Use cable weight machines for shoulder exercises. Learn tips and techniques for working out the chest, back, shoulders, and arms in this weightlifting video. Take action: work anterior and lateral deltoids by pulling handle straight up to side, but don't lock elbows, raise arms straight out to the front. Lance is certified personal trainer through American Fitness Association of America. He graduated from UNC with a biology degree and currently works for a gym. He specializes in weight traini...

Isolate muscles in the back with some simple exercise methods. Learn tips and techniques for working out the chest, back, shoulders, and arms in this weightlifting video. Take action: isolate back muscles with feet wider than shoulder-width, and bring weight down to hips but don't lock elbows. Lance, the instructor in this how-to video, is certified personal trainer through American Fitness Association of America. He graduated from UNC with a biology degree and currently works for a gym. He s...

Work out multiple back muscles with compound exercises. Learn tips and techniques for working out the chest, back, shoulders, and arms in this free weightlifting video. Take action: grip handles on the outsides, cross legs, bring chin to top of the bar, and return slowly, but don't swing legs. Lance, the instructor in this how-to video, is certified personal trainer through American Fitness Association of America. He graduated from UNC with a biology degree and currently works for a gym. He s...
Whether it's a small business or a work group inside a large corporation, all members need access to the same materials in order to work effectively. Mac OS X server makes it easy for groups to collaborate and communicate through their own Wiki-powered Internet website. To learn how to use Wiki Server with Mac OS X Server, watch this video tutorial.

Have you tried working out with an isolated lateral bench press? Iso-lat bench presses are an essential part of lifting weights and strength training. This fitness how-to video tutorial demonstrates how to do an isolated bench press to strengthen the upper body. Learn tips and techniques for working out the chest, back, shoulders, and arms in this weightlifting video.

Have you tried a chest fly on a weight machine? Both a weight machines and a chest fly are an essential part of lifting weights and strength training. This fitness how-to video tutorial demonstrates strengthening the chest with flies on a machine. Learn tips and techniques for working out the chest, back, shoulders, and arms in this weightlifting video.

Do you dream of standing on stage in front of millions of fans with a guitar in your hand? You can make this dream come true, if only you could play the guitar! This guitar tutorial series from Robert Renman teaches you the basics of guitar playing along with a few beginner and intermediate techniques. You can learn how to play a a great Freddie King song "Big Legged Woman" with this guitar lesson. Freddie King, also known as the "Texas Cannonball" was a very influential American blues guitar...

In this tutorial Lindsay Adler will teach you how to add makeup to your models in Photoshop. Sometimes you do not have access to a makeup artist, or after the shoot decide you want a splash of color. Lindsay will teach you to add makeup in a few quick steps in Photoshop.

To make this origami SST paper airplane, begin with a square. The origami SST (supersonic transport) was designed by Dr. James Sakota. The plane was first featured in the 1960's book The Great International Paper Airplane Book, a documentation of the Scientific American first International Paper Airplane Competition. It won first place for origami/nonprofessional. This plane flies excellently in a fast, long distance glide! Learn how to make the origami SST paper airplane by watching this ins...

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

Add a little South American flavor to your wrist by learning to make your own Peruvian bracelet. You'll need some heavy string and some macramé skills to craft your own Peru-style bracelet, but trust us—it's not hard. Just follow along with the video and see how easy it is.

