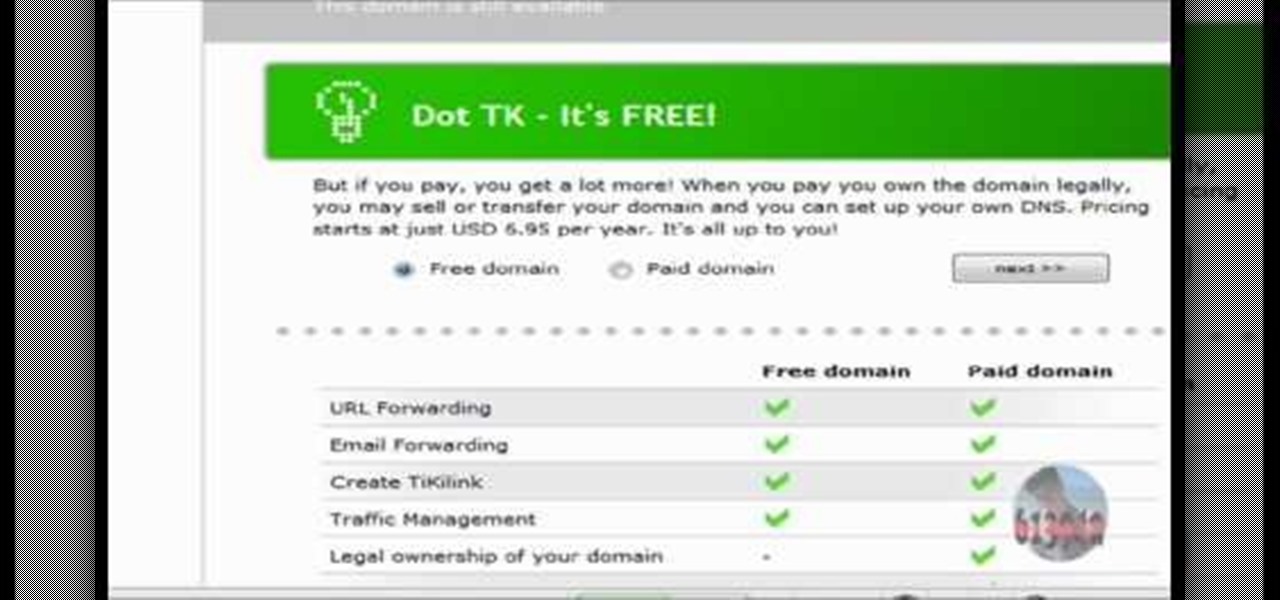
In this tutorial the author shows how to use a proxy at your school and get on the blocked site like MySpace etc. Now he points to the Dot.tk website and how to access it from Google.com. Now if you want to access any website you just need to copy the link and paste it into the pointed field in the Dot.tk website and now you can choose a new domain name for the website. Now you can choose the free domain option in the next page where the new website is setup. Now he shows how to go through th...
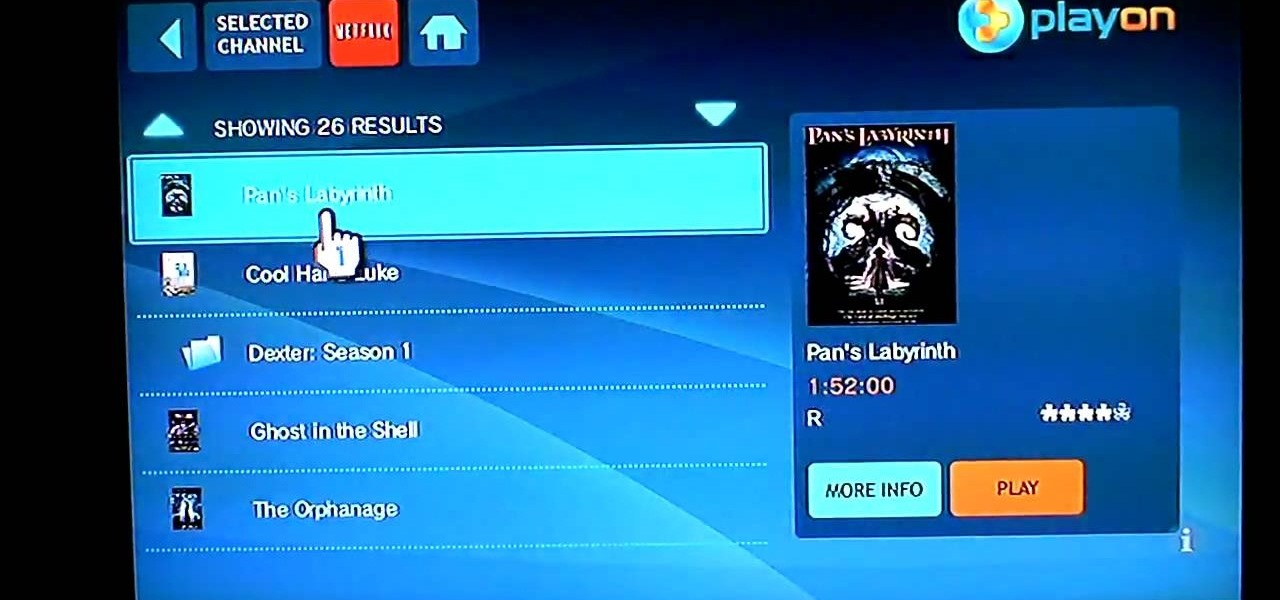
In this how-to video TechVW shows you how to watch Hulu, Netflix and more on a Wii home gaming system. He shows by using a web program called PlayOn that can be accessed through Wii Opera, you can connect to your computer to play videos streamed over the network. He goes on to show the different services offered and how to access each of them and a brief display of how they are used and what features they have.
