Want to learn how to play Jason Mraz on the guitar? With this tutorial you can learn how to play "I'm Yours" by Jason Mraz on the acoustic guitar. The capo is on the 4th fret in standard tuning. This version is a simplified version of the song and is not exactly how Jason Mraz plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "I'm Yours" by Jason Mraz.

Want to learn how to play "Superman" on the guitar? With this tutorial you can learn how to play "Superman" by Joe Brooks on the acoustic guitar. The capo is placed on the 10th fret in standard tuning. This version is a simplified version of the song and is not exactly how Joe Brooks plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play guitar along to "Superman" by Jo...

Want to learn how to improvise and play jazz piano? Well first you have to learn from the jazz greats of yesteryear. This lesson teaches you how to play "The Man I Love"by George & Ira Gershwin on piano. With some practice and basic understanding of music theory and harmony you will soon be able to improvise jazz solos over basic chords. Soon you will be able to play along with any tune with this jazz piano lesson. Check out this jazz piano how to video and you will be on your way to playing ...

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

You just sat down, coffee in hand, and the day is ready to start. Now that you have taken a few sips, let me pose a question: What is living in that coffeemaker of yours? The answer might make you dump that coffee down the drain pronto.

Welcome back, my rookie hackers!

If you want something more than the standard white flash from the LED on your iPhone 4, sure you could take it apart and replace it with a new colored LED or cover it with colored material, but why would you want to do all that when you can do something a lot cheaper and A LOT CHEAPER!

No more do you need to fumble with keys. The 2010 Lincoln MKT has a button ignition instead of the standard key ignition. And it might be confusing at first, but this video will show you how to start and turn off your vehicle by using the push button (available on select models). No more digging in your purse or pockets… simply have the key fab within a certain distance and press the ON button. It's that easy!

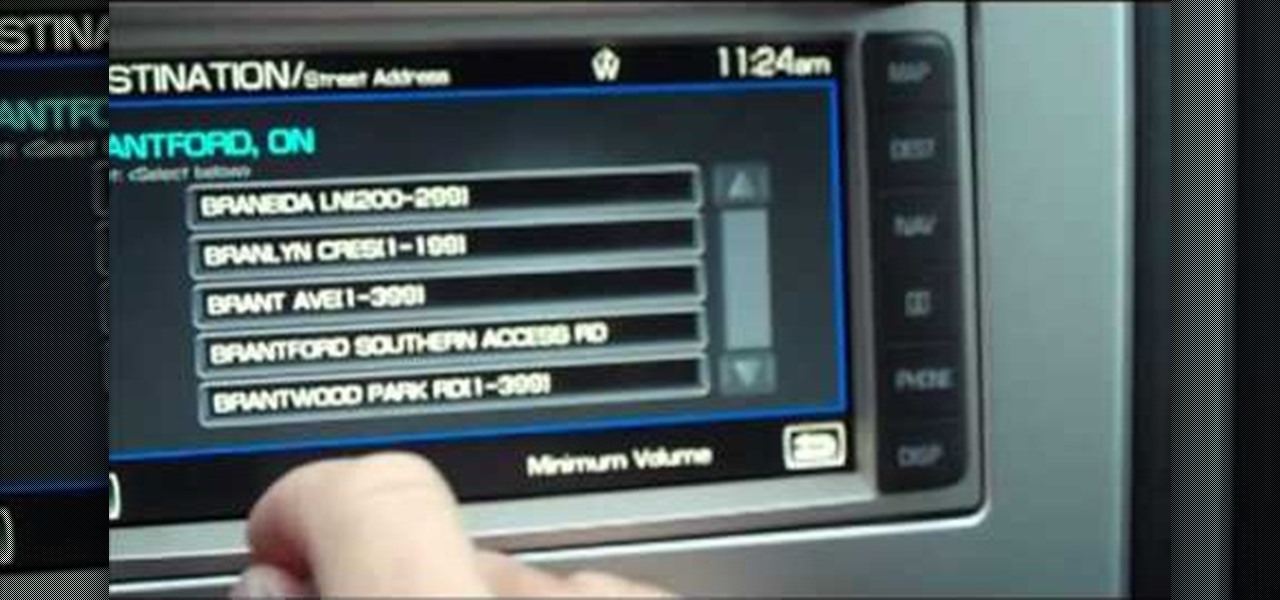
It's easy to get around in the 2010 Ford Lincoln MKX, because it has a built-in navigation system. But how do you use it? How do you find your way around? This video will show you the steps necessary to set a waypoint on the touch screen inside the 2010 Lincoln MKX. Getting directions is so easy!

