How To: Steal Wifi at Work and Unblock the Sites They Restrict
Just a little tutorial I put together for those that love to text at work or school or any other place really that you spend a lot of time in. I hope you enjoy.


Just a little tutorial I put together for those that love to text at work or school or any other place really that you spend a lot of time in. I hope you enjoy.

All you paying Spotify users are about to get another exclusive privilege besides getting out of all those annoying "Ever wonder what it would be like to have Spotify premium?" ads. The Sweden-based company is looking to lower the royalty fees they have to pay to major record labels for their music, by compromising on their policy that all their music be free to paying and nonpaying users. Spotify would for a limited time restrict access on major album releases to their paying subscribers.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.
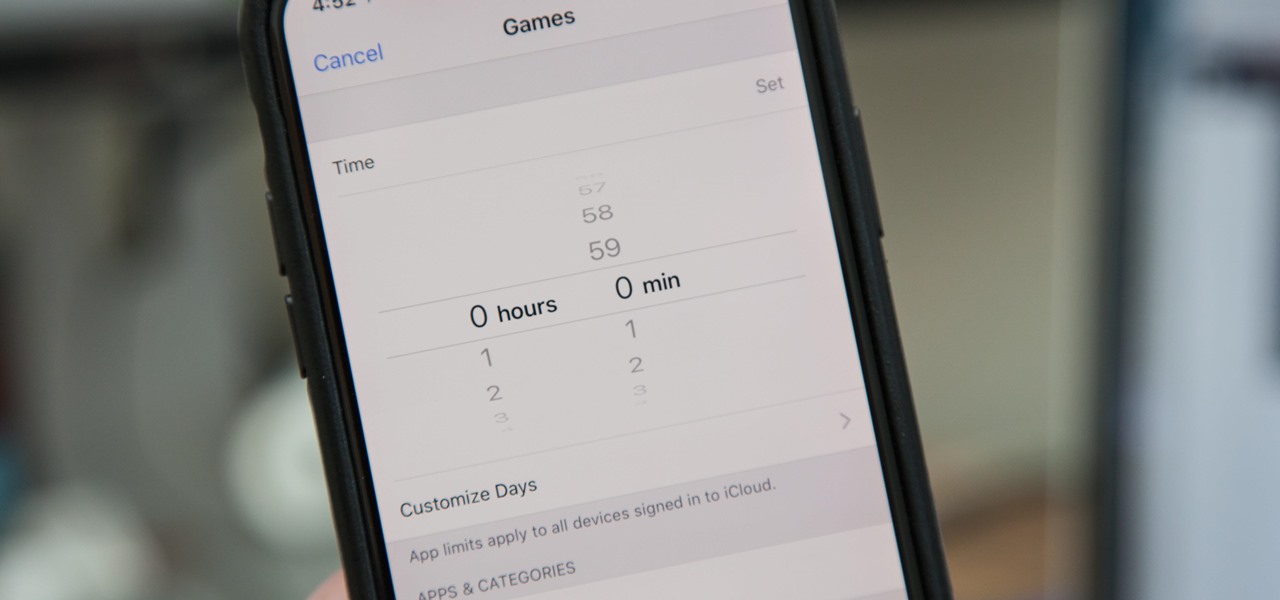
Most of us have, at one point or another, found ourselves glued to our smartphone in a trance-like state, totally unaware of what's around us. Well, Apple has a way to curb overuse with an awesome tool for iPhone starting in iOS 12. It can help nudge us away from our phones to spend more time attending to real-life matters.
For reasons unknown, Microsoft decided to change the way the Guest account feature in the new Windows 10 operating system works. In previous versions, the Guest account feature allowed you to set up a limited account for other users so they don't have access to your important documents and settings. Now, the process requires assigning an email to a new account and configuring share settings.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.
If you want to set privacy rules or moderate who has access to the different content that you share on Google+, take a look at this tutorial. It will walk you through the settings and features of Google+ that allow you to restrict who can view and see the information you post to your profile.
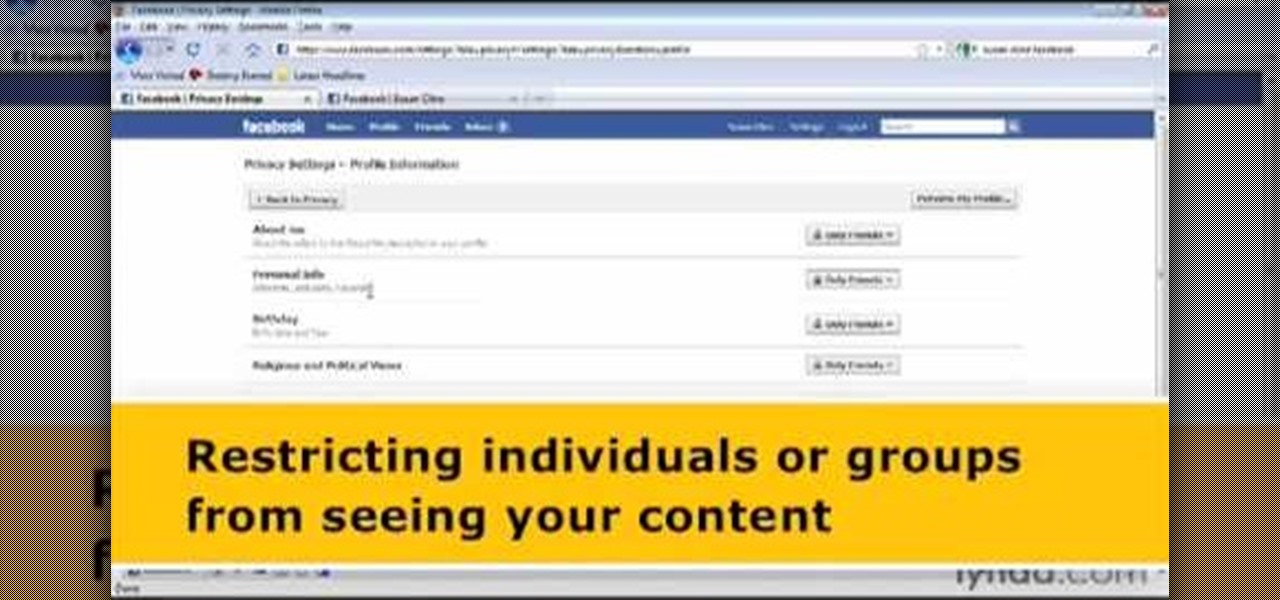
Facebook is one of the most popular social networking sites out there, so make sure you are being safe! Susan Kline shows you in her Facebook Essential Training series how to Restrict certain aspects of your profile. Login to Facebook and view your Privacy Settings. From there you can pick your About Me, Personal information, Wall Post, Photos and more and restrict showing it to people. You can pick everyone, certain friend lists, Networks, and even individualize it down to one person.