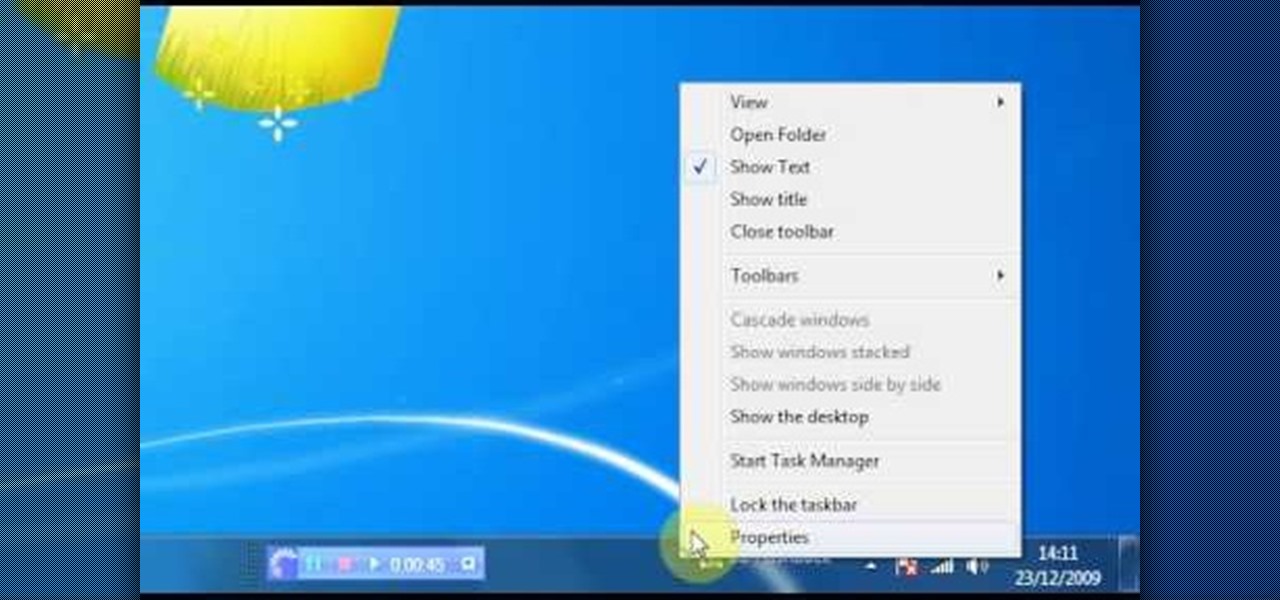
Check out this video for info on how to setup the quick launch toolbar in Windows 7. Quick launch makes it easier and faster to access your favorite folders and programs. The quick bar can be activated and deactivated depending on your preference and provides simple access to frequently used objects. This tutorial will show you a quick step by step to activate this handy tool in Windows 7 just like it worked in Windows XP and Vista.
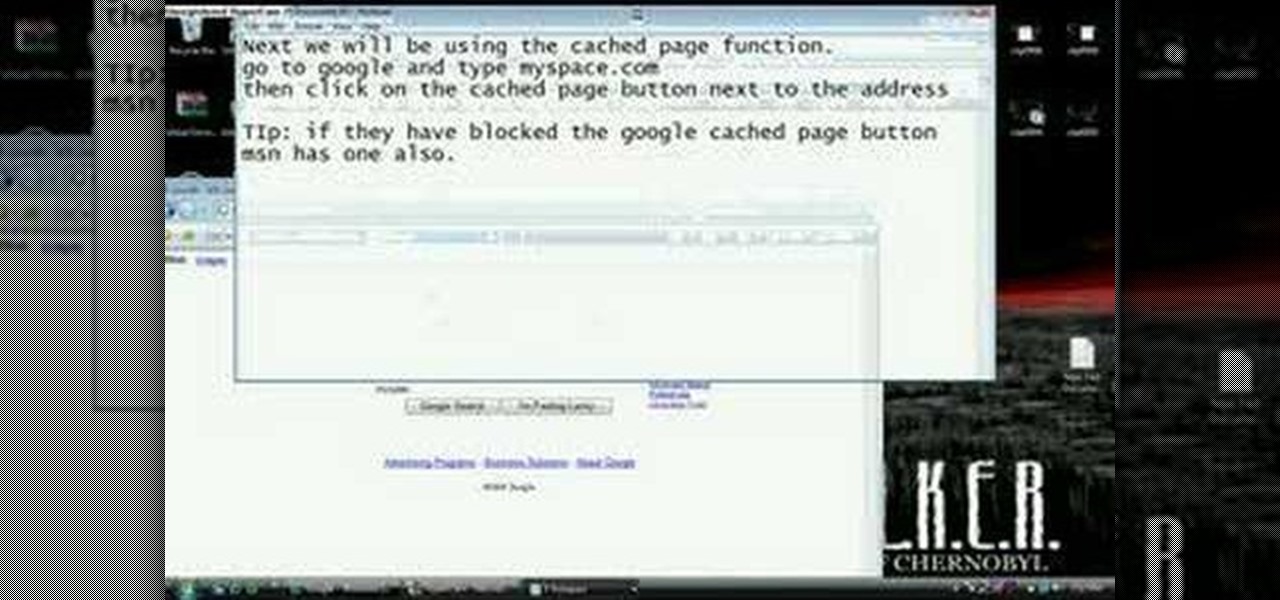
Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt.
Get more out of Google Maps with their improved places pages! Most people don't know how much information Google Maps provides users with. This episode of Tekzilla will educate you on how to access this comprehensive page and make the most of your Google Map experience.