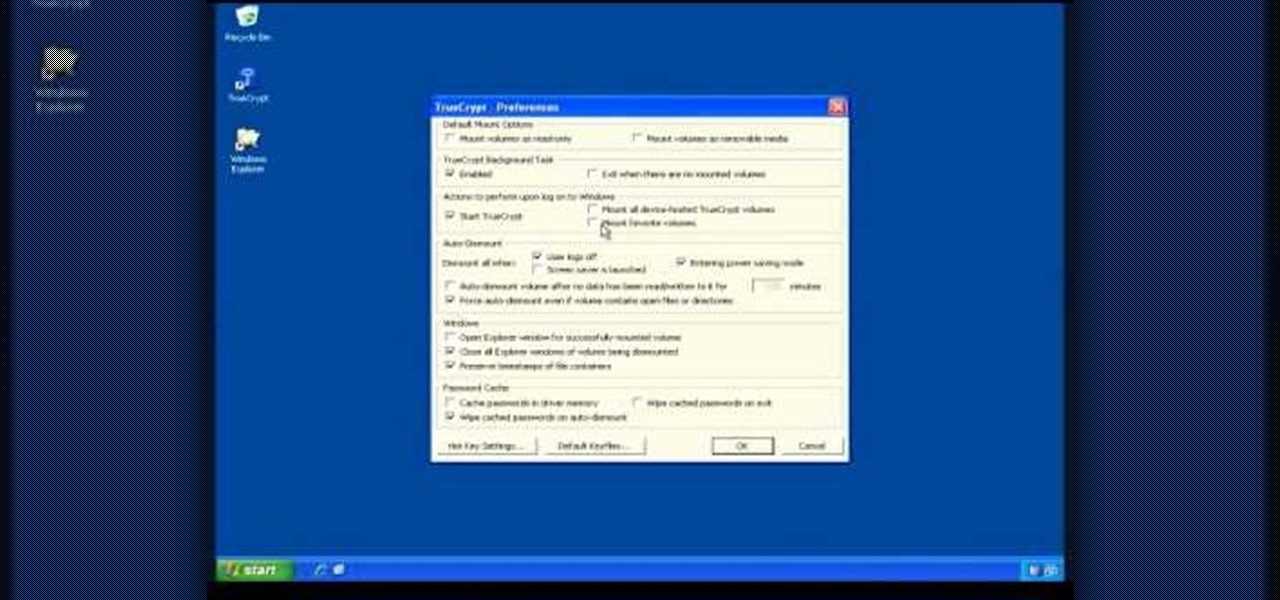
How to use or mount a TrueCrypt volume to access the data that you have encrypted with the program.

If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.

Hey, you, still stuck at home? Cheer up, today is the first day of spring. Yes, really. And since you're probably locked in on TV, we're guessing you need a break from some of the less than sunshiney news reports rolling in. Well, no worries, because there's actually some good news to report.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

There's definitely some malware-ridden apps on the Play Store. When it comes to the third-party apps you've connected to your Google Fit account, some have a crazy amount of permissions they have no business accessing. For example, you probably don't want a heart monitor app having access to your personal location data.

Under the rocket's red glare and the bombs bursting in air, the Statue of Liberty is swaying in celebration this Fourth of July thanks to Snapchat.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

On Thursday, Mojo Vision, a startup comprised of former engineers from Apple, Amazon, Google, and other Silicon Valley mainstays, emerged from stealth backed by $50 million in funding for a hands-free augmented reality platform that runs without smartphones, tablets, or other devices.

For the augmented reality hardware industry to progress towards the consumer segment, display technology needs to get better. Investors recognize that, and they are showing AR display makers the money.

Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. Fortunately, some of you can fix this.

Huawei recently announced the Honor 7X, a mid-tier smartphone aimed at budget-conscious consumers. Spearheaded by the Kirin 659 SoC, it offers great performance at a price point where speed is normally an afterthought. Today, Huawei is making this $199 phone even more attractive by announcing a new limited edition color.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

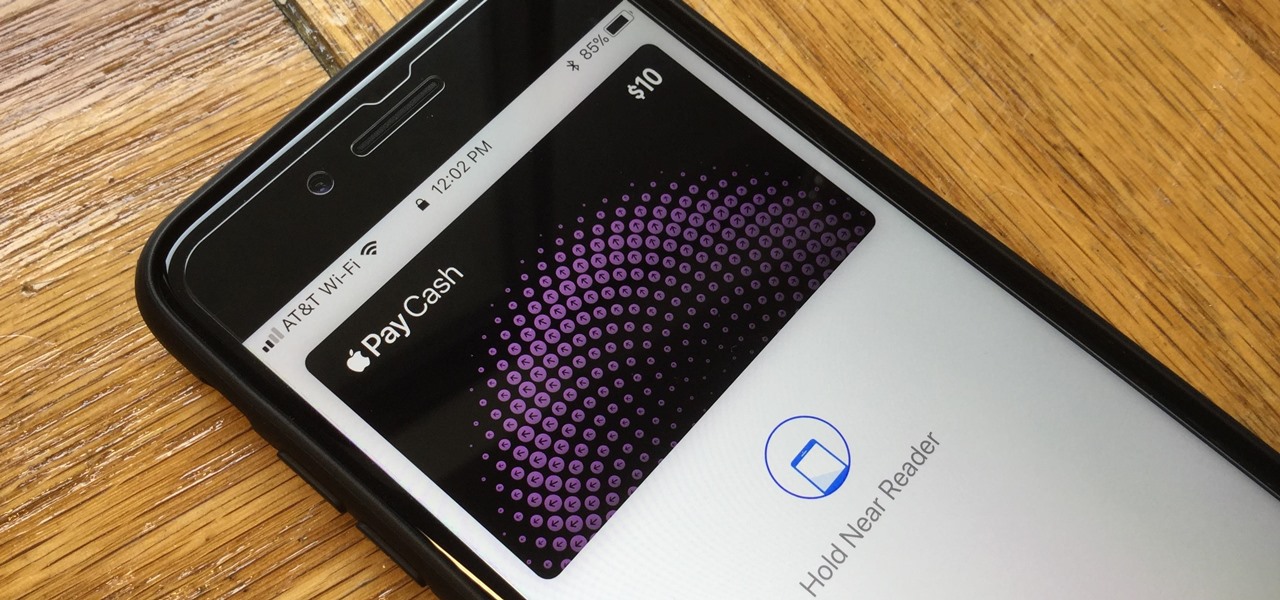
With Apple Pay Cash in iOS 11.2, your iPhone potentially becomes the only form of payment you need. Whether you're sending money to a friend via iMessage or paying for your groceries, you can use Apple Pay Cash to complete those transactions. It makes sense, then, that Apple would allow you to add your Apple Pay Cash card to the lock screen, for quick access wherever you are.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

