In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

At this point, it'd be surprising if an iPhone release wasn't coupled with some sort of new scandal or controversy; it's gradually becoming Apple's new modus operandi. First, there was antennagate with the iPhone 4. Then it was scuffgate with the iPhone 5. Last year, it was bendgate with the iPhone 6 models. This year, it's chipgate with the iPhone 6S models, which affects something important to all on us—battery life.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

One of the biggest new features in the soon-to-be-released Android 6.0 Marshmallow is something Google is calling "Now on Tap." Essentially, this service will be able to scan the contents of any screen on your Android device, then after you long-press the home button, it will provide you with relevant information about anything—from movie times to directions or dinner reservations.

Hello guys, its been quite a while since my last post. (sorry for the lack of images)

We've all been there. Channel surfing lazily whilst reclining on the sofa—then all of a sudden, the remote stops working. Out of frustration, you hold the remote up higher, press the buttons harder, or maybe a even give it a good smack hoping that will fix it. Right around this time, you start to wonder if your trusty old remote has finally called it quits or if it's just a dead battery.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

Who doesn't experience food cravings? Whether you're trying to adhere to a strict diet, or simply hoping to avoid sugary, fatty foods, curbing cravings can feel like a monumental task.

Ah, the fabled dark mode. In the past, many users were delighted to find the existence of something called Royale Noir, a dark theme option that was available for Windows XP. Yet for reasons unknown, Microsoft had kept knowledge of Royale Noir a secret until some bright minds discovered its existence, and the rest is history.