Changing the hold music piped into your company phone is a prank some callers will appreciate—depending on what you replace it with.

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

Studying to be a nurse? Then here is a nursing how-to video that teaches you how to do a central venous access. Every nurse should know the basics of this technique, follow along and see how easy it is to draw blood from a central line. These medical tips are sure to help you pass your nursing exam with flying colors. Remember when performing a central venous access, all caps must be replaced each time blood is drawn. You must swab the port for 1 min prior to withdrawal. Follow your hospital'...

There is a security flaw with any Apple iPhone running firmware version 2.0.2. This flaw potentially gives a person access to your email account and contacts when you have your iPhone locked. This video demonstrates a simple, but impermanent, fix for stopping others from accessing your private information. To protect your own Apple iPhone, watch this tutorial.

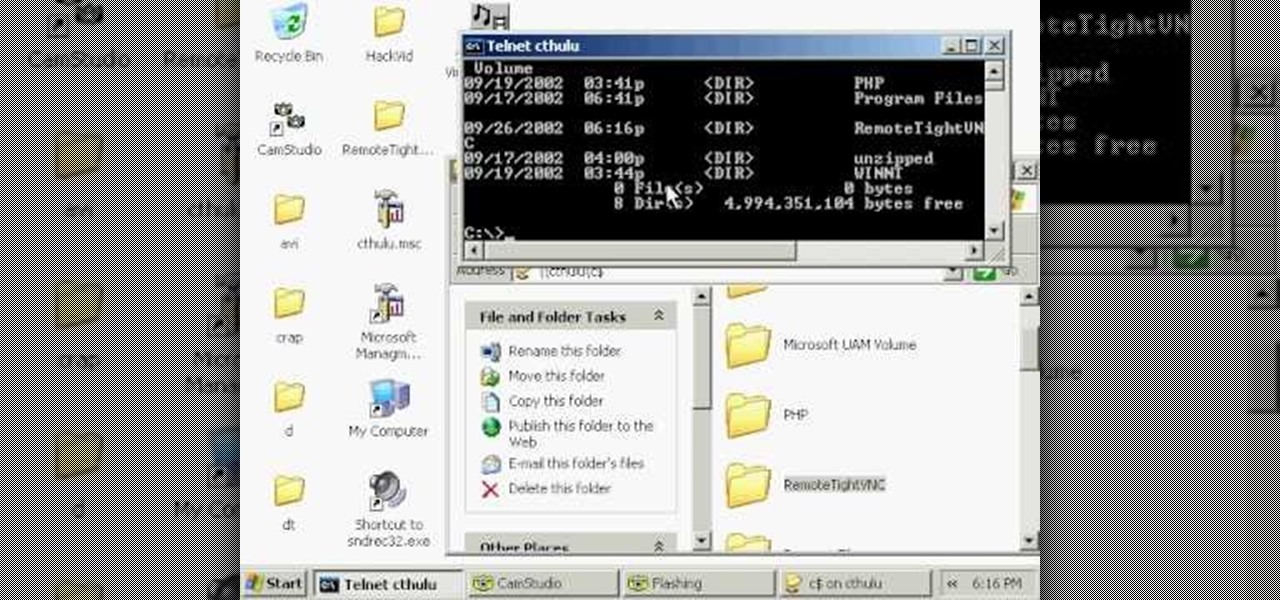
In this video tutorial, you'll learn how to install VNC, or Virtual Network Computing, remotely onto a Windows machine for GUI access. This tutorial assumes you know how to start a session and get into active command line access in a remote Windows PC. For step-by-step instructions, press play.

This video will show you how to access the application store from your iPhone 3G, and then show you some demonstrations of a few selected apps that you could get. If you have a new Apple iPhone 3G, this is an awesome feature. Play games, keep organized, find movies... you can do it all on the Apple iPhone 3G, right out of the box.

An explanation of how to get access to your Linux desktop from any other computer connected to the Internet.

From Windows 95 through Windows XP, setting file and folder permissions was accessed in the same way. With the introduction of Windows Vista, many things have moved, including this feature. While it works in largely the same way, the steps you take to access these features has changed. This short video will take you step by step through changing file and folder permissions in Vista, with a focus on setting hidden files to show in Explorer.

