This video will show you how to identify addons slowing down browser speed. If you have enabled a huge number of addons all of which is not necessary and consumes huge memory will slow down speed. Now you could identify which add-ons consume how much memory and are they necessary. According to this you can disable few of them to speed up your browser.
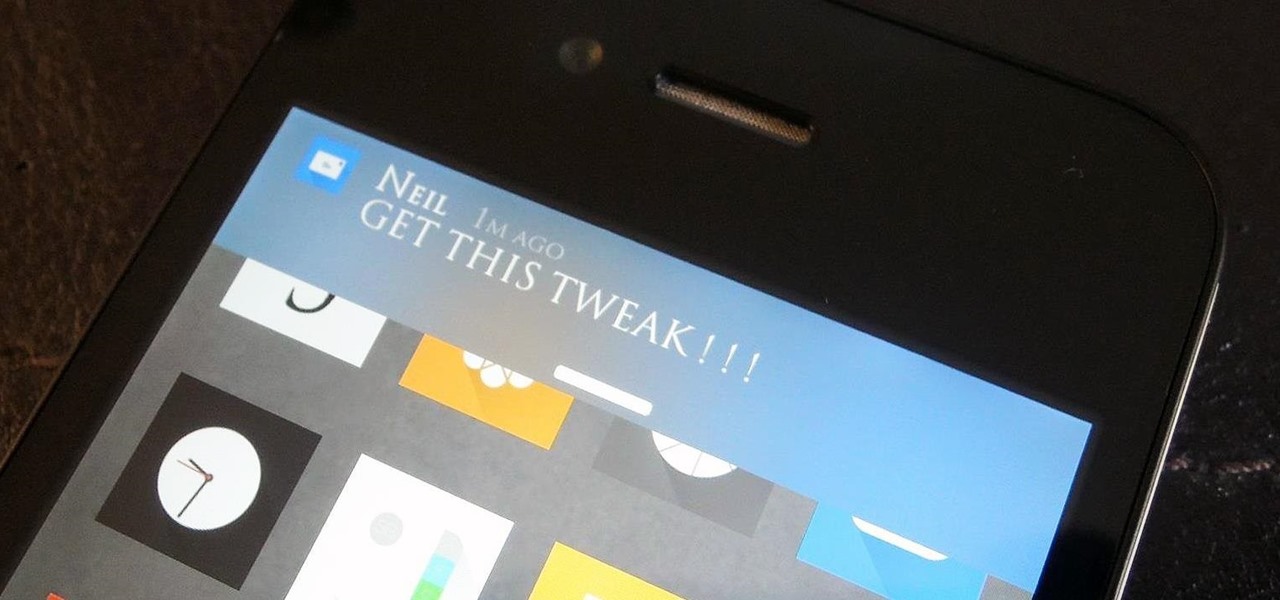
A banner alert for notifications is like the Robin to our iPhone's Batman—they're taken for granted and don't really get the recognition they deserve. Yes, they can be disruptive at times, but just like Robin, they can be necessary for getting things done.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

