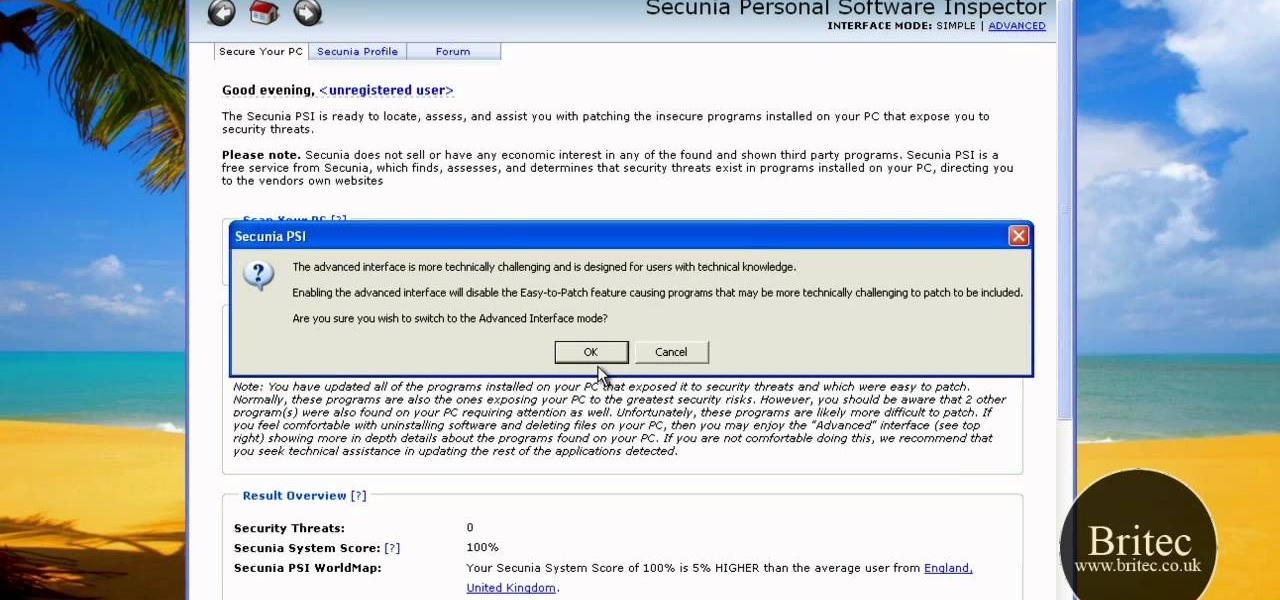
Looking for a primer on how to use Secunia Personal Software Inspector or PSI to remove malware from your Windows PC? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.
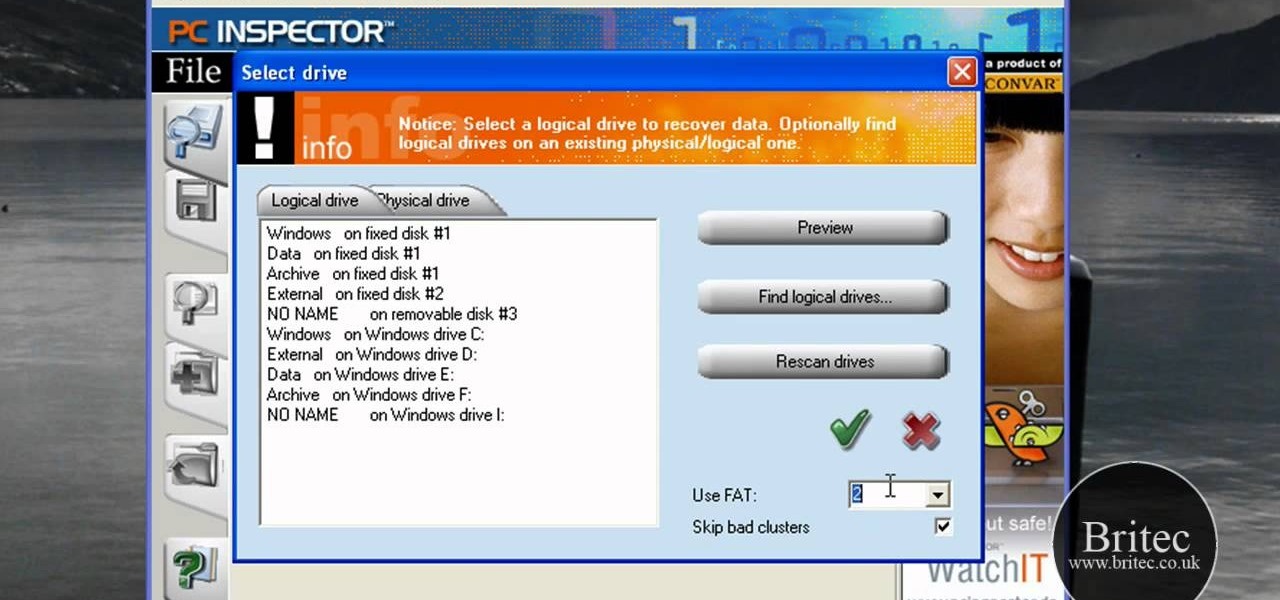
In this data recovery tutorial the instructor shows how to recover deleted files and lost data using a free software called PC Inspector. On your computer you may loose data sometimes due to a corrupted hard drive, or because you deleted it accidentally or some other reason. Now some times you will need to recover that important data and it will cost you hundreds of dollars to get it done outside by the professionals. Now you can avoid this and use a free software called PC inspector and reco...
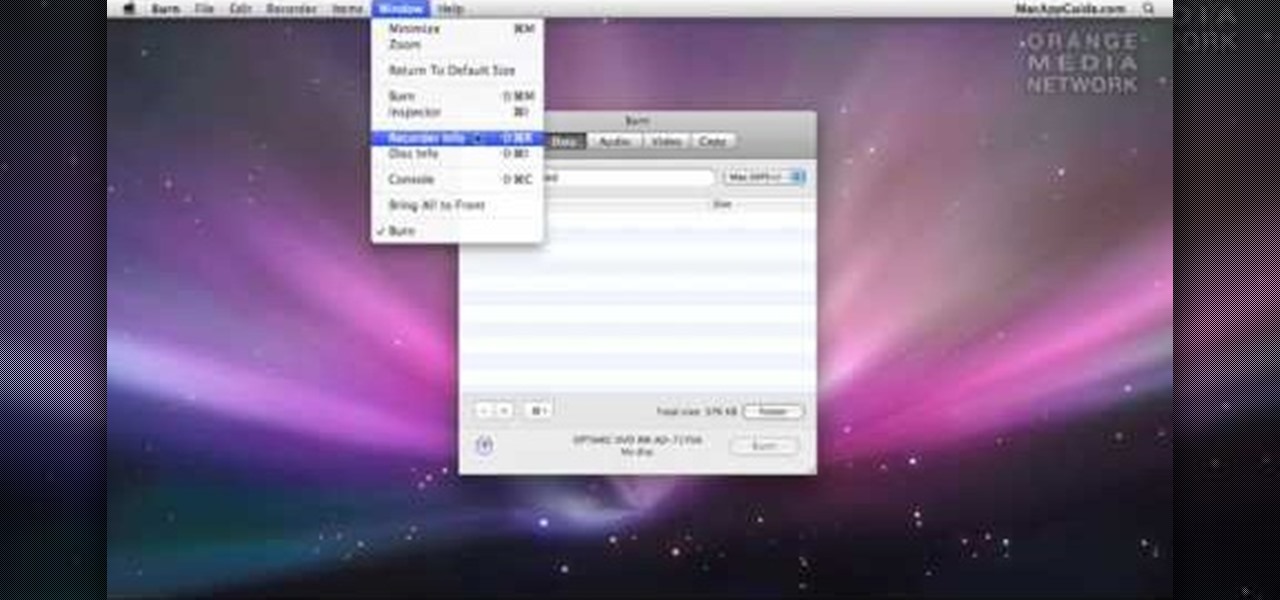
In this video tutorial, viewers learn how to burn a CD or DVD on a Mac computer with the Burn application. Burn is able to create data, audio and video discs. The Inspector window allows users to edit extra information about the disc. To open Inspector, press the Command and I button. It is also able to create disc copies. To burn a disc, name the disc and select a format. Them simply drag the file(s) into the program and click Burn. This video will benefit those viewers who have a file on th...
Creating widgets can be easy to make using Dashcode. This tutorial will take you through the process of creating easy to do widets with simple steps. This tutorial also talks about some of the other features od Dashcode and how more advanced parts like debugger and inspector. Sit back and enjoy!
Aperture's metadata inspector is a one-stop location for editing the metadata associated with your images. Some of this metadata is automatically stored within the image files of your digital camera, and aperture automatically reads it when you import your photos. You can add other metadata, such as keywords, yourself.
Use LiveType to create professional titles in your Final Cut Express project. Match the properties to those of your Final Cut Express project, add text, choose a font, and format your text using the inspector. The title shows up on the canvas and in the timeline. You can also add sophisticated backgrounds, effects, and animation.

