Kim the in-house mechanic for Driverside shows you how to quickly and easily replace your cars air filter. The reason you would need to change your air filter is that over time the flow is reduced which consequently reduces your car's gas mileage. To change your air filter you first need to locate it on your car. The air filter is under the hood and usually in a box that either has clips of fillip's head screws holding the cover on. Remove these to gain access to your filter. From there you c...

In this video, learn how to convert the American pound (lb.), a United States customary unit of mass, into kilograms (kg), a metric unit of mass in the International System of Units (SI).
Link shortening is the process of cleaning up the URL link which is long and converting it into a short URL. You can use bit.ly to do link shortening. Using bit.ly you can not only shorten the link but also track the users who are using those links. To use this service go to the http://www.bit.ly website. There in the home page you are provided with a text box. Enter your long link in the text box and submit it. Now the website converts the long URL and provides you with a short link which ca...

One of the first things you'll have to do when repairing and opening up your MacBook Pro 17" Unibody is taking off the bottom case. This is where you'll access all of your guts. See how to remove the bottom case on a MacBook Pro 17" Unibody laptop.
Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to shop iTunes on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Check out this quick tip for Apple's Final Cut Pro. See how to use the "add" composite mode in Final Cut Pro. Footage Firm has given DV Professionals access to free footage of a numbers graphic.

Instagram is one of the hottest mobile apps to date, yet they have no way to upload photos straight from your computer. You can log into the Instagram web app to like and comment on photos in your feed, but that's about it. Fortunately, there are third-party apps that let you do more on Instagram from your Mac or Windows computer, so you can enjoy Instagram pics on the big screen instead of your tiny iPhone or Android device.

mIQ? What is it exactly? It's a handy web service that helps you manage your mobile life, with free and easy online access to all of the content and information stored on your mobile device. How does it work? Best Buy has answers. The Best Buy Mobile team explains how simple it is to use mIQ to backup all the data on your cell phone, including messages, photos and contacts.

When you're playing a game on your iPhone, the chances are good that you'll come across an ad you have to watch before you can continue — especially on free games. While it may be annoying to be forced to wait for 10 seconds or even up to a full minute, it can be even more frustrating when you accidentally leave the game to visit the ad's linked app or site when trying to hit the little "x" to continue gaming.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

If you're using a VPN app to block ads or secure your Galaxy's internet connection, Samsung has decided you need yet another non-dismissible notification from One UI to tell you about it. Not just a status bar indicator like Bluetooth or Wi-Fi, but a full-size alert that can't be dismissed. The entire time your always-on VPN is running.

Google's G Suite collection of premium cloud services and apps have become popular with business customers, with more than six million subscribers now.

Some of the oldest art on Earth was created 36,000 years ago on the walls of the Chauvet Cave in France. However, these days, physical access to the cave is restricted in order to preserve the site.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

The landscape of augmented reality marketing is growing by leaps and bounds nearly every month, with Hollywood and the cosmetics industry leading the way.

Parkinson's disease, a condition that can impair movement and coordination, affects over 10 million people worldwide. And with around 60,000 Americans being diagnosed every year, we're on track to see almost one million Parkinson's afflicted Americans by 2020.

The augmented reality cloud will probably be one of the most important pieces of digital real estate in the next few years, and China has no intention of being left out of the virtual land grab.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

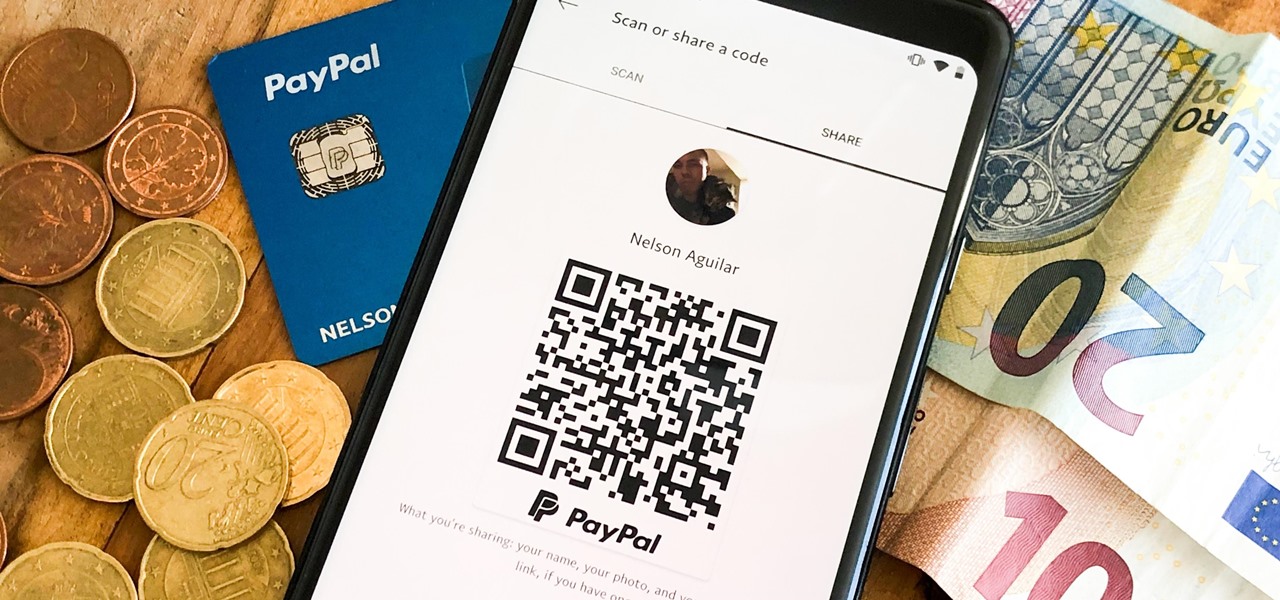
There are many ways to send and receive money on PayPal. You can use an email address, a phone number, or a PayPal.Me link, but if you're standing right next to the person you're trying to pay or get digital cash from, the easiest way, by far, is to use QR codes.

