
How To: Do the pada hastasana (hand to foot pose)
Want to freak your friends out by walking around looking like a human pretzel? Twist and bend your way to yogi bliss by doing this hand to toe pose, also known as a pada hastasana.


Want to freak your friends out by walking around looking like a human pretzel? Twist and bend your way to yogi bliss by doing this hand to toe pose, also known as a pada hastasana.

Mastering the concepts of the BOOT.INI file (the boot loader) in Windows XP to better control your Windows configuration.
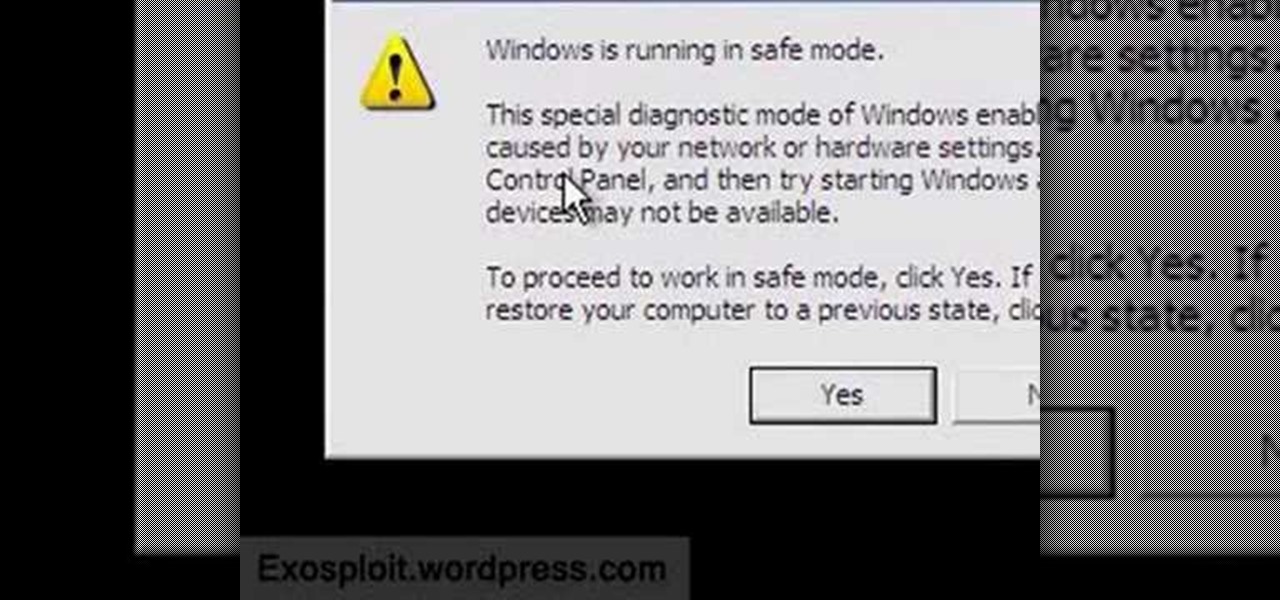
This video will show you how to boot in safe mode on Windows XP. Just follow these instructions from the video. Now go to Start -> Run and type in msconfig. and click OK. Now select the BOOT.INI tab and select /SAFEBOOT, click apply and close and then it will prompt you to restart. After you restart a message will appear. Click Yes and you will notice that your screen resolution is small and you will have the classic theme. To return to normal mode just repeat the steps and uncheck the BOOT.I...