Don't get stuck on the course searching for the right putter. In golf, the old standard for organizing clubs entails putting the shorter clubs in the first slot of the bag, the middle irons in the middle brackets and the big clubs in the back. In this quick and easy to follow video, you will get a step by step on how to arrange your clubs so you know where everything is. So, get ready to be your own caddy and find out where to place putters and hybrids in a golf bag with this clip.

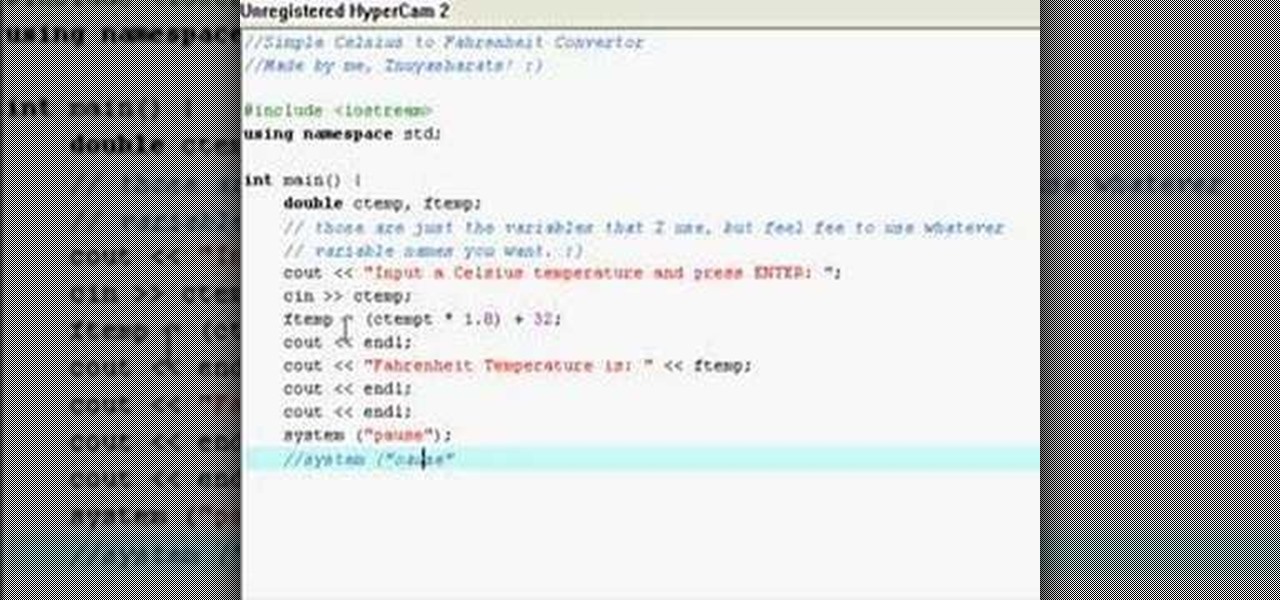
In this video, the instructor shows how to convert Celsius to Fahrenheit using a C++ program. This video shows how to do this by a live example where the instructor writes down the code to do it. First, code the basic structure of a c++ program that contains the include and all other statements. Now accept the value of temperature in Celsius from the standard input. Now multiply that value by 1.8 and add 32 to it to get the value in Fahrenheit. Display the value to the output. Finally, compil...

In this how-to video, you will learn how to tune a guitar with the help of an online tuner. You will need a guitar. Listen to the low e string note being played and tune your guitar's low e to that tuning. Listen to the a note being played and tune the a string accordingly. Listen to the d string open note being played and tune the d string. Listen to the g string open note being played and tune your g string accordingly. Listen to the b note being played and tune the b string accordingly. La...

Sure, you've heard of poi, but this is not your standard fire poi… it's with hula hoops instead… hoop poi. Learn how to perform a forward three-beat weave in hoop poi. If you prefer the kindness of a hula hoop over the flames of a poi bag, hula poi is your answer. The forward three-beat weave is a great poi trick to learn.

Although mainly demonstrational, this video shows you how to play "Key to the Highway" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

When you're sharing a printer, dealing with cables and networking can be a hassle. Having a printer with built-in wireless or using a wireless conversion kit for standard printers, allows easy sharing of your printer with multiple computers.