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

The first annual Snap Partner Summit kicked off on Thursday in Los Angeles, and with it came some new products announcements, several of which enhance Snapchat's already robust augmented reality powers.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Mobile app publishers are using augmented reality to solve everyday measurement problems from measuring the length or height of items to previewing furniture in the home.

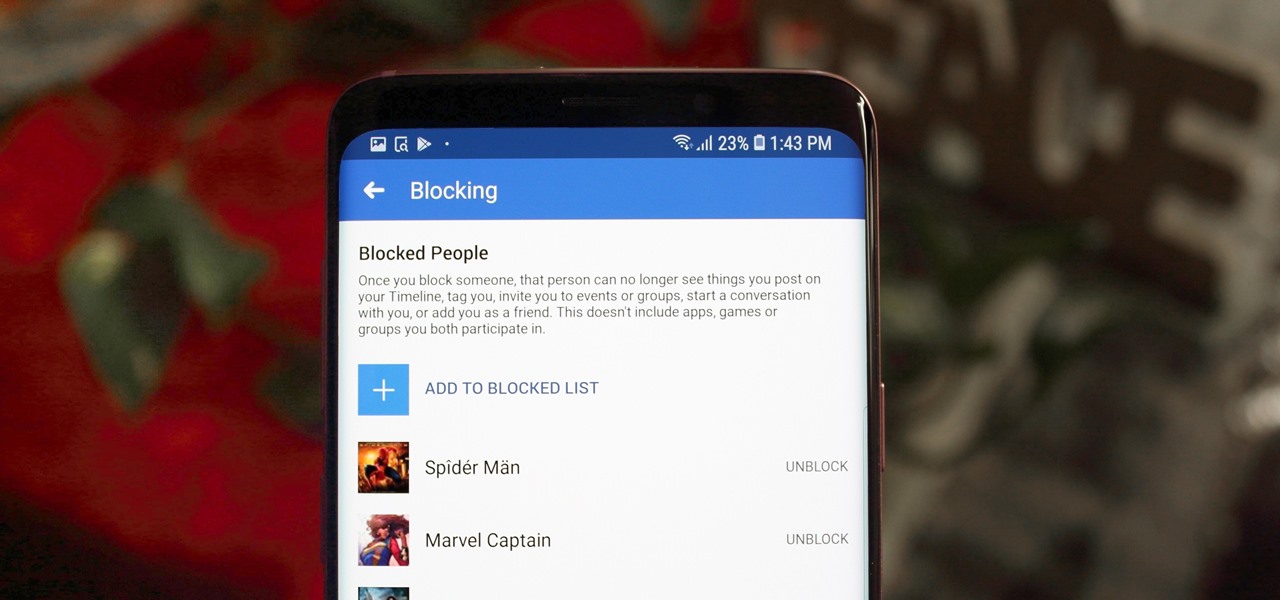
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your profile altogether. It's not just a tool for the full desktop website — in fact, the blocked list is easy to manage right from your phone.

After weathering an executive departure and reports of a failed sale to Apple, Leap Motion is getting back to the business of pushing the envelope for augmented reality development and interaction.

Well-regarded men from the history of the United States tend to grace the country's currency, but what if equally deserving women were honored in the same fashion?

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

The addition of a new research mode for Microsoft HoloLens will enable researchers and developers to tap into a wider range of data collected by the device's sensors.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Another AR cloud savior has emerged this week in Fantasmo, a startup that wants to turn anyone with a smartphone into a cartographer for spatial maps.

Snapchat is making it easier for developers and creators to build augmented reality effects in Lens Studio with a slew of new features, including seven face templates.