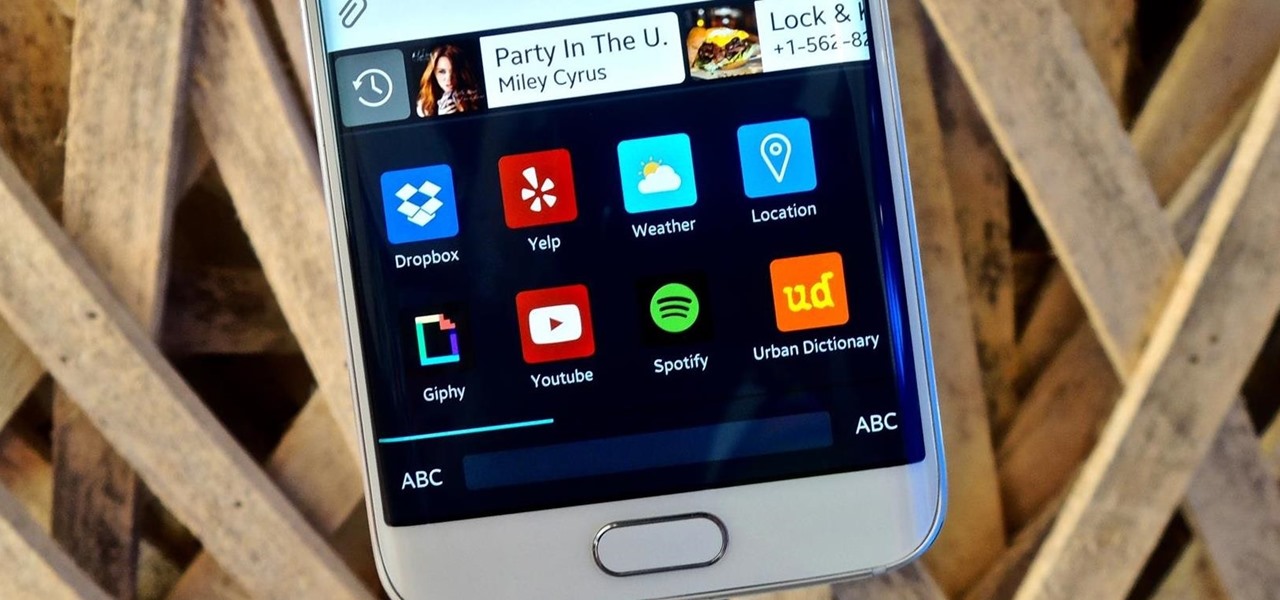
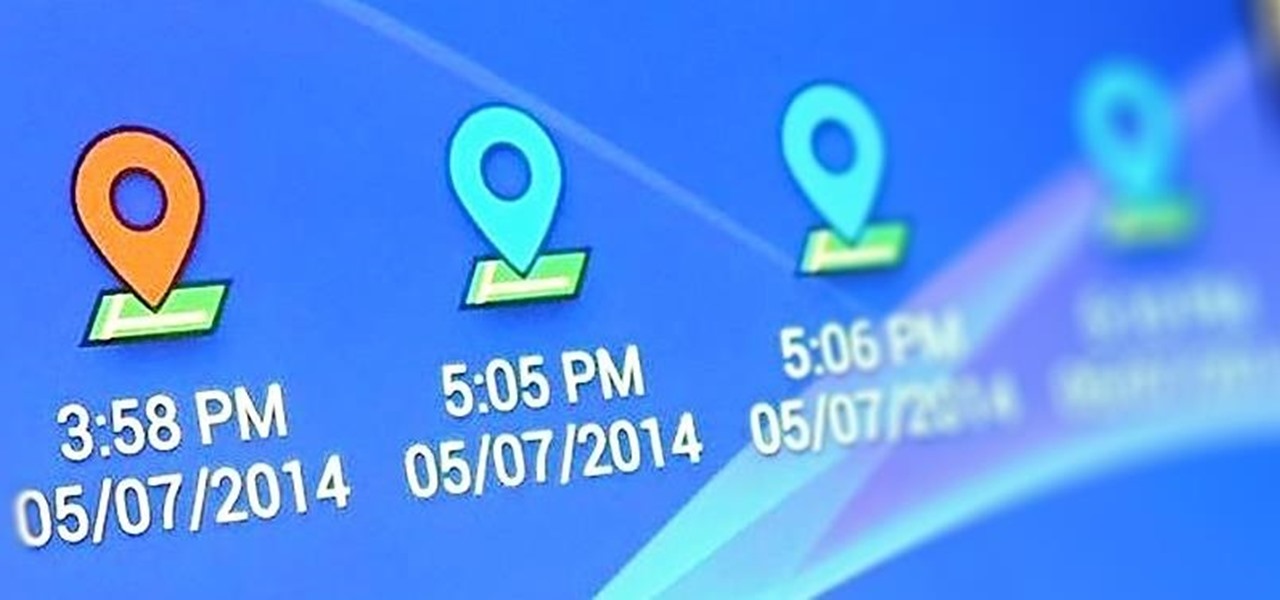
In addition to sharing emojis and GIFs, most of us also probably share various types of links through email or text, whether it be for a Google Maps location, a bar or restaurant on Yelp, or an awesome song on Spotify.

We've all been there: slipping on a pair of perfect yet slightly uncomfortable shoes, hoping they'll stretch to fit perfectly. After about 30 minutes of wear, suddenly those fantastic shoes aren't feeling very great. By the end of the day, your poor feet are covered in throbbing blisters.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

Today we are pleased to announce the end to the Apple vs. Android war. About a year ago, our Gadget Hacks team started working on a top-secret project to dual-boot both Android and iOS on the same phone—and we couldn't be more proud to announce that we've finally succeeded! Your phone can now run both iOS and Android—whenever you want. Right now.

Thanks to the strenuous efforts of our Gadget Hacks development team here at WonderHowTo, the fortified barrier segregating Android from iOS has finally fallen down.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

Google debuted YouTube Music Key in November, and for $10 a month, this essentially turned YouTube into a music streaming service. With ad-free music videos and background audio playback, YouTube serves as a viable alternative to Spotify or Pandora for Music Key subscribers.

With Android devices getting bigger by the year, you'd think there would be a native multitasking solution by now. While Samsung and LG have included such features in their customized builds of Android, the stock base that manufacturers start with still doesn't include multitasking support.