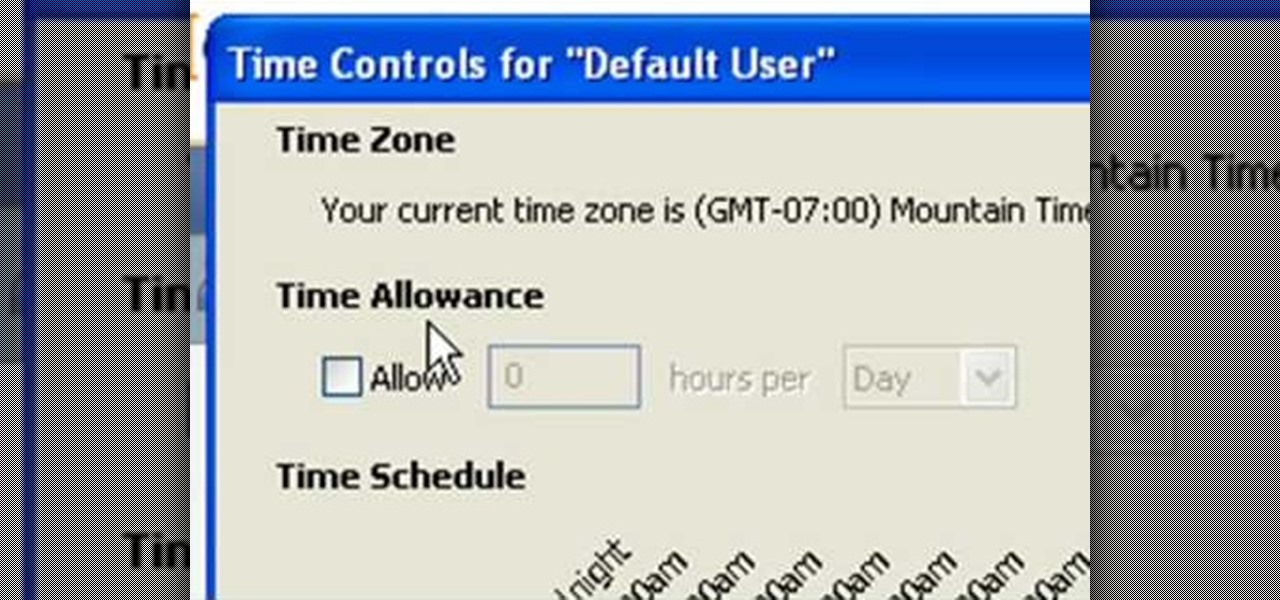
In this tutorial, Andy from TopTenReviews shows us how to restrict internet time usage with Net Nanny. First, open Net Nanny's dashboard and find where it says "time controls". You will see "internet usage", make sure you click on this. Now, a new window will pop up where you can choose time allowance, schedule times and blocks to your specific preferences. Once you pick these, click "ok" and your restrictions will be set and saved! This is a great way to control when your children and others...

A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.