In this tutorial, we learn how to clear an internet cache with Don Schechter. First, you need to click on the start menu, then find the "run" link. Type in "Msconfig", then click "ok". Now, click on the "general" tab, then click on the button next to "selective startup". Now, unclick the check marks next to "process systyem.ini, process win.ini, and load startup items". Click "ok", then restart your computer. Now, go to the "system tools" program in your Control Panel and select the file you ...
In this tutorial, learn how to fix a missing or corrupt ntoskrnl.exe file on your PC. Cause:
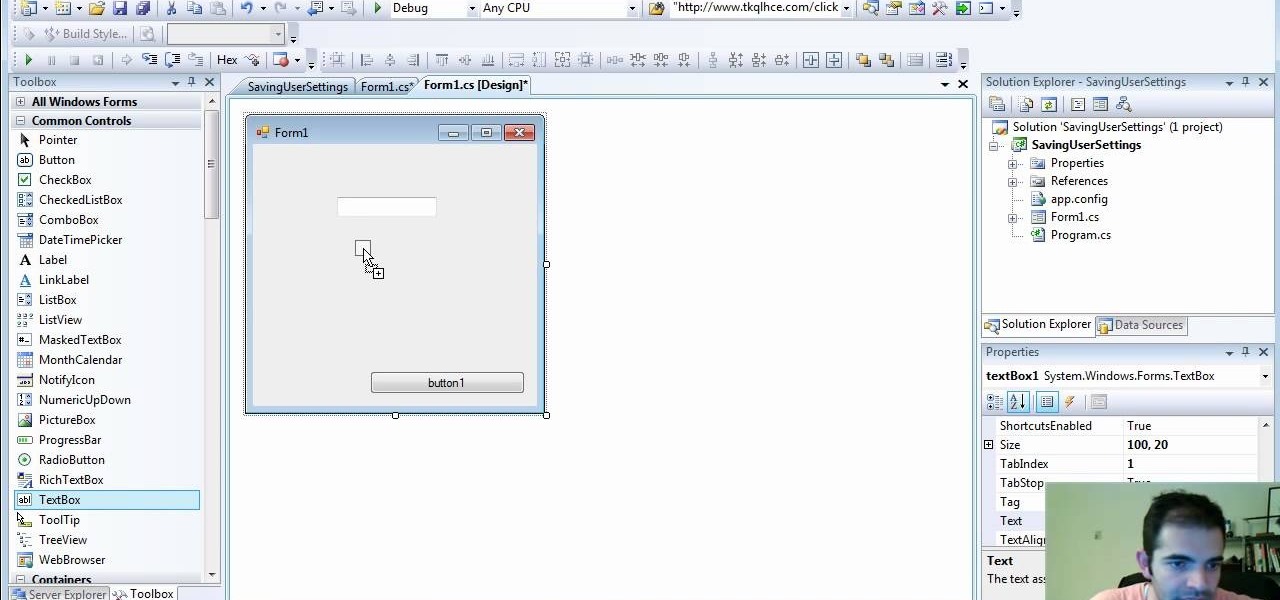
Check out how to save your user settings in Microsoft Visual Studio using C# programming, that way when you restart the program, it can remember some of your important information. This will specifically show you how to save your user settings using the .NET Framework instead of working with custom INI files.
If you have been looking for a way to get the popular Joomla Content Management system running on Windows with IIS, you may have run into many problems. In fact, many people spend days trying to get Joomla running on IIS and run into roadblock after roadblock. The problem is getting PHP, MySQL, Joomla and IIS to all play nicely together. As you search for solutions, it is easy to find part of the answer, but rarely do you find it all in one place... until now. In this video tutorial we start ...

There are a couple of limitations that Microsoft put in to Windows 7 upgrades that can prevent users from upgrading and ultimately force them to do a clean install. First limitation is that they won't let you to upgrade Windows 7 if you run Windows 7 release candidate that was released earlier this year, which they won't let you to upgrade to a download Windows edition. If you are running Windows vista ultimate you cannot upgrade windows 7 professional. We have to buy an ultimate edition then...
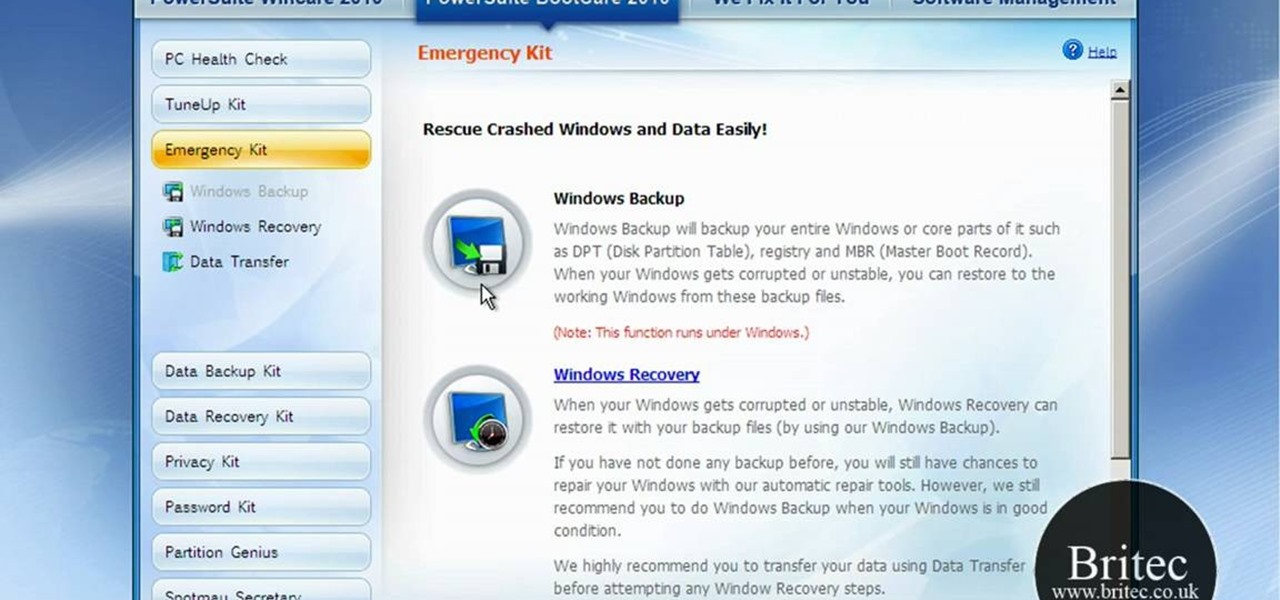
If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs.
When you try running Apache, Joomla, PHP and MySQL at the same time, you should expect a few hiccups. But there are ways to get them running smoothly and effortlessly together, and this video will outline the process of getting your Joomla Content Management system up and running correctly on Windows.

