While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.
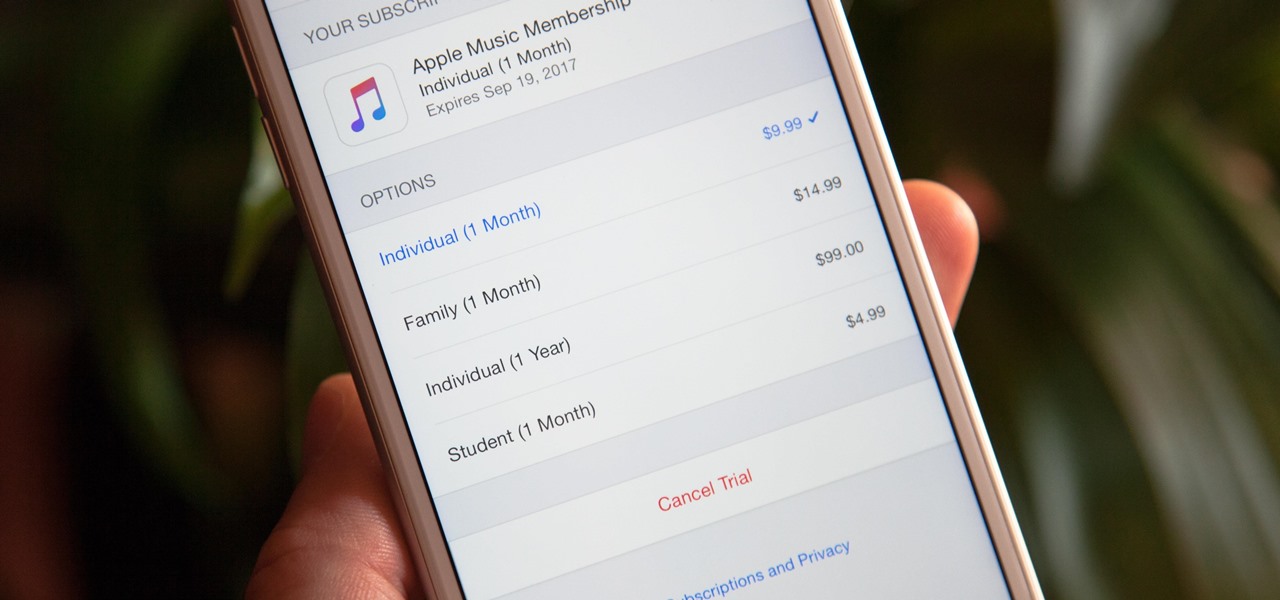
Apple Music offers a cheaper subscription option to those of you who look for it — only $99 for a year. If you are already an Apple Music user, you can access the option right now. Otherwise, you have to sign up for a normal monthly plan first, then switch to this plan to get a better deal after.
The Note 7 debacle taught Samsung an important lesson on cramming oversized batteries into their handsets, and they've applied it diligently to their Galaxy S8 and S8+. You might even say the company has gone a little too far in trying to achieve a balance between battery size and battery life, as it not only not only sets screen resolutions to 1080p by default and warns users about maxing out display brightness, but it also keeps close tabs on individual apps' battery usage.

Those of us with modern smartphones know that 4G LTE networks have provided us with a phenomenal experience. One light years beyond what we had access to before. For some time, AT&T has been teasing its dive into the next iteration of network speeds, agonizingly doing so without any specific dates for when they would actually deliver. But today, AT&T confirmed what they call the "5G Evolution," and it's available now.
The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

Here's another workday distraction for all you social media lovers out there: Pasted, launching out of beta today on iOS, is a simple collage and photo editing app mixing iconic '90s imagery with a love of the The Shins.

ModiFace, the makers of Sephora's Virtual Artist app which allows users to try on multiple different combinations of makeup through augmented reality, has just bumped up its augmented reality strategy. The company is now including a live-stream option for all those personal makeup trials you've been secretly admiring from the comfort of your own phone.

Google Assistant has introduced tappable shortcuts on the Google app for Android, iOS, and Google.com this week.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

If your Android phone was made by Samsung, LG, HTC, or any other manufacturer that likes to apply skins on top of stock Android, then your camera app is tied to the custom gallery app that was preinstalled on your device. In other words, when you tap that little image preview icon after taking a picture, you'll be taken to a camera roll interface that was made by an electronics manufacturer.

Today at the Unite '16 conference in Los Angeles, Unity's Timoni West and Amir Ebrahimi showed off its new virtual reality authoring and world editor, EditorVR, using the HTC Vive. Coming in December to Unity is a version of its editor that works inside a VR headset, which will change the way developers interact with the worlds they build—even if they aren't building for VR.

