When you think about consumer VR headsets, you either imagine a computer-tethered powerhouse like the Oculus Rift and HTC Vive, or something portable yet limited that utilizes your smartphone like Google Cardboard. Somehow, we haven't seen much in-between, but the Idealens aims to fill that gap.

We're on the verge of an amazing evolution of technology where we can work and play in virtual worlds that merge with our own—or let us escape into our imaginations entirely. But creating virtual, mixed, and augmented reality experiences requires resources and hardware that not everyone has access to. If you want to build something awesome with the Microsoft HoloLens (or one of the other awesome platforms), we want to help you do just that.

New Android versions have always been released on a fairly regular schedule—in late Fall, Google debuts a new Nexus device, while simultaneously publishing the next iteration of the world's leading mobile operating system. But things are different this year, as we now have numerous indications that Android Nougat could be released as early as August or September.

We admit it: we are ranch dressing fanatics. We like to put it on our simple salads, spread it across our chicken wings, and dip homemade sweet potato fries in it. Plus, since childhood, neither of us can eat pizza without ranch dressing to accompany it.

Ah, the sensation of that first bite of sorbet in the heat of summertime: icy, refreshing, decadent in flavor and texture. We love sorbet almost as much as we love ice cream, and making it at home is actually pretty simple. Most recipes call for just water, sugar, and a base fruit of some sort (like strawberries or watermelon).

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

Automated bots are growing on Facebook Messenger, and while they can be helpful, they also have the potential to get very annoying, very quickly. That's because these bots are enabled by default to send you "sponsored messages," or, you know, spam.

Scrambled, sunny side up, hard-boiled, soft-boiled, over easy, and poached: there are only so many ways to cook an egg before you get bored and look for inspiration somewhere else.

We're maniacs for mustard: we put it on our sausages, our salmon, our turkey club sandwiches... you name the dish, we find an excuse to spread mustard on it. So it's not surprising that it's a common item on our grocery list.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

We've been on a constant hunt for the best way to make almond milk at home, and we think this trick might just be the most genius yet.

We're so used to seeing things in particular ways that anything different just doesn't make sense to our brains. Culturally, we like to read things from left to right, and from top to bottom. Change that and our brains struggle to adjust.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Frozen meat is a saving grace for weeknight meals. Whenever I crave a certain protein, all I need to do is defrost it. Sometimes, I don't even need to defrost it in order to use it.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

For the past couple of years, random internet dwellers have embarked on an ambitious quest to see just how useless a box can be in hopes of earning sweet, sweet internet points. Welcome to the world of useless machines.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Obviously this is just a teaser, and who knows how soon we'll see something like this in real life, but just go ahead and watch the video first before you continue reading.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

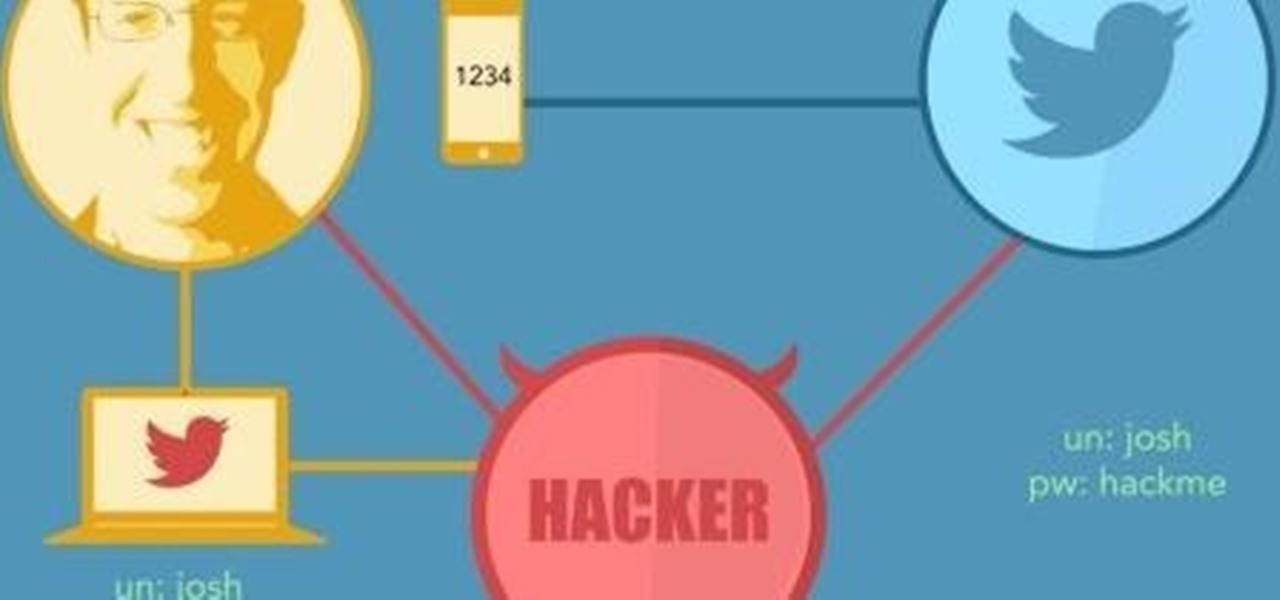
Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Apple just sent out a new update to their iPhones, and while that normally wouldn't have any impact on Android users, the fact that they included 184 new emojis means that the text messages you receive from friends and family members with iOS devices might come across with blank or missing characters.