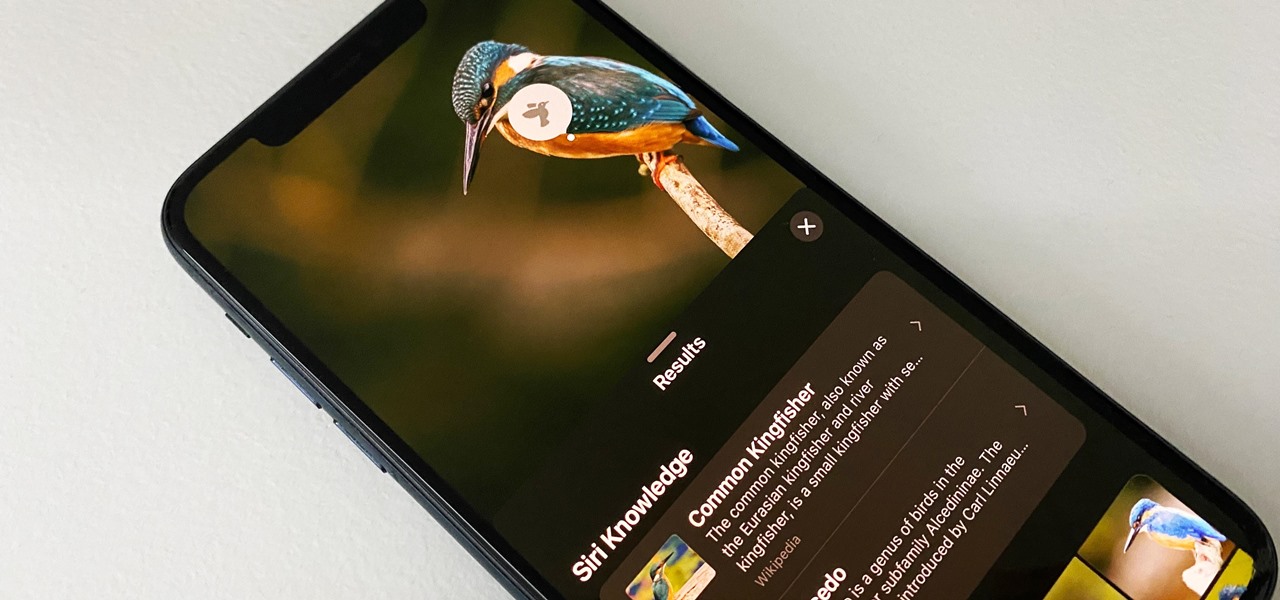
When traveling or sightseeing, you may come across a landmark you can't quite identify and want to know what exactly it is and the history behind it. It could be a building, waterfall ... anything. If there are no signs around or they're in a different language, you'll have no idea what you're looking at. Fortunately, Google Photos can be your personal tour guide with the power of Google Lens.
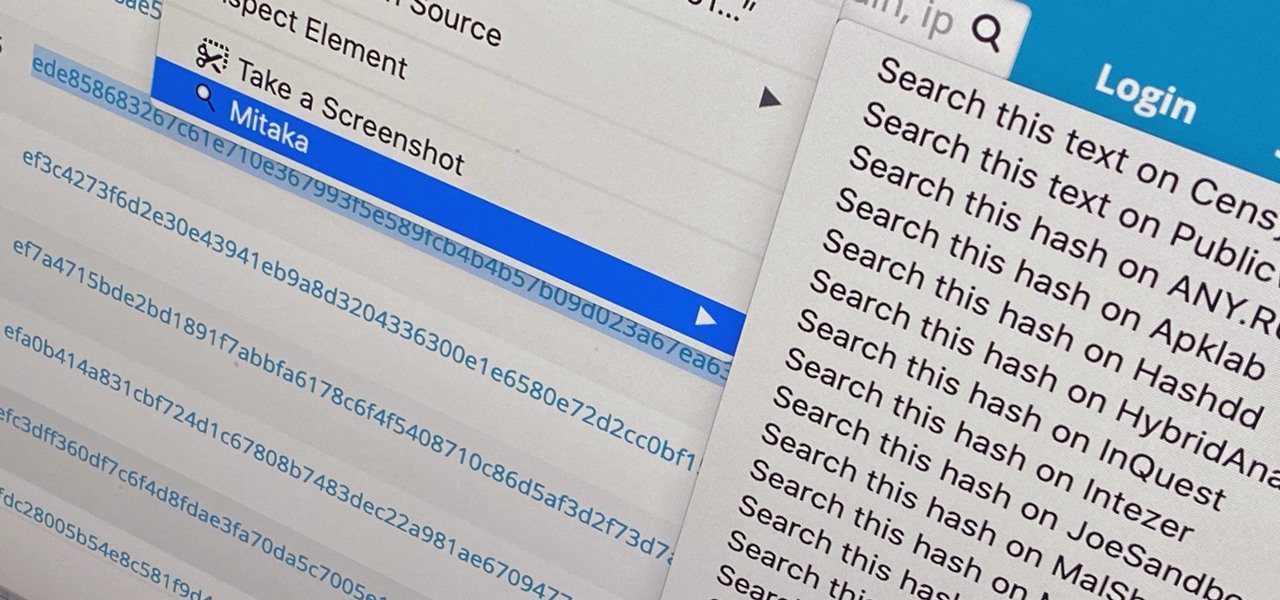
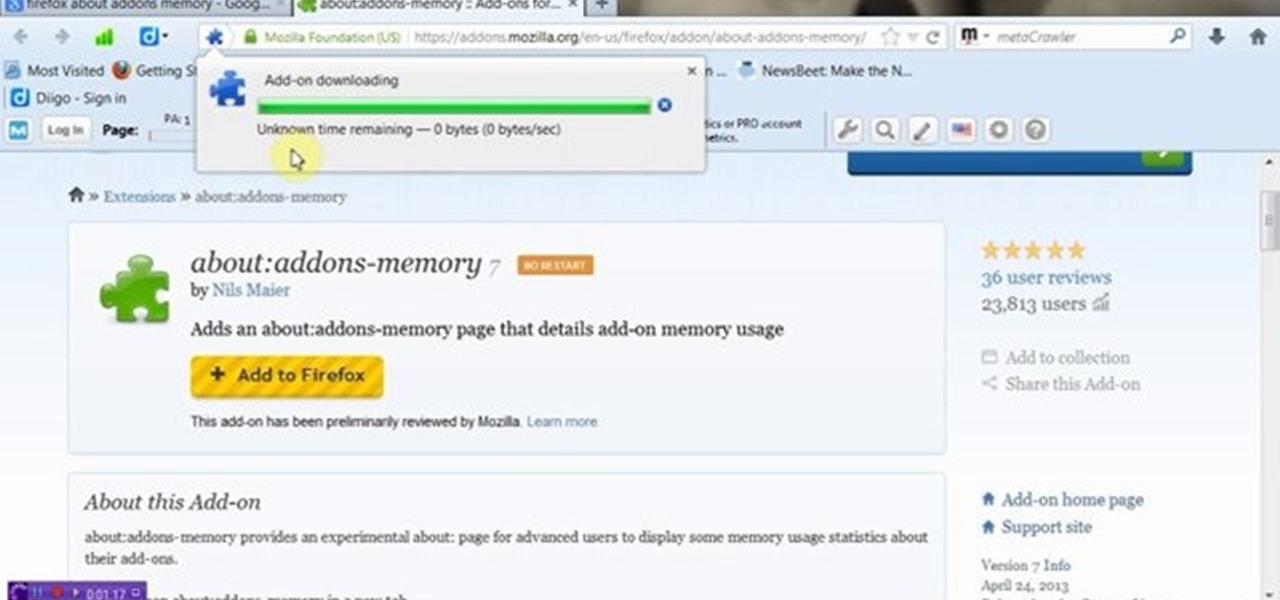
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

