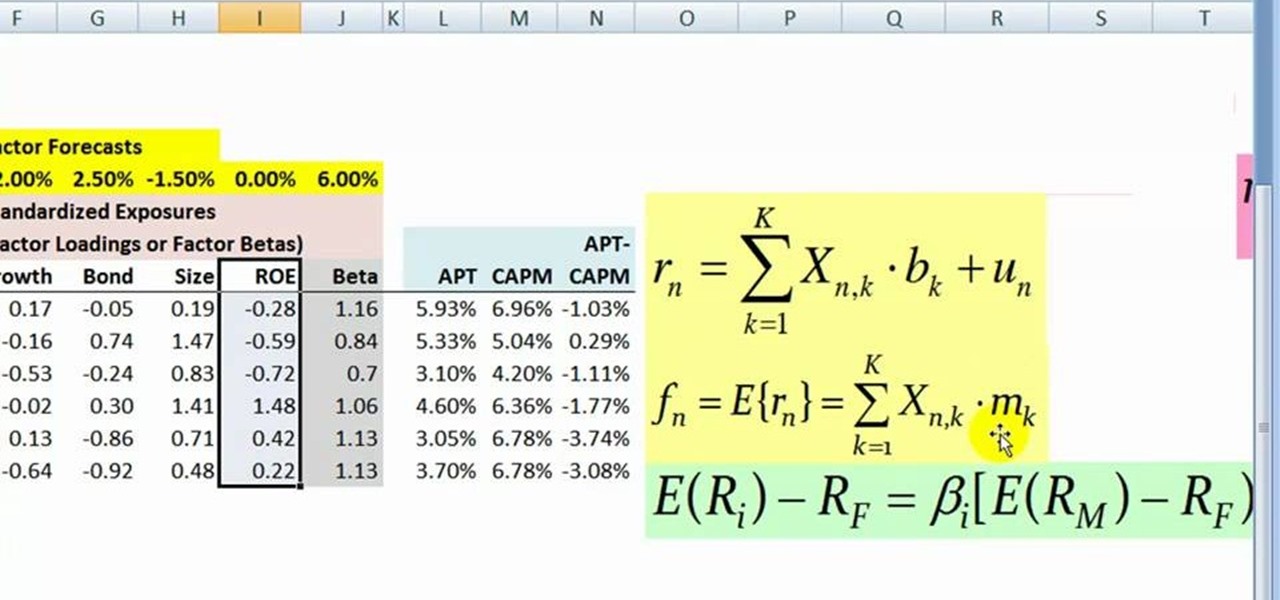
This video teaches you how to use APT (Arbitrage Pricing Theory) models and formulas. This video shows two specific parts of the APT models the first being the after the fact version and the before the fact version. The before the fact version is focused on as being the most important which is used to calculate expected returns to calculate risk. It is discussed how flexible this model is and how different factors can be moved in and out of the formula and how each different factor is used. T...