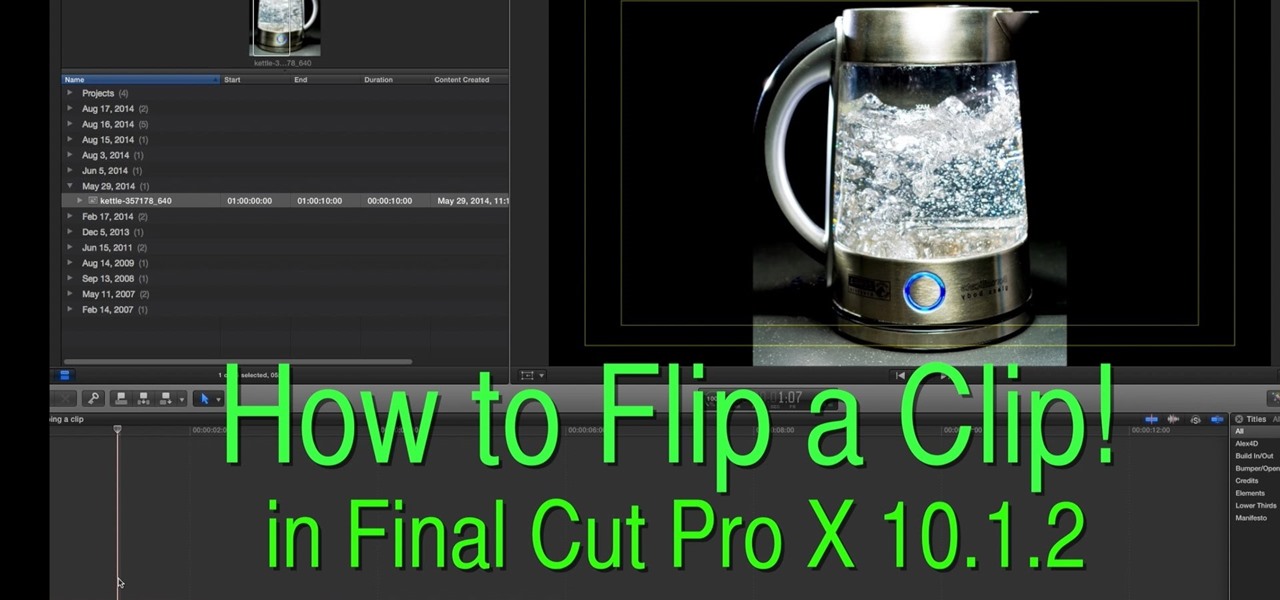
This is a great how to for all users in Final Cut Pro X 10.1.2 Video: .