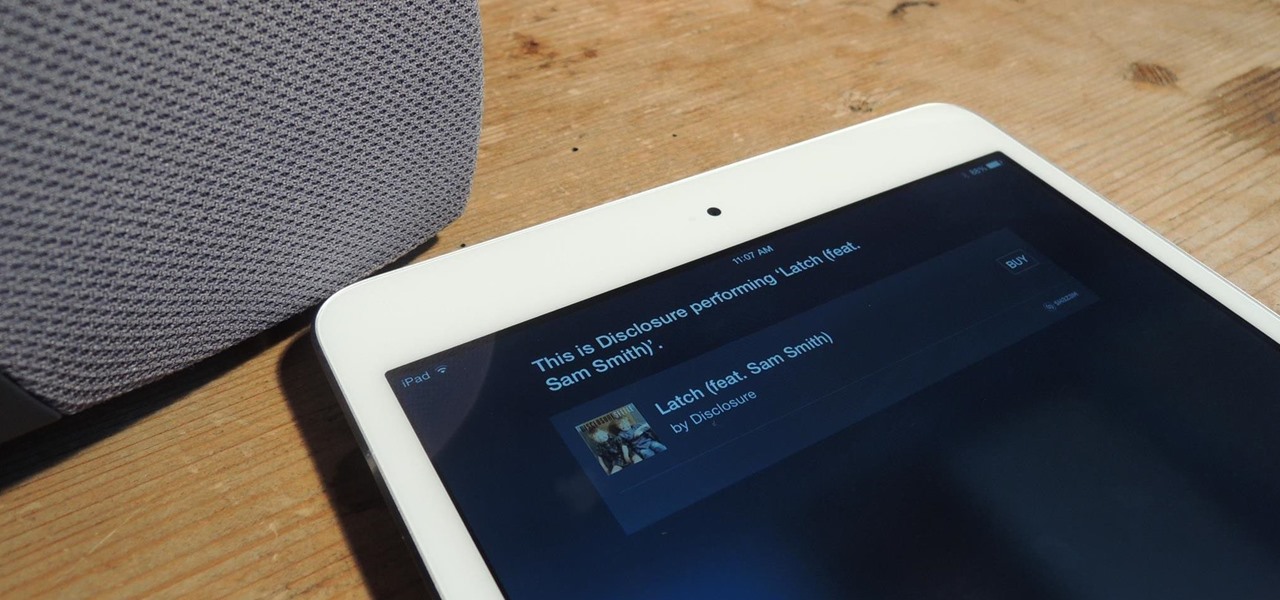
Since Shazam became available on iPhone, it's been easier than ever to identify a song playing somewhere in the background. You could hear something you like while watching a movie or sitting in a coffee shop, and all you have to do is open the Shazam app and have it listen for you. But what about music playing on your iPhone via Instagram, TikTok, and other social media apps?