The widget selection on Android is one of the main things that set it apart from other mobile operating systems. You can get quick, at-a-glance information for topics like weather, news, music, and much more, all without ever leaving your home screen.

We recently covered a set of ported apps from the new cloud-based smartphone, the Nextbit Robin. These ported APKs brought two of the Robin's slick new stock apps—Camera and Gallery—to any other device, but the launcher was conspicuously absent.

Several Samsung phones have a feature that turns the screen black and white when the battery is getting low. This takes advantage of the AMOLED display in these devices, because unlike red, green, and blue pixels, no battery power is used to display black pixels on this type of screen.

If you get a ton of emails each day, your mailbox probably has thousands of unread messages, and that annoying badge icon will keep reminding you of it. Fortunately, iOS comes with some tools to help you bring some sense of order to that chaotic mailbox of yours.
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let a logo dictate what kind of phone or tablet you buy.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

When they were purchased by Google back in 2011, Motorola underwent a sweeping change in software philosophy. All throughout the UI on their flagship devices, edgy design patterns were replaced by clean, minimalist interfaces akin to vanilla Android. This philosophy has continued on as Motorola's signature, even though they have since been sold to Lenovo.

Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

For those times when you can't get something done by clicking a few buttons with your mouse, the Windows command prompt has always been an indispensable tool. But as much as advanced users have relied on this useful utility, it hasn't seen a significant update since the Windows 95 days.

With every version bump, Android gets a new Easter egg that can be accessed by tapping the "Android version" entry in Settings. For the most part, these have generally been little animations or live wallpapers that depict the Android code name, but starting with version 5.0 Lollipop, things got a bit more interesting.

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

Unless you have a newer iPhone 6S or 6S Plus, the front-facing "FaceTime" camera on your iPhone has a pretty weak, low-res sensor, which means unflattering selfies. You could use the rear "iSight" camera to take a high-res selfie, but framing your mug properly and hitting the shutter is difficult, takes many failed attempts, and usually results in a lackluster photo.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

In an attempt to increase advertising revenues, Snapchat introduced Discover back in January of this year, a feature that brought a handful of prominent media partners, such as CNN, ESPN, and Vice to your feed, along with their tailored news stories and videos.

With iOS 8.4 and iTunes 12.2, we got our first look at Apple Music, Apple's new streaming subscription service. While it's a little late to the party, there is definitely an incentive for iOS and Mac OS X users to switch over from competitors due to its heavy integration with the Apple ecosystem.

T-Mobile's "Uncarrier" initiative has done wonders for my wallet and my data usage. Before I had to deal with being throttled down to 2G speeds after passing my data limit, but thanks to their unlimited data plans, I'm free to use as much LTE data as I possibly can. The only downside is, when sharing data through a mobile hotspot (tethering), T-Mobile imposes a 5 GB limit (which was recently upped to 7 GB for some).

On an Android device, you can download almost any file type into a neat and tidy "Downloads" folder, and those files can then be accessed with an appropriate app, shared via email, or transferred over to your computer. On an iPhone, there is no such folder, and saving files from Safari is almost impossible unless you're jailbroken.

Google recently announced the beta release of a developer tool called ARC Welder for Chrome, which allows developers to run and test their Android apps on any computer with the Chrome browser installed.

In 2014, Snapchat introduced a special type of Filter called Geofilters. Geofilters only appear when you're in a specific location. For example, a Disney Land Geofilter will only appear if you're actually there. Rather, your phone needs to think that you're at Disney Land. By spoofing your GPS location, you can effectively travel all across the globe — at least in the eyes of Snapchat.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

