
Sillhouette Challenge: Into My Future I Suppose
Hipstamatic, Camera+.


Hipstamatic, Camera+.

Zombies have followed hot on the heels of vampires as the monster du jour in modern America, and this has been particularly pronounced in video games for some reason. Gamers dig zombies, we suppose. The zombie game folks are even developing some camaraderie amongst themselves, as evidenced by the easter eggs exchanged in Left 4 Dead 2 and Dead Rising 2: Case West. This video will show you where and how to find a Left 4 Dead 2 reference / easter egg in Dead Rising 2: Case West.
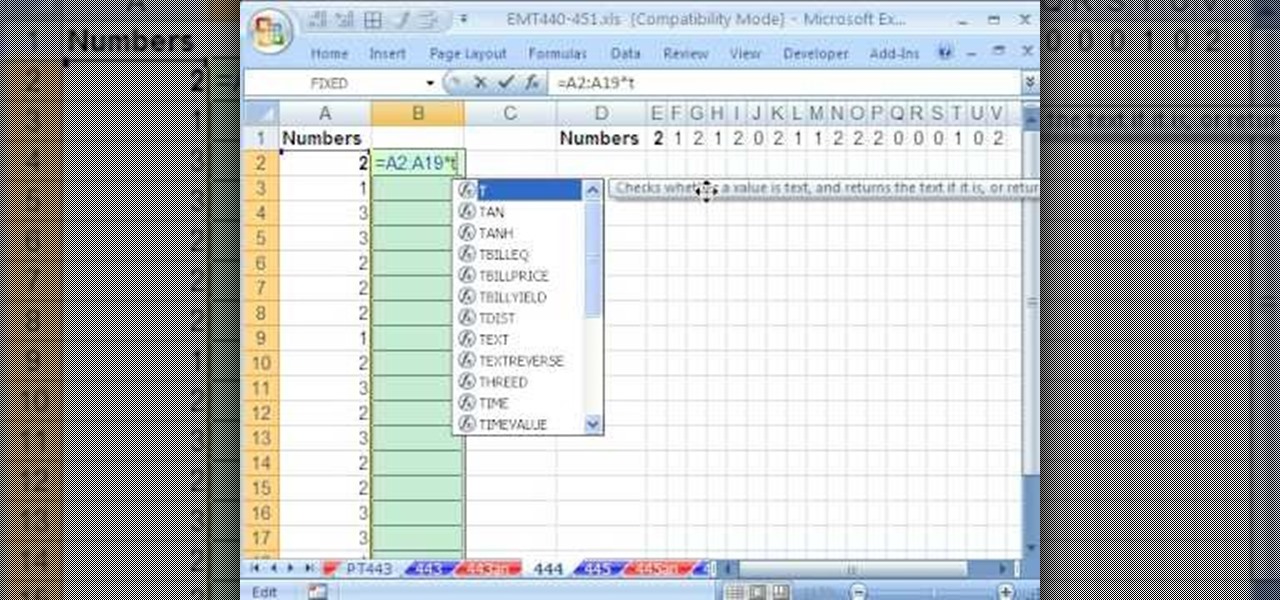
Description Of Excel Magic Trick 444-> to understand this you can also download it from EMT 440-451.

Learn how to tie an Anchor Hitch (also known as a Bucket Hitch) - A very secure means of attaching a rope to an anchor or any other object that you can't afford to loose (like a bucket down a well, I suppose - thus the alternate name). I actually do use this hitch for temporary anchor attachment (preferring to permanently splice instead) as well as for my bucket lanyards when washing down my boat's deck.

This video teaches us the method to write an equation in slope intercept form and to graph it. The equation of line is y = mx + c. m is the slope and c is the y intercept or the point where it crosses the y axis. Let us find the equation of line if it crosses (8,6) and m=1/2. Substituting the values of x,y and m we get 6=(8)(1/2)+b. Simplifying we get b=2. Substituting the values in the equation of line, we get y = m/2 + 2. Suppose we want to find the x coordinate of a point on the line given...