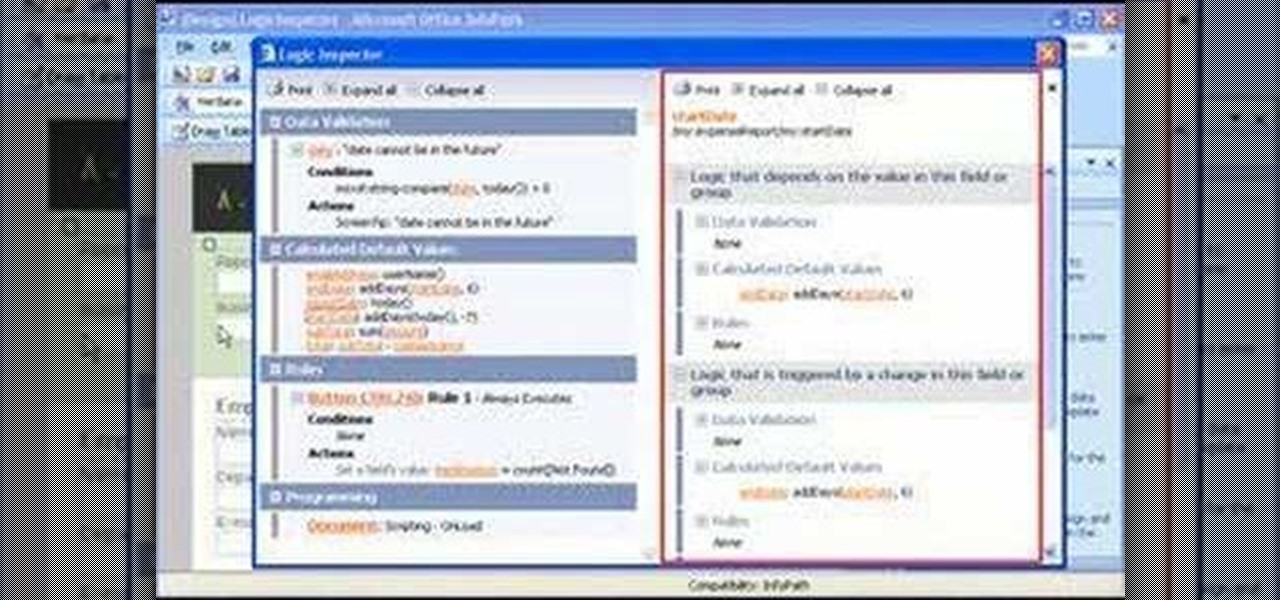
You don't have to check the settings for every control individually — you can use the Logic Inspector to see a form's business logic displayed in a single window, grouped by features such as data validation, calculated data values, rules, and programming. Take a look at this instructional video and learn how to view the logic in a form template with Microsoft InfoPath.

This tutorial demonstrates how to turn on Safari's Debug mode so you can use additional functionality like the JavaScript console, Web Inspector, and spoof Internet Explorer.

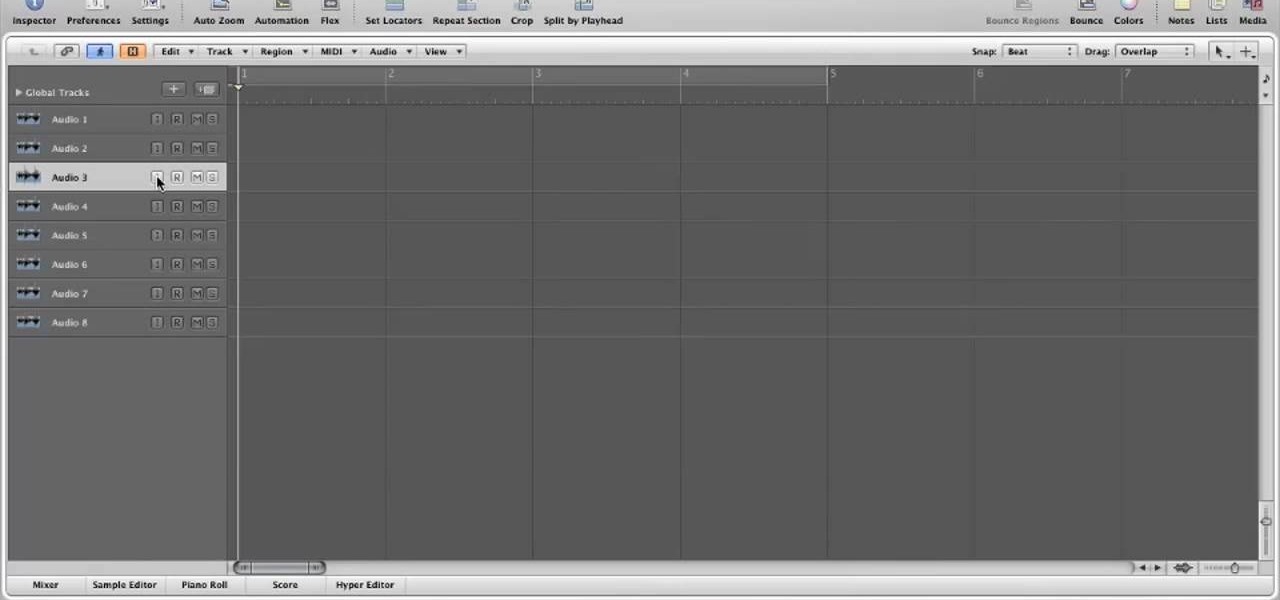
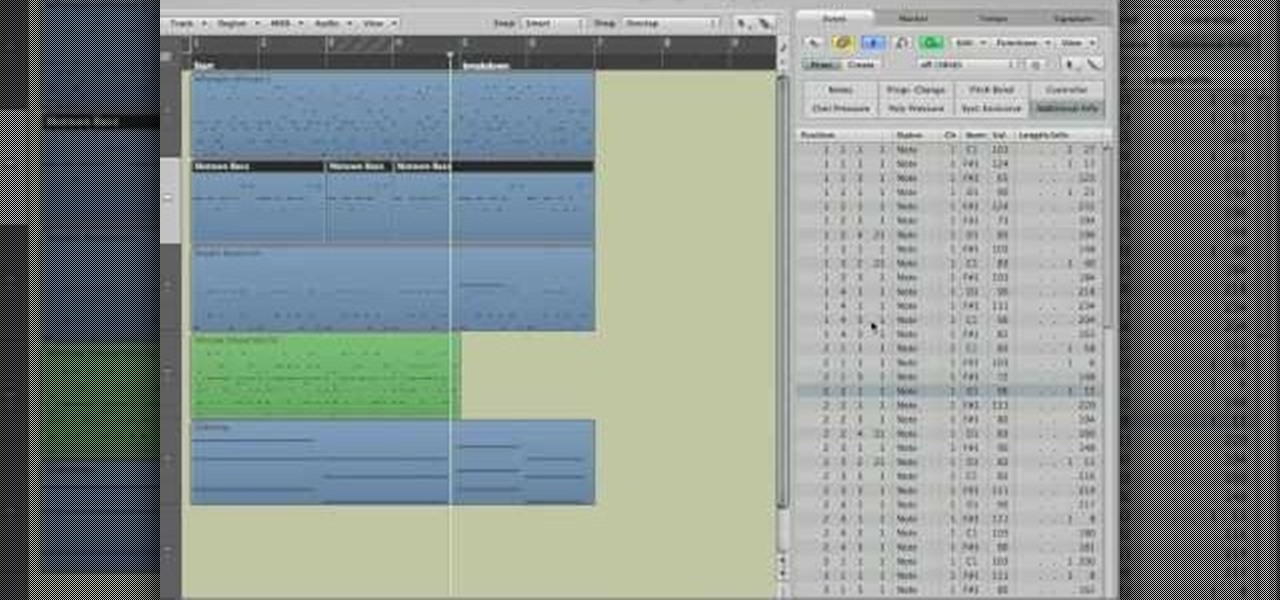
This video in the Software category will show you how to use multitrack live recording in Logic Pro 9 . This video is from Lynda. Say you are going to record a 4 piece band; drummer, base, guitarist and a singer. Use separate mikes for all four. First you make 8 different mono audio tracks. Go to track menu and click new. Type in 8 for number, select audio, format will be mono. Now you click the ascending box, order the inputs from one to eight and click create. Now you have 8 audio racks. Cl...