Microsoft dropped a couple of huge bombs at their Windows 10 event Wednesday afternoon. Free operating systems and holographic glasses? This must be a Sci-Fi novel or a Hollywood blockbuster, because it reeks of fiction.

Brought to you by Brother International Corporation. Whether you are looking to complete a home improvement task, or you are hoping to start a new hobby, staying focused and energized during projects can be daunting. With emphasis on organization, planning, and creativity, we gathered together tips that will help you successfully tackle any project on your plate!

Android 5.0 has a cool new feature called Priority Mode that allows you to silence your phone's ringer except for when certain people call you. It's something you'd enable right before bedtime, for instance, if you don't want to be disturbed unless it's someone important trying to reach you.

The volume is maxed out, but that doesn't stop me from hitting the volume key on my Nexus 7 in hopes that it will magically get louder. This happens to me everyday as I watch videos or play music. The simple fact is that a Nexus 7 tablet just doesn't get very loud. At least, not loud enough for me.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

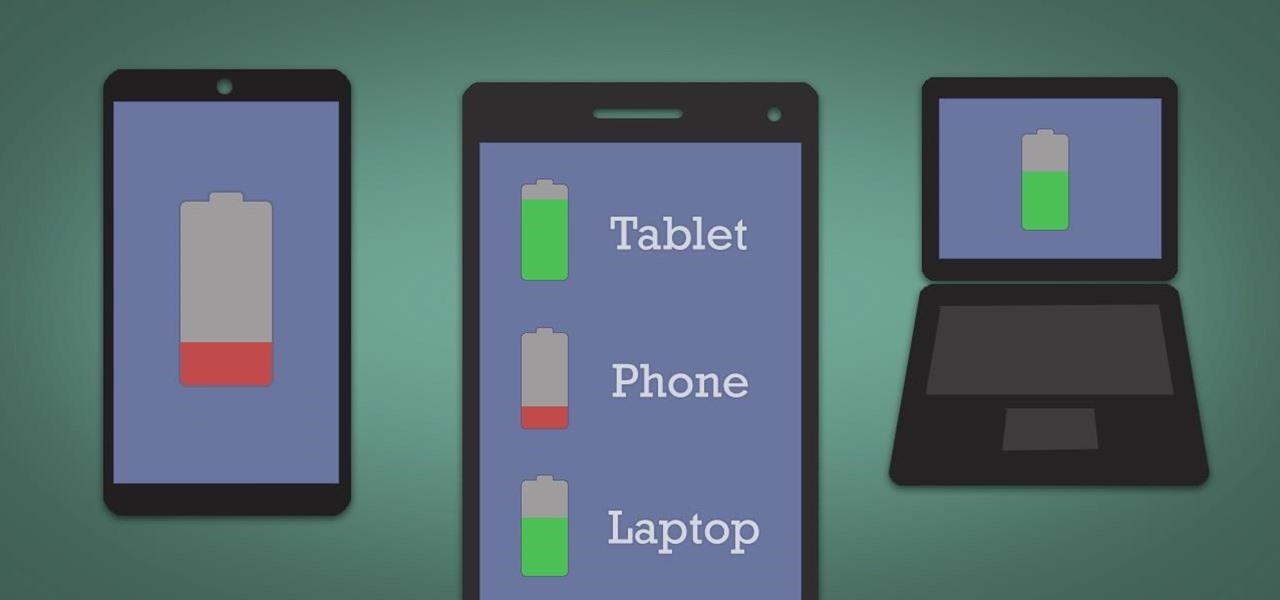
It's hard enough to keep tabs on the battery life of one device, let alone all of the different gadgets that a typical consumer owns in this day and age. Say your smartphone is running low on juice, so you switch to your tablet only to find out that it's almost dead as well. Better hope your laptop is fully charged, right?

It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access contacts, make calls, and send emails and texts.