In this video, it teaches you how to do a dance move called the windmill. To start out you use the basic move with your right hand turned and left hand straight your elbow goes into your stomach. when you get into this position you lift your right leg up then your left leg and your right leg swings under. You want to turn yourself and push off with your arm that is in your stomach. It shows hints to make it easier for you to do and teaches you that the first windmill is the one you have to le...

Suppose you created a project plan in Microsoft Office Project 2007, and you want to add a new column of information. You also want to be able to choose not to display the new information, but you don't want it to be lost. Take a look at this instructional video and learn how to create a column, hide a column, and show a column that you previously hid.

Well, if you know a little bit about Rubik's Cube notation, and want to be a speed demon, then well, watch. If you know nothing about logarithms, then I suppose you should start somewhere else though. This is not for the cubing novices.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.
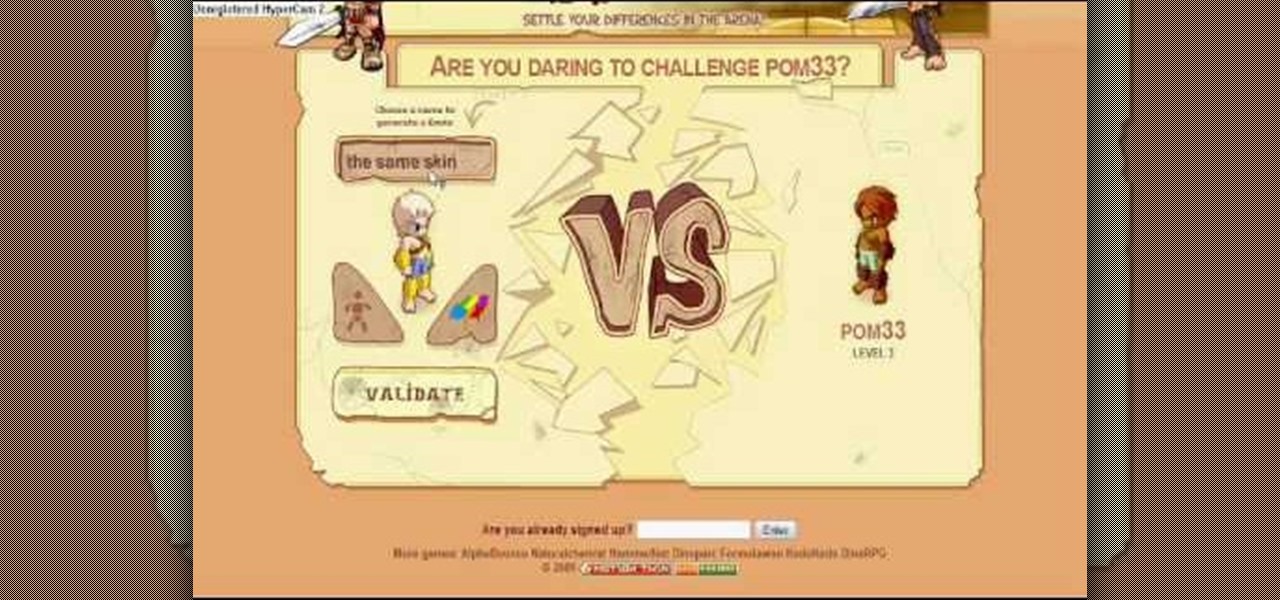
Click the more info tab to see the instruction on how to get a bear on Mybrute.com. This is a tutorial on how to get a Bear on Mybrute.com, An Online RPG Game, It's a very popular game that a lot of people plays everyday, You don't need to do much action with your hands just sit back and enjoy the show. Getting a bear is hard, because it's a extremely hard pet to get on mybrute.com, some sample pets are Dog,Wolf/Panther,Bear. If you can't read what I typed or did on to get a bear here's a lis...