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

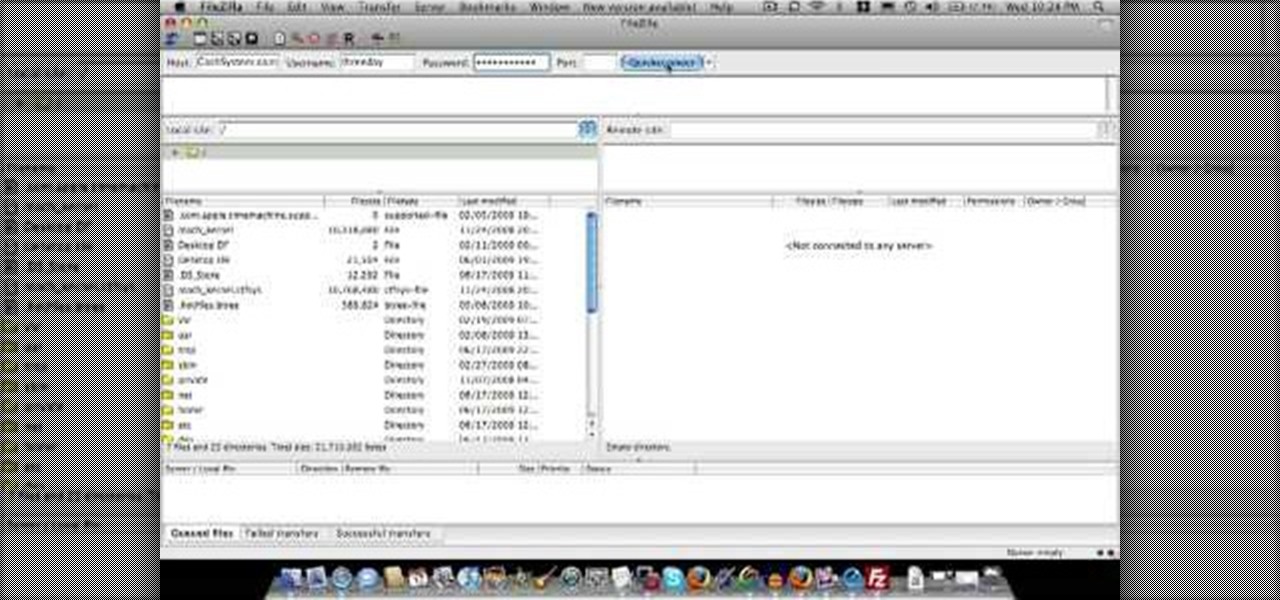
In this video tutorial, viewers learn how to create a FTP from a local computer to a website. In this video, viewers are shown (once you've chosen a web host) how to perform FTP file transfers from your local computer to your website. FTP (File Transfer Protocol) is a process that you can use to transfer files from your local computer to a remote computer (your website). Once you've set up a hosting account, your hosting company will provide you with FTP login credentials. Using an FTP softwa...

Get to know how to use Logic Pro's arrange page in this short tutorial. Use the arrange area to work with the audio of your song. Change the timeline by choosing a time and beat. Use the toolbar area to do some functions. Use the icons to easily open up media and list areas. Use the bin to store your audio. Use the browser to look for your audio songs. Use the event list editor to edit your MIDI information. Use the inspector to view the channel strips of your track. Use the editors in the bo...

