Stop! Do not pour that leftover wine, coffee, or bacon grease down the drain. And those herbs that have been in your fridge so long they've literally turned on you? And what about when that recipe only calls for two tablespoons of heavy cream, a quarter cup of tomato purée, or three cloves of garlic? Unless you plan on using the leftovers again in the next week or so, don't bother refrigerating them because they won't last.

There's nothing in this life that we love more than making one ingredient or one food tool do multiple things. It saves money! It saves time! It makes us look smart at cocktail parties!

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.

Macaroni and cheese is one of those dishes that automatically make me feel all is right with the world. I even like the boxed kind in a pinch. However, real macaroni and cheese is pretty easy to make and is worlds better than the boxed kind. It's also pretty easy to make really, really good macaroni and cheese once you know some essential pointers.

In case you haven't heard, chia seeds are off of the novelty plant grower and in your supermarket. Why? Because they're a nutrient-dense food loaded with calcium and fiber (18% and 42% respectively of your RDA per one ounce of seeds). There are even some preliminary studies that show chia might be useful in combating diabetes.

Eggs are incredibly important to cooks, and not just because they're tasty and a complete protein (many erratic genius/artist types make a point of eating an egg or two for breakfast). Yes, they are great when perfectly poached, scrambled, hard-boiled, and even scram-boiled, but they serve literally dozens of functions when used in recipes, especially baked goods.

If you've been to a farmer's market during tomato season, chances are you know that heirloom tomatoes are pricier (and funnier-looking) than their hybrid counterparts.

Whisking liquids seems somehow quaint, especially since there are good, cheap devices out there like immersion blenders and hand mixers that can whip cream, turn egg whites into meringue, and mix batters for you.

Want to show all your foodie friends that you're really in the know? Then it's time to master the art of making edible dirt. Chefs out there are finding ways to take various foodstuffs and dry, char, and combine them to give the appearance of actual dirt—only with a rich, savory taste.

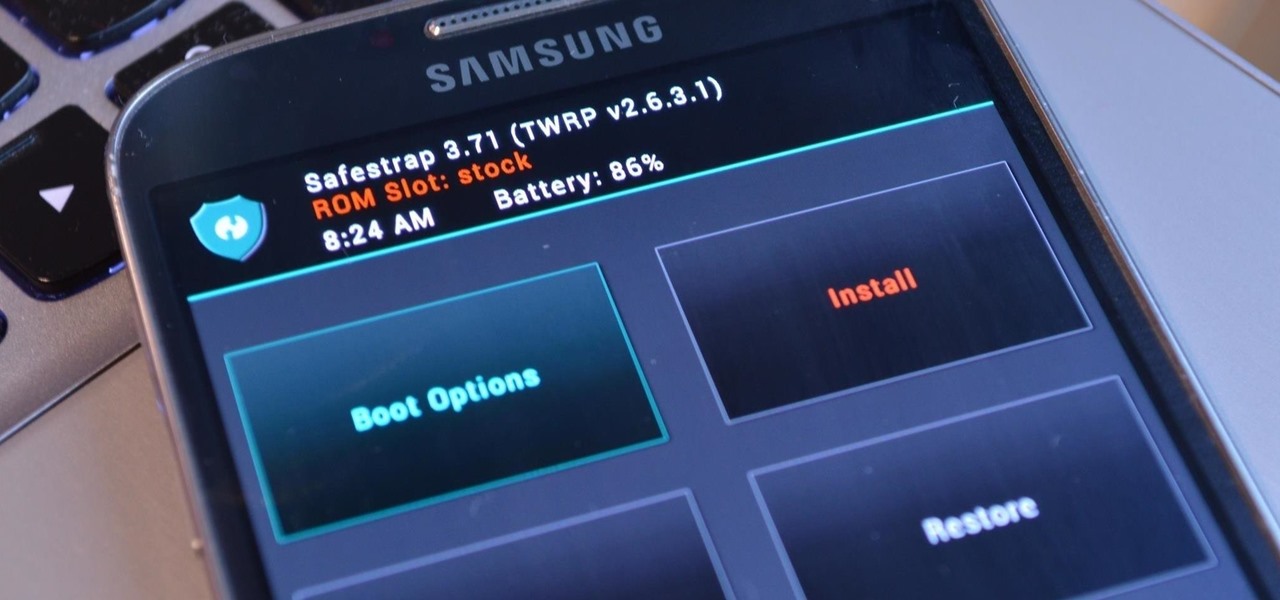
Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

With warm weather comes bugs, and with bugs come bites, and with bites come itches. From ticks and spiders to mosquitoes and bees, insect bites come in sundry shapes and sizes, but they all commonly pull an itchy, red reaction out of our bodies.