We don't know how you feel about your little girl eating her favorite princess for her birthday, but we suppose this Cinderella cake is too cute to pass up...and to nom on.
Whatever happened to the mix tape? A few years back, there wasn't a better and more meaningful gift to give someone than a mix tape full of jams specially tailored to his/her tastes. But with MP3s and internet streaming being the most popular forms of music listening these days, we suppose it's no surprise the mix tape has died out like the dinosaurs.

In this Software video tutorial you will learn how to setup email in Microsoft Office Outlook 2007. Suppose you have a Yahoo email id and you want it in Outlook, go to tools > account settings > email > new and fill out the details. Then check the box next to ‘manually configure server settings’ and click ‘next’. In the next box, choose the 1st option and click ‘next’. To get the information for filling up in the next box, go to the Yahoo page shown in the video and copy and paste...

Learn how to find out whether your girlfriend is using you or she really loves you in simple steps. First remember that you can control only yourself and you cannot control the actions of other people. In this case your girlfriend must not still be ready for a longer steady relationship. If she is not allowing you to stay with every now and then, you can stop staying with her totally. Suppose she is suffering from any depression be there for her but don't stay with her whenever she asks to. S...
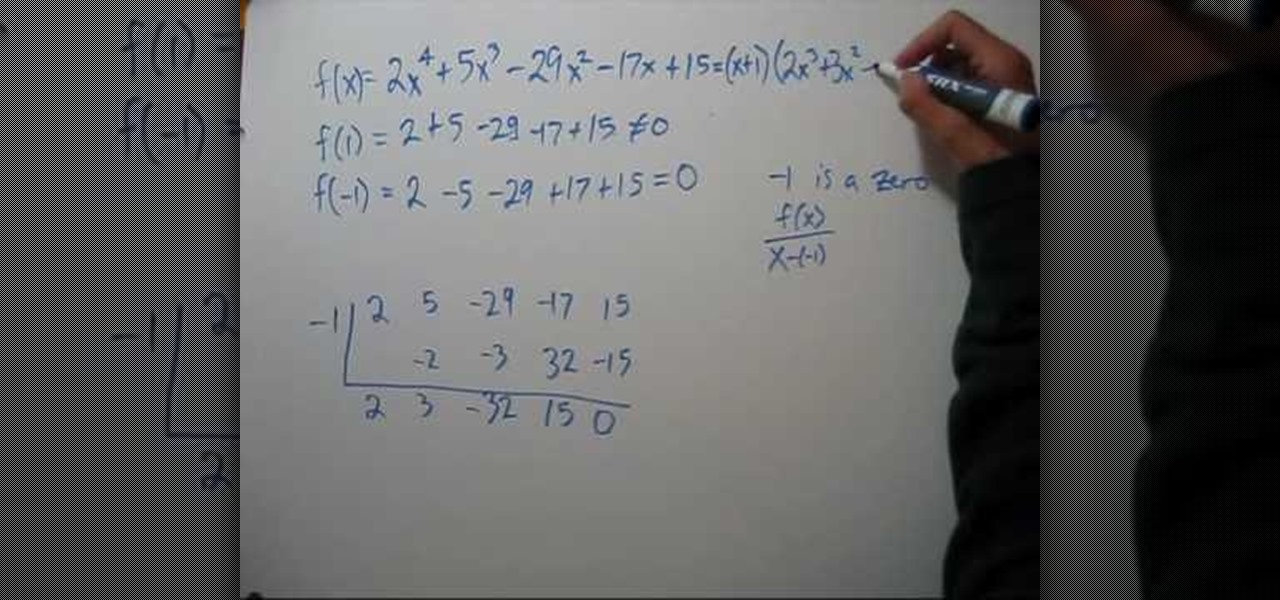
This is the video about how to Factor & find zeros of a polynomial. How did I know that x=1 and x=-1 were roots of the polynomial. Suppose the polynomial has a rational root, let's call it. I will assume that p and q are co prime, i.e., the fraction is reduced to lowest terms. What we will be doing is somewhat similar to "factoring by guessing" of quadratic polynomials. Since is assumed to be a root of P(x), we know that if we multiply both sides by, we obtain: Transfer them to the other side...