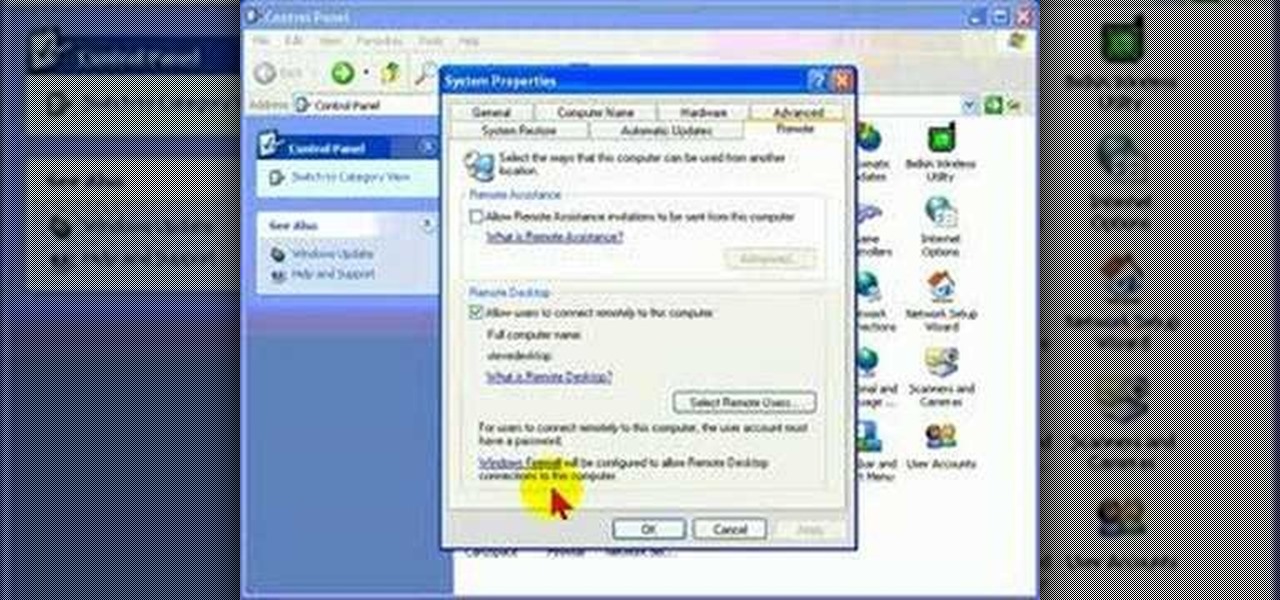
Remote Desktop is a feature of Microsoft Windows, that allows you to access your PC from anywhere in the world, and use it as if you were sat right in front of it.

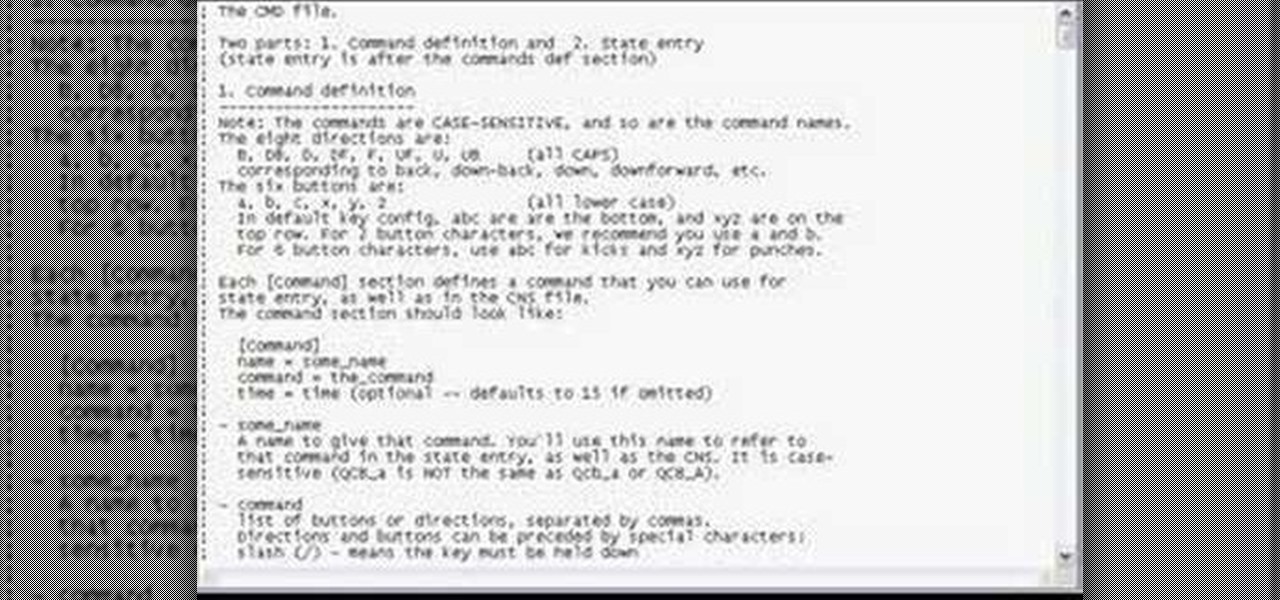
This is a tutorial on how to access characters command list in Mugen - the custom PC game engine - to see how to perform special attacks and basic moves.

In this video you will see how to access network security cameras through google search engine easily!

In iOS 13, Safari has become even more powerful, especially when it comes to privacy. The browser will warn you when you create a weak password for a new account. Your history and synced tabs in iCloud are end-to-end encrypted now. And there are per-site settings that let you choose which domains can and can't have permission to use particular device hardware or sensors.

