I go back and forth between two home screen apps: Nova Launcher and Action Launcher. While I prefer the aesthetics of Nova, I like Action's Quickpage feature since it puts some of my favorite apps just a swipe away. But now, I've found a way to replicate this feature on Nova (or any other launcher), and it works even better.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.
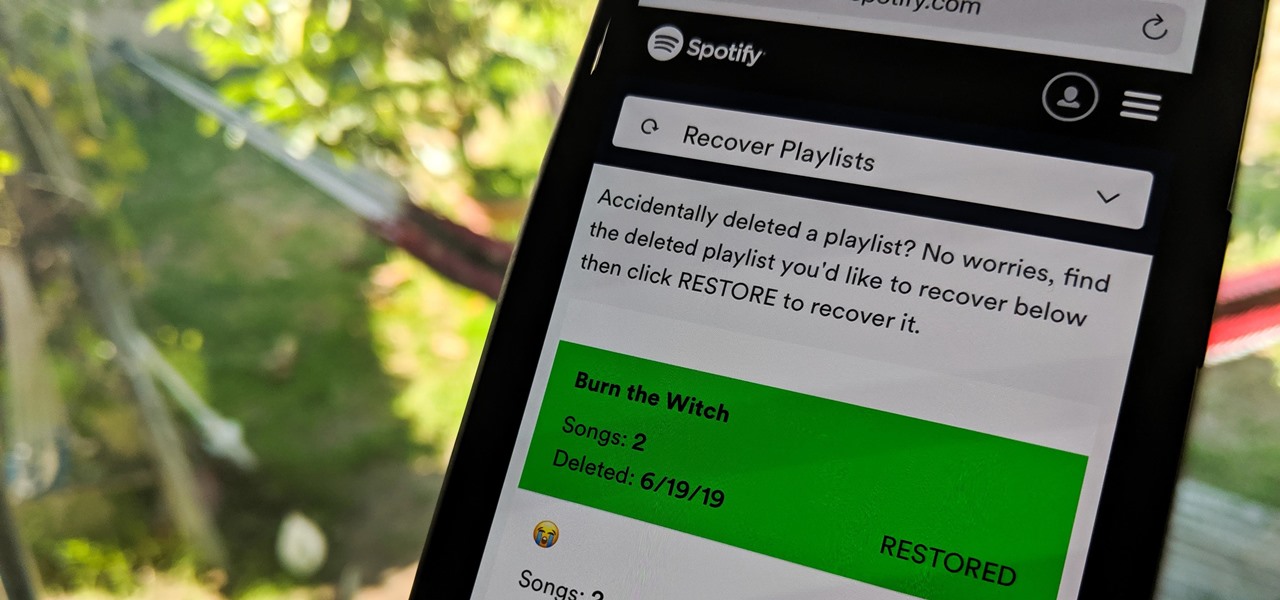
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.
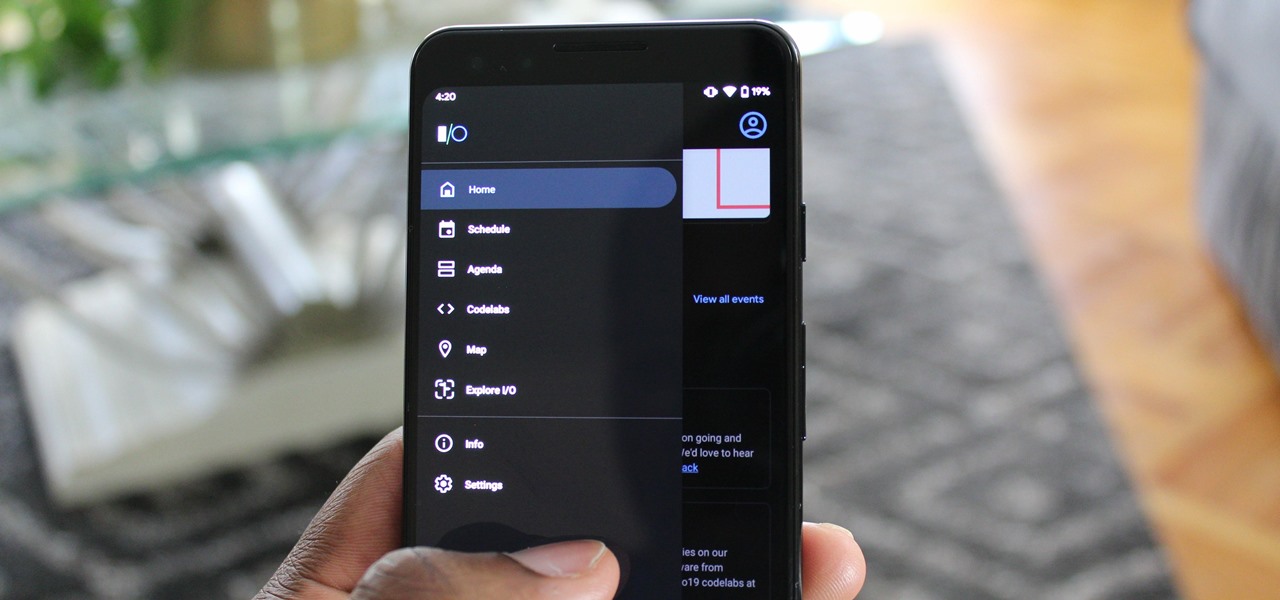