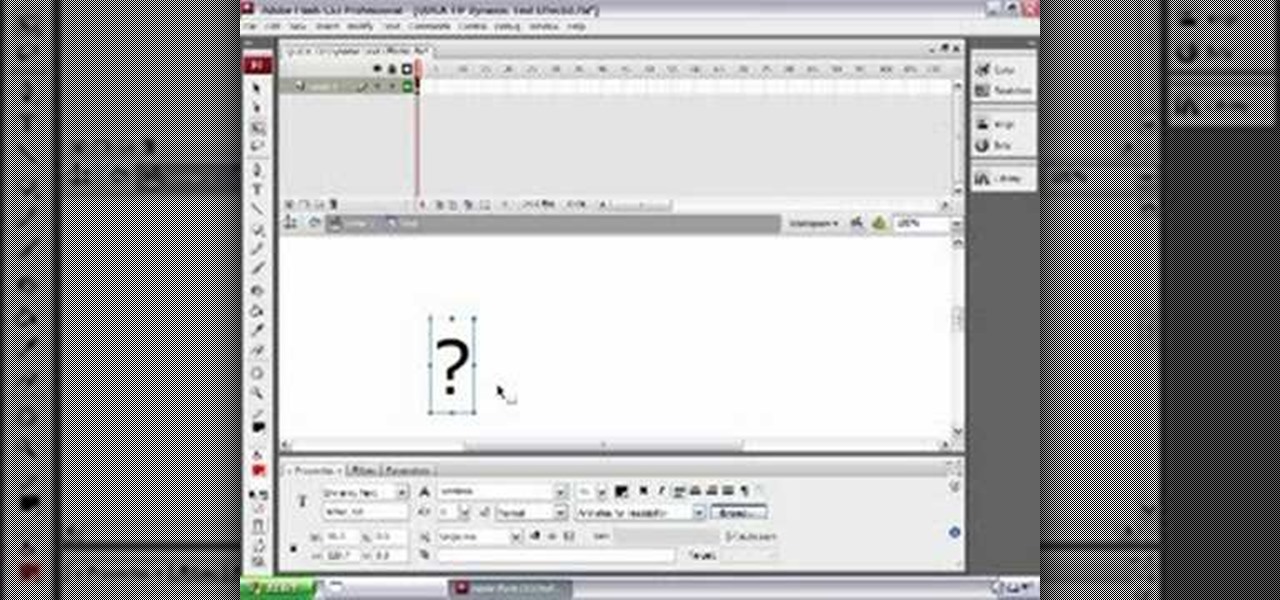
Todd welcomes us to a new episode of the YouTube show All Things Adobe - Chad and Todd Podcast. This episode concentrates on adding alpha and rotation effects to Dynamic Text Field in Flash CS3. First we get to see a 100 frame text animation and the preview works perfect in the program. But when you go to preview it in an outside window, the effects do not work, due to the default nature of the settings. You have to go to Library, then click the text symbol. Click embed in the property inspec...

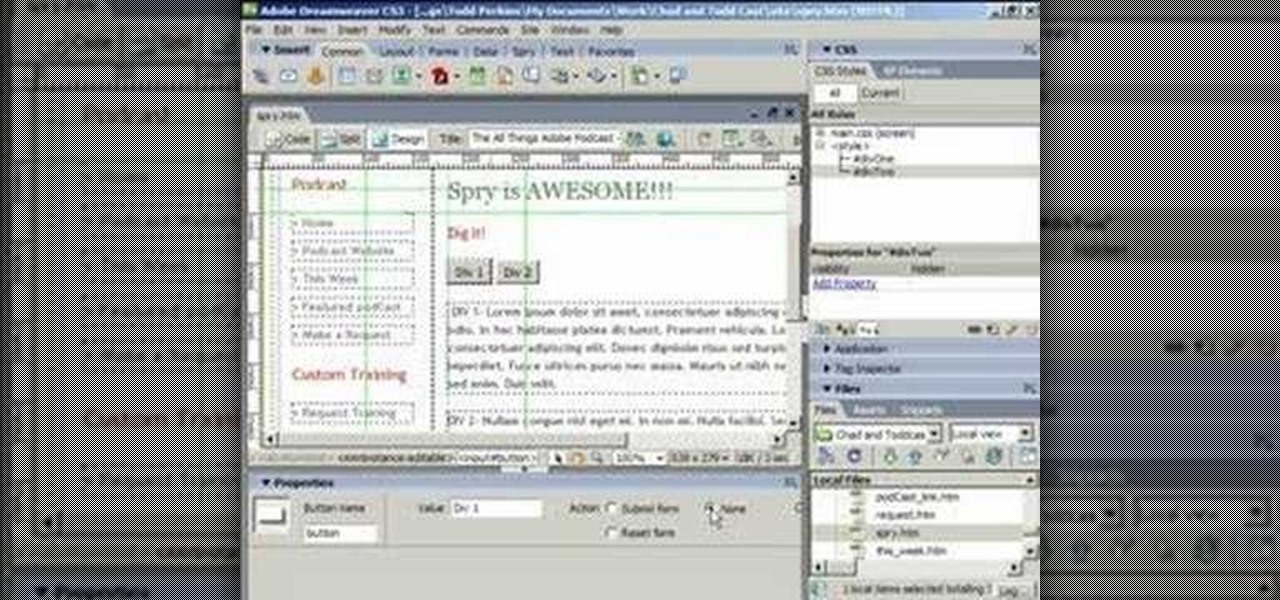
ChadandToddPodcast teaches you how to use the spry framework for AJAX in Dreamweaver CS3. This allows for effects on the page to happen, without the need for the browser to refresh. You start with a simple .html page. You have 2 buttons and 2 div tags with text in them. Div 1 and div 2 have the visibility property set to hidden. Click on the div 1 button, go to Tag inspector and click behavior with a plus. Click Effects and choose Appear/fade. The target element should be div 1. Fade from 0 t...

John Gregory shows just how simple it is to make and edit videos using Windows Movie Maker. In you movie maker window, Just click on “Import Video” and import a video that you want to edit. Here, John takes up a video he has already created. You can see the different slides in the video. Select all the slides and drag them to the time-line and paste it there. Now you can view the slides on time-line. Next, is giving a title to the video. Here, the title used is “how to send a video mail”. Joh...

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

This video from CNET Insider Secrets tells you how to recover deleted files from a data drive. If a disk is still readable by the computer, files may be recovered. Files may be recovered using the PhotoRec program, PC Inspector or other programs that may be available. An example is shown where mp3 files are deleted from a flash drive. We are then shown how files are recovered using the PhotoRec program, including how to select the correct file system. The mp3 files are recovered along with va...

