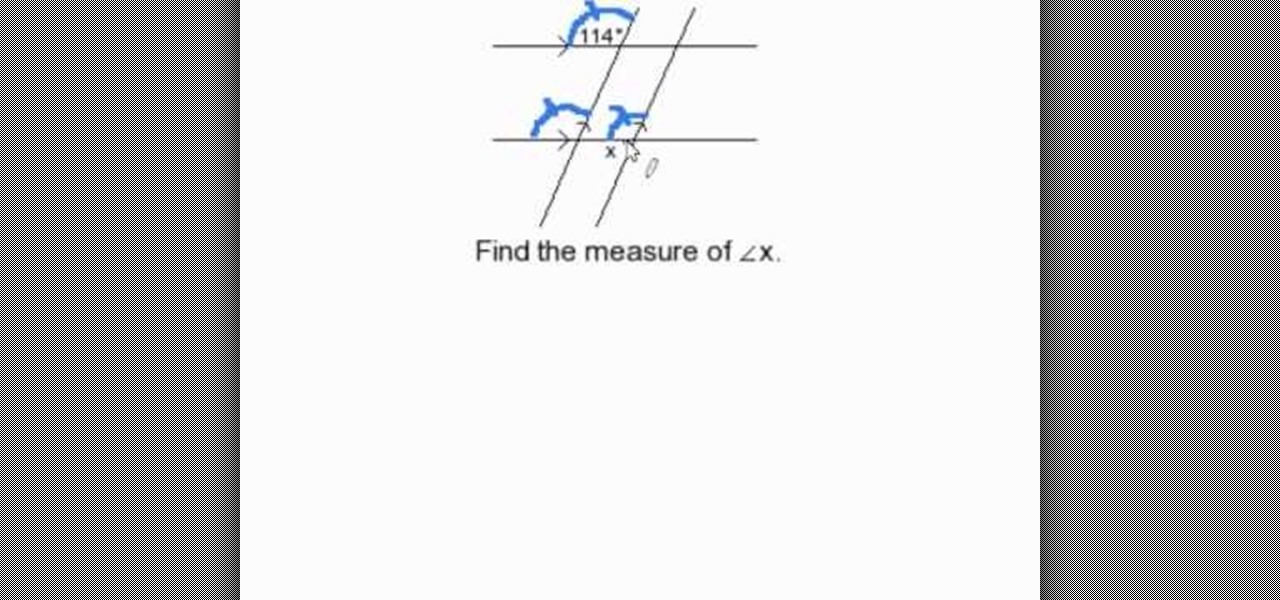
Consider two pairs of parallel lines, one pair horizontally and another is inclined from vertical position. If one of the four angles is given, then the other three angles can be easily identified. First select the angle which is down to the known angle, it will be same as first one. Then according to the law, that a straight lines consists of 180 degrees. For example if the known angle is 114 degrees, the unknown angle will be 180-114= 56 degrees.

Azaleas are relatively care free. To ensure they look their best they require adequate moisture. Make sure the roots in particular get plenty of water especially during the first year or so. Mulch is important, two or three inches of horticultural mulch like straw or pine bark will help protect their roots, which grow close to the top of the soil. They don't need to be pruned. If you want to shape or remove dead wood, wait until after they bloom. By doing it at this time the dead wood is easi...

The video deals with a clear step by step process of making a plastic airplane. He asked us to select the model of the airplane we are going to make first. He has selected the North American F86A SABRE model in this demo.
Award winning author Susan L. Reid teaches us how to write a great mission statement for your business. 1. First, write your "purpose statement". This answers what your business wants to accomplish and what problem or need your business is trying to address. Simply state the answer to this question. 2. Write your "business statement'. This describes the activities or programs your business must do to support it's purpose. Ask yourself what you are doing to address the need identified in your ...

You can stop being lazy by using these tips to motivate yourself to find an interest in life. You Will Need

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a USB device.