Android 10 goes all-in on gesture navigation. Unlike Android 9, all three buttons which made up the navigation bar are replaced with gestures, with the biggest change being the back button. The problem is this same gesture is already used within apps to access the side menu, so in Android Q, this has been changed.
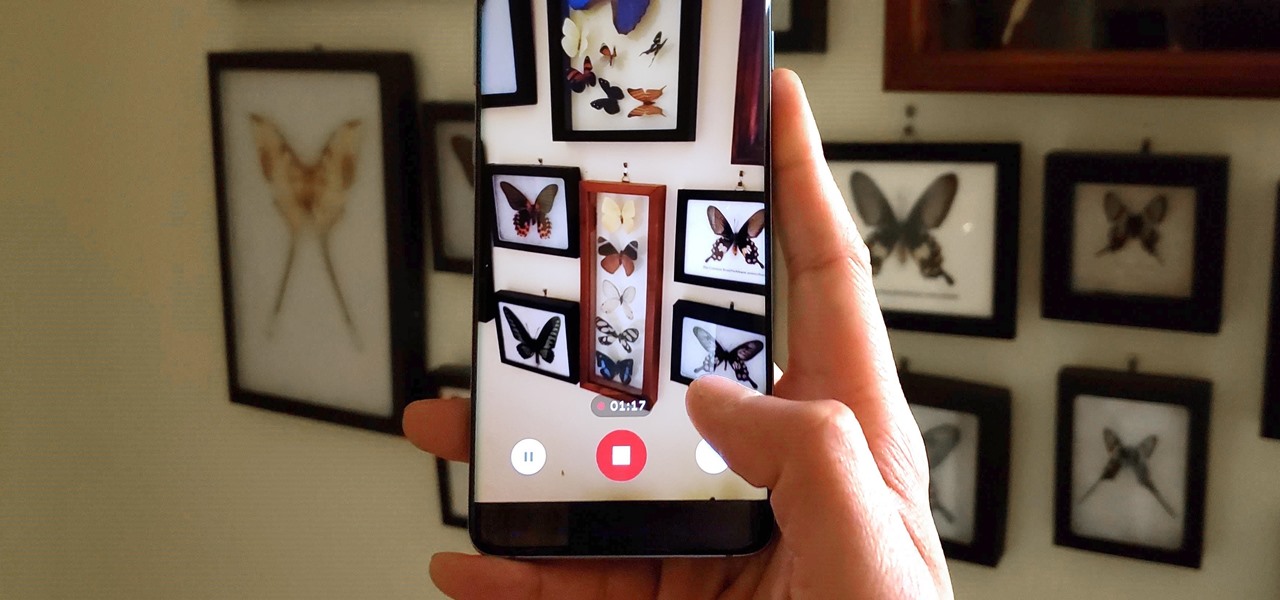
Though primarily a Pixel exclusive, Google Camera has become the go-to camera app for many Android users. Not only does come with a standout features like Night Sight and capture better photos than most stock camera apps, but it's also packed with functionality that makes it a one-stop-shop for all your photo and video needs.