I don't know about you, but I love options. Personally, I think Android's notification system is easy to use — providing access to new notification with a swipe down from the top of the screen. But, as Android users, we like the ability to do things differently whenever we see fit, so what if you wanted a different way? Well, with Action Launcher, this is possible.

Gestures are a big deal on an iPhone X, XS, XS Max, XR, 11, 11 Pro, and 11 Pro Max. Without a Home button on Apple's super-premium smartphones, several actions had to be mapped to gestures instead, which impacts other areas of the system such as the Control Center.

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

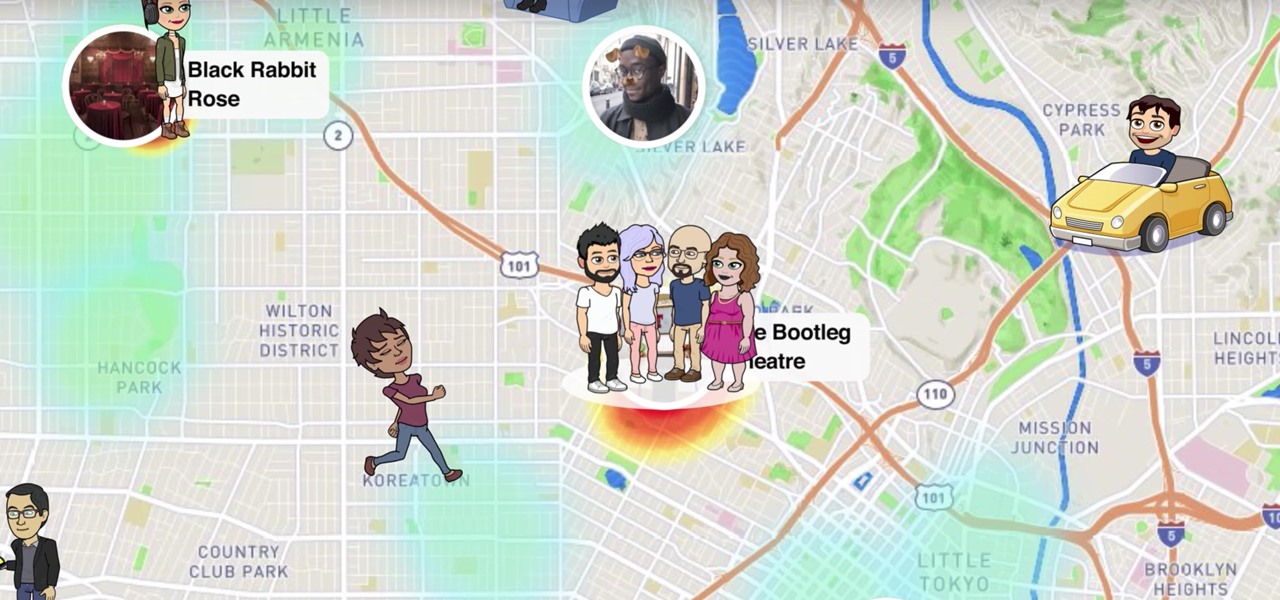
Snapchat recently updated their Android and iPhone apps with a new feature called Snap Map which lets you share your current location with other Snapchatters, as well as see their current locations. It may sound like an interesting new feature, but sharing your exact location with all of your Snapchat followers is dangerous, to say the least. Luckily, it's easy to turn this feature off.