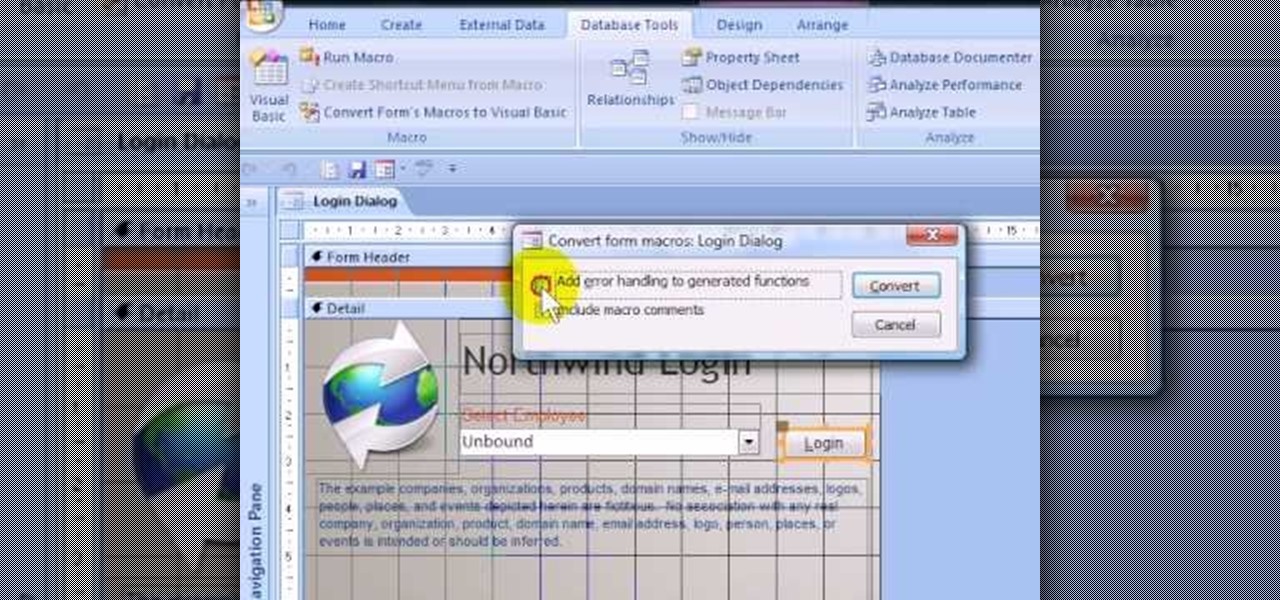
If you want to password restrict some of your data, or just want to know who is doing what in Microsoft Access 2007, you will want to set up a login form for MS Access 2007. This is an easy procedure, and you can create one yourself with just a basic understanding of the structure for MS Access. Watch this video, and Uncle Gizmo will show you how to do a login form and several other forms for MS Access.
Kids can have fun using the iTunes music store while parents still control the credit card and content their children can access. Parents can restrict access to certain content, set up a shopping cart to review music choices before they're purchased, and give kids a monthly allowance.
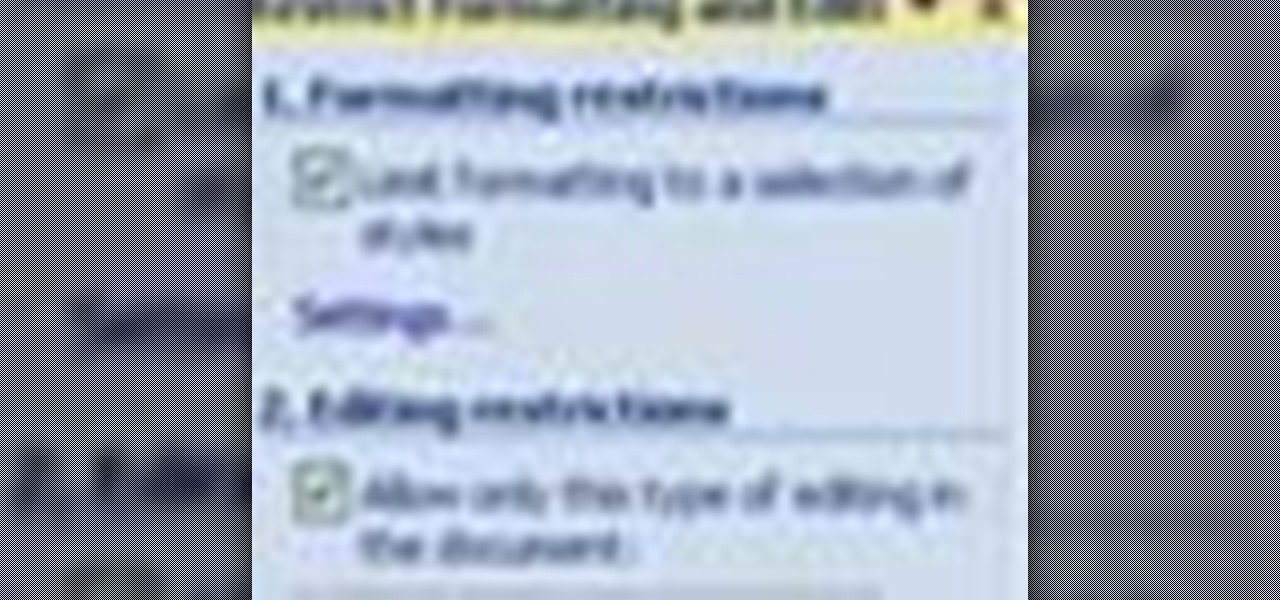
In this tutorial, we learn how to prevent edits or changed in documents in MS Word 2007. Start by going to the review tab, then click on protect documents. Then, click restrict formatting and adjust the different settings. Click on the check marks to choose what types of settings you want to restrict from being changed. This can make it impossible for anyone else to edit the pages except for the original author. You can also make an enforcing protection password so only the document creator c...