Apps that can display virtual furniture in the home are one of the most popular applications of mobile AR today, but Houzz has decided to raise the stakes with its latest update.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

It looks like it's cuffing season for AR hardware makers and telecommunications corporations. With AT&T aligned with Magic Leap as its exclusive wireless retailer on the high-end AR side, Verizon has also reached a master reseller agreement with Vuzix, according to a filing with the Securities Exchange Commission.

If you use the internet regularly, it's nearly impossible to avoid memes. They are the epitome of internet culture, demonstrating how jokes can spread and change like wildfire. While there are many different types, the most common ones you'll come across are images and GIFs with humorous text accompanying them, and we've found the best iOS apps to help you create your own.

Call Screen is one of best features on Pixel phones. With one button, you can screen calls using Google Assistant and avoid pesky spam callers. However, after the call, there is seemingly no way to access the transcripts for future review. Fortunately, there is a way, but it is tucked away.

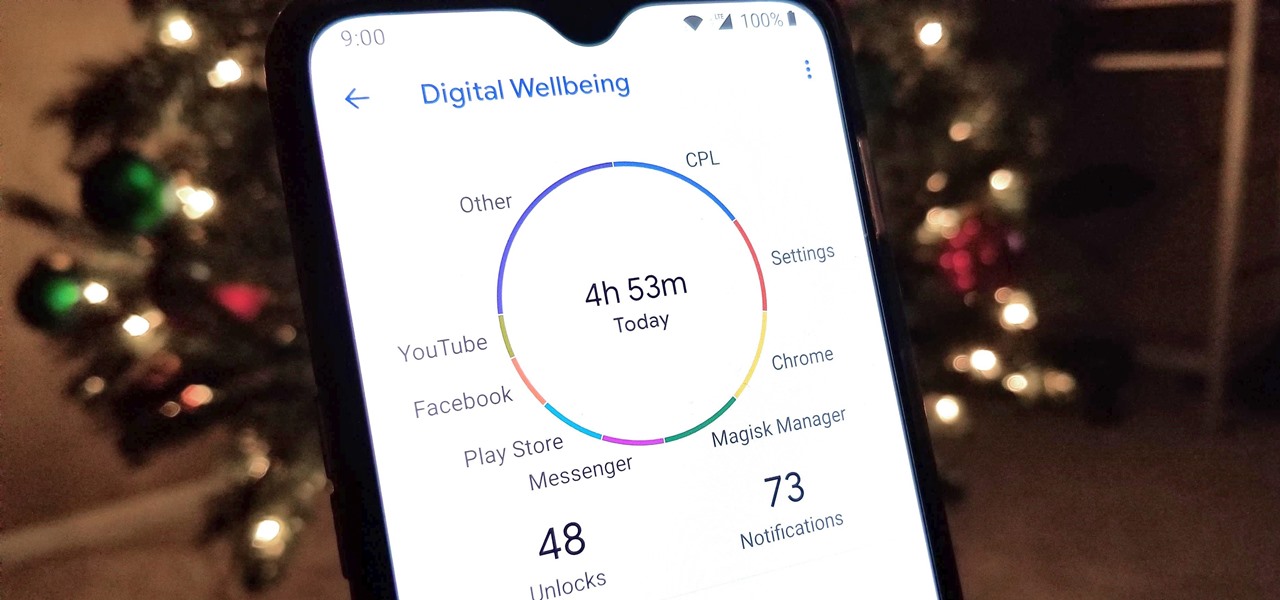
Living in this age of smartphones and always being connected can sometimes have us getting carried away with our devices. Whether it's an addiction to our phone or if we just feel like cutting back on some daily screen time, there's a great tool that can help with that — Google's official Digital Wellbeing app puts you in control by laying out all the stats you need to help curb your daily smartphone habits.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

