The Sanctuary menu system in Fable 3 has spawned some controversy, but it's pretty novel when you consider that there are a hidden Gold Chest and Gold Key right there in your pause menu! Watch this video to learn how to unlock and find the Gold Key and then the Gold Chest in your sanctuary.

MGMT is only two full-lengths old, but their impact on pop music has been massive. "Time to Pretend" has spawned legions of imitators, and for good reason. If you want to play a classy version of it, watch this video to learn how to cover the song on solo piano.

Silent Hill might be the single scariest game of all time, and it has spawned many sequels and films of wide-ranging quality. If you like the games and want to cosplay as one of the sexy yet demonic nurses from Silent Hill 1 and the film, this video will teach you everything you need to know, from what fabric to get to the pattern and how to put it all together.

Lady Gaga's landmark "Bad Romance" video not only ushered in a new era of avant-garde video making and performance art thereafter copied by Rihanna and Christina Aguilera, but also spawned a whole pack of makeup, hair, nail, and dance tutorials.
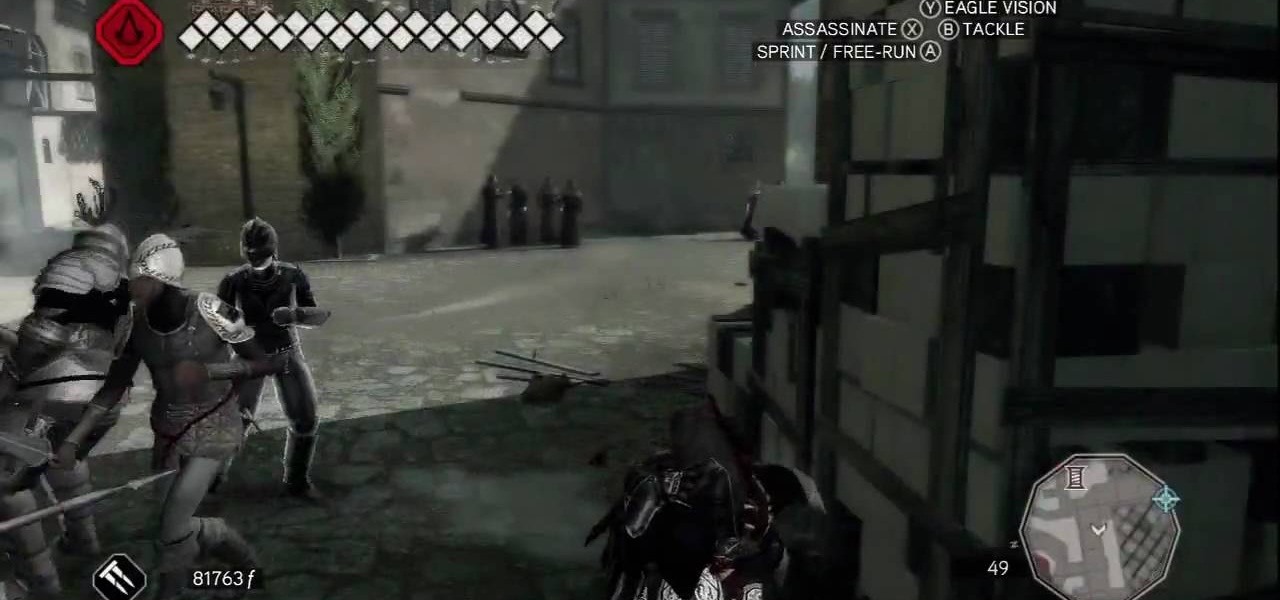
Assassin's Creed 2 was so popular of a game, that it spawned not one, but two downloadable content expansions, for both the Xbox 360 and PlayStation 3 versions. The first DLC was called The Battle of Forlì, and the second, Bonfire of the Vanities. This video game walkthrough focuses on the latter, in 1947 Florence, Italy, where the mass burning of sinful objects is an everyday event.

Sonic the hedgehog is the titular character of the media franchise of the same name which has spawned numerous games, animated movies, comics and TV series.

"She's Not There" is a great song from The Zombies in the 1960s, a top-ten hit in the U.S., and it spawned a number of covers, including hit version from his 1977 album Moonflower. Not quite as famous as the original, peaking at #27, but good nonetheless. And that's the version you'll be learning in this bass how-to.

I seriously cannot get enough of these sweet ass emblems for Call of Duty: Black Ops 2. Thanks to the new emblem editor, there's just so many possible designs to be made.

Portal, the popular game from Valve, has been critically acclaimed since its release in 2007. Its unique gameplay and humorous storyline is the reason for its popularity amongst nerds everywhere. This has also spawned a large community in cosplay and prop design. The most popular aspect of the game has to be the awesome portal gun. The gun creates companion portals on almost any surface that allow the player to jump form place to place with ease and also allows you to move heavy objects with ...

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

A little over a year after emerging from stealth, augmented reality gaming startup Illumix has launched its first title using a familiar formula, but with a new twist.

Already a dominant force at the box office, Marvel Studios appears intent on establishing itself as the ruler of augmented reality media as well.

When Magic Leap One owners unbox their new devices over the next few months (or, if they are lucky, days), they will have some familiar augmented reality news content to consume.

For social media platforms like Facebook, augmented reality represents a whole new art form with which users can express themselves online. Now, Facebook is giving those users a new brush.