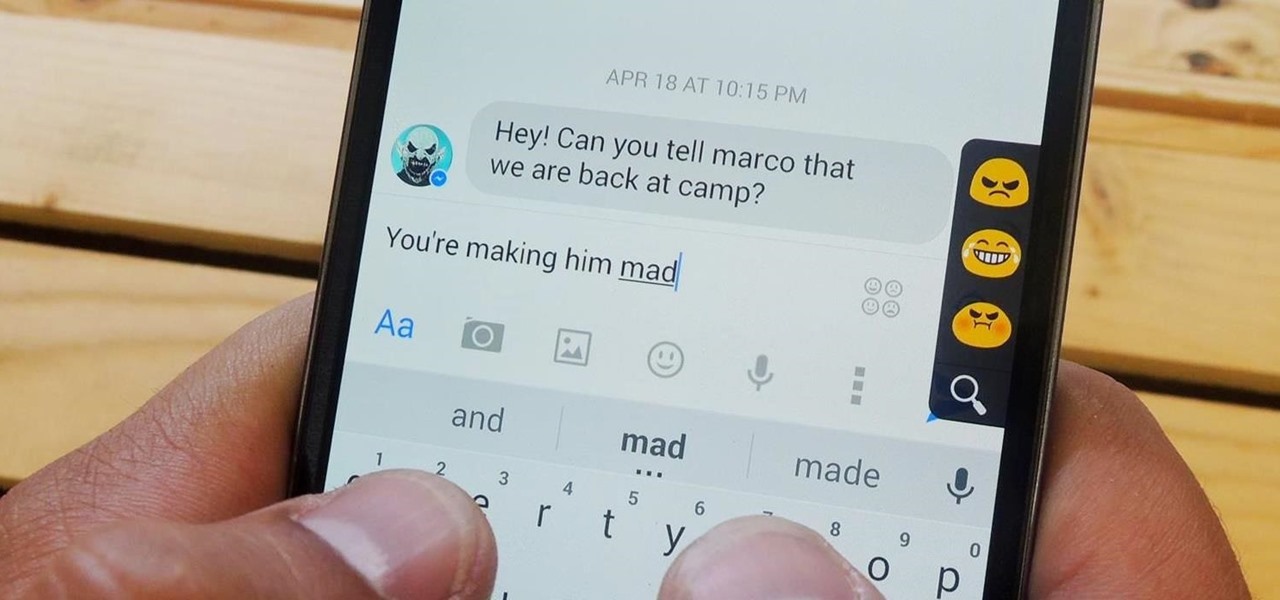
Some third-party keyboards, like SwiftKey for example, include a convenient feature that suggests emojis as your type based on the content of what you're saying. Unfortunately, many keyboards, including most stock ones, don't include this function.

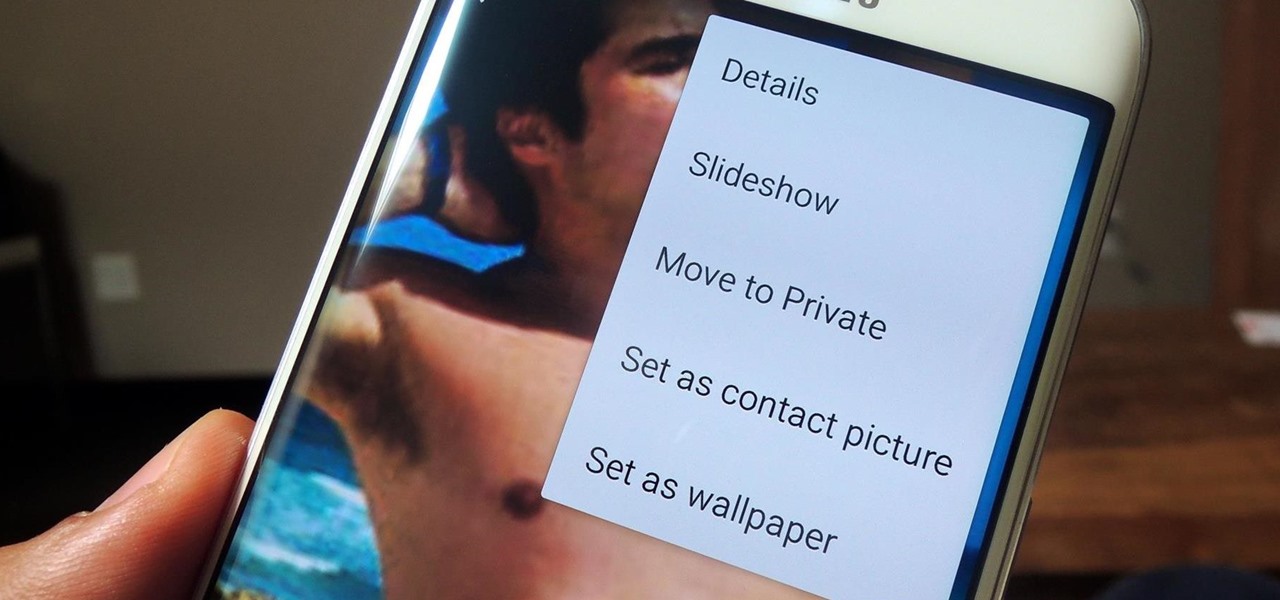
If you have a smartphone, chances are you have something on it you don't want others seeing. Whether it be photos, videos, or documents, some things are best left private. Not everyone is a saint, after all.