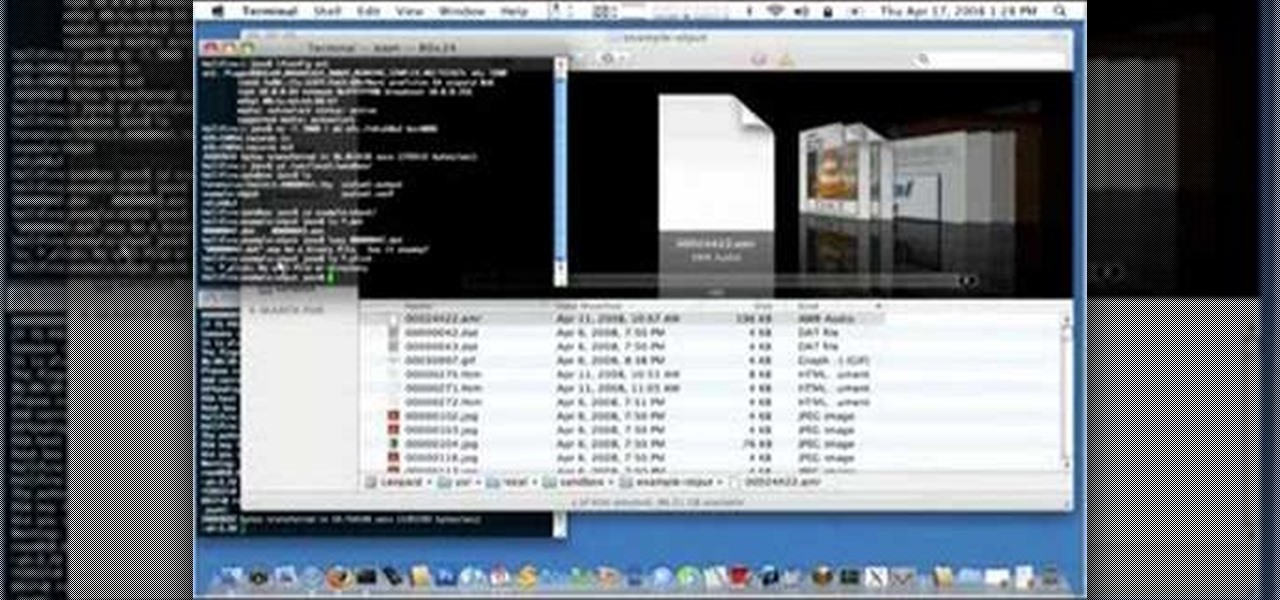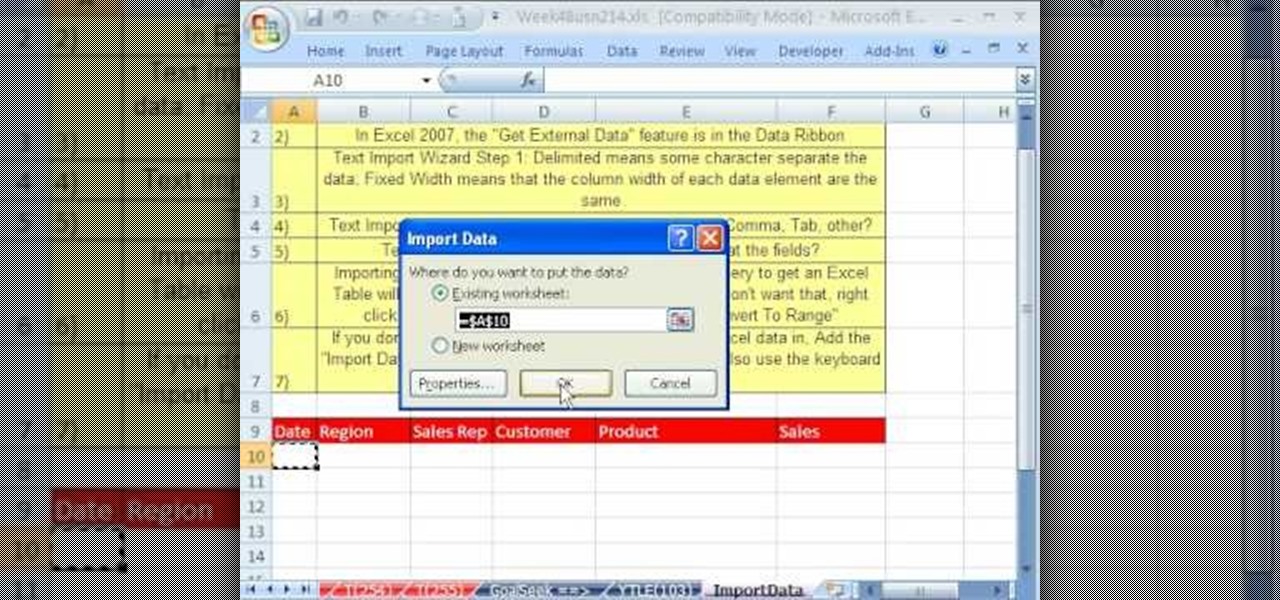
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 23rd installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to import data into Excel from text files, web sites, Excel files and Microsoft Office Access files. Also see how to import currency rates and major indicies from ...