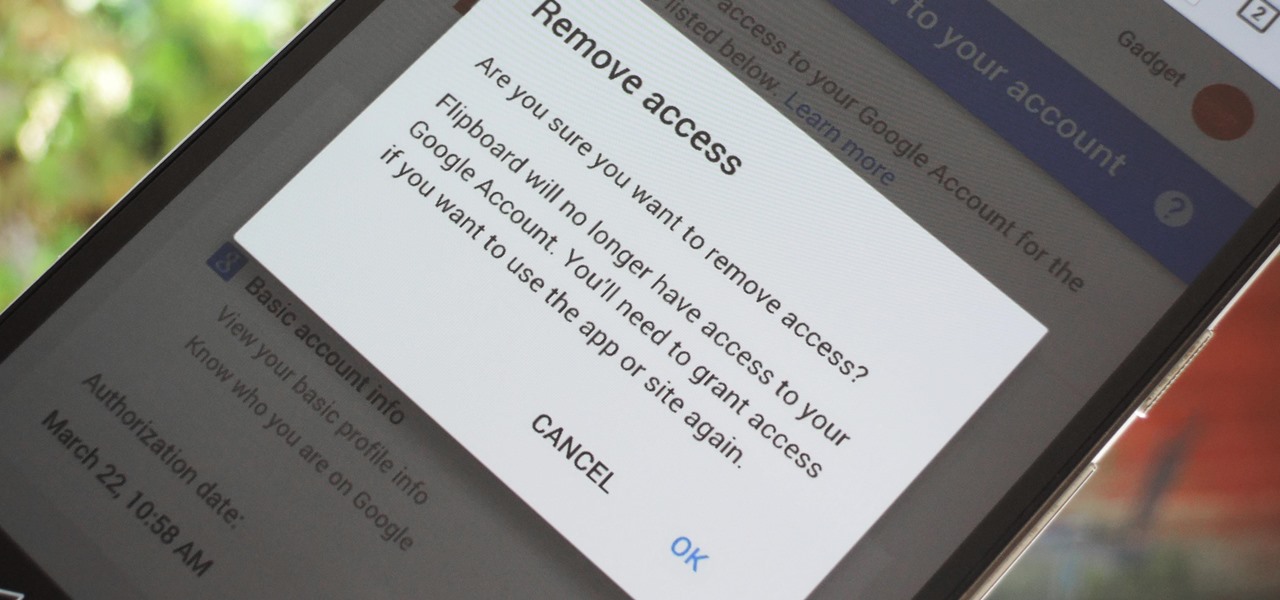
Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

Five Phases of Hacking:- The five phases of Hacking are as follow:

For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

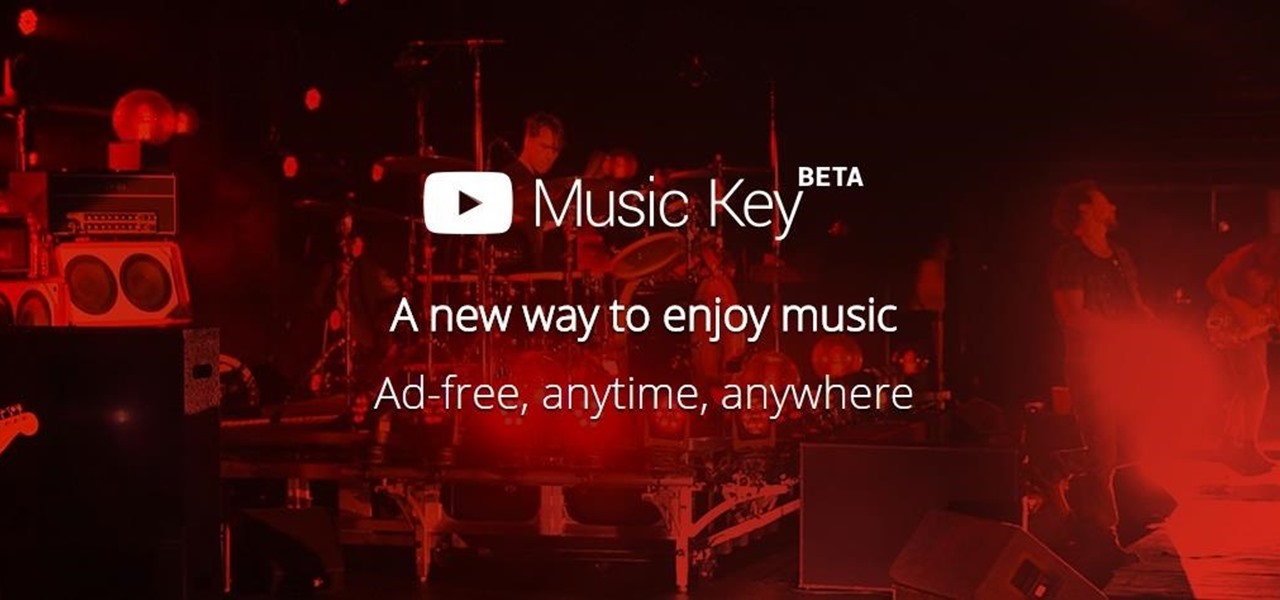
It's been rumored for months, but now we've got some official news about Google's newest music offering, YouTube Music Key. The subscription service will allow for an ad-free experience with background listening (i.e., having your screen off) and offline playback.

Accessing your recent contacts just became a hell of a lot quicker with iOS 8. In addition to accessing recent apps, double-pressing your Home button now shows off recent contacts at the top of your screen.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