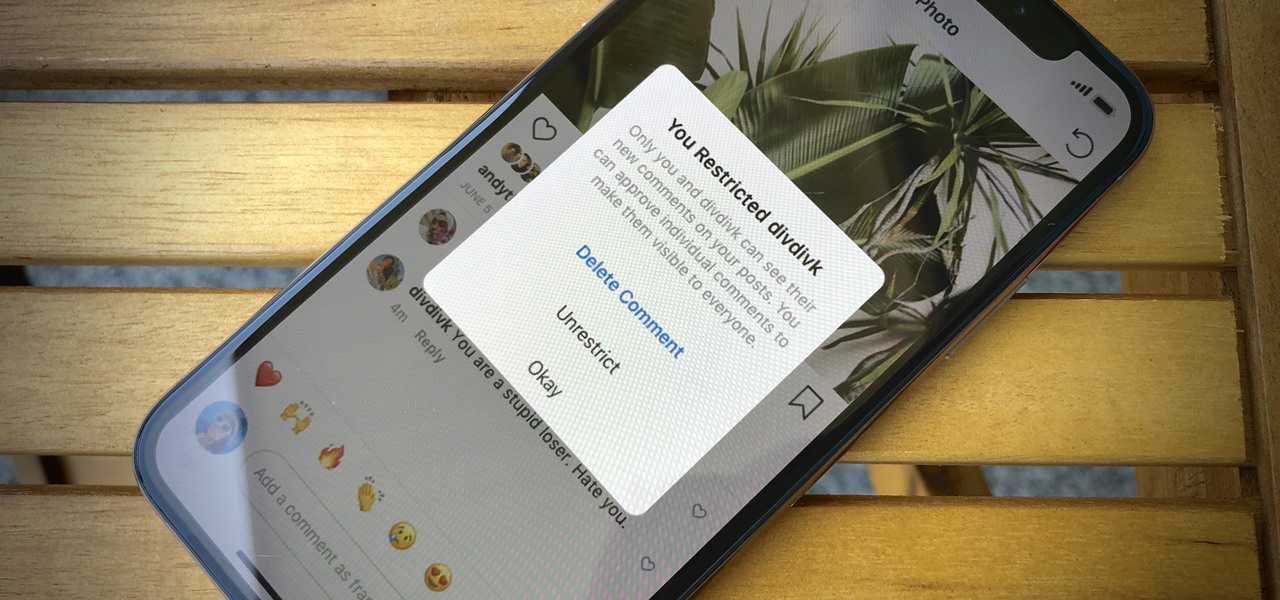
In general, the internet can be a cruel place, and Instagram is no exception. Most of the time, the platform is a fantastic way to share and view unique and creative content, to reach an audience of both fans and friends. People can step out of line and harass or bully others on posts to the detriment of the entire community. However, this type of commenting won't be sustainable for much longer.
360 degree panoramic viewers are a staple of all kinds of websites from real estate to auto sales. This video will teach you how to create a a 360 degree view that will display on your website using Flash CS3 and Actionscript 3. Don't restrict your users to just one photo, let them see all of whatever you're showing them with the tools your learn in this video.
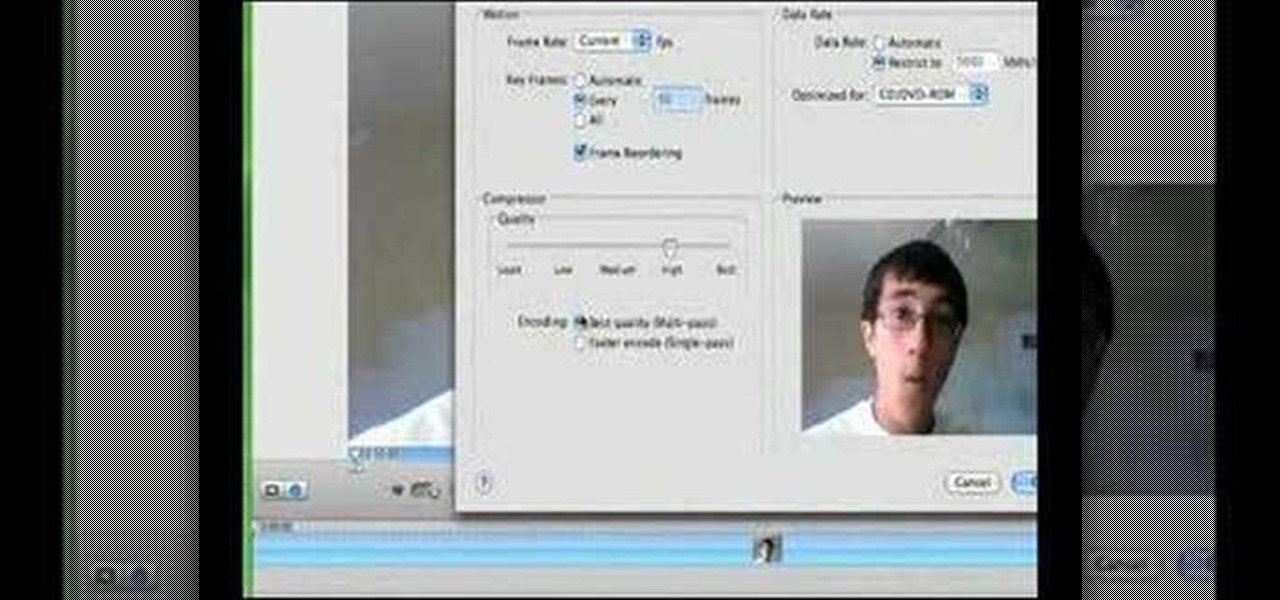
In this how-to video, you will learn how to compress iMovie files into QuickTime files to make them look really good on YouTube. First, open iMovie. Click Share and click Share again. Go to Expert Settings and click on Share. Click on Options and go to Settings. Change it to h264, current frames per second, and every. Restrict should be set at 5000. Optimize it for DVD and change encoding to best quality. Change the size to NTSC 720X486. Check de-interlace video and hit okay. Change the sound...
