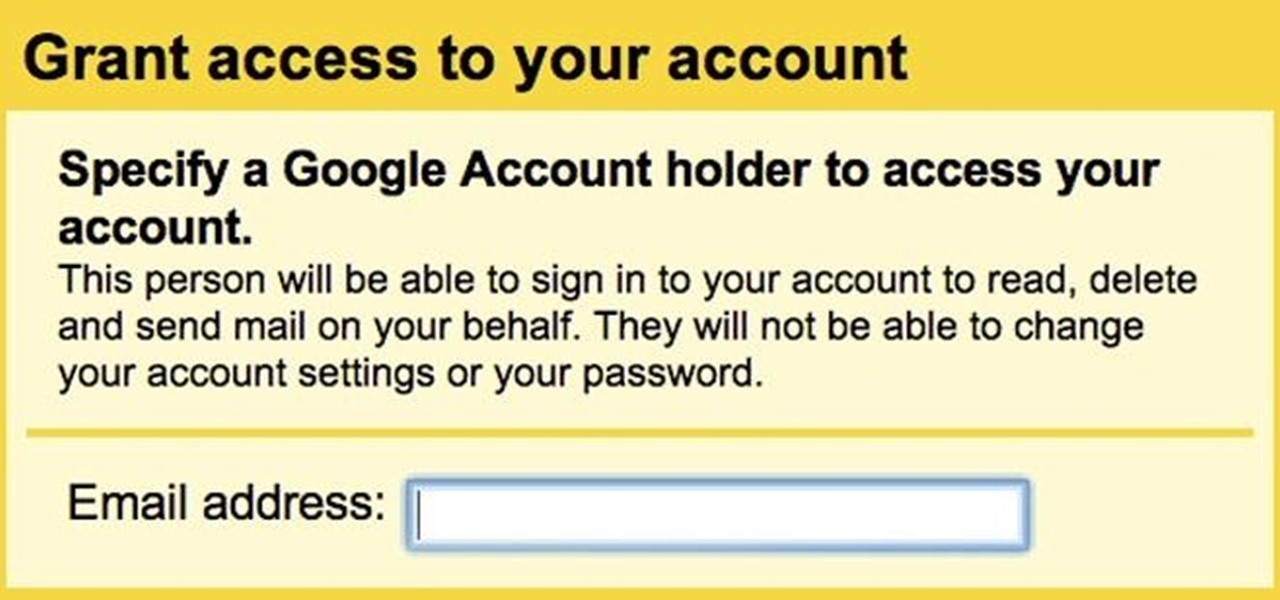
Whether it's because you have no access to the internet or because you're simply on vacation, having someone else check your emails may be a possibility. You can give them your password and screen name, but that's never a good thing. Giving out your password to anyone, even someone you trust, is not something that I would ever suggest for two reasons:

If you bought the new iPhone 5 or upgraded your old one to iOS 6, you may be having issues when you try to upload photos to Facebook. After updating, the first time you try to share an image from the Facebook app, it will ask you to allow access to your Camera Roll.

PICC stands for a peripherally inserted central catheter, and is usually inserted somewhere in your patient's uppper arm, giving access to the larger veins in the chest region. PICC lines are often desirable because they are the least risky way of giving central access to the veins near the heart, especially when your patient will need to have one for an extended period of time. This tutorial shows you everything you'll need to know about how to properly and safely insert a PICC line into you...

For 3D artists new to 3DS Max, learning your way around this massive piece of software can take a long time. It need not do. This video will teach you how to use some of the many hotkeys in the program to navigate it like a pro, easily accessing all of the most popular tools and allowing you to save a lot of time modeling. Now that you know what buttons to press to access functions, watch some of our other 3DS Max tutorials for more advanced functions.