The better the meat you use, the better your homemade beef jerky will turn out. You will want to go to your butcher and get as good a quality meat as you can afford and have the meat sliced really thin. Beef jerky is a great way to preserve your protein for a snack. This video will show you how to make better beef jerky.

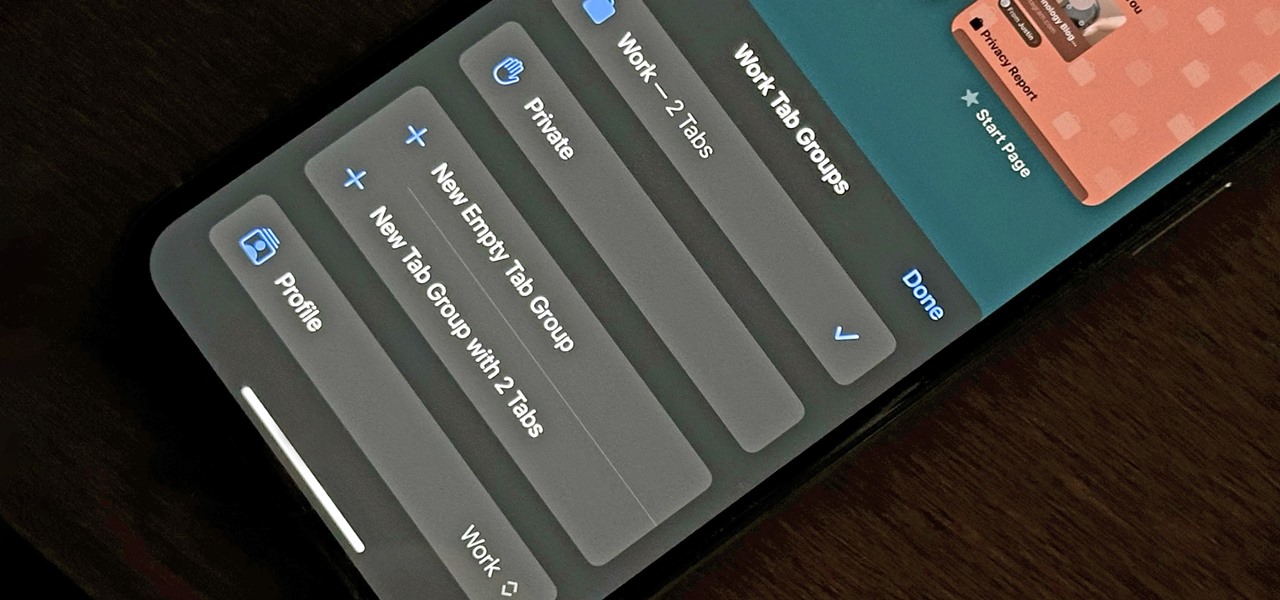
Apple is finally adding profiles to Safari, so you can now keep your personal, work, and other topical browsing totally separate in their own instances, with their own history, cookies, website data, and active extensions.

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.

Downloading content from TikTok is relatively easy, even if the video is protected, but the same can't be said of Reels, Instagram's version of short-form videos. Instagram doesn't make it easy to download content unless it's your own, and that's especially true with Reels. However, there is a way to bypass Instagram's restrictions on your iPhone and save videos locally without ever leaving the app.

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

Progressive Web Apps hope to one day bridge the gap between websites and apps by giving the former more access to your phone's features, but they're not very common yet. In the meantime, you can take matters into your own hands with an app that uses your system WebView to render websites in a full-screen, borderless window with a few extra features — a lot like a native Android app.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 dev beta 2. Who's ready to start up the conversation all over again?

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

After testing a series of Android 8.0 builds, Essential hit the reset button and jumped to Android 8.1 Oreo. The beta program didn't last long, as Essential has now released the official 8.1 update to the masses. The features from the 8.0 betas are all still there, plus a few goodies specific to the updated version. We'll highlight the standouts here.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

Fight me all you want, but it ain't a party without alcohol—whether it's a Halloween party, Christmas party, dinner party, or even a damn wedding. (If you think that people will stick around after dinner for a dry wedding, then you're sorely mistaken.)