If you hold your phone upright while taking a video, you've surely seen the horrific end results. When you try to play the video back on any other display, roughly 70 percent of the screen is occupied by black bars.

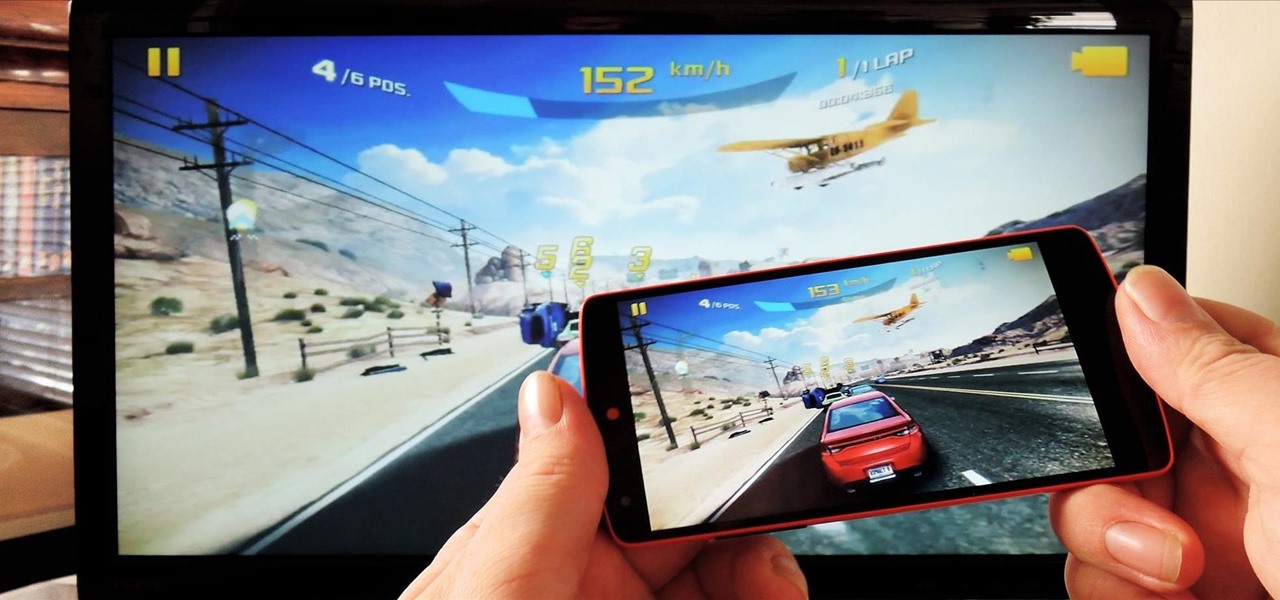
Broadcasting your gameplay for others to view has recently become a phenomenon with the advent of Twitch.tv. While computer-based gaming is well represented these days, streaming of mobile gameplay has been virtually non-existent.