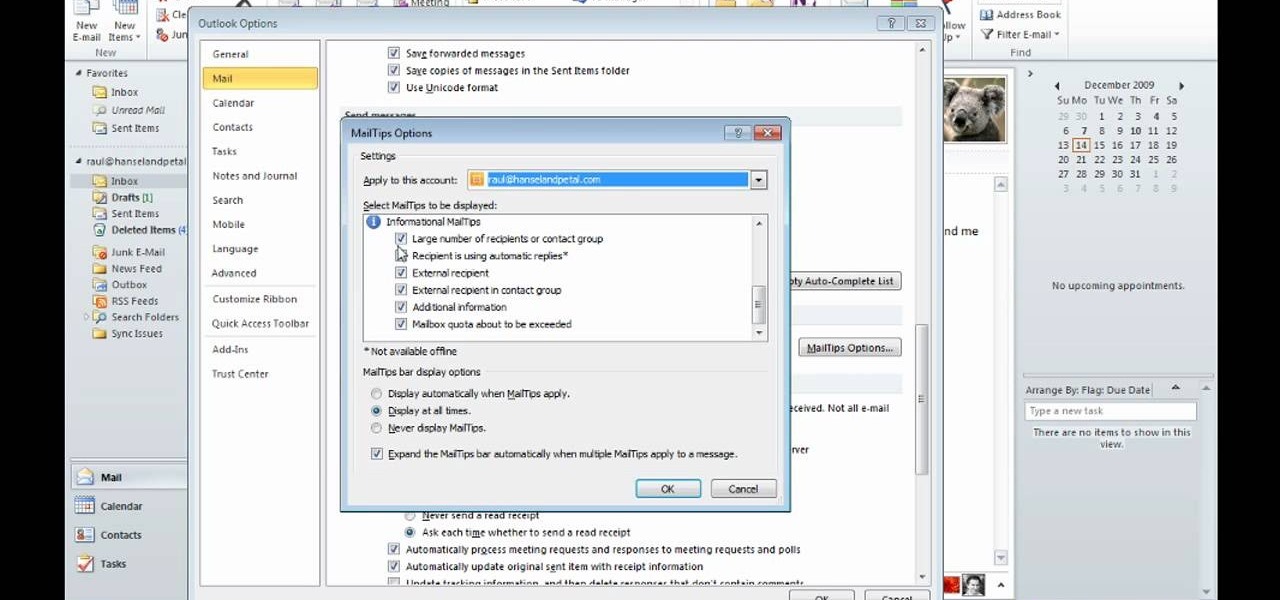
David Rivers is back to give us some more tricks on using MS Outlook 2010. In this video he tells us how you can avoid sending email to the wrong person by setting up some email preferences in MailTips. MailTips actually has the ability to alert you when you are about to send an email under certain conditions. Don't worry about sending an email to your boss that was meant for your co-worker. Your MailTips folder contains many options that you can use to restrict some of your outgoing mail and...

Childhood obesity is becoming a national epidemic. If we don't improve what our kids eat soon, the next generation will have a significantly shorter lifespan. Instilling good eating habits when kids are young makes it much easier for them to stay healthy as they grow older.
In this video the instructor shows how to set parental controls for a user ID account in Windows 7. To do this go to the 'Start Menu' and go to 'Control Panel'. In the Control Panel window select the 'User accounts and Family Safety' link. There is an option called 'Set up parental controls for any user'. Select that link and it opens a window where it asks you to Choose a user and set up parental controls. There you are presented with some user accounts that are currently active on that syst...

Not exactly sure how to get a hold of a death certificate? Whether you need a death certificate to trace your family history or to make a legal claim, follow these steps to get the record you need.

Is the proper term nudists or naturalists? Doesn't seem to be too much of a difference, because when it all boils down, they're both still butt-naked on the beach. Nude beaches are fascinating places for the adventurous spirit, but unless you’re an old-time nudist, you probably have questions about the proper way to behave on a nude beach. Well, we’ve got the answers.

Super Fly Life brings this traveling video tutorial to teach you how to travel with a cat on an airplane. Traveling and need to fly with your pet kitty? Learn these five travel tips, from cat carriers to travel accessories to supplies, go with style and grace.

Chess is a strategy and logical deduction game between two players that is enjoyed by children and adults alike, from park benches to convention halls across the world. Though the game of chess has taken many variations over its long history, today's form involves black and white teams orchestrated by players and has even entered the digital age, as games and tournaments are played online and via email. Using a square board composed of grids and smaller squares, the game pits a queen's army a...

You'll of course want to set up an admin account when you create your own website, so you can restrict access for everyone else but the admins. This tutorial shows you how to set up an admin account on your website using Dreamweaver.