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Everyone talks about how great sliced bread is, but there's nothing better than the taste of a just-baked loaf of crusty French bread. Like most beautiful things in life, however, the beauty of the baguette doesn't last. The next day, it's rock-hard, and good for very little except for croutons or breadcrumbs. But there is a trick to make it like fresh again.

The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of the dice sometimes.

Making a good pie crust can seem intimidating to the uninitiated, but once you master this skill, a whole world opens up to you. Not only can you make all manner of fruit, custard, and cream-filled pies once you know all the tricks, you can branch out into the world of quiches, savory pies, and flaky, crispy turnovers, too. We've already told you how to get perfect, firm fruit pie fillings, so now, let's learn about crust.

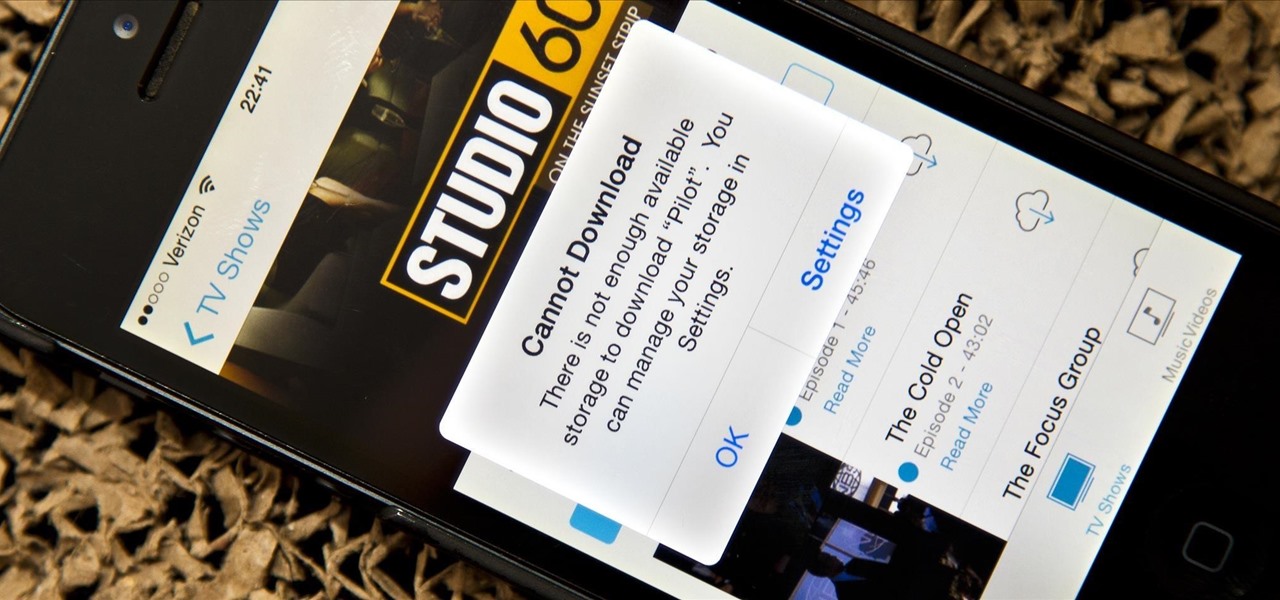
Running out of storage space on your iPhone is annoying, but trying to free some up is downright aggravating. Until they figure out a way to throw a terabyte of flash memory in there, you're going to have to do some spring cleaning every now and then, especially if you're trying to update to iOS 8.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Visit a webpage on your iPhone, iPad, or Mac, and there's a good chance you'll be bombarded with distractions such as ads, fullscreen pop-ups, cookie consents, log-in requests, notifications, email signups, sticky videos, and calls to action. If you're using Safari and content blockers, "Block Pop-ups," and Reader mode can't hide the elements you need, Apple's got a new tool you should be excited about.

Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

Apple wants to support the advertising economy, but its primary focus of late has been user privacy and security. In Safari, cross-site tracking, which lets content providers track you across websites and apps to show you more targeted ads, is disabled by default. However, content providers can get around that using less privacy-invasive ad measurements, but you can stop that too in iOS 14.5.

"What's your Wi-Fi password?" That's usually the first thing guests ask for when you have them over. You tell them the network name, then try to explain your complicated hacker-resistant password, which becomes a whole ordeal. But there's a better way to do it, which doesn't rely on using the same mobile OS as your guests.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.