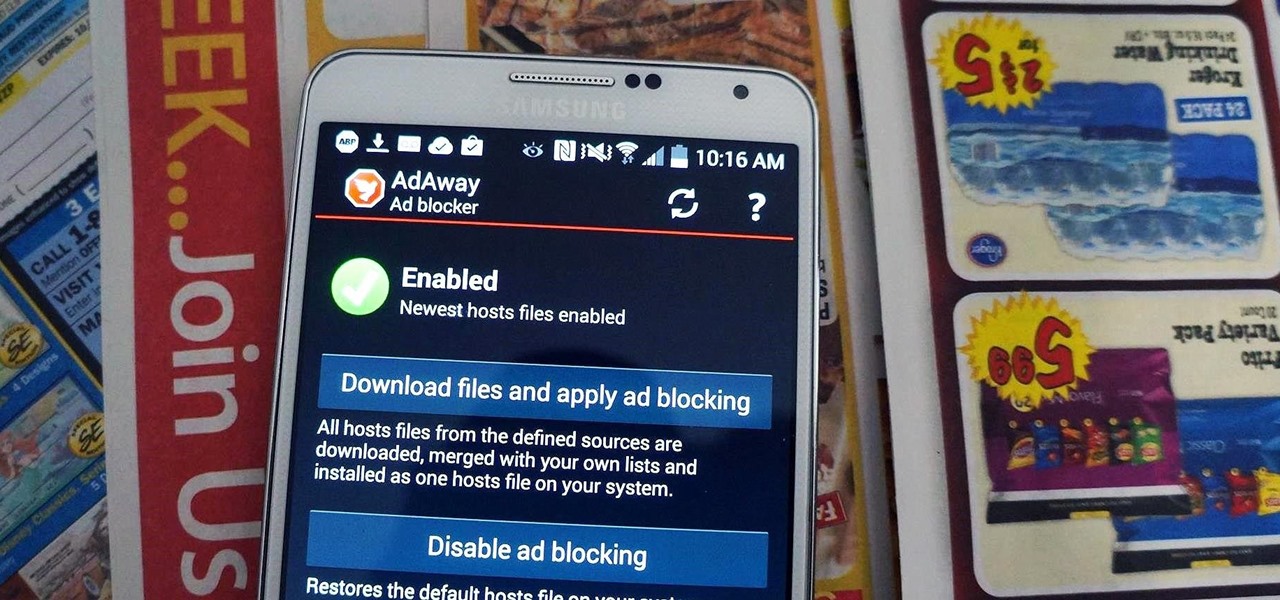
The Play Store is loaded with just about any app you can imagine. While many are free or have a "lite" version of a paid app for download, often enough, these freebies have intrusive ads cluttering up your screen.

Your heart is constantly work for you, yet you think nothing of it—and Samsung wants to change that. They stuck a dedicated heart-rate monitor on the Galaxy S5, they're putting one in the upcoming Note 4, and they're bound to slap one in every Galaxy device thereafter.

There are two types of bricks ("brick" as in "bricking your phone")—soft and hard. Soft bricks are recoverable—something has probably gone wrong with some critical system partition, causing a bootloop or inability to boot in some way. Fine. Re-flashing everything should fix that instantly. Hard bricks are not recoverable—if you manage to hard-brick your Nexus, you are in trouble.

Love making gifts for your loved ones? Here is a tutorial that shows you how to make a play doh rose. It's really easy and fun to make.

I am a graphic designer, so I have to collect massive pics from webpages to provide me with inspiration. But sometimes I need to use them everywhere, even if I've no access to computers or laptops, so I have to resort to mobile devices.

Many of our everyday apps include a menu tab or search bar, like Chrome and Twitter. In fact, a lot of times those are the first things we go for, as search is universal in most apps, and app settings are just about always accessible through the menu.

I passed a cool looking bar the other day that I wanted to check out. When the weekend came around, I was ready to go, but for the life of me couldn't remember where it was. Not wanting to retrace my steps or drive around aimlessly, I gave up.

I still have a nexus one. This little phone 196 Mb of storage space (and most of that is taken by the system). But I have somehow managed to live off it for 2 years. This is for anyone with a small amount of memory. We will be using Link2SD. MUST HAVE CWR AND A ROOTED PHONE.
Hello, Freakje118 here! Today 13/04/2014 ends the Ice Castle Competition! What a shame only 3 people participated but okay, life goes on! Here are the winners and their prizes

Hey everyone, freakje118 here! This week, the first challenge ever will be to build an awesome and icy ice castle! It can be any size you want but please use the plots. Let your imagination work and make something great of it! you can use any blocks that you want! Ice, water, quartz, wool,.... But remember, it should be an ice castle!

One draw that Samsung's Galaxy S line has had over the Google Nexus 4 and 5 and the HTC One (though the M8 appears to be following suit) is expandable storage. Pop a microSD card into the slot and you have extra storage for music, photos, and even apps themselves in some cases.