Authorization allows you to copy your music store purchases to other computers and burn them to CD and protects the artists. Each computer you use to play your purchase must be authorized using your music store account. You can authorize up to 5 computers; yours is automatically authorized.
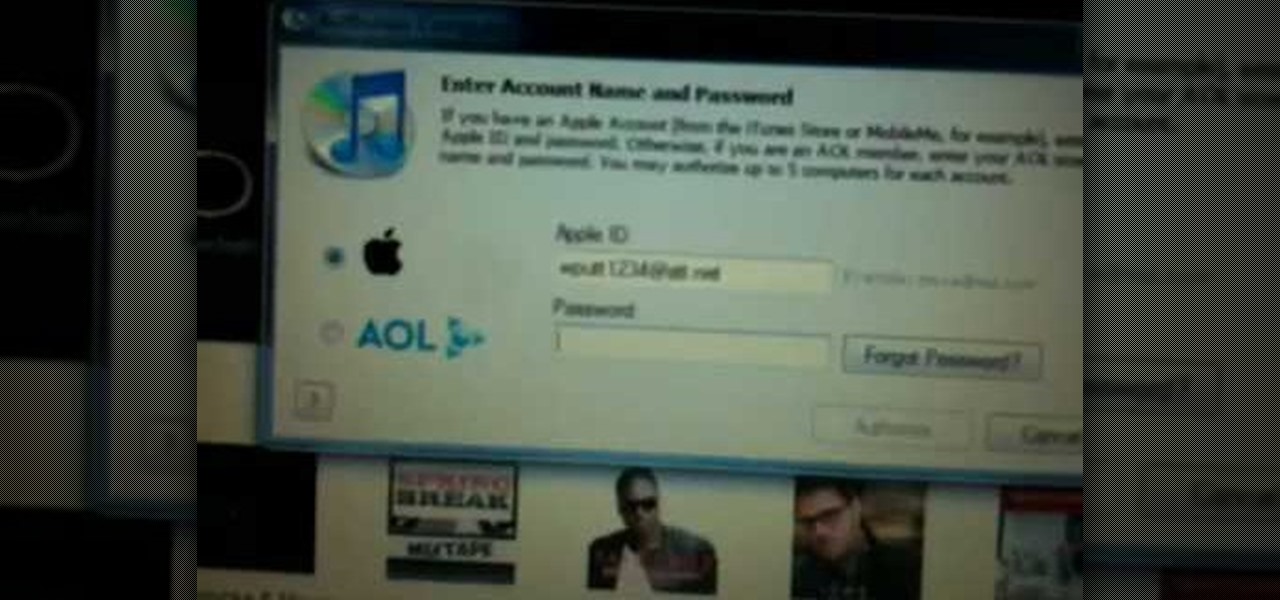
In this video from wadeputtii we learn how to authorize or de-authorize a computer on iTunes. Go to iTunes, sign into your account. Now click on Share and you will see Authorize Computer or Deauthorize Computer. If you want to authorize, click on that and enter your apple user email address and password. Then click authorize. If you have a new computer or you want to prevent someone else from using your account on your computer and you want to deauthorize your old computer, go to Share and De...

You may not realize it but when you buy music or movies from iTunes, you have to authorize it to be used on a computer and you can only authorize five computers. It's pretty easy to buy and replace computers and if you don't de-authorize the old ones, one day you will download a song and it will tell you that you have reached your five computer limit. At that point, what do you do if you don't have any of those computers anymore? Now Apple has put a fix in iTunes itself. Go to the iTunes stor...

If you like chips and don't have a massive overeating problem, you've probably had this problem: you're eaten half your bag of chips, but you don't have a bag clip to seal the bag and protect the freshness of your chips! Enter this video, in which a charming young Israeli teaches us how to fold a chip bag with an airtight seal without using a bag clip. You'll never have to eat a stale chip again!

The History Channel features great fighting tutorials on their show Human Weapon. Here they go into the ancient Israeli art of Krav Maga. Bursting will counter a surprise attacker by hurling your power into their core and blocking their weapon from striking you.

This tutorial shows you how to use the star took and a few other basic functions with Adobe Illustrator 5 to replicate the Star of David on the Israeli flag. Master a few basics of image manipulation with this tutorial.

Watch this instructional video to learn how to make kadaif. All you need is kadaif, sugar, date syrup, cheese, and hair hallavah. This is supposedly the best dessert in town and it looks incredible. This recipe is from Israeli.

If you don't know exactly what goes on during Hanukkah, this series of videos will set you straight. Hanukkah is the most recognized Jewish holiday, right around Christmastime, and Chaim from Maoz Israel is going to show you some traditional customs that are performed during the eight days of Hanukkah 2010. Learn about the menorah, sufgaiyots, the mysterious dreidel and the traditional Chanukah songs.