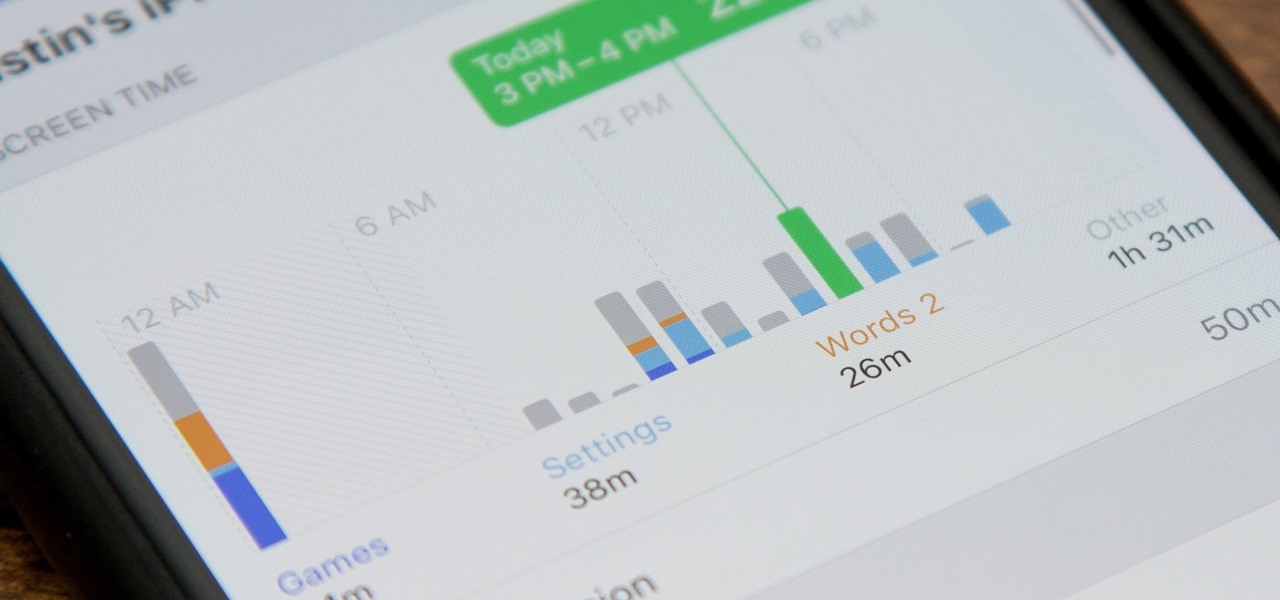
Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

As Android device partners ship new products, Google has been diligent in its efforts to ensure that users can enjoy ARCore apps once they boot up their new toys.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

A new set of APIs for Unity promise to make it easier for developers to publish apps that support both ARKit and ARCore.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Apple's digital health initiative in iOS 12 includes Screen Time, a settings menu that shows you how much time you spend playing games, reading news, and whatever else it is you do. This menu also lets you schedule downtime away from your iPhone, set time limits for your apps, and more. While this is all great, it's hidden inside the Settings app — but there's a faster way to access this data.

We learned during the LG G7 ThinQ announcement that AT&T would be carrying a new V series device, the V35 ThinQ. In the LG V35 ThinQ's press release, LG revealed its specifications but left out pricing and availability. Thanks to Project Fi, we now know its price tag, and you may not like it.

Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.

HTC is entering the augmented reality market through the back door by giving developers access to the stereo front-facing cameras on the Vive and Vive Pro VR headsets.

Google Chrome is an incredibly popular web browser on both iOS and Android devices, just like its desktop version. That's why it's number one browser in both the iOS App Store and Google Play Store. But for those of you who want even more features, you can test drive the Chrome Beta and get new updates first.