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

When you take a photo of something interesting, like a landmark, piece of art, animal, or plant, there's a good chance you'll also want to know more about that something than just what you see in the frame. When this happens, you can take advantage of Apple's content recognition service for iOS and iPadOS without having to install any third-party apps.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Using Shazam has quite literally spared me hours of searching the internet for the name of a song I briefly heard for a few seconds. At WWDC, it was announced that iOS 8 now has Shazam technology integrated into Siri. What makes it even cooler is that you don't even need the Shazam app on your device.

How do you know if the Beats By Dre Studio headphones that you are about to buy online are genuine? Always ask the seller to use the youVerify app before you buy. Smarter Selling, Safer Shopping.

Previously, if you missed a call or text on your old Samsung Galaxy S3, there was a white LED notification to let you know. It's a nice feature that most smartphones have, but wouldn't it have be nice to know what kind of notification it was before picking up the phone?

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

Here is a cool show that is all about meteorite identification! These two videos touch on some characteristics of stony (chondrite) meteorites that can help you to positively identify a meteorite.

When cars start to get older, their many fragile moving parts start to make noises they never made before. Sometimes, when your car starts making a new noise, it can be very difficult to identify what is causing the noise and what you need to do to repair it. This video offers some great tips for finding the source of different kinds of car noises, from engine noises to suspension noises.

Ever wonder what tree is which in the bush, or what each tree is useful for? This video tutorial will show you how to identify the various trees that are useful in Bushcraft. Andrew Price explains the difference between the trees, like Ash, Beech, Holly, and Elder trees, and their uses. If you need to survive in the wilderness, this is a great way to do it.