This quick how-to video yoga tutorial demonstrates how to do eka pada bakasana. Eka pada bakasana is more commonly known as a one legged crow pose. Watch and learn the basics of this ancient yoga posture.

The Jitterbug is a popular swing dance, also known as the Lindy Hop and East Coast swing. In this four part how to video, Mike and Tina of Head Over Heels demonstrate the Jitterbug stroll. There are four steps to the Jitterbug stroll, the Pada Pada, the Knee Slap, the Suzie Q, and the Tick Tock. Watch this dance tutorial and you will be doing the Jitterbug in no time.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!
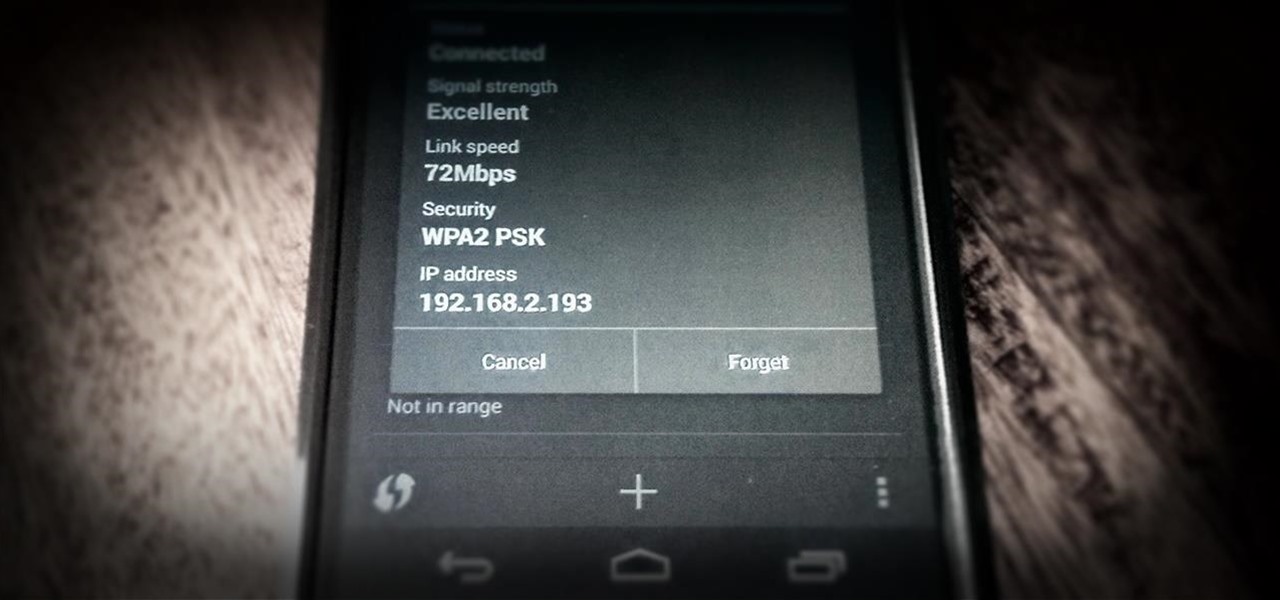
One of the most common complaints that people have about the Nexus 4 would have to be its intermittently poor Wi-Fi performance, a problem that for many, persists through the installation of updates and even custom ROMs.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

He may be the oldest person to have invented an app for Apple devices, but 84-year-old George Weiss didn't originally intend on marketing his Dabble word game to the mobile crowd. He first came up Dabble back in 1958 when he was just 31. “A lot has changed since 1958, but people still love a good game,” said Weiss on his introduction into the iTunes App Store last month.
What is Google Dorking? Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly by using specific search criteria that should yeild results, should it find matches to known mistakes/errors in a website or webserver.
Technology: The Less You Know the Better?