Not every nurse can get an IV every time, that's why it's important to stay in practice for the proper technique used for inserting a peripheral IV. This is a common medical procedure that all fields related to medicine should know. Even the soldiers in the military are taught how to insert an IV — every soldiers, not just the medics.
Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

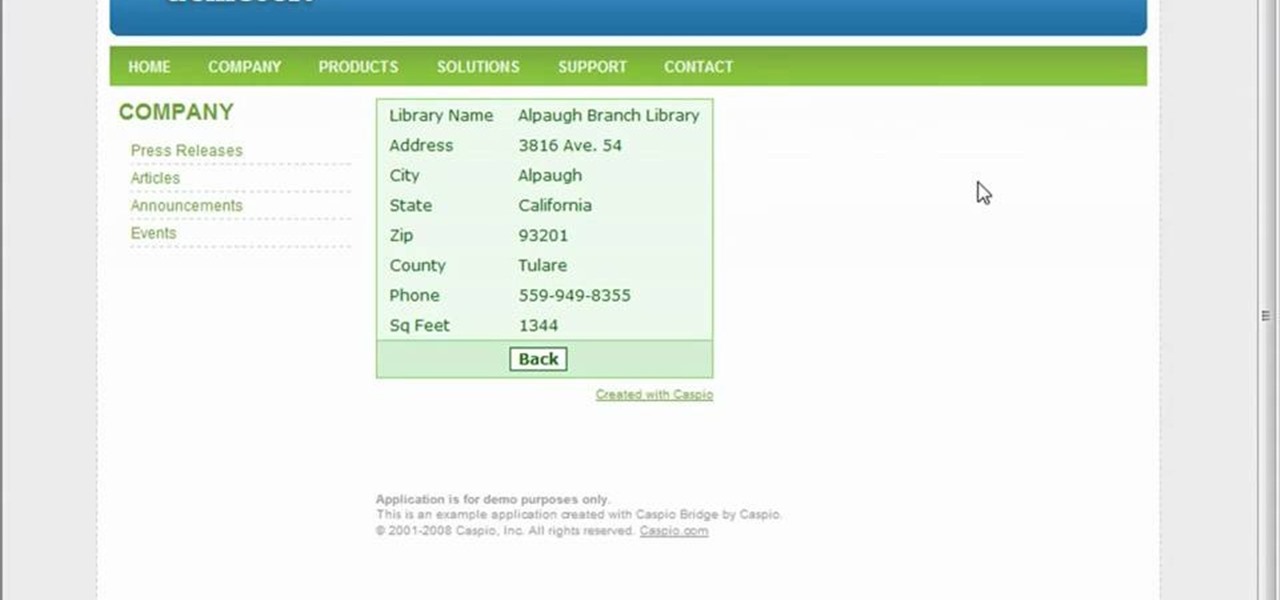
To start off the process of publishing your access database online we first look at a sample MS ACCESS database with typical formats and a online searchable application where users can search by library name or city and get details of the library. There are 3 steps to publish the database. The first step is importing data which can be done through clicking on the file menu and then click on import data through a Microsoft Access Database. Now select the file you want to import through the bro...

Once you have access to the Detroit City Hub in Deus Ex: Human Revolution, it's possible to unlock a secret achievement dubbed 'Balls' on the Xbox 360 version of the game. This Giant Bomb walkthrough will help you locate the basketball hoop you'll need to earn the achievement with, and give you a little tip on how to easily get the ball through the hoop.

Clip Art from Microsoft Office allows you to insert stock photos into you PowerPoint, Word, Excel and Entourage documents easily. You can gain access to the Office Clip Art site easily in any of the mentioned applications. The Microsoft Office for Mac team shows you just how to download and use clipart from Office Online in this how-to video. You can get free stock images of low-priced professional quality photos.

If you're trying to streamline your work on your Windows 7 PC, here's a handy little program to help you speed things up. Quick Cliq lets you you customize your Windows startup menu to give you one-click access to files, folders applications.

Access your iPad's capabilities for foreign languages, special characters, Caps Lock, and more. Start with the Keyboard Setting in your General section, where you can find numbers, symbols and extra characters, as well as typing shortcuts (like tapping the spacebar twice to insert a period).

Rooting your phone grants you superuser access to your phone. And while this will void your warranty, it will also allow you to download third party applications (among other things). This tutorial shows you the process for getting root access on a Samsung Captivate cell phone.

In this Computers & Programming video tutorial you will learn how to use the Remote Desktop feature within Windows XP. This application will enable you to access your home computer from office using the internet. This application is really very easy and simple to use. You have to ensure 3 things for this to work. Ensure that the computer on which your files reside that you want to access has all the components of XP installed. This is the host. The computer that you want to use to access the ...

