You might not think a mixed reality headset could help kids eat their vegetables, but that's the exact premise behind Habit.at—the app that won the "Social Good" category at the 2016 HoloHacks competition in Los Angeles.
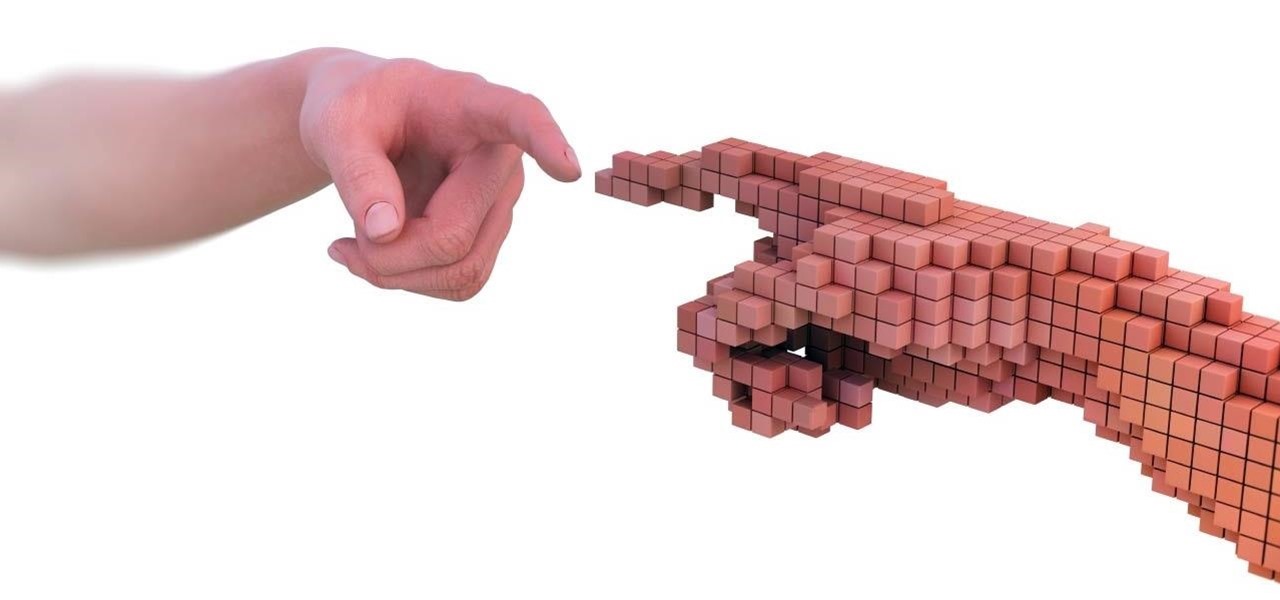
Augmented reality (AR) holds much promise for how we'll interact with technology in the future, but we still have many hurdles to clear before that dream fully comes to fruition.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

It's no secret that the microwave is a modern-day wonder that, when used correctly, can cook a wide variety of food in a snap.

Delicious hash browns are ridiculously easy to make at home. So skip the diner and save your money—use this salad spinner trick instead to make crispy and seasoned hash browns quickly and with ease.

If you consider yourself a regular coffee, tea, or hot chocolate drinker, you probably have a kitchen cabinet full of stained mugs that refuse to scrub clean. Thankfully, there is a better solution that doesn't involve continuing to fight those stains with a sponge, bleach, and elbow grease. The answer to your coffee or tea stain problems is Cafiza: an awesome espresso machine cleaning product that is popular amongst professional baristas... but also doubles as an extremely effective ceramic ...

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

Most wood furniture is long-lasting, durable, and resistant to great wear and tear over the years. However, set a single sweaty, wet cup or bottle on the surface of your favorite wood dining table, or your prominently placed wooden coffee table, and you'll end up with a round water ring stain that is difficult to get rid of.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

We've all been there. Channel surfing lazily whilst reclining on the sofa—then all of a sudden, the remote stops working. Out of frustration, you hold the remote up higher, press the buttons harder, or maybe a even give it a good smack hoping that will fix it. Right around this time, you start to wonder if your trusty old remote has finally called it quits or if it's just a dead battery.

When I was a little kid, my parents often eschewed cakes for my birthday parties, and instead opted for ice cream sundaes and banana splits. It made perfect sense: ice cream is so easy, and you can get multiple flavors to ensure that everyone is happy.

When you go to the grocery store, chances are you're confronted with the usual piles of apples, berries, bananas, and melons. All well and good, right?

Though you may scrub every inch of your kitchen, there are plenty of trouble areas that are nearly impossible to get clean: gunked-up tile grout, rust in the sink, and caked-on burners and grates on the stove. As far as burners and grates go, you're in luck, because there's a simple solution to returning even the grossest ones back to their original shine. The Key Is Ammonia

T-Mobile's "Uncarrier" initiative has done wonders for my wallet and my data usage. Before I had to deal with being throttled down to 2G speeds after passing my data limit, but thanks to their unlimited data plans, I'm free to use as much LTE data as I possibly can. The only downside is, when sharing data through a mobile hotspot (tethering), T-Mobile imposes a 5 GB limit (which was recently upped to 7 GB for some).