Curtis Smith, Extension Horticulturist with Southwest Yard and Garden, and Rick Daniell, Bernalillo County Horticultural Agent, discuss how to identify problems with vegetable plants in your garden. Gray or white spots on a squash leaf are natural if they do not rub off. Blossom end rot can afflict tomatoes, squash, chilies and melons. Blossom end rot indicates a calcium deficiency during times of vigorous growing during uneven watering. Fertilize when the plants are young. Sun scald can affl...

This video illustrates the quick and easy method to Identify and control garden pests on grapes and roses . The process is comprised of the following steps:Step 1:Garden pests are quite common in grapes and roses.Step 2: To identify these gardener needs to keep a very sharp eyes on the plants every day. Negligence may lead to disaster of the entire crop.Step 3:Garden pests can be commonly seen on the leaves on inner side or on the shoots of the plant.Step 4:Randomly select the plant and check...

How to identify insects in your gardenCarol Sutherland explains us in this video of how to identify insects in your garden. She is an extension entomologist and she explains her view on the insects here. To be known is that some insects are damaging, some others we want to be aware of and some are necessary in your garden. Here during the garden season you get to see insects on trees as they form a familiar habitat. Mostly on the split ends and the broken ends the insects gets invaded. She sh...

Tenderfoot is the first rank earned as a Boy Scout. The requirements of becoming a Tenderfoot provide basic skills to begin preparing the scout for higher adventure outings. Earning badges and receiving recognition can be very satisfying to boys. However, keep in mind that the badge is only a representation of a valuable set of skills that a scout has learned and demonstrated. The skills, wisdom, and experience gained through the activities of the scouting program are of much more value than ...

Second Class Boy Scouts work on building their outdoor survival and camping skills. Compass work, nature observation, camp tools, and swimming are areas where new skills are mastered and demonstrated. A second class scout, having completed all the requirements, should be able to lead a hike, care for his own equipment, set up a campsite, and perform basic first aid.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

This will illustrate us how to identify various kinds of insects in the trees. here are the following steps :Step 1: First of all get a Pictorial version of book based on insects.Step 2: Now on the tree look for various kind of insects and as well as there eggs laid by them.Step 3 : now look for the pictures in the book and match these with the insects on the trees .Step 4 : To be confirmed about the right identification look closely for the shape of the legs off the insect and as well as the...

In this how-to video, you will learn how to identify and control problems with Bermuda Grass. If you are worried with allergies, you should check if you are allergic to this particular grass. The seed heads produce the majority of it, but even the pollen produces these allergies. Regarding the water schedule, the grass needs water during the summer. If you have a fine textured soil, you should water about one time a week. If your grass is turning a blue-gray color, it might be lacking water. ...

This will illustrate us how to identify problems with evergreen trees. Here are the following steps:Step 1: First of all look for all the evergreen trees.Step 2: Now look for the problems that is whether there is any fungal or bacterial infection occurring.Step 3 : Now look for the climatic requirements as well as the water requirement for the plant.Step 4: Look whether the conditions are available to your surroundings or not.Step 5: Also find out whether the soil type is idle for the plant g...

This video explains how to identify problems with the peach tree borer. The video begins with a peach tree shown with bore issues below the dirt line on the trunk. The instructor then explains that most of the pesticides used for this problem are no longer available and that most people have turned to more organic pesticides to solve the problem. The video then explains that you must first clean all the bore and dirt away before trying to apply pesticides to the tree. After the bore holes hav...

In this Home & Garden video tutorial you will learn how to identify pecan weevil problems. John White presents this video along with Carol Sutherland, extension entomologist. After pecan is infected with pecan weevil, it has the potential of spreading in the entire area. The indication of pecan weevil infection is an opening on the crust of the pecan which may or may not be a perfect circle. But, on the nuts the holes are perfect circles. There is usually one hole on the nuts; though sometime...

Identify pinion needle scaleWe are going to look at this insect because eggs are being laid. Two year old needles are being cast off. This is a sign of infestation. There is also sparse, open foliage. This tends to be a chronic infestation. The insect is the pinion needle scale. You can see tiny, bean shaped bumps on the 2 year old needles. The insects move to last years new growth and feast on the sap of the needle all summer. You can see egg masses and web on the trunk of the tree. The inse...