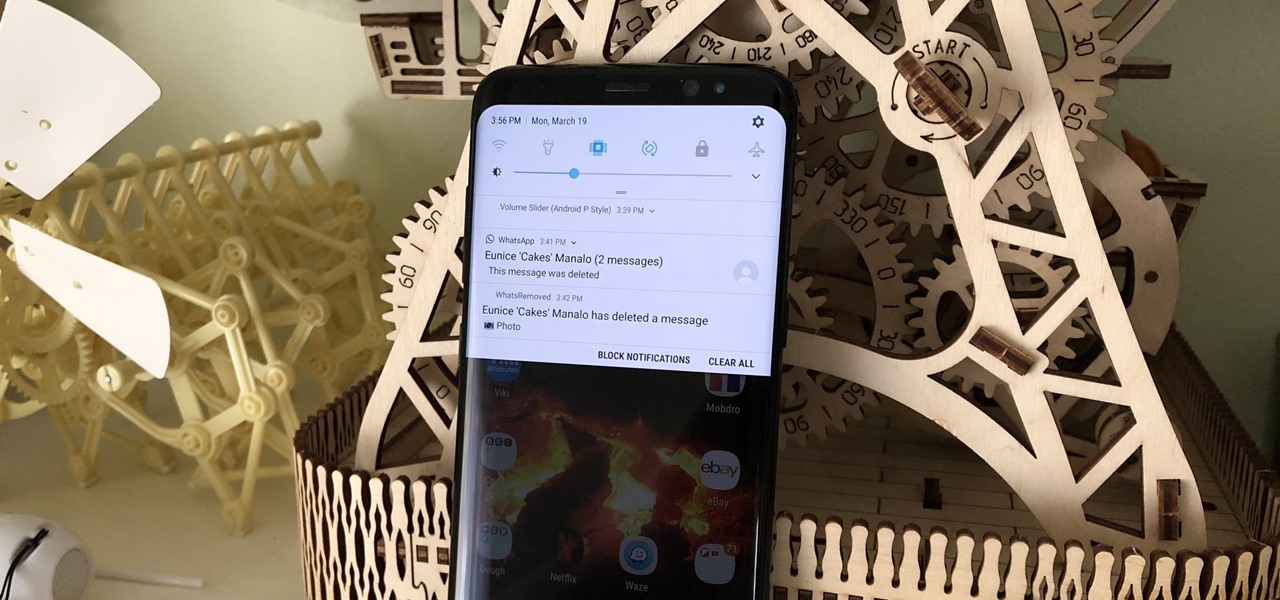
To help keep potential drama at bay, WhatsApp lets you delete questionable messages before the other person even sees them. If you're on the receiving end and you're curious about the deleted text, however, there's an Android app that lets you view erased messages.

Snap Inc.'s dedication to augmented reality has expanded the world lenses in Snapchat to our own Bitmojis. While it's great to see our characters interacting with real environments, we haven't seen them connect to other Bitmoji in AR space. That all changes with "3D Friendmojis," a lens from Snapchat that lets you stage scenes between your Bitmoji and a friend's.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

The Pixel 2 and Pixel 2 XL launched in 2017 with three colors: Clearly White, Just Black, and Kinda Blue. For those who wanted to stand out from the crowd a bit, Kinda Blue was the clear choice. Verizon, however, had other plans in mind, and Kinda Blue became exclusive to the carrier. That is, until now.