Kelly Campbell explains the disarm while doing gun from behind defense. This time when an attacker is pushing you forward.hing gun from behind at a distance defense. Krav Maga is the same brand of self defense used by Matt Damon in the Jason Bourne movies.

Make something easy that the kids will love too with this wonderful recipe for lemon chicken in garlic & herb butter sauce. Take your family dinners to new levels with help from this video.

A TFU was set up to review Navy service uniforms. This uniform is approved for E6 and below. It will replace the summer white and winter blue uniforms. This is how the female uniform should be worn.

Jarret Waldman explains a simple Krav Maga sweep technique

Krav Maga Worldwide Sherman Oaks Human Weapon Jarret Waldman teaching defense for gun to the head while kneeling executioner style.

A Krav Maga ground fighting technique for a quick release from the guard

Jarret Waldman explains why Imi the founder of Krav Maga uses a single handed defense instead two in other systems for gun from the front attack.

Krav Maga Sherman Oaks Human Weapon Jarret Waldman teaching a choke from behind with a thin wire or rope defense.

In this video series, our expert Julio Rivera will tell you all about krav maga, he will show you how o defend against a front choke, a side choke, and a rear choke. He will teach you how to defend against a bear hug, a wrist grab, and an escrima stick attack.

Despite how easy it looks in this video, finding and acquiring this rooftop wanted poster in Mafia II is not a simple task. But, if you're determined to get the wanted poster of drug trafficker Vladimir Semotan (aka Preacher), then follow along the best you can. Geoff and Jack from Achievement Hunter will show you the way to the roof of the Authorized Repair Shop to grab the poster, which will bring you one step closer to the Card Sharp achievement on the Xbox 360.

This is an electronic travel authorization system used to gain travel authorization to the United States. There are certain countries that fall under a visa waiver program, meaning that you do not need a visa to enter the US to visit. In that case you use the ESTA system. The countries that qualify in the VISA waiver program include Andora, Australia, Austria, Belgium, Brunei, The Czech Republic, Denmark, Estonia, Finland, France, Germany, Hungary, Iceland, Ireland, Italy, Japan, Latvia, Lich...

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

When it comes to Hi-Fi music streaming services, Jay-Z's Tidal is one of your only choices. But as you can imagine, true High Fidelity audio requires faster download speeds than your average music service. So the question becomes, how do you listen to Hi-Fi tracks on Tidal when a speedy internet connection isn't available? Offline music is the answer.

In late 2012, Instagram CEO Kevin Systrom made a sudden and controversial change to his social media service when he removed Twitter Card support.

I am a graphic designer, so I have to collect massive pics from webpages to provide me with inspiration. But sometimes I need to use them everywhere, even if I've no access to computers or laptops, so I have to resort to mobile devices.

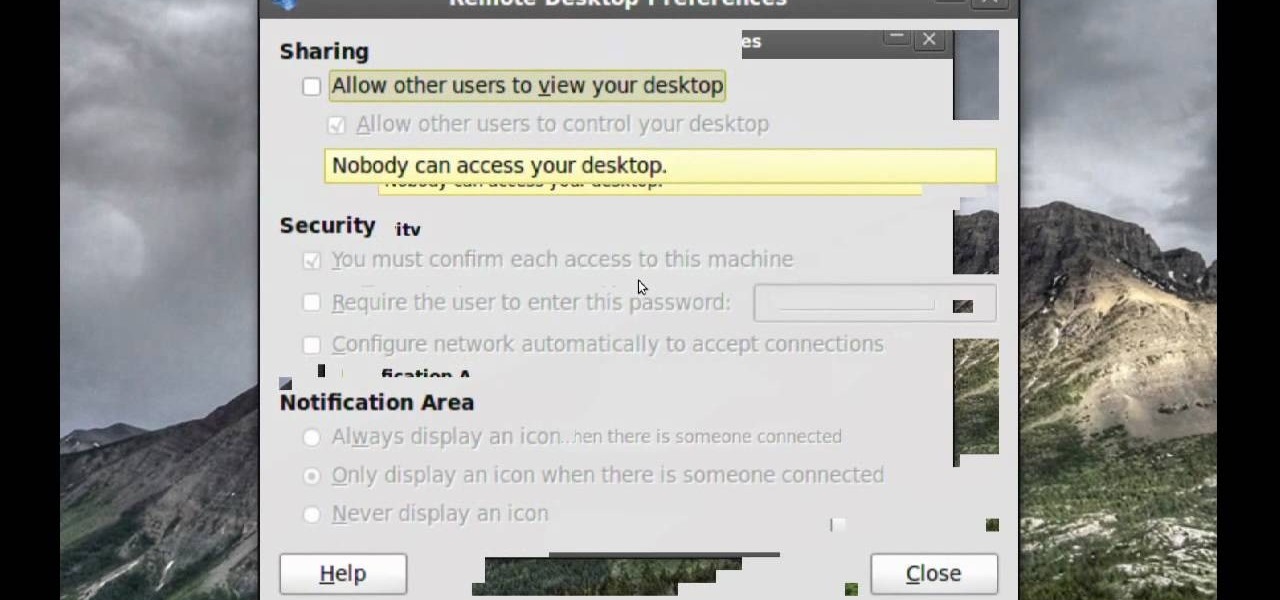
Remote assistance is a feature that, as its name suggests allows a user to remotely control another computer. The user can then use the remote computer in the same way as if the user is physically present there. Most modern operating systems support this feature.