If imitation is the sincerest form of flattery, then Niantic must be blushing constantly, as numerous copies of Pokémon GO have spawned over the past year or so, seeking to capture the same success, often adding the lure of tangible prizes from brand partnerships.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

A fresh batch of developer info has been revealed on Magic Leap's Creator Portal. On Thursday evening, the normally secretive company gave the general public perhaps the closest look yet at Magic Leap One's Lumin operating system.

Pokémon GO's augmented reality journey is continuing with Apple's newly announced ARKit. It's no surprise considering Pokémon GO is the largest mainstream augmented reality game, with 500 million downloads.

Text adventure games, such as the well-known Zork series, were some of the first computer games ever made, second only to the likes of Spacewar! and the better-known Pong. So let's travel back in time for a moment, to a time that never was.

A new dating app has arrived, and it'll finally land you a date with your celebrity crush ... kind of. The app — Dating AI — uses face search technology to help you search for potential love interests that resemble a celebrity you're attracted to.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

One of the more enjoyable parts of Christmas (other than opening gifts of course) is going out to find the perfect tree, struggle bringing it into the house, and decorating it. As the years went by, I realized that our tree looked exactly like every other tree in the neighborhood: the same lights, the same angel at the top, and the same red, green and white ornaments.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

There are two types of people in this world: those who recognize Wordle grids of yellow, green, and gray/black blocks and those who do not. No matter which category you fall in, there's a Wordle-inspired game that's perfect for you.

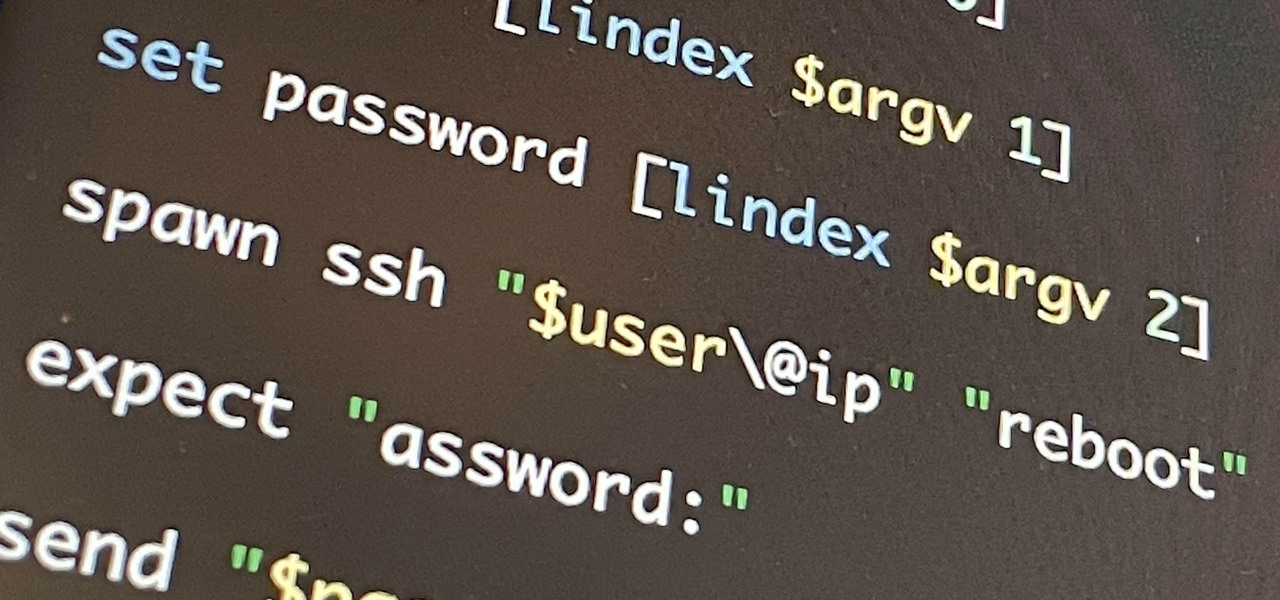
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate delivering an SSH payload with an "expect" script.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

When the topic of Pokémon Go comes up, the typical response is, "Do people still play it?" The answer is a resounding yes!

The popularity of breakdancing waned by the late 1980s, but has been recently rediscovered by a new generation of dancers who perform in professional competitions. While taking breakdance lessons might seem to violate the very ethos of the “streets” movement which spawned the genre, no one will ever know you learned the basics of breakdancing in a free online video course. Our expert dance instructor demonstrates the foundations of up-rocking, popping, locking, the six step, and power moves l...

While taking Breakdance lessons might seem to violate the very ethos of the “streets” movement which spawned the genre, no one will ever know you learned the basics of Breakdancing in a online video course. Expert dance instructor Julie Urich demonstrates the foundation of toprock, downrock, and power move steps you’ll need to ensure you don’t “get served” during your next battle.

Deadly natural disasters can happen at any moment— earthquakes, hurricanes, tsunamis, floods, fires and especially tornadoes. That's why you have to be prepared.

I spawned three ender dragons while in creative mode with world edit and flew down underground and dragons start destroying every thing. Awesome!

Angry Birds finally hits LEGOs. It was only a matter of time before some LEGO maniac constructed Angry Birds from those popular little plastic building blocks. Stop motion brickfilms are sure to follow.

Think beautiful bokeh photography + just a hint of TRON sensuality and you have photographer Audrey Penven's lovely series entitled "Dancing with Invisible Light: A series of interactions with Kinect's infrared structured light".