In order to access your wireless router settings in a Windows PC you need to use a command called ipconfig. The purpose of this command is to find out what your IP is. Go into the command console and use ipconfig to find out what it is but instead of noting down the IP address, we actually have to note down the default gateway values for the task at hand. Now all you need to do is open your web browser and insert the default gateway values from before into the address bar. By doing so you wil...
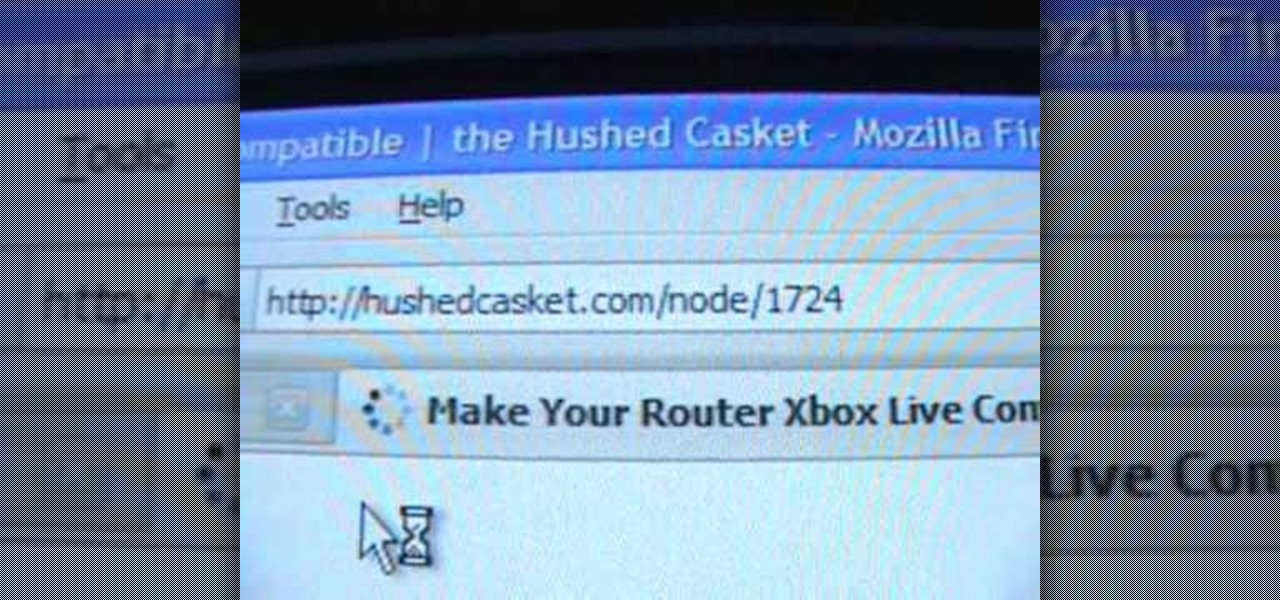
Open your internet browser, type in the address bar 192.168.1.1 and enter your user name and password to access. Look in the right and search for Port Forwarding / Port Triggering. Click on Add Custom Service. Type a name to the service, like XBox Live, now access HushedCasket and scroll down to see the ports you need to open. Go back to the setting and select UDP in Service Type. Put 88 in Starting Port and Ending Port. Go to your XBox and enter in System Settings, go down to Network Setting...