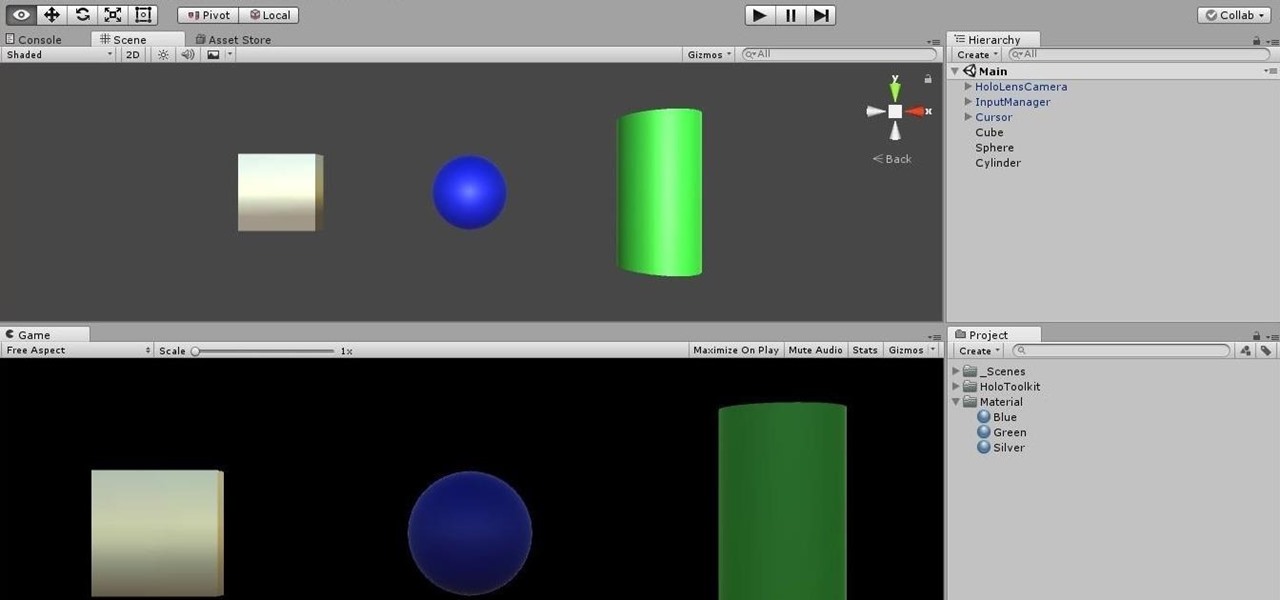
In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

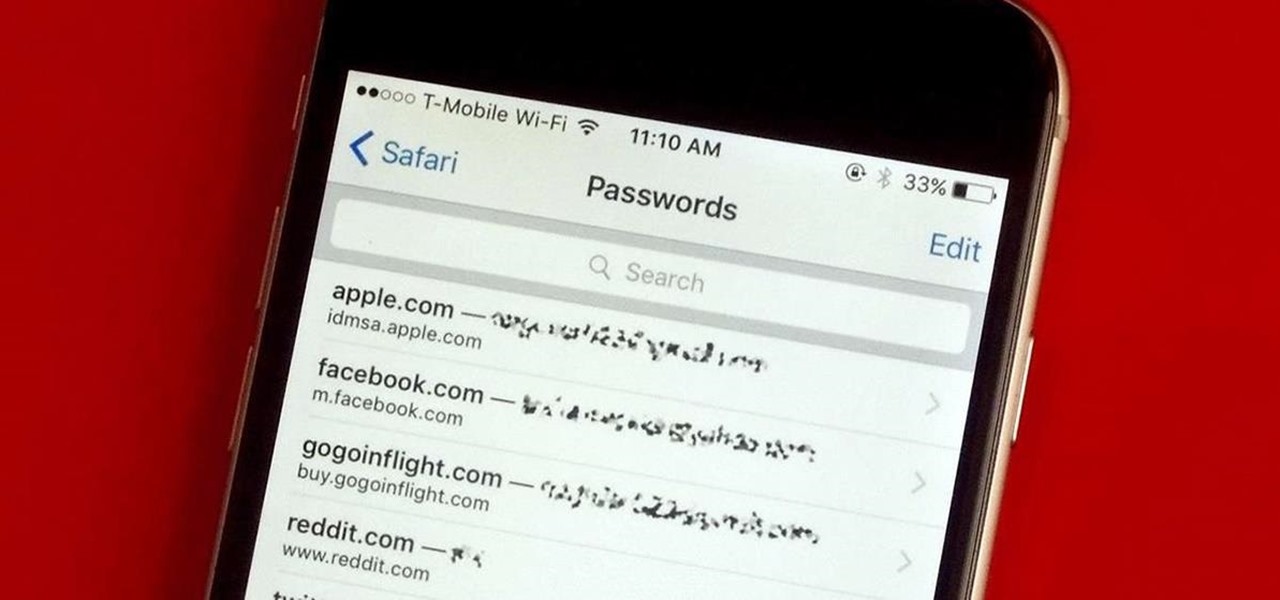
Every time you log in to a website in Safari on iOS, you're also asked if you would like to save the username and password—a great feature of just about all browsers that makes it so that don't have to enter your credentials each time you access website in the future. While this feature is great for quickly getting into all your favorite websites, have you ever wondered where all those passwords are saved on your device? In this guide, I'll be showing you where to find all of the stored usern...

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

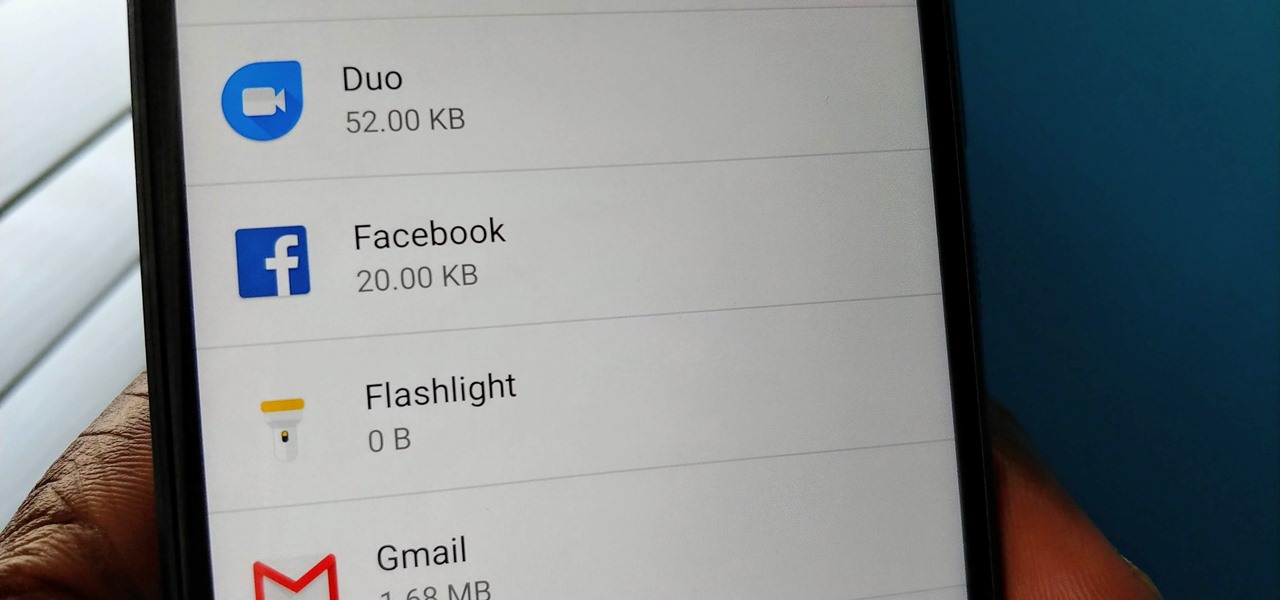
Despite years of user complaints, OEMs are still preinstalling third-party apps on brand new devices. Even in 2019, you'll still find plenty of phones with Facebook preinstalled. What's worse, it's installed as a system app, so it can't normally be uninstalled without root access. However, there are a few workarounds.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