Learn how to do a rotation in geometry with this video! First step is to pout the pencil into the compass. Adjusting the pencil and compass needle is same. Suppose you want 165 degree size circle. Measure the reading with compass in protractor. Note the point and adjust the compass. After place the sharp end of the compass at the point and rotate the compass the circle will enabled. Next use protractor. We see 75 degree acute angle. Place the protractor on the line and mark the reading we wan...
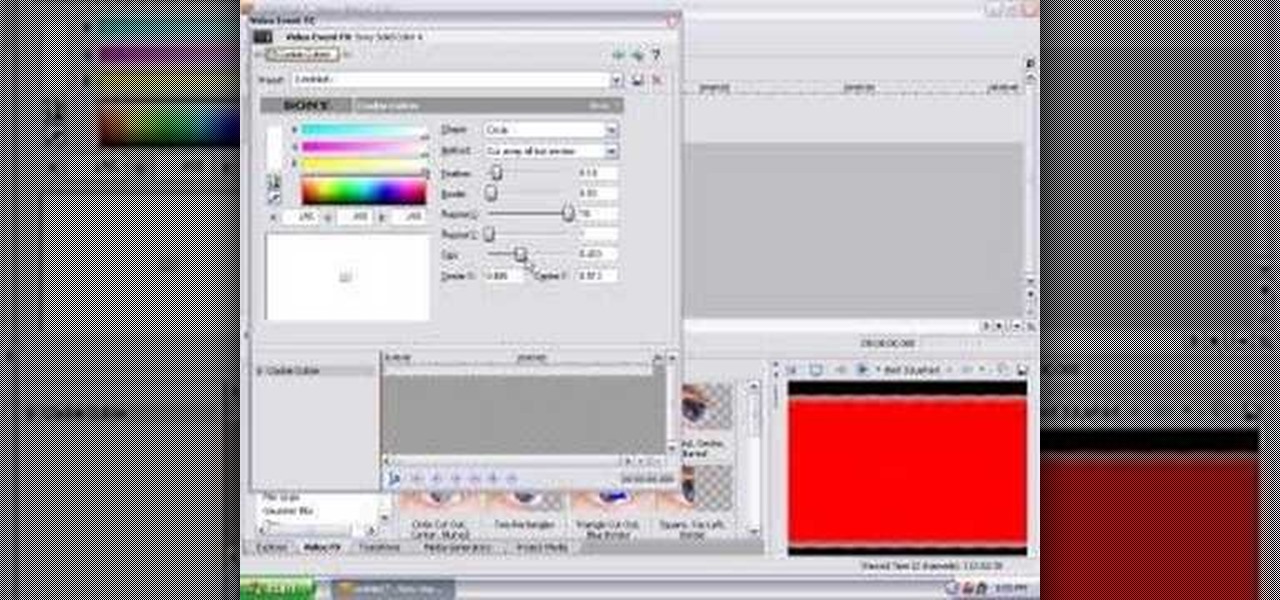
This tutorial shows you the fundamentals of the cookie cutting effects as well as the basics of the newspaper/print effects. Enjoy! 2 In 1 Tutorial I suppose.


If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Adorn your decorative cake with hand crafted fondant icing roses with help from this cake decorating tutorial. To make one of these adorable roses, follow these steps:

This is evil and it destroys people. Let's just get that out of the way. Nonetheless, suppose you need to make someone distrust their own memory and perception of reality. Suppose you want someone to believe in you more than they believe in themselves.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.
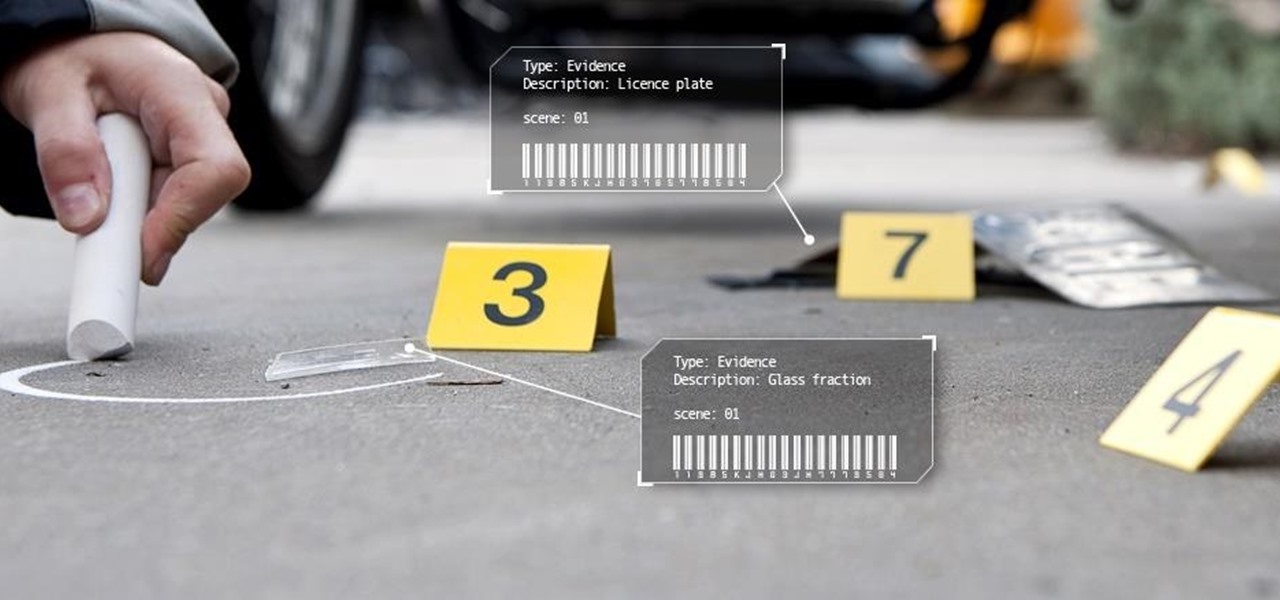
In this tutorial I am going to show you how to change some file metadata, this could be very useful if you want to edit or access a file and remove any evidence of your changes.
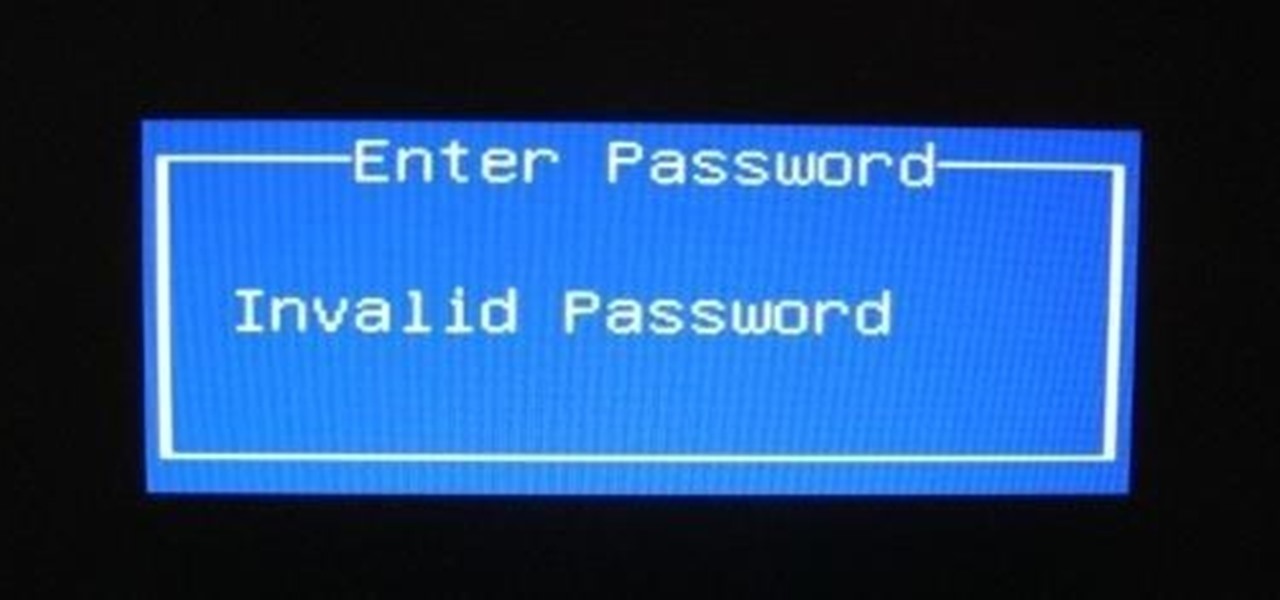