White rice is cheap, filling, and tasty. No wonder so many countries in the world rely on it as a mealtime staple, including most of East and Southeast Asia. Alas, because of its relative lack of nutrition and its high calorie count, consuming lots of white rice regularly also puts people at risk for diseases like diabetes and obesity.

Resources for finding new music are at our disposal in all corners of the internet; the only problem is deciding which one is the best for you. Spotify, Pandora, and Rdio all have options to discover new music on your smartphone, but they tend to expose mostly established artists, making the process of finding lesser-known but good music a game of trial and error.

Thanks to the strenuous efforts of our Gadget Hacks development team here at WonderHowTo, the fortified barrier segregating Android from iOS has finally fallen down.

Show your significant other just how much you love them by surprising him or her with one of life's most precious, romantic gifts—bacon! Best thing is, this passionate treat works for any day of the year (Valentine's Day, a first date, anniversary, etc.), since love and bacon go hand in hand.

Android Lollipop has an awesome feature called "Battery saver" mode that reduces power consumption through various tweaks in order to squeeze in an extra hour or two of standby time when your battery is running low. It does this by disabling background processes as well as location services and transition animations, so the phone is essentially running at half-throttle.

Many manufacturers add a custom skin on top of their Android builds, but none are more widely praised than HTC's Sense UI. The general consensus among Android users says that HTC's visual tweaks are done in good taste, and the features they add are both functional and warranted.

I have a weird fondness for the texture, if not the taste of Velveeta (and Kraft American cheese slices). No other cheese has quite the same amount of slip or smoothness and manages to stay that way, undoubtedly because Velveeta contains sodium alginate, an algae derivative that helps it stay so silky-smooth even as it heats up. It also contains a high level of protein-to-fat ratios, which is what makes it a champion melter.

Marmite: either you love the stuff or hate it. ("Love" meaning you are British and grew up eating it, and "hate" meaning you are everyone else.)

I've known eaters who will fearlessly bite into the hottest peppers, but even they have quailed before durian, the fruit that hails from Southeast Asia and whose smell has been compared to garbage, rotting flesh, and the bathroom post-use. However, this hefty globe with its spiny, prickly outer covering isn't called "the king of fruits" for nothing. According to its many fans, its stench does not correlate to its taste, which has been described in extremely flattering terms. Monica Tan of The...

Android's beauty is in its customization; you can have widgets for anything, launchers that look and feel completely different from one another, and fonts you can change at any time. And it doesn't stop at aesthetics—you can go much deeper than looks.

Every so often, we come across an app that makes us wonder "Why didn't someone think of this before?" This is definitely the case with developer Dor Sakal's latest offering, FloatNote.

I'm always looking for the best apps and services for my Android, and that means sticking strictly to the Google Play Store is a no-go. If you're like me and tend to install a lot of APKs (application files), you're probably tired of seeing the "Install" confirmation that always pops up.

If you thought iOS 7 was a drastic change from previous iterations, iOS 8 will certainly continue to rock the boat. From a revamped Control Center to enhanced "Continuity" to ephemeral messaging, Apple's newest mobile operating system will have many of you relearning the "basics."

When Yahoo! purchased the home screen replacement app Aviate back in January, many were wondering if the internet giant intended to continue development of the launcher or if the transaction was just another acqui-hire.

I am a graphic designer, so I have to collect massive pics from webpages to provide me with inspiration. But sometimes I need to use them everywhere, even if I've no access to computers or laptops, so I have to resort to mobile devices.

When looking at weather applications and widgets, one major characteristic I look for is efficiency; something that will separate it from the rest of the herd. The stock weather widget looks great on my home screen, but I have to exit whatever app or game I'm in when someone asks me about the weather.

Ever wonder why when you defrost meat, there's all that pink liquid at the bottom of the plastic bag? That liquid is called "purge," and it's not good.

Apple hates game emulators. Go ahead, look around in the iOS App Store, you won't find any. But who needs 'em anyway?

The first thing I do when I wake up in the morning is run to the kitchen to make coffee, and I know I'm not the only one. According to a survey by the National Coffee Association (yes, there's such a thing), 83% of Americans drink coffee, and I'd bet most of that consumption happens in the morning.

I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

Maybe you are on your phone a little too much sometimes. But when you are rocking some of the best mobile games being offered it can be hard to pull yourself away. If you get a new phone or a App Store gift card you are going to want to load yourself with the hottest app available. And once you're done playing, take a little time out to enjoy the family too.

If you turned on your HTC One for the first time and wondered what that weird icon that looks like an N is, it indicates that NFC is on. It seems strange to me that HTC wanted to waste Status bar space on an NFC indicator, but sometimes we just have to deal with it. However, if you're a softModder, you don't have to just deal with it. The icon can't be removed permanently, but there is a very easy way to hide it forever.

The new Moto X may not have a lot going for it when it comes to hardware, but there are some pretty cool software features that makes it a tempting device. One of these cool features is its Active Display notifications that appear on the lock screen.