Removing a vehicle's tires and inspecting the brake rotors is possible with a few easy steps. First, remove all five lug nuts and remove the wheel from the vehicle. A power tool will easily remove the lug nuts. You now have access to the wheel so the next order of business is to lift off the wheel. Once the wheel is off the vehicle and safely set aside, return to the vehicle. You now have access to the brake pad. The final step in the process is to inspect the brake pad for thickness and abno...
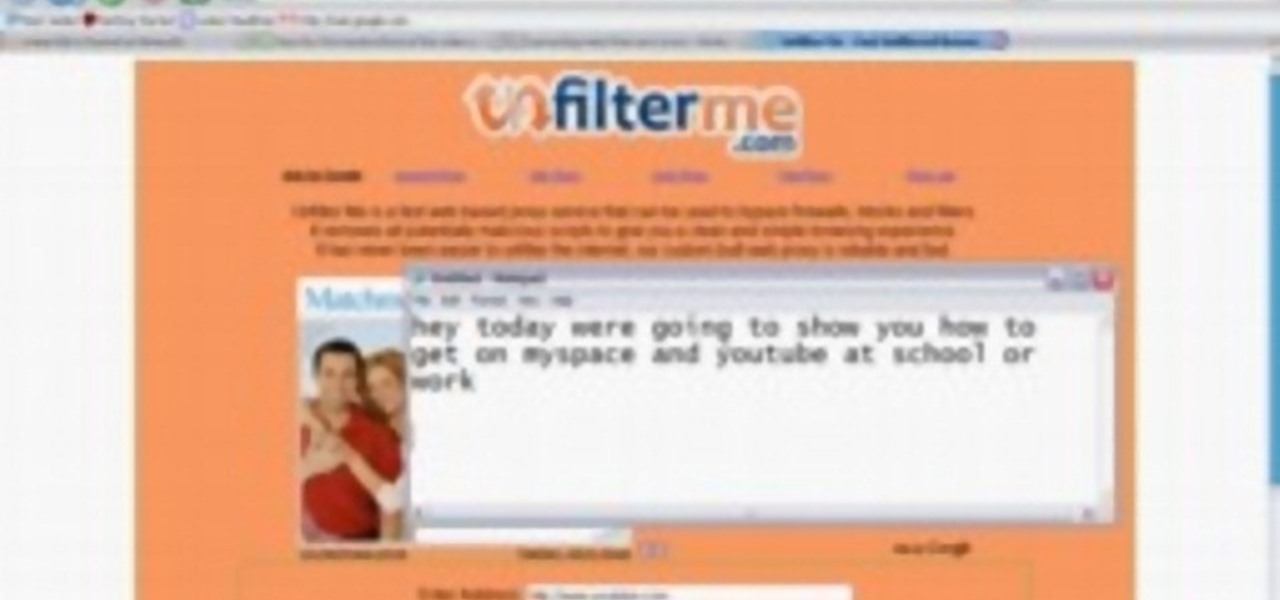
This video shows you how to easily access blocked website like MySpace or YouTube at school. The first thing you have to do is open the web browser and surf to Unfilter Me . Then, type your desired web site URL in the "Enter Address" field. Hit the "Start Browsing" button and wait for the site to load. Note that the URL in the address bar is different. This is the easiest way to access blocked websites at school. That's it! Good Luck!
Learn how to change the themes in Gmail with this video. * Access your Gmail account.