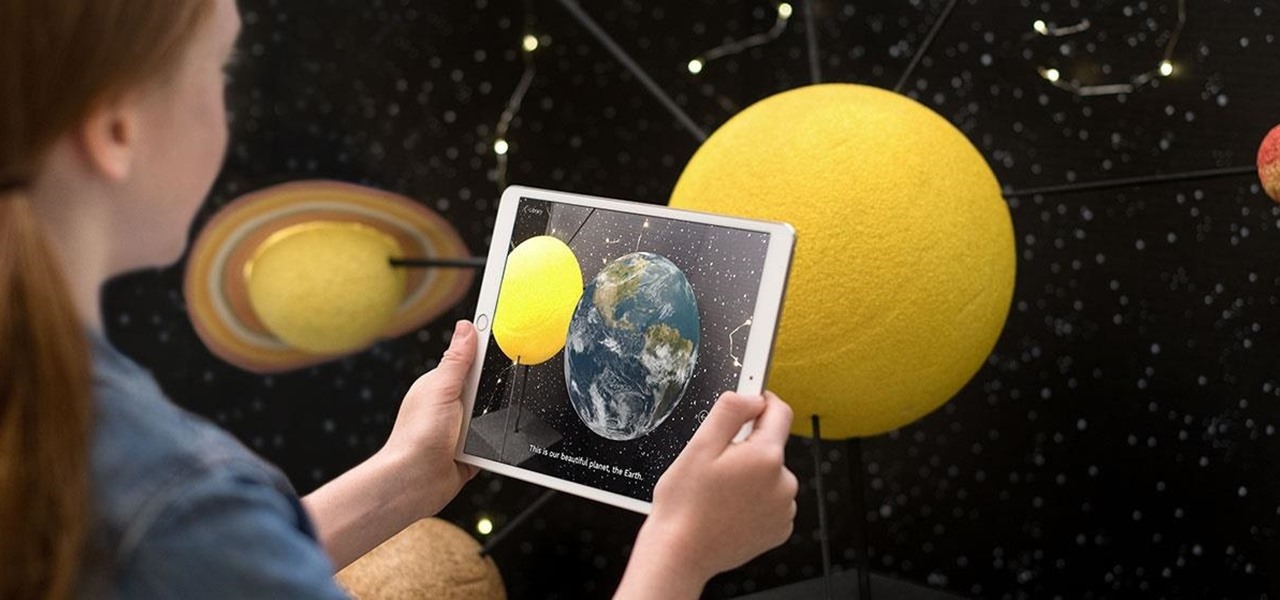
Apple CEO Tim Cook's most recent tech prophecy is that "AR will change everything." And now, that includes Apple's own website.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

In 2018, there are more ways than ever to watch your favorite sporting events. You can stream them with a number of services, or you can simply watch it on a TV. Many fans will even watch it at a sports bar. The problem with a sports bar is that you won't be able to hear the game over the sound of dozens of loud bargoers.

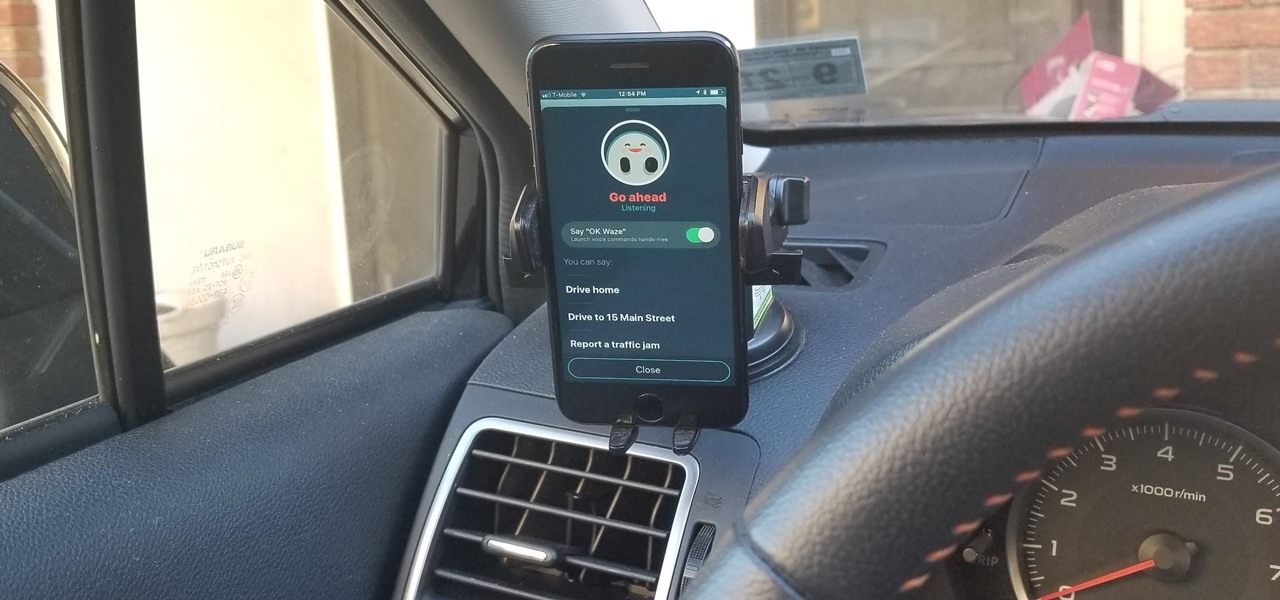
Drivers the world over are painfully aware of the inherent danger of taking their eyes off the road even for a second. In fact, according to the National Safety Council, 27% of all car crashes result from distracted driving due to attempted cell phone use. Fortunately, Waze comes with a feature that can help keep you from being a part of this grim statistic.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.