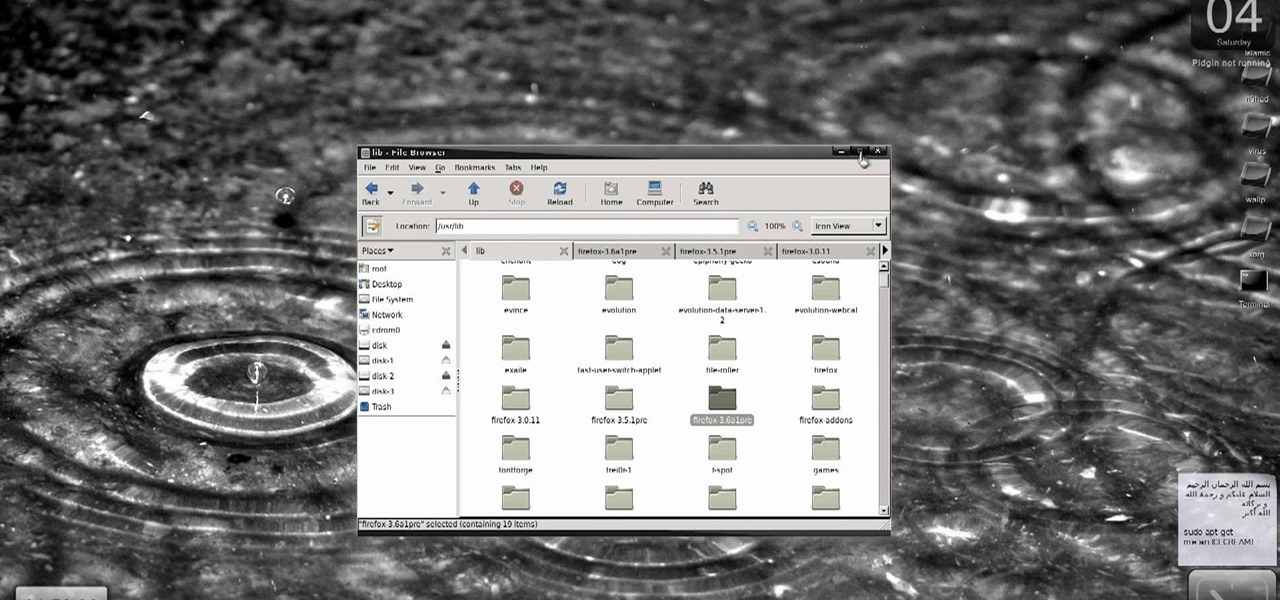
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install Firefox 3.5/3.6 and make it the default browser on Ubuntu Linux.
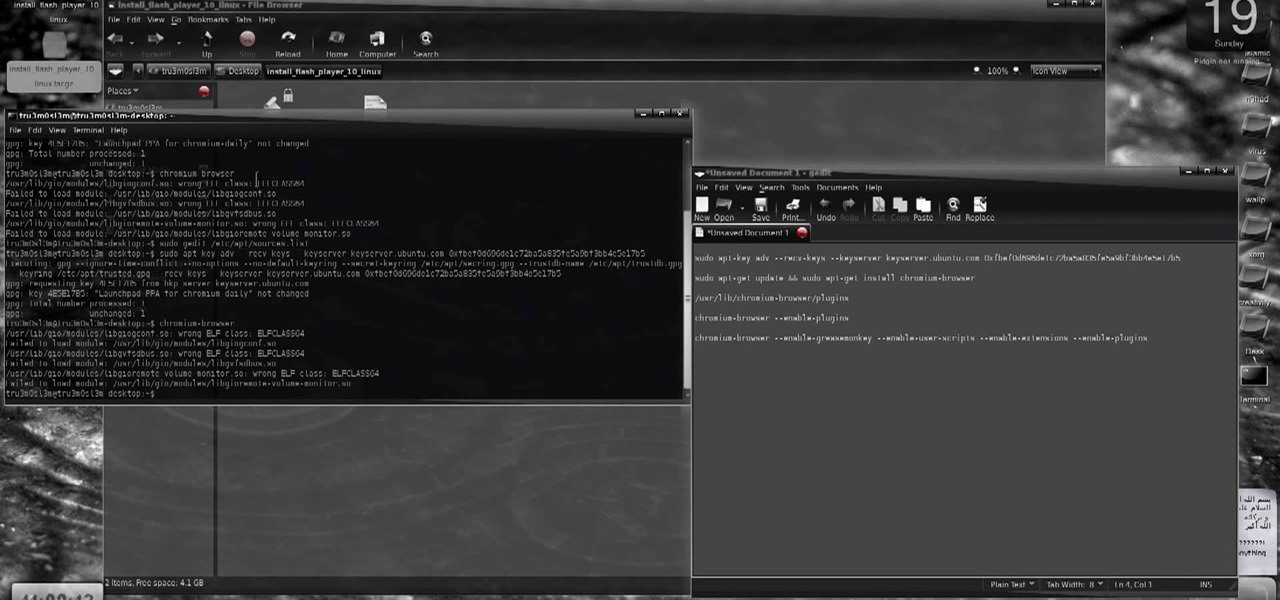
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install and enable Flash for Chromium on Ubuntu Linux.
Looking for a simple way to update your Linux distribution? This video tutorial demonstrates how to upgrade your Linux distribution via the apt-get command in the terminal. To get started using the apt-get update tool, press play!