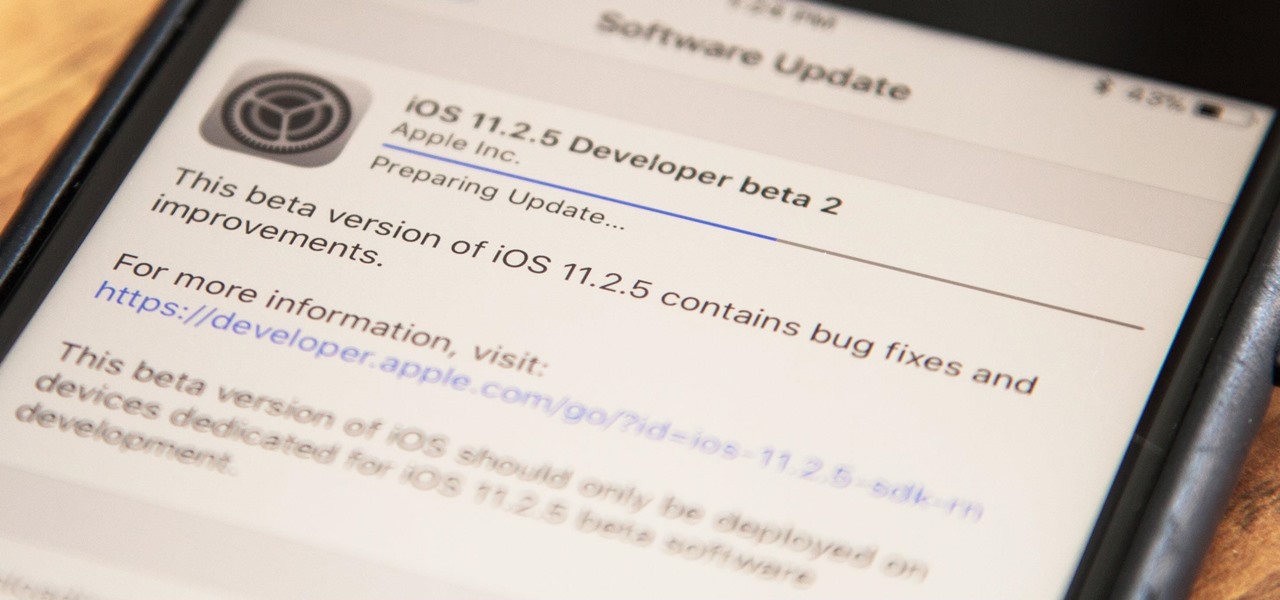
Apple has released the second beta for iOS version 11.2.5 for developers on Dec. 19. The update comes six days after the release of the first 11.2.5 beta which updated the Music app to include a persistent "play bar" at the bottom of the window, along with some bug fixes. Public beta testers received the update on Dec. 20.

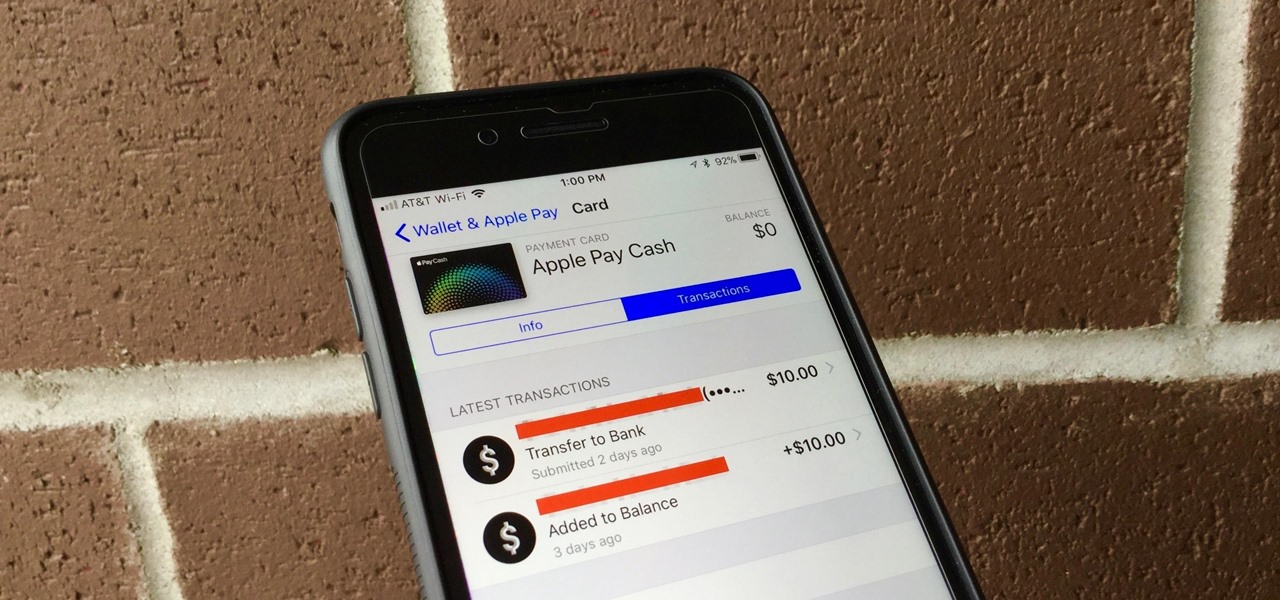
With Apple Pay Cash, sending and receiving money with fellow Apple users has never been easier. One big plus about Apple's new Apple Pay Cash card is that all of your transactions are available just a few taps away, so you can see all your person-to-person payments, balance additions, and bank transfers.