In this video one of the ultimate iPhone hackers, Jonathan A. Zdziarsk, demonstrates how to use a forensics toolkit to recover deleted text messages on an iPhone. But wait - there's more! Not only can you access text messages, but almost any other data on an iPhone as well. We can't be responsible for what you find though!

In this two-part video, learn how to jailbreak an iPhone, iPod, or iTouch 3.1.2 with help from computer whiz, Black Rain. In order to complete this jailbreak, you will need Cydia and web access to visit www.blackra1n.com.

Whether it's a small business or a work group inside a large corporation, all members need access to the same materials in order to work effectively. Mac OS X server makes it easy for groups to collaborate and communicate through their own Wiki-powered Internet website. To learn how to use Wiki Server with Mac OS X Server, watch this video tutorial.

In this tutorial Lindsay Adler will teach you how to add makeup to your models in Photoshop. Sometimes you do not have access to a makeup artist, or after the shoot decide you want a splash of color. Lindsay will teach you to add makeup in a few quick steps in Photoshop.

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

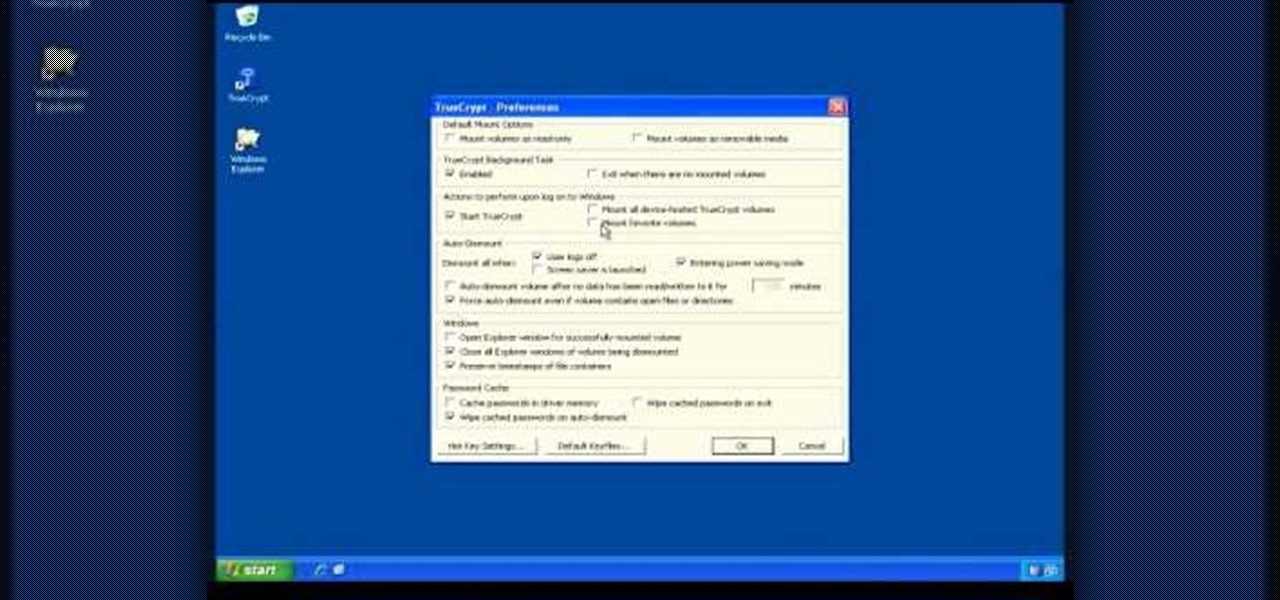
How to use or mount a TrueCrypt volume to access the data that you have encrypted with the program.

You can't get the same gaming experience on your iPhone as you would on a PlayStation 5, Xbox Series X, or gaming computer. The processing power is less, the controls inadequate, and there are many on-screen distractions, all of which make mobile gaming less enjoyable. While you can't fix many of these issues, there is a way to prevent some problems, and that's thanks to Guided Access.