So i ran into a problem few days ago and it seemed to be very annoying one. I got hands on ASUS X55A with broken HDD. So i changed HDD and woo enter bios password. I hit enter and got into bios where uder security tab was shining ADMINISTRATOR PASSWORD INSTALLED. There was no user password but administrator password was set and it led to that i wasnt able to boot anything. At all.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...
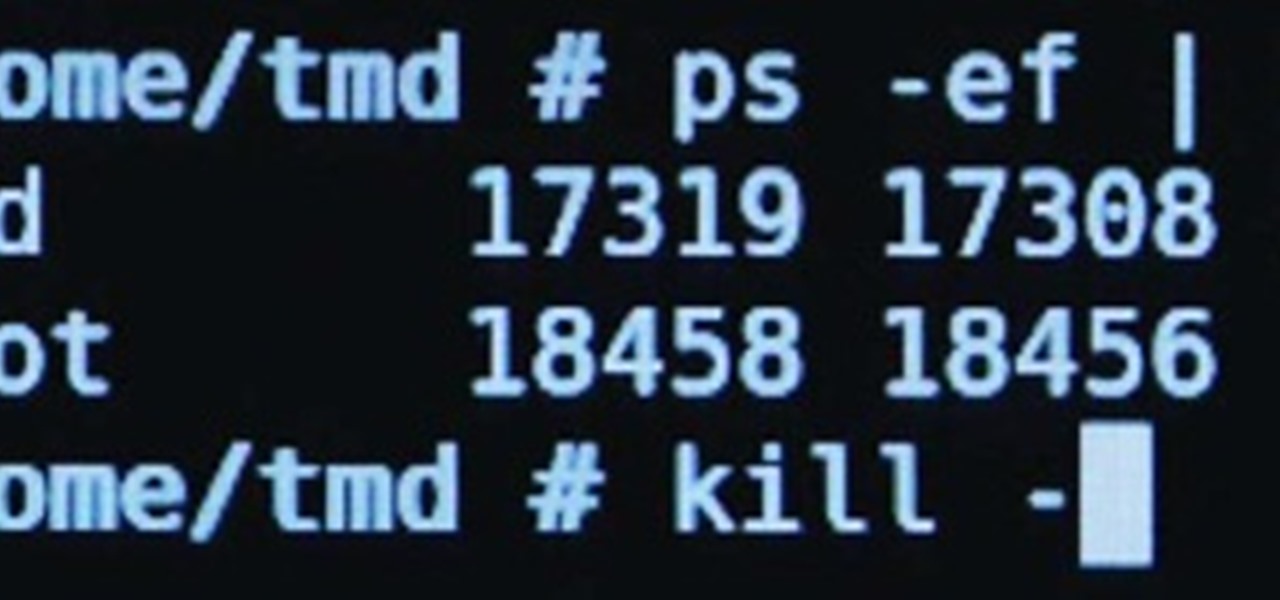
I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.