Earlier this week, we told you about the new Star Wars augmented reality collaboration with Nissan that will bring the famed science-fiction franchise to auto showrooms, and now we can show you what it looks like.

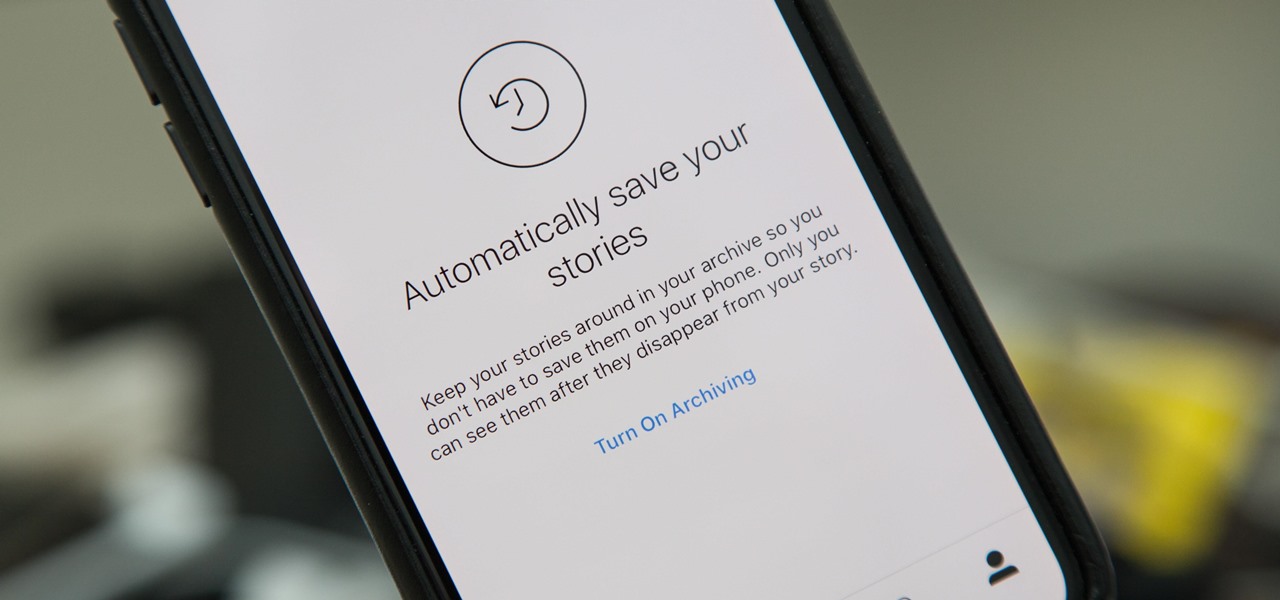
If you're familiar with Instagram Stories, you know that you can download your story to your iPhone or Android device for offline viewing. Those downloaded stories can easily get lost, and Instagram is finally doing something to keep that from happening with a new archive option for stories, similar to the regular posts archive.