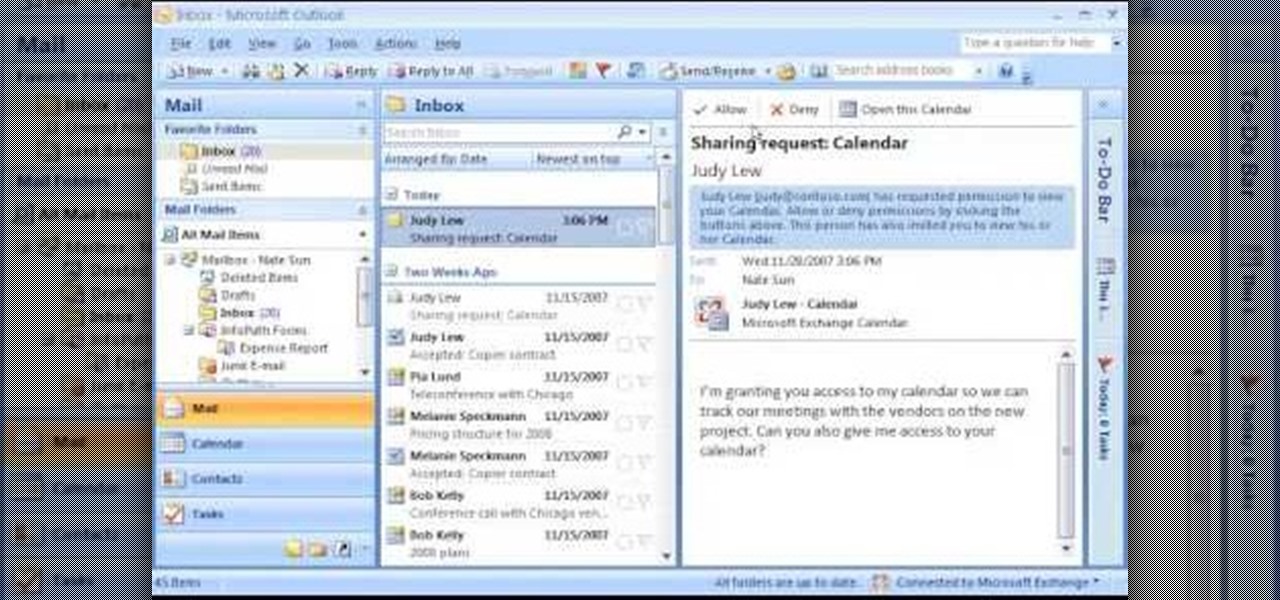
This tutorial shows you how to share your calendar three ways in Microsoft Office Outlook 2007. If your company uses Microsoft Exchange Server, you can share your calendar within the organization by using that feature. You can also send a snapshot of your calendar in e-mail to people outside your company. And you can publish your calendar on the Microsoft Office Online Web site and restrict how much detail is shown and who can access it.
Using ASP.NET Secure Services and Applications Services

It is a demonstration of a cream blush with a # 130. We will be using a steela convertible collar and a color called camellia which is #1 and is used mostly as a blush which nice and bronzy. You firstly stamp the brush onto the blush and then lightly tap the brush onto your hand first so as to ensure you won't have too much of blush on your face.

When it’s that time of the month and a heavy period interferes with your lifestyle, it’s time to take action.

Step 1 In the Adobe Flash program, select “Flash File (Actionscript 3.0)” from the “Create New” menu. Switch the workspace layout by clicking on the dropdown menu in the upper left of the top menu bar, and selecting “Designer.” You can adjust the size and color of the document by adjusting the settings in the Properties panel.

In the unlikely event you're ever in a plane crash, these tips will dramatically improve your odds of walking away from it alive.
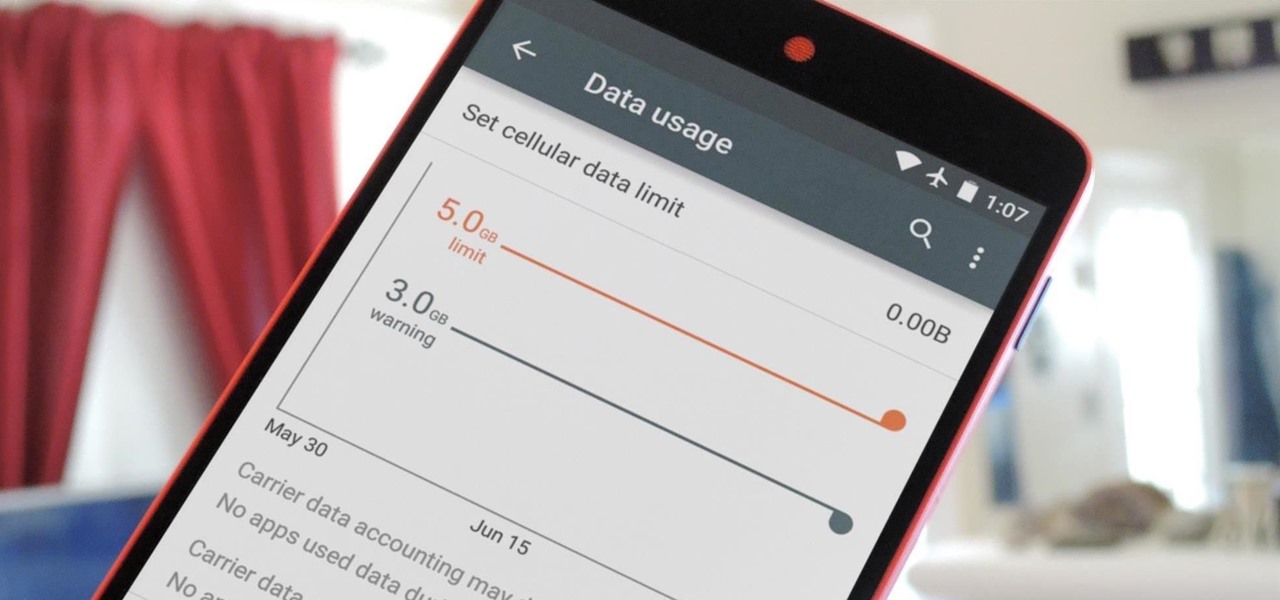
Ever watched Netflix on your phone only to realize an hour later that you forgot to turn Wi-Fi on? That's a whole lot of data used.