This video tutorial gives you a way to access websites that you can not normally access because of a web block or filter. What you need to do is click on the ‘Start’ button and then click on ‘Run’. In the small window, type in ‘cmd.exe’; this then opens a black window. Then type in ‘ping’ and the website; this gives you an address that you type in directly to your web browser, granting you access to a normally blocked website. This comes in very handy when you are in such locations like schoo...

Can't wait until you get home to get onto MySpace? This video gives step by step instructions on how to try and unblock MySpace while you are at school or on a server that does not allow access to the site. This video does not have narration, but has written instructions on how to get around blocked sites with out using a proxy server. However, you have to have access to the system 32 files for this tutorial to work, and accessing these files does go against a lot of network policies.

Using a Phillips head screwdriver remove the screw under the handle in the back of your iMac. Remove the screws outlined in the picture below. Remove screws 1 and 2 with a standard Phillips head screwdriver. Screws 3 and 4 use a standard flat head screwdriver. After removing the screws, gently pull out all of the plugs. Next holding the clear handle just below the bar code, pull out the section of the iMac.

Brown construction paper comes in handy when you are working at a site. It however can be a pain to access and cut. Watch this how to video to make an easy access rolling paper rack at any construction site. Use it to cover floors and cabinets without having to bend over.

Sometimes the difference between a sprain and a fracture can only be identified with an x-ray. However with the help of this first aid how-to video you will learn to properly treat a sprain. Complete a modified primary survey of the work related accident, access the limb that was injured, and apply ice. These first aid tips will help your workers stay healthy.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

A tutorial about why the two page resume isn't appropriate for most IT positions, and how to access a Linux server remotely and change the run level to turn off the GUI.

It wasn't too long ago that the power menu for stock Android didn't offer much beyond turning the device off, but Google has steadily added more functions, like capturing screenshots and provisioning access to emergency information.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

The story of Meta and its Meta 2 augmented reality headset isn't over, there's a new development that could impact its ultimate fate.

Do price tags on mobile games give you pause? We get it. With so many freemium games out there, it's tough to justify spending three or four dollars on a game for your iPhone or Android device. That's why you wait for moments like this one, as both "Reigns" and "Reigns: Her Majesty" are aggressively on sale.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

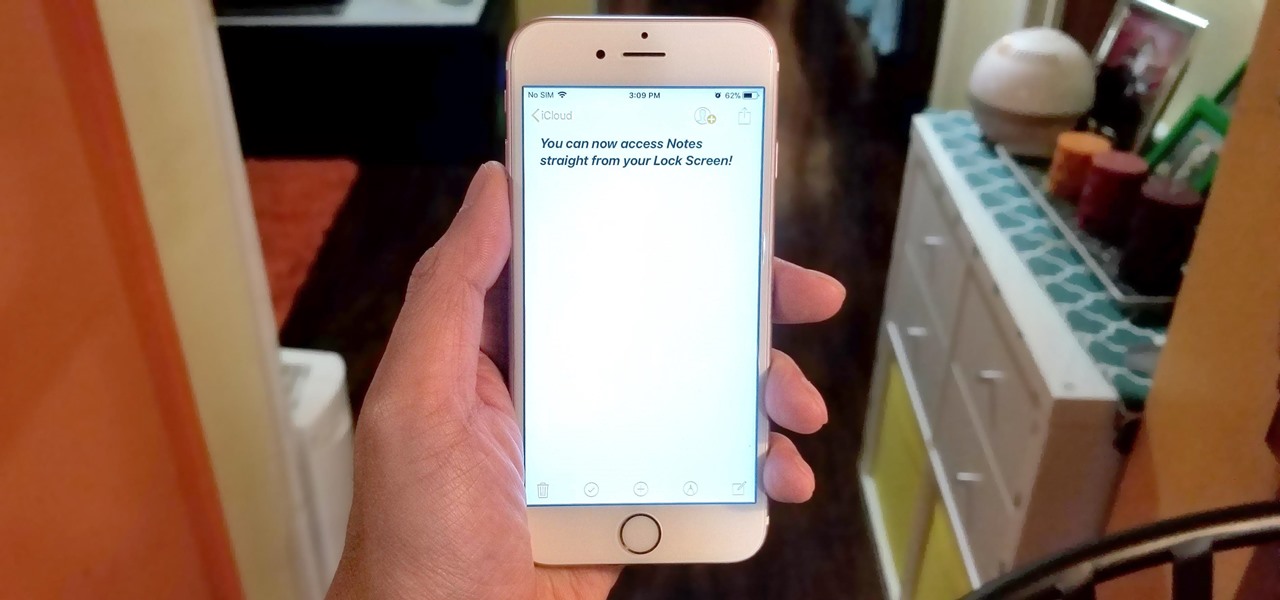
All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