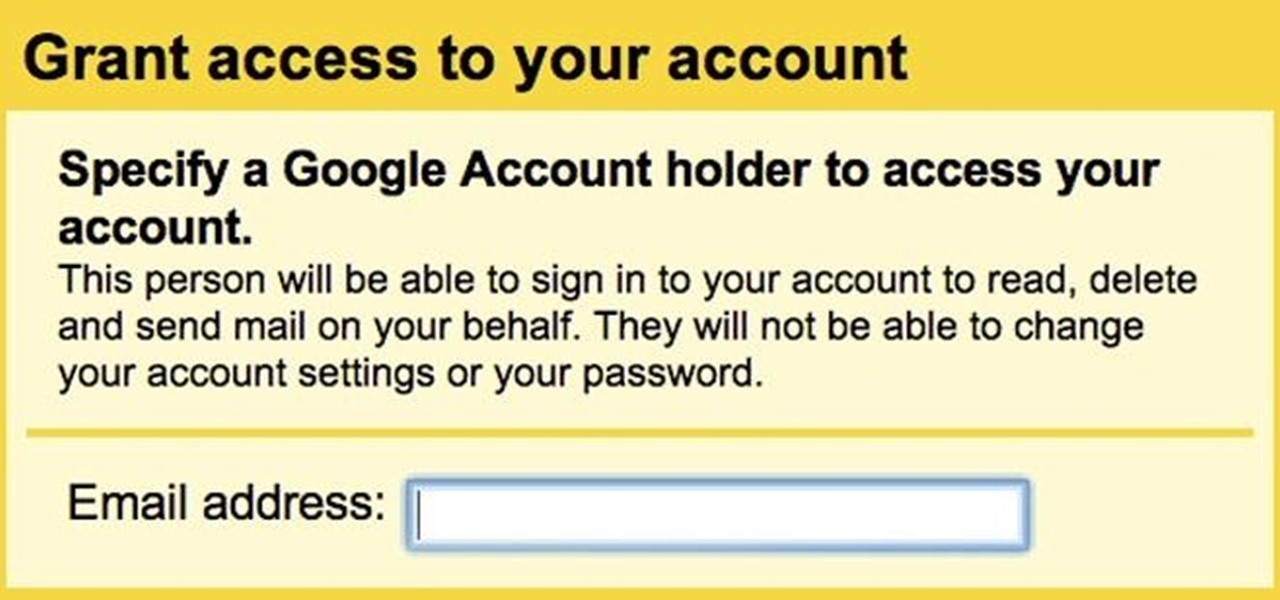
Whether it's because you have no access to the internet or because you're simply on vacation, having someone else check your emails may be a possibility. You can give them your password and screen name, but that's never a good thing. Giving out your password to anyone, even someone you trust, is not something that I would ever suggest for two reasons:

PICC stands for a peripherally inserted central catheter, and is usually inserted somewhere in your patient's uppper arm, giving access to the larger veins in the chest region. PICC lines are often desirable because they are the least risky way of giving central access to the veins near the heart, especially when your patient will need to have one for an extended period of time. This tutorial shows you everything you'll need to know about how to properly and safely insert a PICC line into you...

For 3D artists new to 3DS Max, learning your way around this massive piece of software can take a long time. It need not do. This video will teach you how to use some of the many hotkeys in the program to navigate it like a pro, easily accessing all of the most popular tools and allowing you to save a lot of time modeling. Now that you know what buttons to press to access functions, watch some of our other 3DS Max tutorials for more advanced functions.

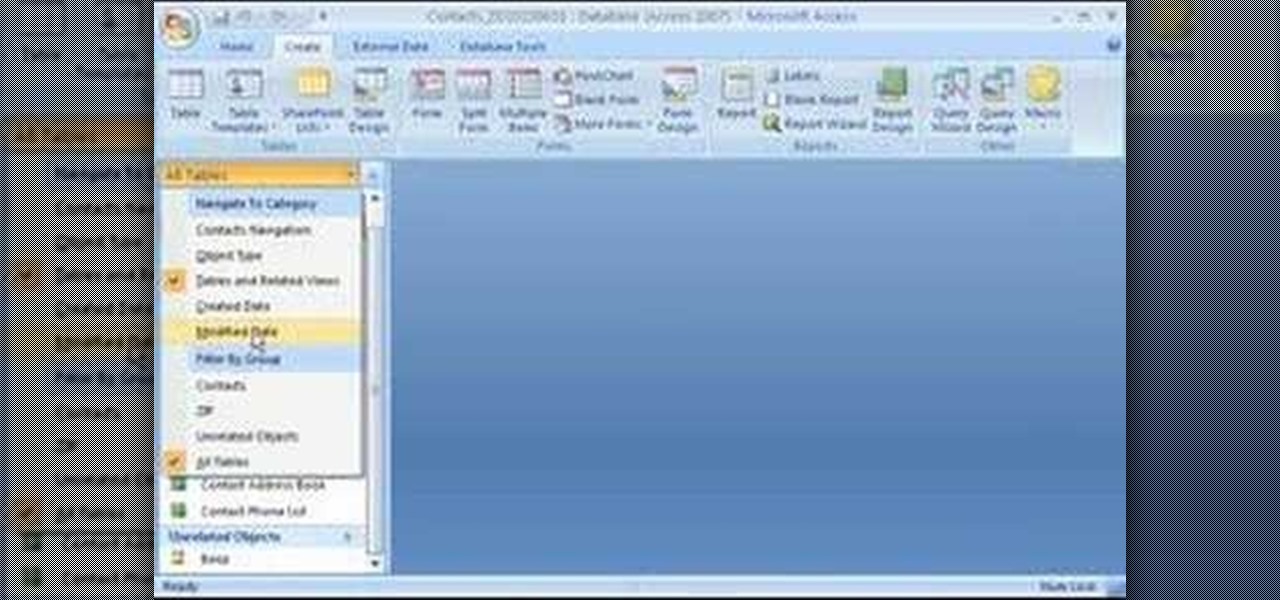
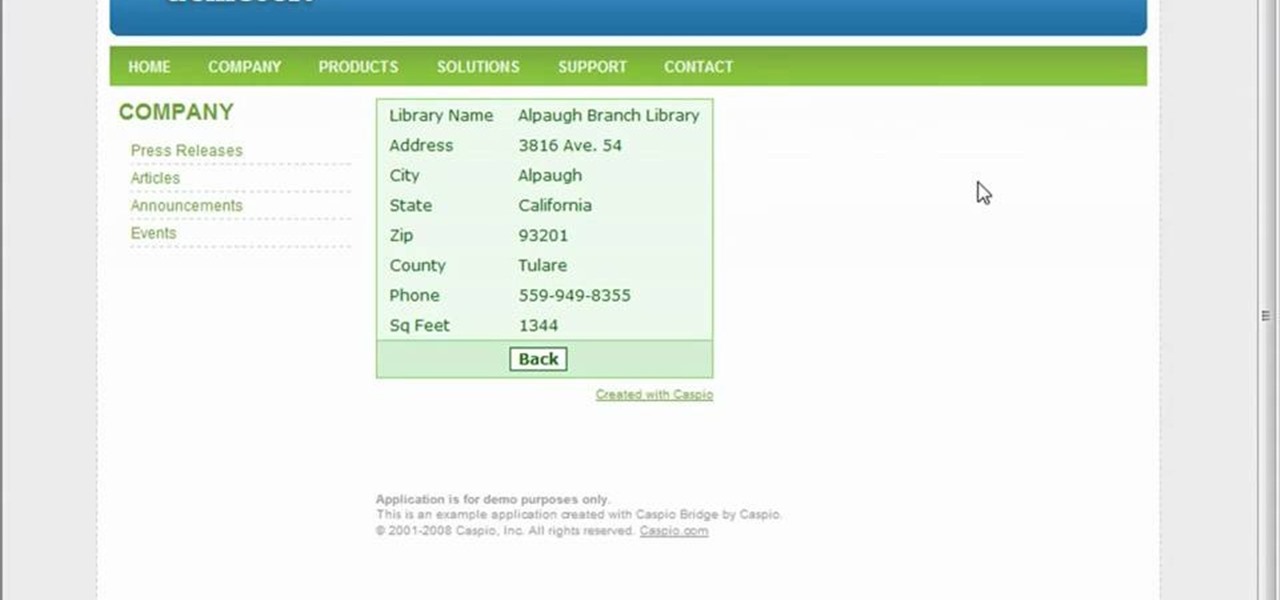
To start off the process of publishing your access database online we first look at a sample MS ACCESS database with typical formats and a online searchable application where users can search by library name or city and get details of the library. There are 3 steps to publish the database. The first step is importing data which can be done through clicking on the file menu and then click on import data through a Microsoft Access Database. Now select the file you want to import through the bro...