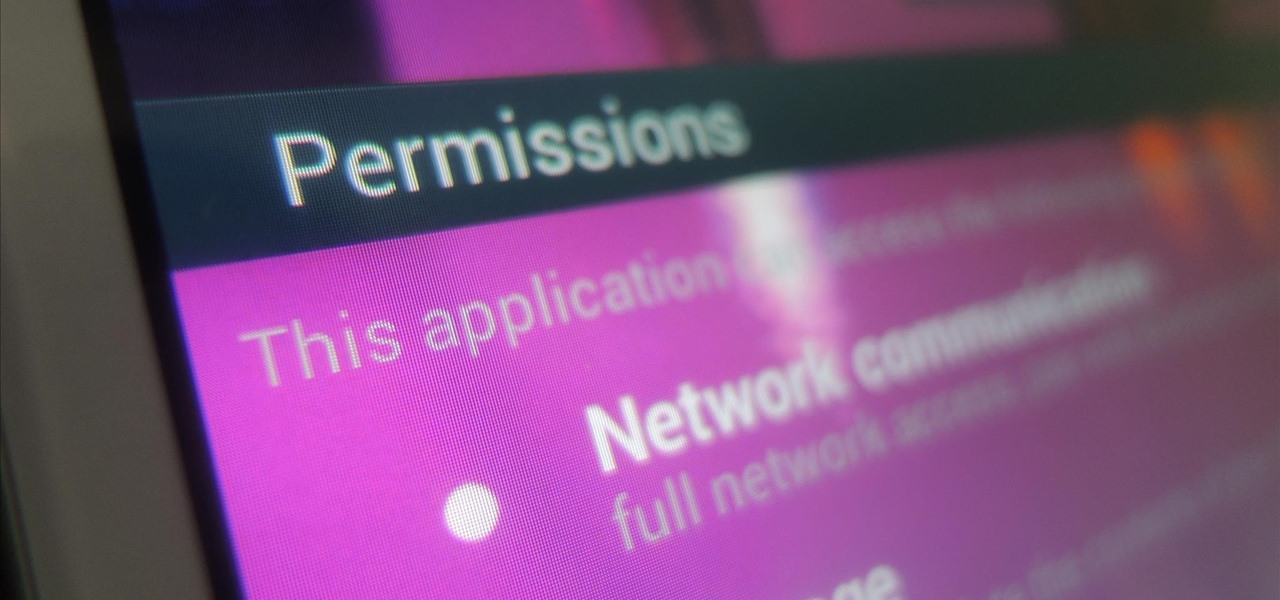
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.
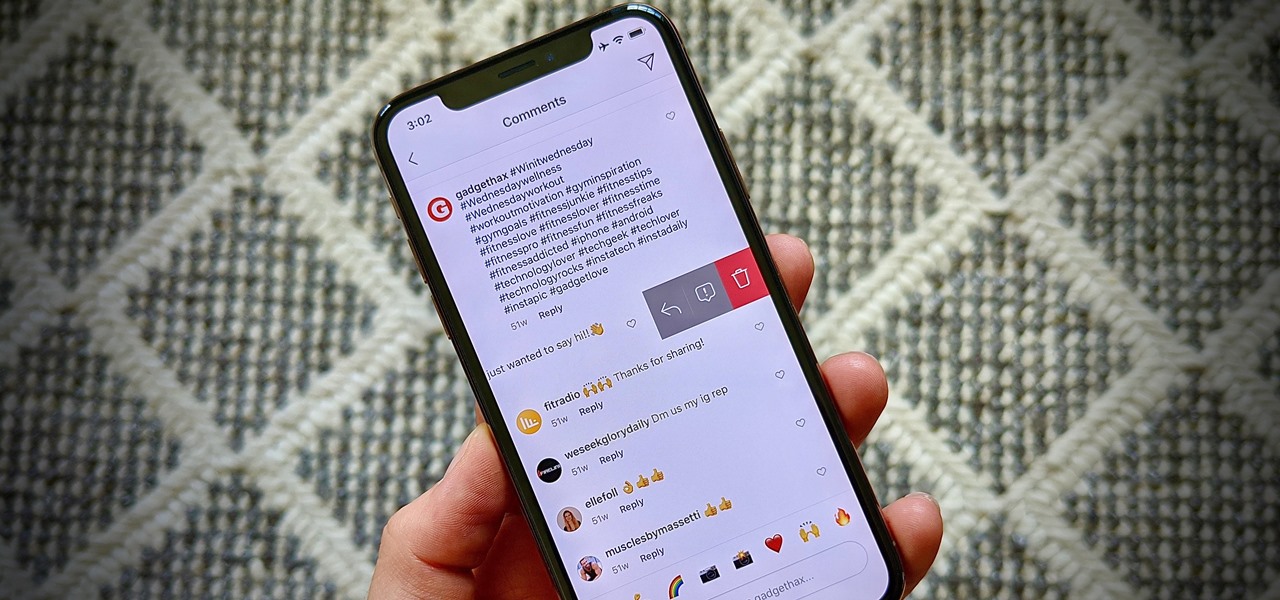
When you post a photo or video on Instagram, it's always nice to see positive comments from friends, family, and even fans. On the other hand, it's never fun to see spam or hate messages underneath your posts. Before, you'd have to delete these comments one by one, but now you can delete comments in bulk.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.
Keeping your Samsung Galaxy Note 2 clean and neat can become a hassle, especially if you're an app whore. As the amount of applications on your device goes up, so do your notifications, which will clog up your Status bar with icons alerting of recent news and tasks.

Among iOS 11's many criticisms, one of the more surprising complaints came from parents worried that Apple wasn't doing enough to monitor and control their children's iPhone usage. Apple seems to have taken these issues to heart, as iOS 12 introduces new and improved parental controls to help encourage healthier mobile habits for kids.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.