Third-party apps on your iPhone must ask for your permission to access your library in the Music app. Some will even want to get access to your Apple Music account. If you no longer use the apps, you shouldn't be letting them have access anymore. It's easy to hunt them down, and doing so might even show some apps you can't even remember giving any permissions to.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

On Sunday, Microsoft did what everyone expected the company to do by unveiling the long awaited HoloLens 2.

WaveOptics, makers of diffractive waveguides, has inched closer toward getting products featuring its technology to market through a production partnership with a consumer electronics company whose clients include Google, Microsoft, and Sony.

On Thursday, Mojo Vision, a startup comprised of former engineers from Apple, Amazon, Google, and other Silicon Valley mainstays, emerged from stealth backed by $50 million in funding for a hands-free augmented reality platform that runs without smartphones, tablets, or other devices.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. Fortunately, some of you can fix this.

In the weeks following Google's AR toolkit launch last month, the availability of quality ARCore apps has been somewhat limited. That changed on Tuesday, as a flurry of new and updated apps arrived on the Play Store, including some AR experiences available exclusively on Android.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

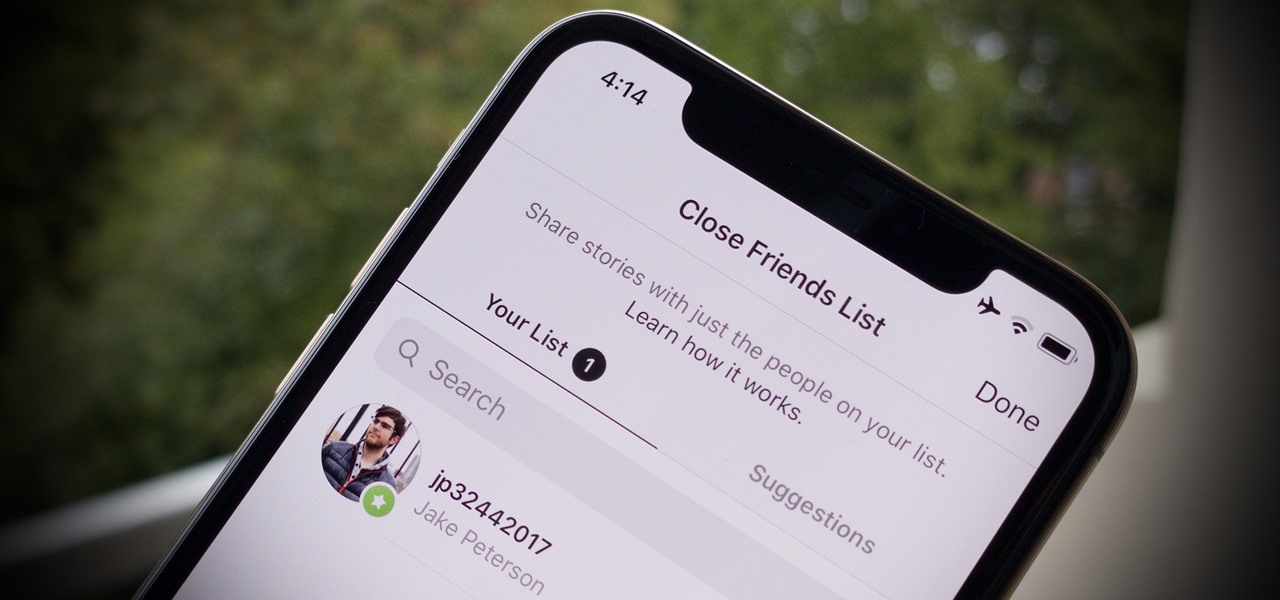
Instagram is a great platform to share photos and videos with the world, but sharing with smaller groups is near impossible. You can directly message pictures, stories, or post links to friends, but that only works for one person at a time or in group chats you create. To share your content with a small group of people you care about the most, you'll want to use the "Close Friends" list.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

3D Touch is only available on the 6s and 7 series iPhones right now, and likely future models, so those with older devices are missing out on all the cool "Quick Actions" available for app and settings icons. But the new iOS 11 is finally bringing some of those helpful shortcuts to iPhones without 3D Touch built in.