Apple ProRAW, the new RAW shooting format available on the iPhone 12 Pro and 12 Pro Max, is now available in iOS 14.3. But you won't find a switch for it in the Camera app after updating your iPhone, and that's because it's an opt-in feature you have to unlock.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

In a departure from Apple's newer iPhone models with Face ID technology, the 2020 iPhone SE goes back to the old days where the Home button ruled, and Touch ID was the biometrics method. But if you've never owned an older iPhone with a Home button, something as simple as shutting down and restarting the iPhone SE could elude you.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Black Friday is upon us. Whether you prefer to duke it out in stores or calmly shop online, there's no doubt you'll find great deals on the items you're looking for this holiday season. It's the perfect time of year to buy something expensive, like a good pair of AirPods, Beats, or Bose, at a much more opportune price.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Surprising? No. Exciting? Absolutely. After a grand introduction by at the Apple event on September 10, 2019, the iPhone 11 is finally here. We may have known nearly everything about this new iOS device ahead of time, thanks to the usual surge of reliable leaks and rumors.

While the portability of mobile phones makes gaming convenient, it isn't a perfect playing experience. With touch controls, small screens, and limited specs, smartphones lack the comfortability of dedicated gaming devices. But with a few tips, you can enjoy games as if you were playing on the Nintendo Switch.

Though more well known for their OLED displays and advanced cameras, Galaxy phones like the S8, Note 10 & 10+ and S10 series are a force to be reckoned with when it comes to audio. In fact, flagships from the S9 on up feature AKG-tuned stereo speakers, along with a slew of software enhancements that make listening to music a truly pleasurable experience.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

When you can't think of a way to respond in Messenger with words, emojis and stickers will do the trick. Since Facebook is all about the "likes," which use a thumbs-up icon, there's a shortcut to the symbol just to the right of the chat field. It's always there to send a quick like in response to something. But it doesn't have to be the standard Facebook thumbs-up sign — it can be any emoji you want.

OnePlus always seems to offer affordable yet powerful tools for videographers of all kinds. The camera hardware itself is crucial, but what's hardware without good software to highlight its real potential? It doesn't matter which version of the smartphone you have, they're all powered by the very same OnePlus camera app.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

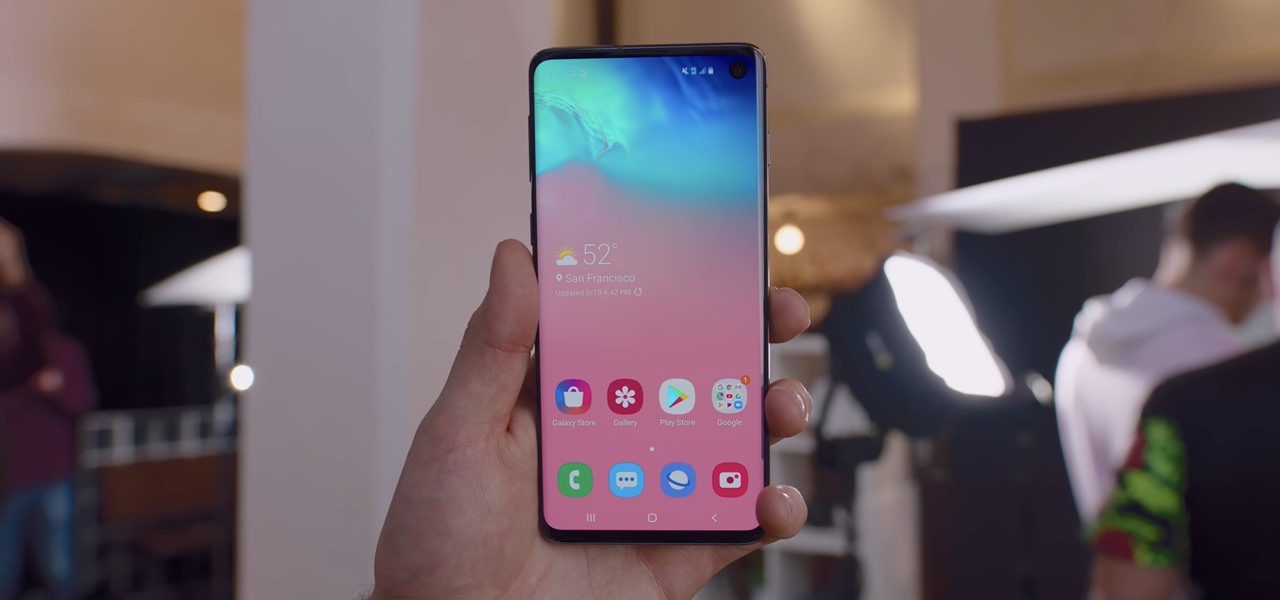
The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

Update: The LG G8 ThinQ has been announced. You can read all of the official specs at our full article on the new phone.