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

The Nokia N900 smartphone suffers from a lack of quality games due to Nokia's restrictive OS, but fortunately you can get WebOS games from the Palm Pre loaded onto it pretty easily by following the steps outlined in this video tutorial.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

First of all, before we start, the modules and some of the tutorials belongs to Und3rf10w, not mine!

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install cool themes on Ubuntu Linux.

In this iPhone/iPod Touch tutorial, you'll find out the best way to get the rock app onto your device. The first thing you will need though is a jailbroken iPod Touch or iPhone in order for this to work and obviosuly Cydia donwloaded onto your device. Make sure to add this source in cydia: http://apt.modmyi.com/ Enjoy!

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install GRUB 2 and apply themes on Ubuntu Linux.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install Zekr (Qur'an Study Tool) on Ubuntu Linux, Windows, and Mac OS.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional TTF fonts on Ubuntu Linux.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

This video explains to the viewer the advantages of replacing washing machine hoses. As well as, rather more importantly, explaining how to complete the process. According to the creator the rubber hoses that are standard to most washing machines are subjected to high pressure water for many years. As they are only made of rubber they are apt to break and start leaking. This can cause many thousands of dollars worth of water damage. The creator recommends replacing the rubber pipes with reinf...

It's so convenient to take a screengrab of one of your most favorite moments from your favorite movie or show, but sometimes you just can't. But you can actually take a snapshot of it. Check out this video tutorial on how to create screenshots from videos on Ubuntu Linux.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

This video tutorial is in the Electronics category which will show you how to unlock your iPhone 3G on jailbroken firmware 3.0. By unlocking your iPhone you can use any GSM Sim carrier in your phone. For example, if you have an AT&T iPhone and you put a ROGERS Sim card from Canada, your iPhone will not accept it because it is LOCKED at AT&T. This is a software to unlock iPhones. Before you can unlock, your iPhone must be jailbroken. Open Cydia and hit manage. Then hit sources. Now select edit...

Purplesn0w and Purplera1n are both very powerful tools for jailbreaking an iPhone, and this video will show you how to use them! Before you begin, it's important to know that this tutorial will only work if you have 3.0 firmware. If not, download it, or check out another video that covers 3.0.1.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to update Nokia firmware via VirtualBox on Ubuntu Linux.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

There are so many Hollywood actors who simply love the fishtail braid hairstyle. From Tamsin Egerton to Cheryl Cole to Nicola Mclean, everyone gives thumbs up to this cute braided hairstyle. A lot of them prefer wearing it with their lovely gowns at award shows such as Cannes. It's not surprising at all as to why these celebs love this look- it makes the crown area of the head look voluminous, it can be done even with hair that has steps, it goes with every attire, apt for any occasion as it ...

Intricate designs are very common in mehendi for the dulhan, because it's her special day and she would most definitely want to amaze everyone around her.

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

Hello Everyone Today in this post I will teach you how to get a banner for your terminal.(Video Available at the End of the Post) To get a banner first we need "figlet" and then we have to configure it. Its Easy ..

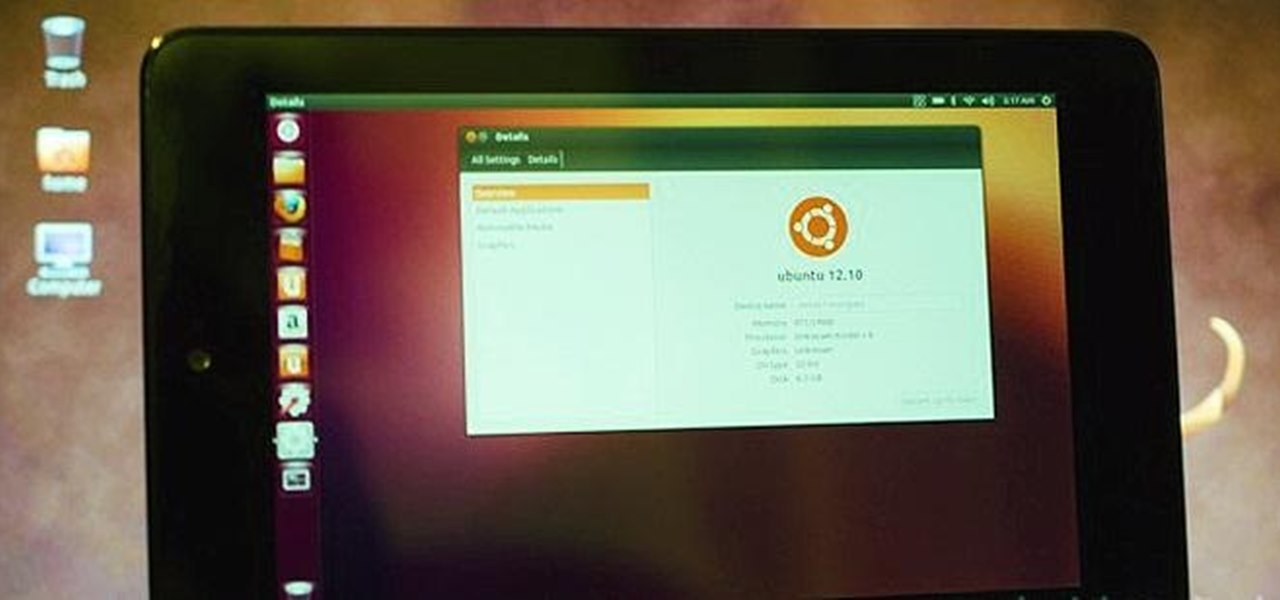
There's over 20 million people out there who use Ubuntu as their main operating system, and the number is steadily increasing due to its thriving community. While it's easy enough to download Ubuntu on your PC, the process to get it on your mobile devices can be fairly more difficult. Thankfully, it's not the hard to get Ubuntu onto your Nexus 7 tablet, but first you'll need to unlock it.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.