AirDrop is an underrated feature that lets you to quickly transfer files like songs and photos via Bluetooth and Wi-Fi from your iPhone to Macs and other iOS devices. It's been a staple in the Control Center ever since iOS 7, prominently displayed for easy access. However, with iOS 11, that quick access to AirDrop has seemingly disappeared.

Is the Home button the main reason you haven't pulled the trigger on a new iPhone? Are you worried that you'll miss its functionality too much, or that simple things like accessing your home screen will be too hard? Well, don't worry about any of that, because Apple came up with some intuitive gestures that makes the old Home button seem clunky and outdated once you get used to things.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

It's about time people acknowledged that judging drug users would do nothing productive to help them. In the US this week, two new programs are launching that should help addicts be a little safer: Walgreens Healthcare Clinic will begin offering to test for HIV and hepatitis C next week, and Las Vegas is set to introduce clean syringe vending machines to stop infections from dirty needles.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

The awesome thing about Android is that you rarely need to settle for what comes stock on your device. If your music app sucks, switch it. If you don't like your home launcher, swap it for a better one.

Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

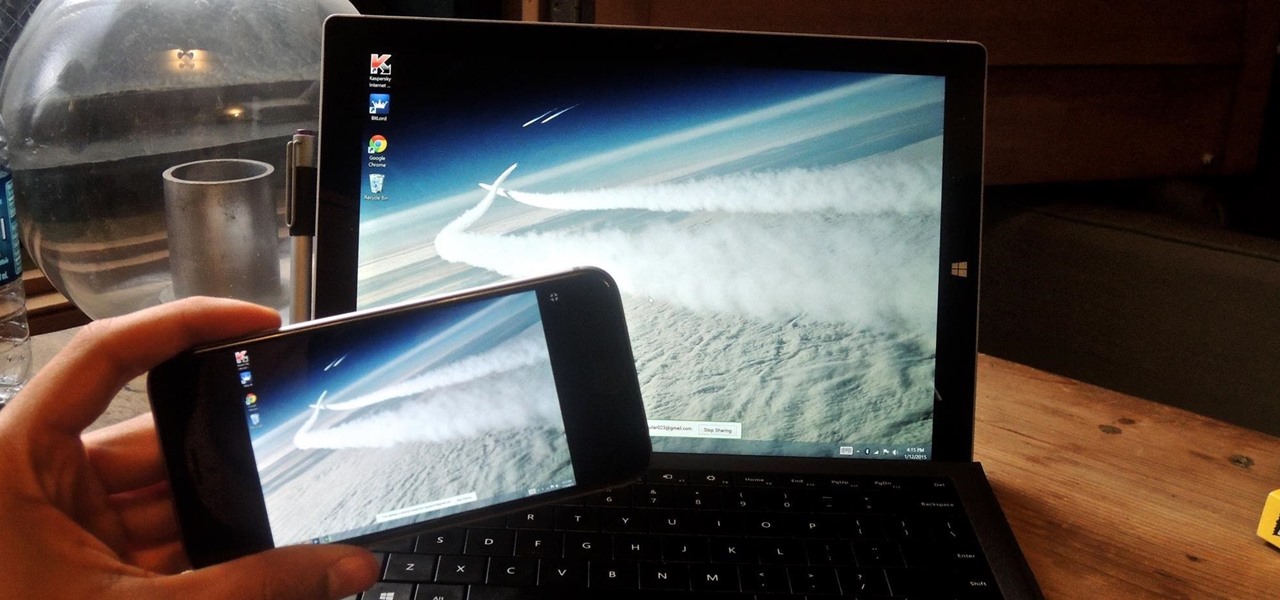
Google's Chrome Remote Desktop, which allows for remote access to your personal computer from your smartphone, has been out for almost a year now. Sadly, it's only been available for Android devices—until now. So, if you got an iPhone (or other iOS device), you can now access and control your computer directly from your smartphone or tablet just like with Android.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.