If you have yet to receive your invitation to next weekend's royal wedding in the UK, then you can still experience part of the pomp and circumstance in augmented reality courtesy of ABC News.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.

Real suffering is sitting through a thirty-second ad to watch a fifteen-second video, or watching your favorite music video in three-second fragments. Real suffering is this: “An error occurred, please try again later.” If you’re a modern human and multitask with multiple tabs while you're on YouTube, you don’t have to sacrifice your bandwidth and sanity. There's a simple way to watch YouTube ad-free and lag-free.
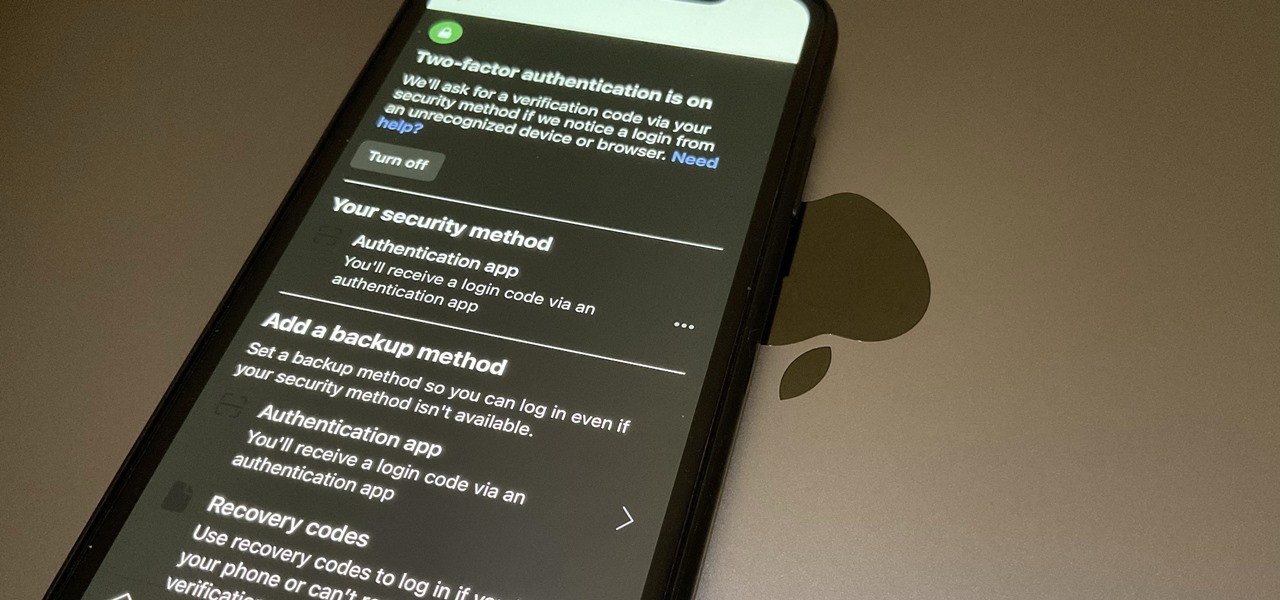
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

Self-driving car models and fleets get most of the media attention, but it is the suppliers that design and make the technologies underpinning the driverless revolution, says Guillaume Devauchelle, the vice president of innovation and scientific development for leading tier-one supplier Valeo.

Your Android phone could be listening to ultrasonic ad beacons behind your back. The unwelcome news comes year after app developer SilverPush promised to quit using its (creepy!) eavesdropping software.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Cooking on a budget isn't always easy, but there's a silver lining: it can be really fun. Ever since I started supporting myself I've enjoyed going shopping, finding the most affordable items, and learning how to make the most of them. Sure, sometimes I wish I could afford to buy a filet mignon and some morel mushrooms every night, but there's a different kind of enjoyment that comes from being able to turn a few dollars into a gourmet meal. For me, that means starting with cheap meat, and af...

I'm human, so it goes without saying that I love bacon. You're human too, which means chances are pretty good that you also love bacon. Yet as beloved as bacon has always been, it's just now experiencing a culinary renaissance, which I love. Bacon chocolate? Heck yes. Bacon donuts? Bring it on. Bacon booze? Now we're talking.