Samsung just announced that the Galaxy S8 is getting a fresh coat of paint, launching a burgundy red color of the flagship in their home market of Korea. There is currently little information about whether this color will come to the US for the S8, but this could be a preview of things to come. The Galaxy S9 is set to arrive in January and may also come in a beautiful red variant.

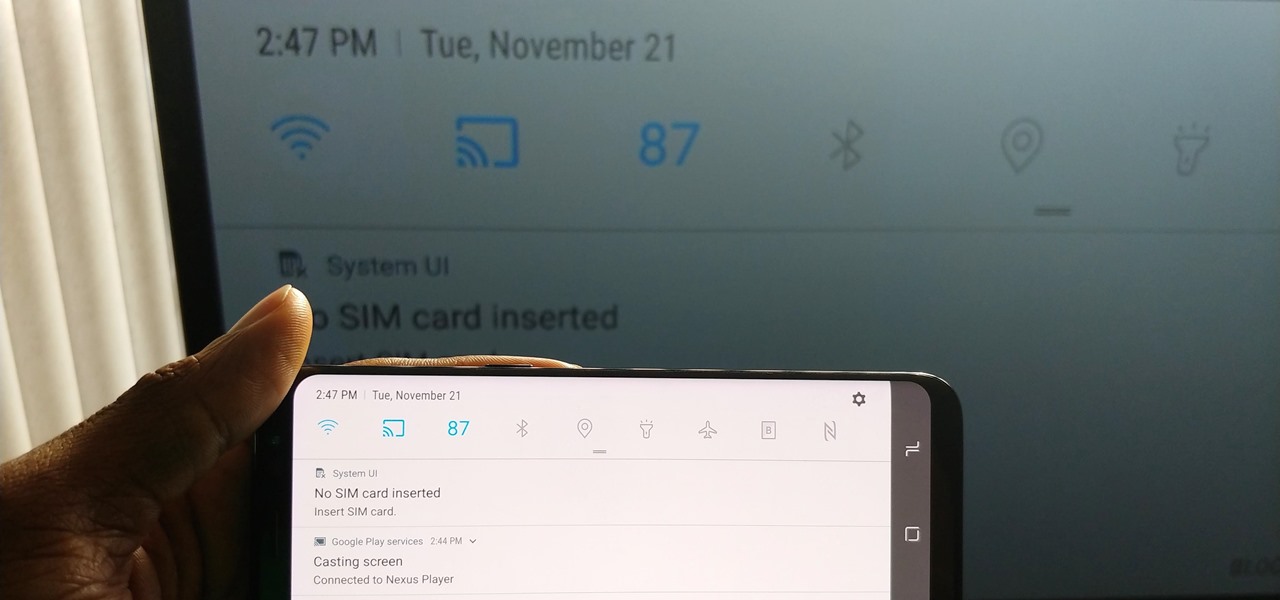
Android's Quick Settings menu gives you easy access to certain actions from any screen, but the tiles available are largely dependent on your phone's OEM skin. For instance, the Google Cast button that can cast your entire screen has been exclusive to Nexus and Pixel devices, even though other phones have the requisite software to use it. Fortunately, there's a way to add it on any device running Nougat or higher.

Apple seeded the fourth beta for iOS 11.2, just one day after releasing iOS 11.1.2 to the public. The new iOS 11.2 beta 4 has also already hit public beta testers and includes mostly bug fixes and security patches to improve the overall experience for iPhone owners.

As it turns out, Apple did get AR hardware into its retail stores for the 2017 holiday shopping season, but it's not the headset we've been hearing rumors about for years; it's the MekaMon battle-bot.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Apple rarely changes the ringtones on its iPhones. In fact, the last addition was all the way back in iOS 7. However, it appears they wanted to do something special with the 10th-anniversary edition iPhone, so Apple included a unique ringtone called "Reflection" on the iPhone X.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Snapchat is mostly credited as the first AR social network, and, like most social media companies, its revenue model is nested largely within advertising. As such, the company now has a new avenue for branded content.