Crakintosh.tk shows viewers how to easily SSH into their iPhone of iPod Touch with an easy method! First, you will need Cydia. Open up the program then go to Manage and click Packages. You will need to click Authorize SSH and Install this. Wait for this to download. Next, go to WinSCP to SSH into your device. The password will be Root and the login Alpine. Once you do this, you can now view all of your files and really do what you want with them. You have now just SSH'd into your device. This...

ClosetFool shows you how to disable UAC in Windows 7 and Vista. UAC is there to protect your computer by asking if you authorized the program to run or make changes. However, it can become annoying constantly having to click "continue" in the dialog box when trying to run programs. To disable it, first click the start button. Type UAC into the search box. The search should return with one selection. Click on it, and select whichever setting you like. In this video, ClosetFool set it to "never...

For those worried that a lustful gaze at a new app on their iPhone X will authorize its purchase, we have great news for you.

It really is a pain getting an Apple device fixed ... What's a gal to do when there's jelly stuck in your Macbook Pro fan and no Apple Store in sight? (Yes, this actually happened to me. Stop laughing.)

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Eating out is great, but being able to cook the delicious ethnic foods you eat at restaurants is even better. It may seem daunting to put together a bunch of ingredients with which you might not be familiar (some with names you've never even heard of!), but with the guidelines below, you'll be making your own versions of ethnic favorites in no time.

China's e-commerce site Alibaba has been making heavy investments in augmented and mixed reality startups. In February of this year, they led a $793 million round of Series C financing of Magic Leap. And now they've just invested in Israeli-based InfinityAR, which acquired $18 million in its Series C financing.

As you have no doubt observed, brothers and sisters do not mate. While they may find one another attractive, they find the notion of sex with one another repulsive. This is because a child produced by siblings has a high probability of sharing the same recessive genes, and recessive genes are often harmful unless coupled with dominant genes.

Stop me if you've heard this one before. A man walks into a bicycle shop, hears about a canoe made of cardboard and is inspired to make an awesome, fully-functional cardboard bicycle. Sound far-fetched? Wait until you hear how his guy actually did it. Israeli entrepreneur Izhar Gafni says that the idea for his method came from Japanese origami. Folding the cardboard increases its strength by 2-3 times, making the material much more durable. Essentially, he made the basic shape for each part w...

This video is provided by "Betty Sell" from AAA travels. In this video she tells about the international travel and also about the important documents to be carried while carrying out an international travel, that is the international driving permit, commonly called as an IDP. It's very important to carry an IDP while traveling overseas because an IDP acts as an important recognizable form of photo identification which helps us to communicate with foreign authorities. To get more information ...

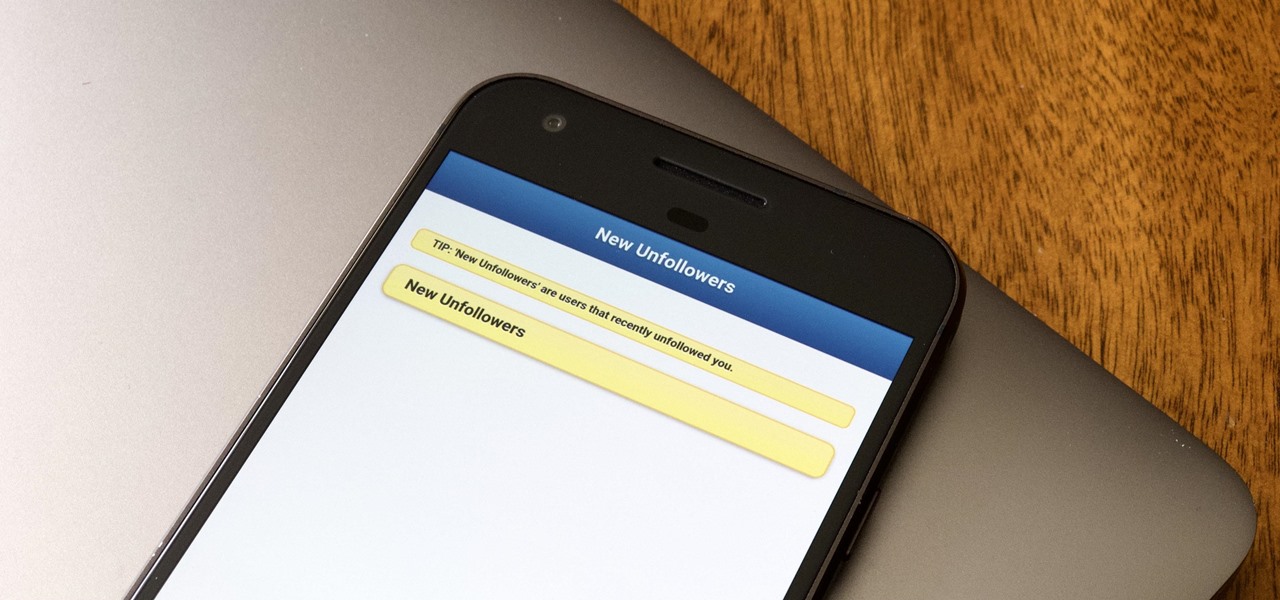
Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

