By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EXT Backpack Telescope to ogle the universe.

In this video tutorial, viewers learn how to create easy, natural openers when talking to women. Conversations can easily be started all the time based on simple observations. Usually guys make a mistake when they try to use a pickup line on a women. Pickup lines don't work because they're taking people out of a present moment. If you are walking around and observing something, chances are someone else is observing it as well. So if you and a woman are observing the same object, she will imme...

In this four part video tutorial series, learn how to write a 12 score essay for the SAT test in just ten days. The SAT essay is designed to measure your abilitity to develop a point of view on an issue presented in an excerpt, support your point of view using reasoning and examples from your reading, studies, experience, or observations, and your ability to follow the conventions of standard written English. Follow these steps presented in this video, and score at least a 10 on your SAT essay!

A short video dedicated to the DNA Phantom Effect and how it might be related to human emotion. The DNA Phantom Effect is a questionable discovery by Russian scientist and "father of Wave Genetics", Peter P. Gariaev. In 1985 the very first evidential proofs of DNA being able to maintain wave/field type memory were found. That same year, the "DNA Phantom Effect" was given its name after observations made by Gariaev stated that physical DNA somehow attracted and manipulated light in a vacuum ch...

Dr. Diana Wehrell-Grabowski provides a brief overview of Buckminister "Bucky" Fuller's accomplishments in this video tutorial.

This five-part series of videos chronicles firemaking in cold and snowy conditions using backpacking equipment only. The series shows the scenery, adventure, survival philosophy, and gear observations.

Learn how to pick a horse at the racetrack. Sure, you could just go with your gut. But if you want better odds, make your decision based on these factors.

Here is a video to help you with the left-hand reverse manoeuvre, which occurs on the driving test. There is a full explanation of the manoeuvre followed by an in-car demonstration. Make sure you keep your speed low and do plenty of observations when you perform this. It should help you along with your driving lessons.

Unusual magnetic phenomena observations are found here. First, we see a rotating and revolving ball magnet in a pyrex bowl. The revolving was expected; the rotating was not. Is this the same phenomenon as the Earth rotating around it's axis as it revolves around the Sun?

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

No matter who you are, a little self-confidence can go a long way toward making your dreams come true.

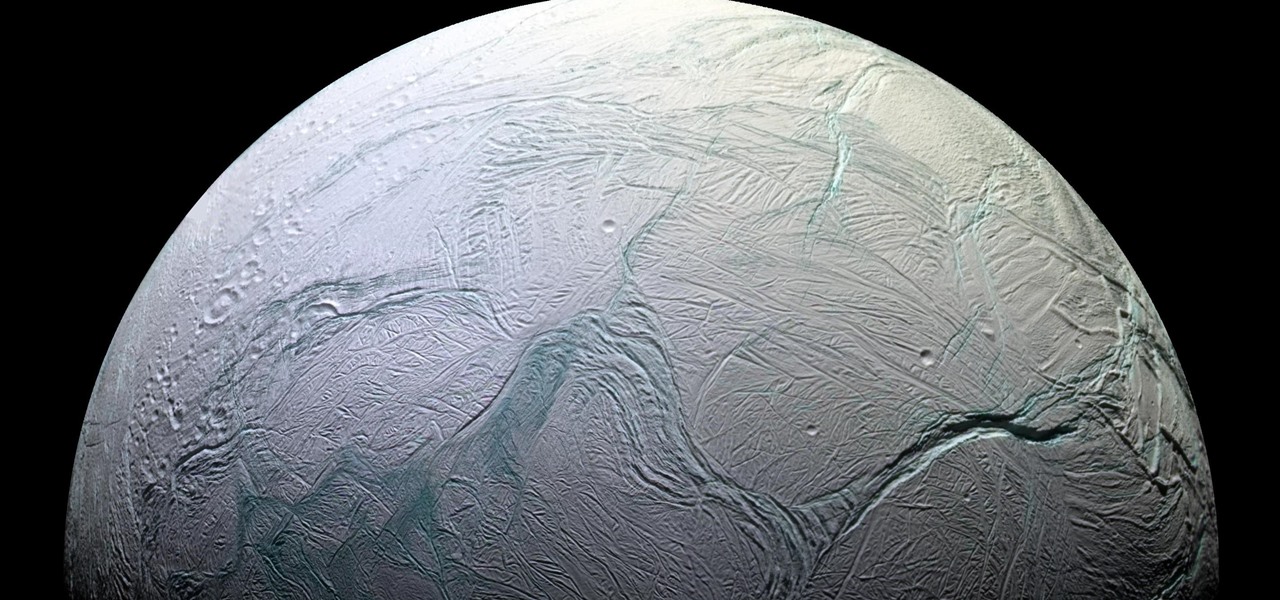
Earlier this year, NASA reported on findings that might point to water, and microbial life, on moons orbiting Jupiter and Saturn. Named Europa and Enceladus, those moons contain large oceans under their icy surfaces, which many speculate could hold microbial life.

The food TV chefs prepare make our mouths water. From one scrumptious creation to another, they fly through preparation without frustration or error. They make us think we can do the same with similar ease and delectable, picture-perfect results. Some of us have noticed, though, that these TV chefs don't always adhere to the same safe food handling guidelines we've been taught to follow.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Already a dominant force at the box office, Marvel Studios appears intent on establishing itself as the ruler of augmented reality media as well.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

Life has many perils: parasites, predators, and pitfalls. Eventually, any organism will succumb, and if that organism has not first passed on its genes, those genes will face extinction.

How would you feel if the stethoscope used by your doctor to listen to your heart and lungs was teeming with potentially unfriendly bacteria?

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Overweight kids often become overweight adults. New research suggests a couple reasons why and suggested that there may be ways to intercept that fate.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

It is not just a bad summer for ticks — it has been a bad decade for the spread of tick-borne infections. New surveillance from the CDC reports rapid expansion and increase in cases of babesiosis, a sometimes life-threatening disease, in Wisconsin.

As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight.

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

The Nexus 5 has a known issue with its display. Affecting all models from the first manufacturing run and most models thereafter, this display issue is easiest to notice on something with a white background. A yellowish tint, most noticeable when compared to other devices, seems to emanate from the Nexus 5's screen.

Introduction So today and yesterday I was playing with TNT (as we all do at one point or another) and I was curious about a few things. From this curiosity, I went on to discover some of the science behind some things you may or may not have known.

Introduction So, today and yesterday I was playing with TNT (as we all do at one point or another) and was curious about a few things. From this curiosity, I went onto discover some of the science behind some things you may or may not have known.

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

It won't come as a surprise to hear that your cell phone, tablet, and laptop are loaded with bacteria and other organic material. While most of these bacteria are harmless, there are good reasons to reduce the capability of your mobile devices to infect you—or other people.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Unless you're a pretty avid home cook, you probably don't know a lot about sous vide. Sous vide is a low-temperature cooking method where food is cooked in vacuum-sealed plastic bags in a water bath for a prolonged period of time.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

If preorder delays are any indication, the iPhone X certainly has some buzz. But does the X have the quality to support that buzz in the long run? After all, a $1,000 (or more) iPhone feels more like an investment than a smartphone purchase. The question on any prospective buyer's mind should be, "Is this thing worth it?"

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

The year 2018 was a rough one for Snap, the company behind the Snapchat app and the Spectacles wearable camera device. From executive departures to reports of slowed user growth, the company that once spurned Facebook's multibillion-dollar advances is now facing a moment of truth as it stares down its uncertain future.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.