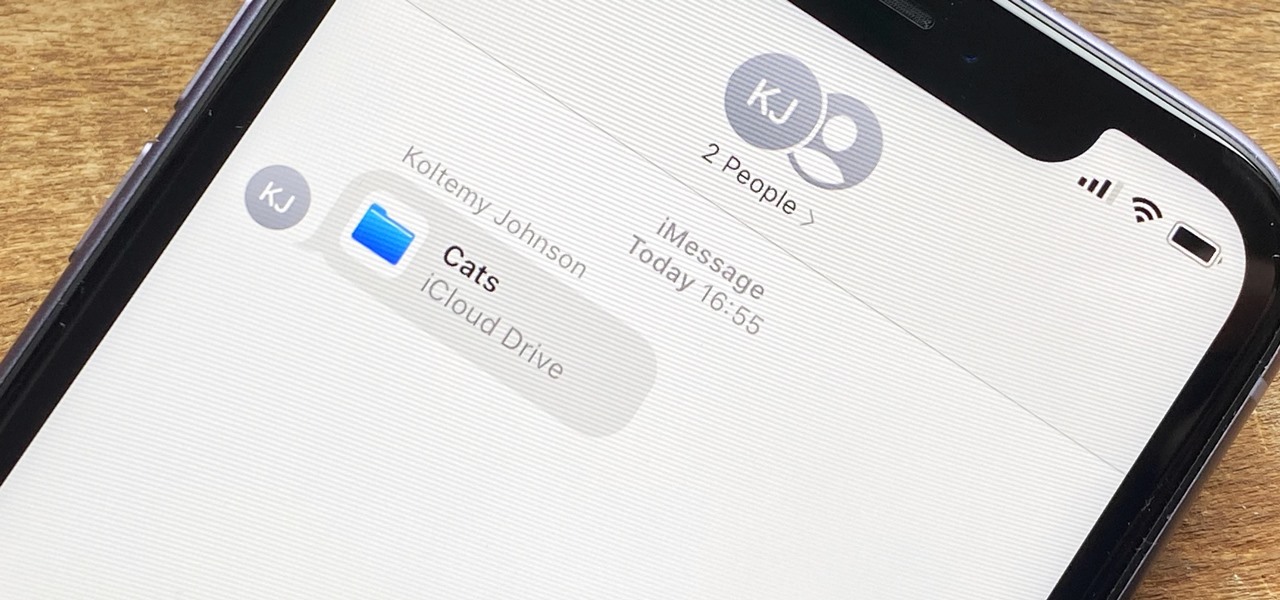
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