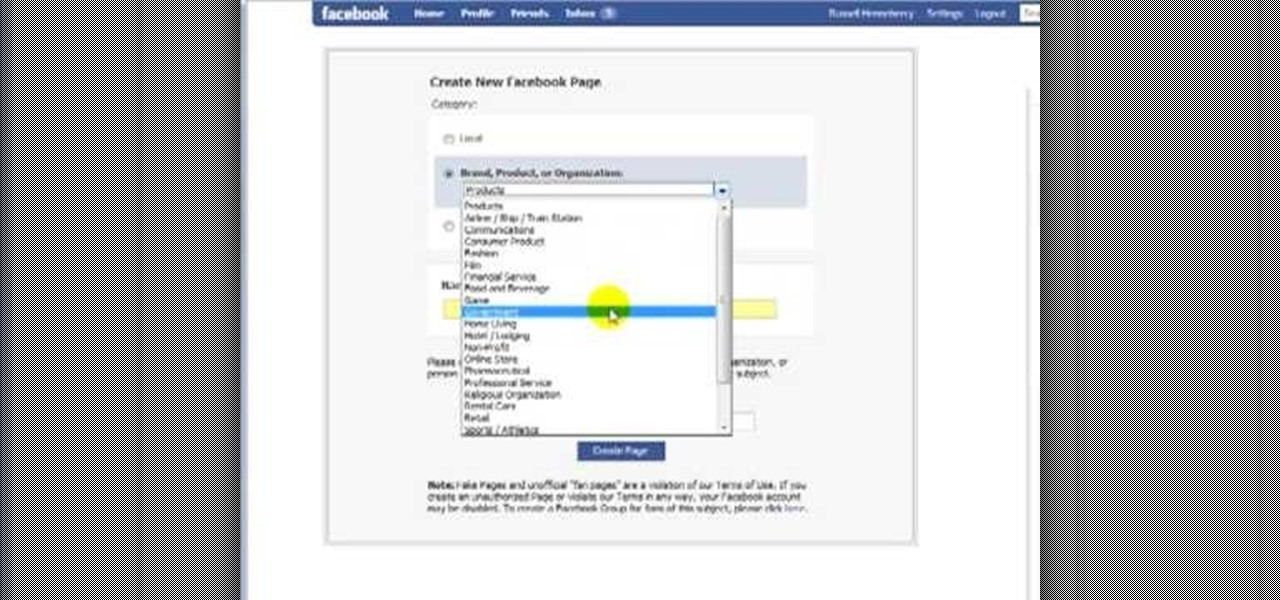
First, you must log on to your personal face book page or create one if you do not already have, but don't log in yet. Then at the bottom of the face book home page click the click here sign within the words to create a page for a celebrity, band, or business click here. Now that you are on this page log in. You will be able to select what you are. Enter name of your website, now select that you are authorize to create this page. You must then enter your electronic signature, which is the exa...

A Facebook page formatted specifically for non-profits can be created in a matter of minutes with this video tutorial from John Haydon. The first step you need to take is to search for any page. In this tutorial, Haydon searches for the page "Facebook Pages/Public Profiles" to use as the example. On the bottom left (of any Facebook page), you will notice that there is a link for "Create a Page for My Business." Click on that link, which allows you to begin the page creation process. Non-profi...

Apple released the third public beta for iOS 13.5 today, Wednesday, May 6. This latest public beta update comes exactly one week after Apple released iOS 13.5 public beta 2, which, among other things, introduced Apple and Google's joint COVID-19 exposure notification API. Public beta 3 updates that settings page to show a more detailed "Exposure Logging" option instead.