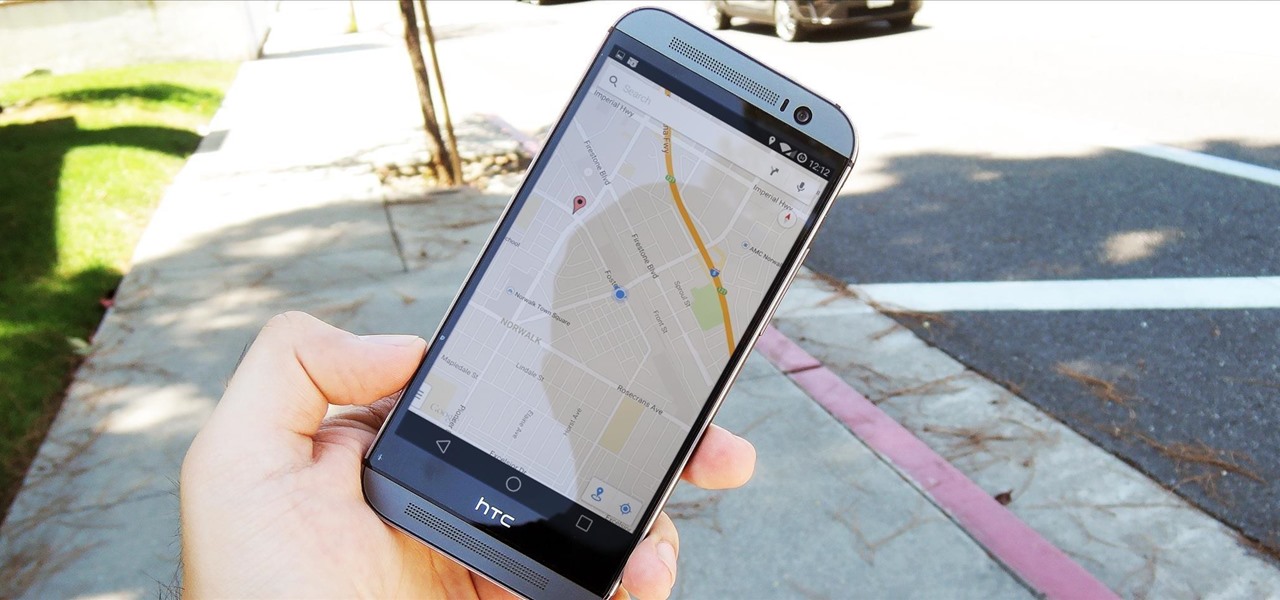
Google's Android Device Manager makes it extremely easy to track down your phone or tablet, but while it's simple to set up and use, it does require your device to have an active data connection, which can be an issue in some areas.
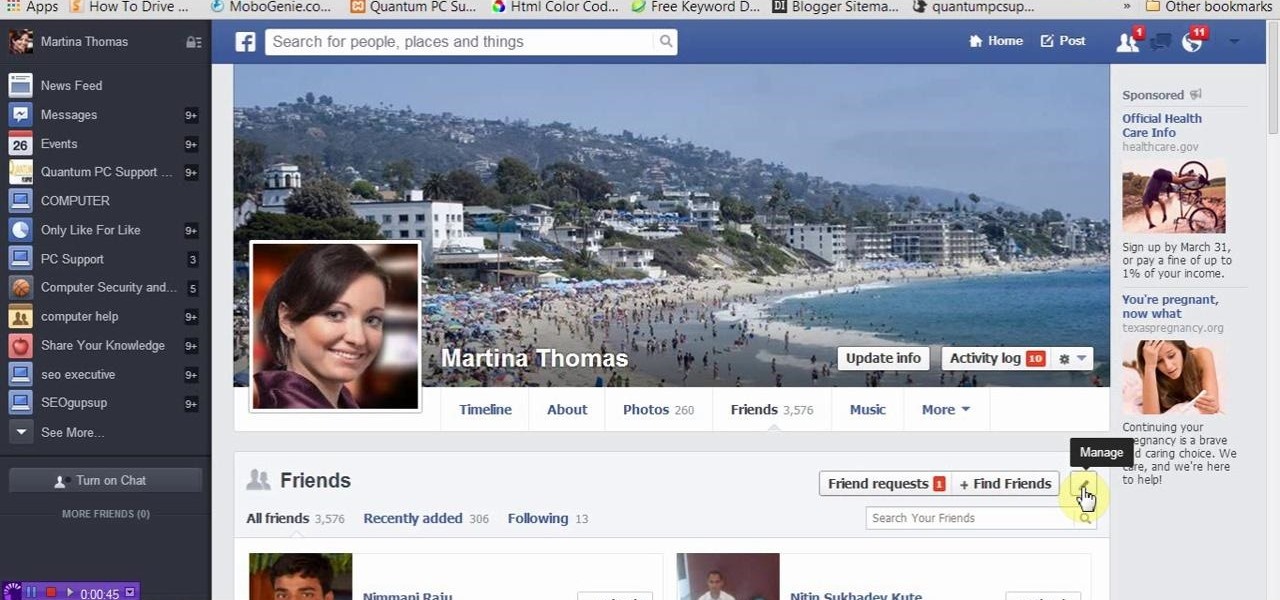
This tutorial video will show you how to hide Facebook friends list from public. With the help of this video you should restrict others from watching your Facebook friends list. Watch the video and employ the technique in your Facebook account.
This video will show you how to control and limit data usage in your windows 8 phone. You may want to restrict your data usage and want to set limits for apps also. If you set your usage limit internet will stop automatically after reaching the limit.