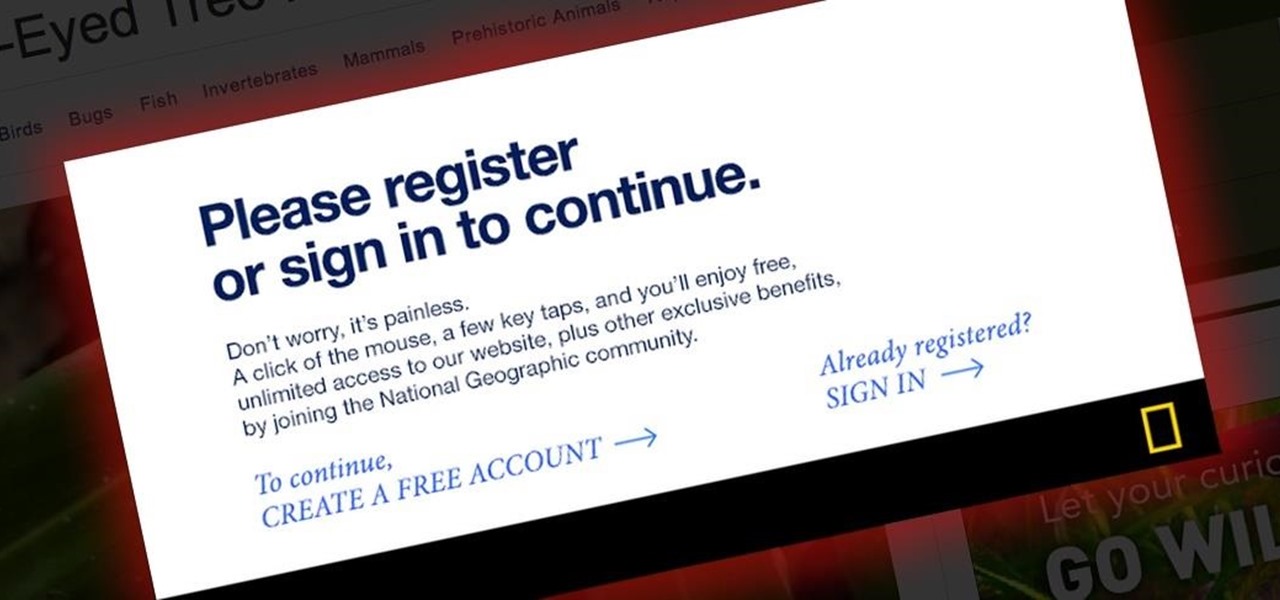
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

Four months after unveiling the latest productivity apps for the HoloLens, Microsoft now has a series of compelling real-world use case videos showing how the augmented reality device and its apps are helping oil giant Chevron.

After hosting millions of free 3D models online, Sketchfab is betting that augmented reality and virtual reality developers and creators will be willing to pay for premium 3D content.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

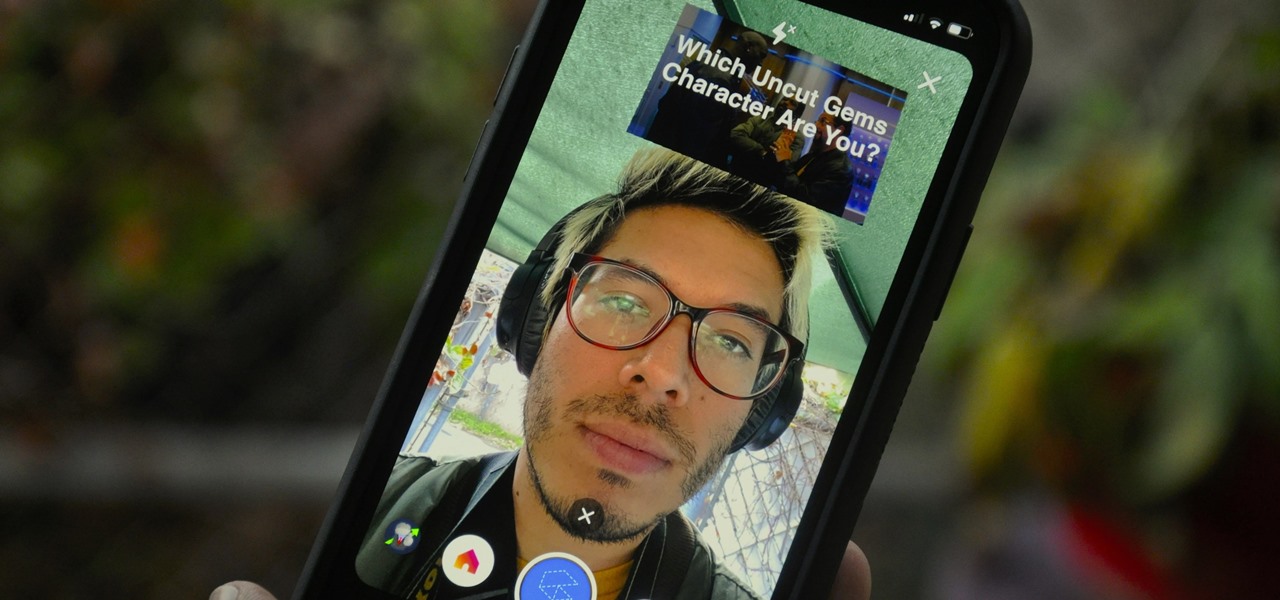
There's a new trend on Instagram Stories: People are making viral AR filters where images of popular characters from TV shows, movies, and other mediums shuffle above your head until one sticks. The filters range from Disney and Pokémon characters to Harry Potter and Friends, but you're not limited to just that because you can create your own "which are you?" filter.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

When using face unlock on the Pixel 4, your lock screen notifications are bypassed by default to help you unlock your phone instantaneously. This is different than Face ID on the iPhone, which shows the lock screen until you swipe up, but only shows notifications when you've been authenticated. If you want to do it Apple's way, there are settings you can adjust on your Pixel.

Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

Why is Windows always asking you for permission before you do anything? Since when does Windows control your computer, and not you? Those user account control popups can be so frustrating, especially when it comes to simple tasks.

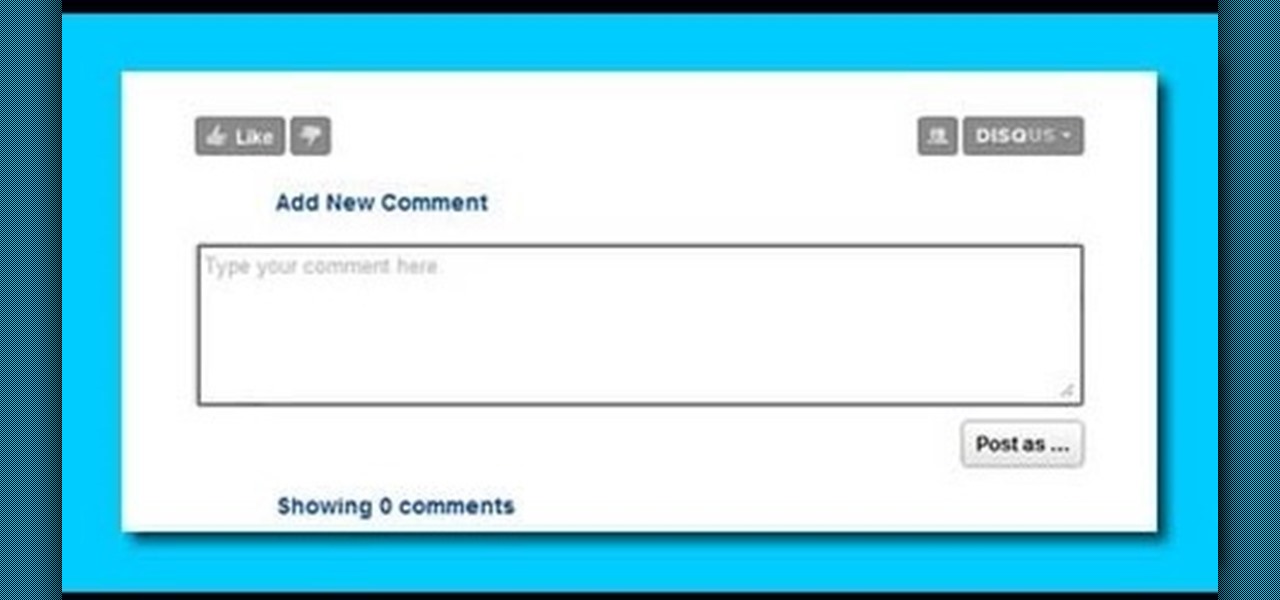
This Dreamweaver CS4 tutorial takes you on a step by step process for installing an automated comment box system for your website. The system is a great way for communicating and interacting with your website users. It has a great feature that automatically sends you an email everytime someone comments in your website. Also it will allow you to post a reply by email.

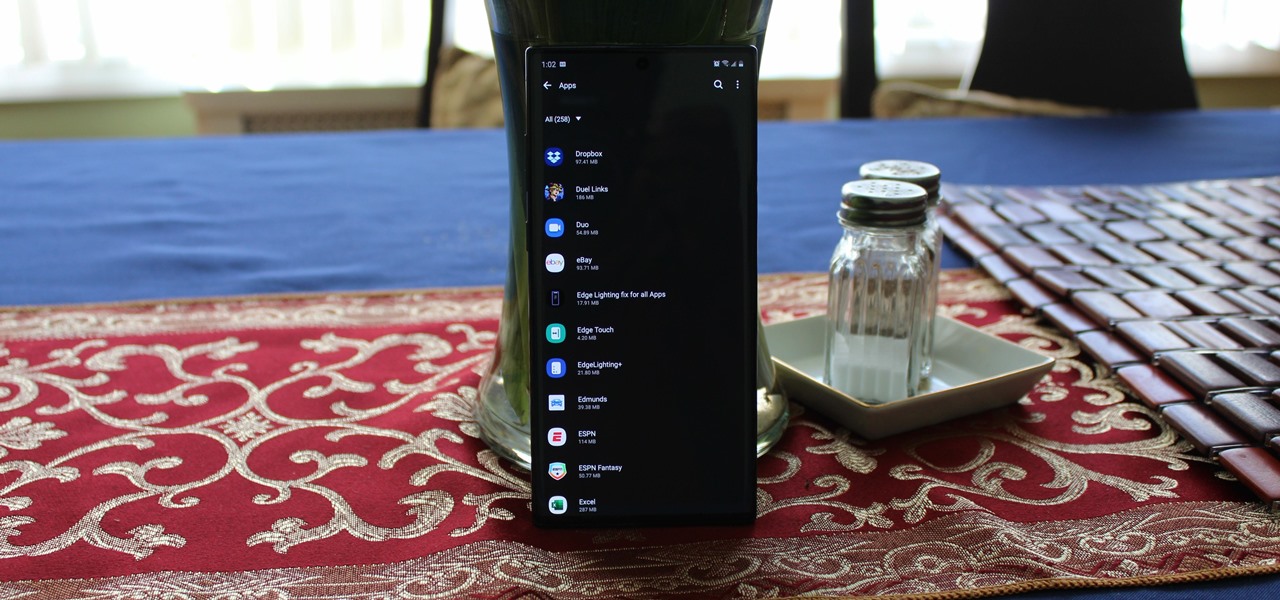
You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.