Second Class Boy Scouts work on building their outdoor survival and camping skills. Compass work, nature observation, camp tools, and swimming are areas where new skills are mastered and demonstrated. A second class scout, having completed all the requirements, should be able to lead a hike, care for his own equipment, set up a campsite, and perform basic first aid.

The first part of this tutorial shows you the various parts of your sewing machine, which will be the same regardless of the model. Then, you're shown how to thread both the top and bobbin of the machine, and start stitching.

There are a number of diaper rashes that your baby can face. Sometimes a rash can be a great risk and hard to treat. You may need to take your baby to a doctor if you have tried treating their rash with different types of ointments/creams/medication and the rash has not gotten better. It may be more than just a wet diaper causing harm.

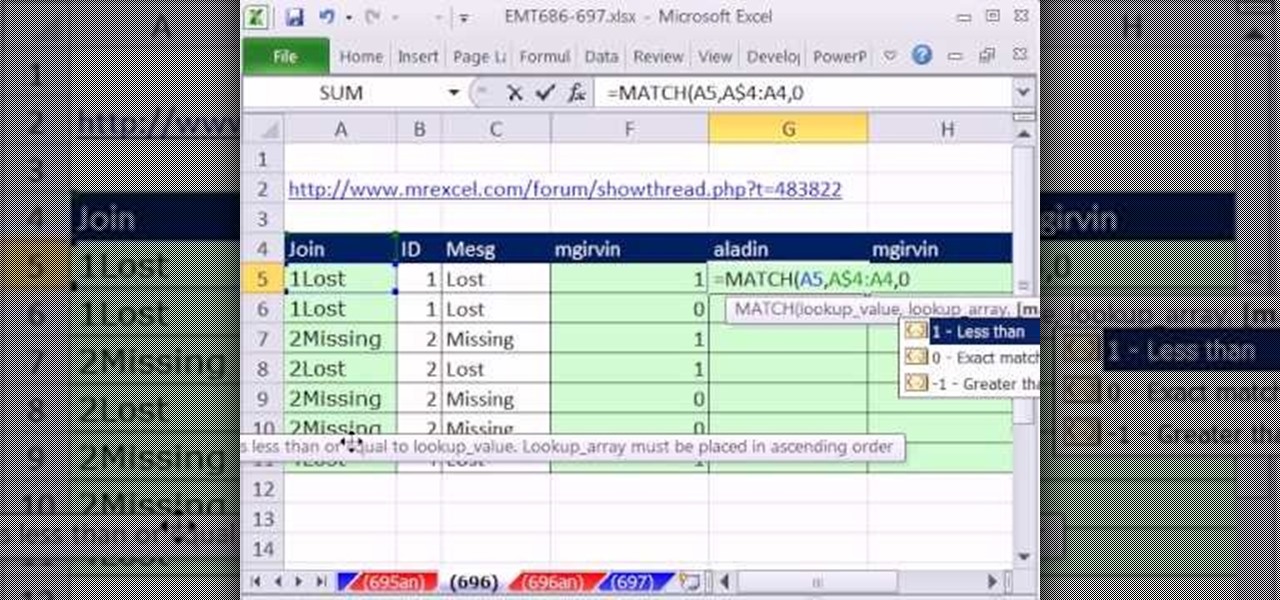
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 697th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a column of 1s and 0s (ones and zeroes) where 1 indicates the first occurrence and 0 indicates any remaining duplicates.

The problems with container plant roots. when purchasing a container plant be sure to check the root system. Wholesale plant sellers tend to leave the plants in small pots for to long. This can lead to problems with the root system. What you have to look for is to make sure the roots are not coming back up and around the base of the plant thereby choking it. When you are replanting be sure to make the hole in the ground 1and 1/2 to 2 times up to 5 times the size of the root ball. This is how ...