There's no debating that the Galaxy S8 and S8+ are top contenders for the most beautifully designed handsets of 2017, but the same can't be said for their TouchWiz interface, which has been met with lukewarm reception at best.

If you're a parent of a toddler (or have a friend that acts like a toddler), you occasionally need to take a break just to preserve your mental health. The perfect way to buy yourself some "me time" in this scenario would be to pull up an episode of Dora the Explorer on Netflix or YouTube, then hand your phone or tablet over to your child (or child-like friend) and try your best to relax while they're occupied.

Google's own devices have always been the first to get new Android features — but unlike the Nexus series, last year's Pixel phones have a handful of exclusive tweaks that were never intended to trickle down to other devices once the newer Android version rolled out to them. These Pixel exclusives included the Pixel launcher and a unique set of on-screen navigation buttons.

As if you needed another example of Android's open-source awesomeness, before the Pixel phones were even released, a flashable ZIP that will give you almost all of Google's Pixel-exclusive features on other devices appeared.

Google's new Pixel phones are shaking things up in the world of Android, as the Nexus line is no more, and the Mountain View tech giant has now become a smartphone OEM. The long-term impact of these moves remains to be seen, but we already know that Google, the manufacturer, will be adding extra software and UI features to the version of Android that ships with its Pixels.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

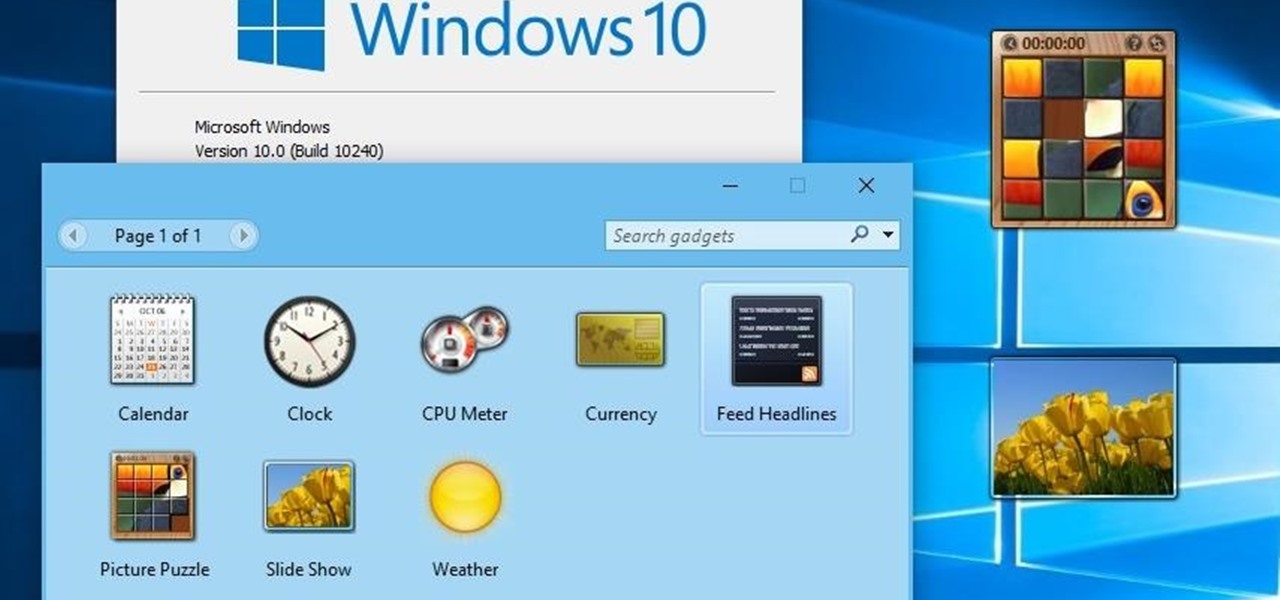
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.