3D Touch is only available on the 6s and 7 series iPhones right now, and likely future models, so those with older devices are missing out on all the cool "Quick Actions" available for app and settings icons. But the new iOS 11 is finally bringing some of those helpful shortcuts to iPhones without 3D Touch built in.

We've heard a lot about self-driving taxis, as car and ride-sharing companies compete to win the driverless gold rush. But FedEx wants to bring its enterprise into the mix, as the head of its freight division has asked the US government to develop laws for self-driving trucks.

Jeep has now jumped on the AR-retail trend with their introduction of the Jeep Compass Visualizer. Customers can now view and customize a Jeep Compass to their liking, all without a real Jeep even present.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Most people I've talked to agree that Shake Shack has mastered the upscale, fast food hamburger quite well. So when a new burger comes out on the ultra-popular fast food chain's menu, you've got to take notice—even if you live nowhere near one.

You've probably heard the old joke about how Ford is an acronym for "Found on Road Dead." Well, the Detroit automaker on Monday announced a new and much better way to help you find your parked vehicle, as well as a whole host of other features—just use your smartphone.

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

With as much creativity and freedom that we have on Android, it feels a little underwhelming that the only gesture we can perform on the status bar is a downward swipe to expose the notification tray or quick settings. Maybe this is a field for Android to expand on in the future, but until that day, third-party developers are exploring this now.

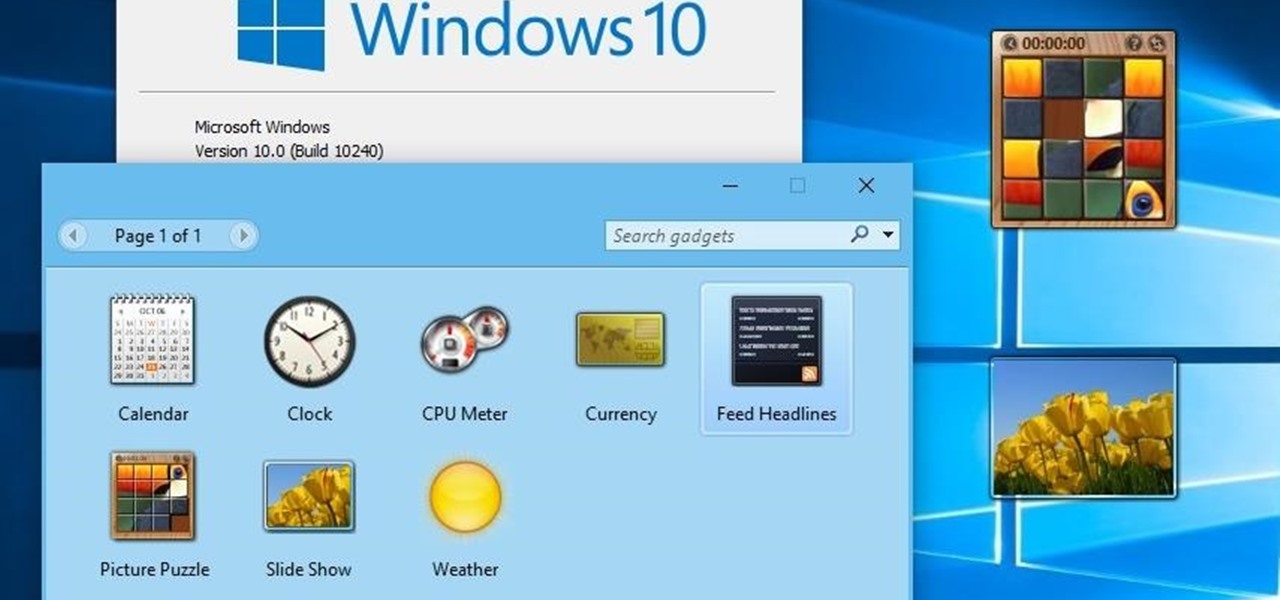
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.

The world's most commonly-used desktop operating system is getting a huge makeover in the form of Windows 10. While there are many sweeping changes in this new version, some of the smaller tweaks may prove to be the most useful.