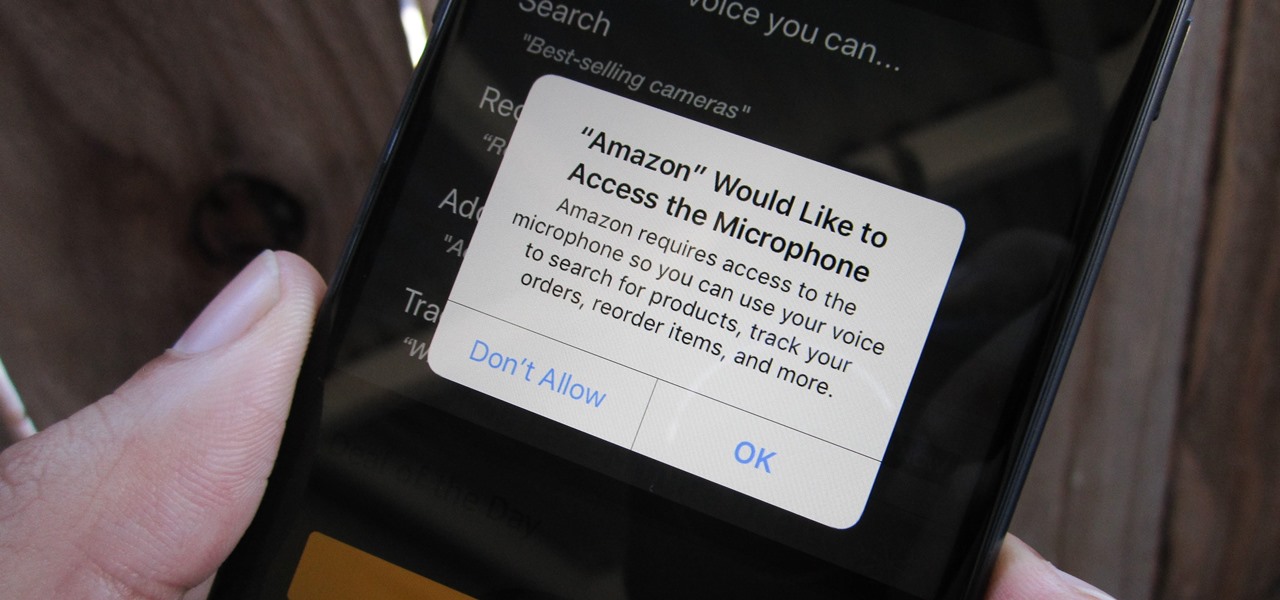
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

Many apps and services that are available for Android can only work if they have access to your Google account. While you're setting up one of these apps, you'll see a popup that says something like "This app would like to access your Google account," and the options are "Accept" or "Cancel." Of course we tap "Accept" here to ensure that the app will work properly, but what are the long-term repercussions of doing that?

A new iPhone exploit has recently been discovered by YouTube user videosdebarraquito, who has found many other exploits and bugs in iOS over the years. This new exploit allows someone to bypass the lock screen and gain access to contacts and photos via Siri, Apple's digital voice assistant—but it only affects the iPhone 6s and the iPhone 6s Plus because it requires 3D Touch functionality.

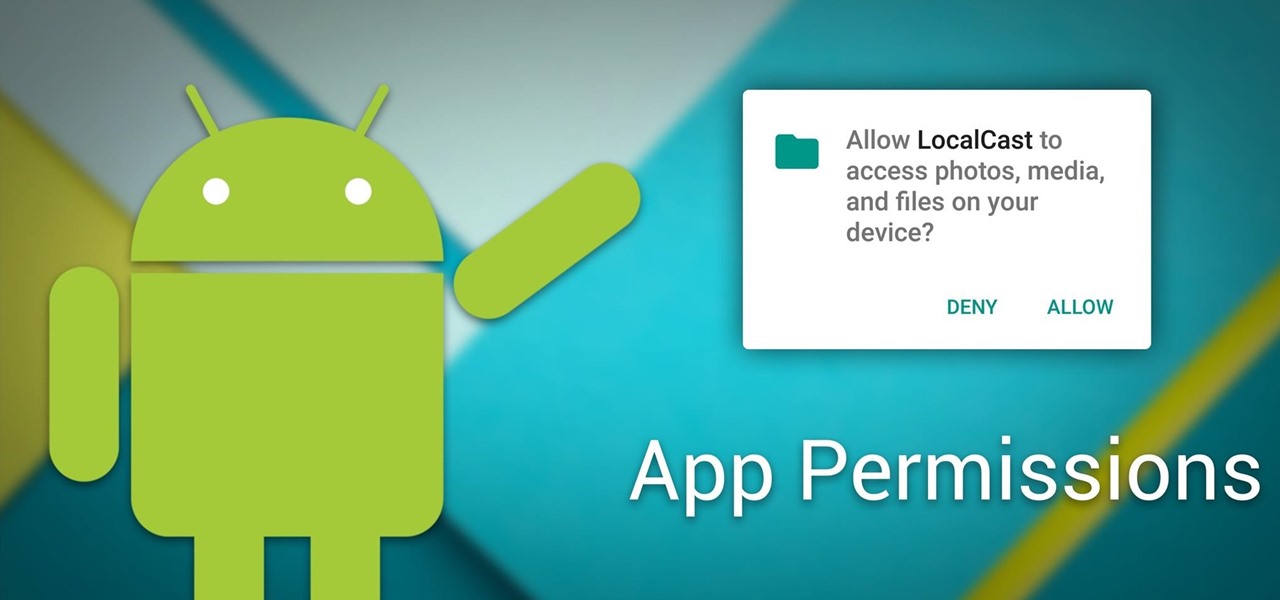
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat.

Contacts on your phone can be messy. Keeping all of those numbers, emails, and addresses organized takes time and, even then, they still may not be be as accessible as you want them to be.

It's hard to believe it's already been a year since I was frantically searching every Best Buy in the Los Angeles metropolitan area to find one with a Chromecast in stock.

Improved S Pen functionality materialized in the form of Air Command controls on the Samsung Galaxy Note 3, allowing users to access shortcuts for their stylus features from anywhere on the screen. While the pie-interface controls are extremely useful, the only way to access them is when the S Pen is removed—making it impossible to use otherwise.

If you bought the new iPhone 5 or upgraded your old one to iOS 6, you may be having issues when you try to upload photos to Facebook. After updating, the first time you try to share an image from the Facebook app, it will ask you to allow access to your Camera Roll.