If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

You may wish to block websites from being accessed on your computer for any number of reasons. Maybe you're a concerned parent who wants their kids to browse the internet safely. Maybe you're an employer who wants to secure office computers or blacklist innapropriate websites.
Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.
Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.
This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.

Audio filters help you create a credible soundtrack. They can remove distracting noises, like the hum of an air conditioner, and add atmosphere, like an echo. Filters are accessed in the effects tab of the browser and organized into two categories: those provided by Apple and filters that come bundled with Final Cut Express. Drag a filter into the timeline and doubleclick it to edit it in the viewer.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

In this tutorial, we learn how to open & utilize the trunk area of a 2010 Prius. To access the cargo area, open the rear hatch by pressing on the release above the license plate. To keep items out of sight, there is a sliding cover that you can pull back and hook into slots. To open, pull towards you slightly, then reel it in. There is additional space under the floor which can be accessed by twisting the locks and removing from the vehicle. Underneath this, there is a cargo bin, and undernea...

This video instructs the viewer about the basics of cloud computing, using more than one computer and managing your computing needs online. The instructor explains, "Cloud computing is a metaphor for using the Internet for your computing needs." A program called cloudo, allows the user to store information online through an interface that looks like a regular computer desktop; then the information can be accessed via password from any computer with an internet connection. Other programs also ...

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to apply localized correction in Lightroom 2.

In this video tutorial, viewers learn how to quickly switch tabs with the keyboard. Users will need the Fire Mozilla browser to do this. Begin by going to the Firefox Mozilla add-on site and search for "crtl-tab". Then click Add to Firefox to install the add-on. To activate the add-on, simply press the ctrl and tab buttons on the keyboard. It will then open a thumbnail of your 7 most recently accessed tabs. There is also a search bar for users to use to find a specific site. This video will b...

Almost every video on YouTube is embeddable. Only those that choose not to feature an embed code or non-embeddable. This embed code can be accessed directly on the video page of the video that strikes you. If you want to embed it, simply click the "Embed" button underneath the video player to generate the embed code. You can tweak this embed code to better serve you and your WordPress blog or website. It will generate the code automatically, and you can grab it and use it for yourself. This c...

Windows 7 uses several options to make it easier to change and locate the cursor on the screen. 1) To access these options select “Start” then click on “Control panel“from the menu.

If you're new to the Internet, or just new to the Safari web browser, you might also be new to the concept of Bookmarks Bar. Happily, this video tutorial from MacMost will teach you everything you need to know about using this handy feature.

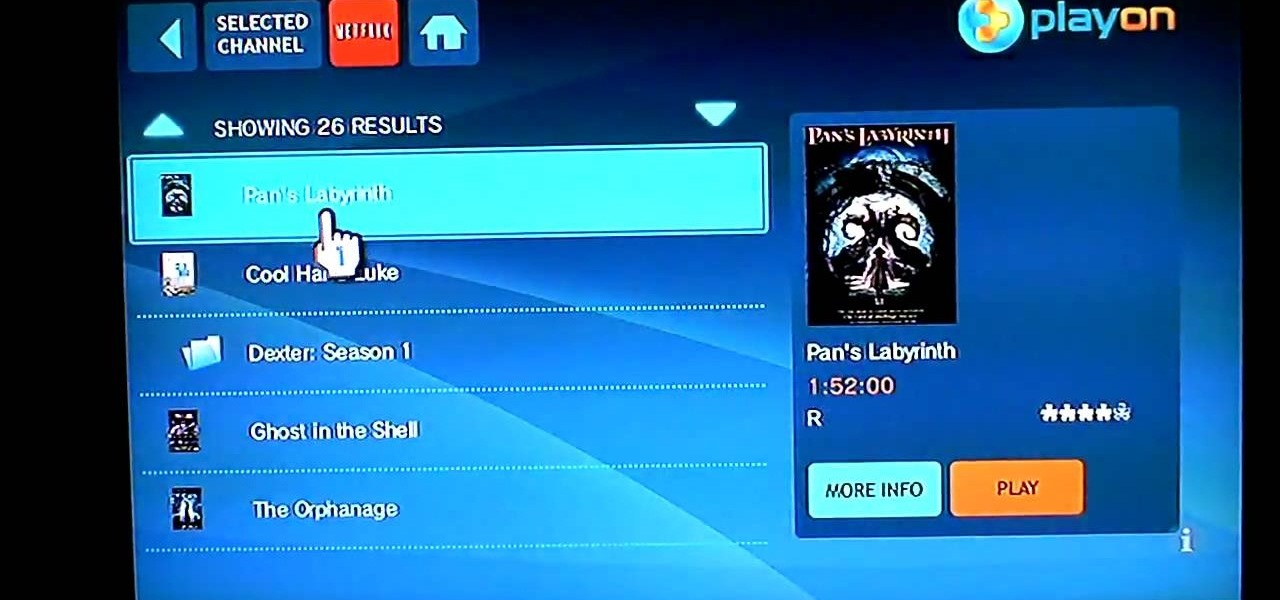
In this how-to video TechVW shows you how to watch Hulu, Netflix and more on a Wii home gaming system. He shows by using a web program called PlayOn that can be accessed through Wii Opera, you can connect to your computer to play videos streamed over the network. He goes on to show the different services offered and how to access each of them and a brief display of how they are used and what features they have.

The pole hitch, demonstrated in this how-to video, is used on a marling spike or rack quite often but it is also a great way to tie off to a winch to bolster your mooring. The Winch Pole Hitch can be tied in the bight, meaning that neither end of the rope needs to be accessed in order to be tied, making it idea for tying up animals. Watch this video knot-tying tutorial and learn how to tie a Winch Pole Hitch.

From Windows 95 through Windows XP, setting file and folder permissions was accessed in the same way. With the introduction of Windows Vista, many things have moved, including this feature. While it works in largely the same way, the steps you take to access these features has changed. This short video will take you step by step through changing file and folder permissions in Vista, with a focus on setting hidden files to show in Explorer.

In this video you will learn how to add various links from Google Maps to an email. The first step you will need to accomplish is to find a section of map you wish to attach to an email. After you have the section of map in view you will see a copy link option at the top right of the image. After you select the copy link you can now open your email program. Once you've accessed your email select attach link and copy/paste the address into the link field. The map image will now be properly att...

Different ways of using a proxy bypass to access blocks sites is shown with ease in this video. Many places explained to be blocked with internet security such as libraries and schools. Using a search engine such as Google you need to search for a proxy site. After a proxy site has been found you will use it to access the blocked websites through another servers internet provider. The narrator explains that proxies are just a way to bypass internet blocks by avoiding using the blocked compute...

In this video we learn how to perform knee replacement surgery. The knee joint is accessed with an incision. Then, a number of different surgical tools will be used to perform the procedure. The part of the knee joint is removed first with surgical saws. Then, the artificial joint is put back into the area. Once this part is secured with screws, an insert will be joined in with it to keep it in place. The artificial joint is checked for the last time, then sutures are used to closed the joint...

In this video tutorial, viewers learn how to use the Mouse Keys feature in a Mac OS X computer. This feature can be accessed under the Mouse & Track-pad tab, in the Universal Access menu. Turn on the feature by checking On. Once turned on, users can use the number keys on the keyboard to move the cursor in any direction. Users are also able to use a keyboard shortcut to turn on or off the Mouse Keys, adjust the Initial Delay, adjust the Maximum Speed and change Cursor Size. This video will be...

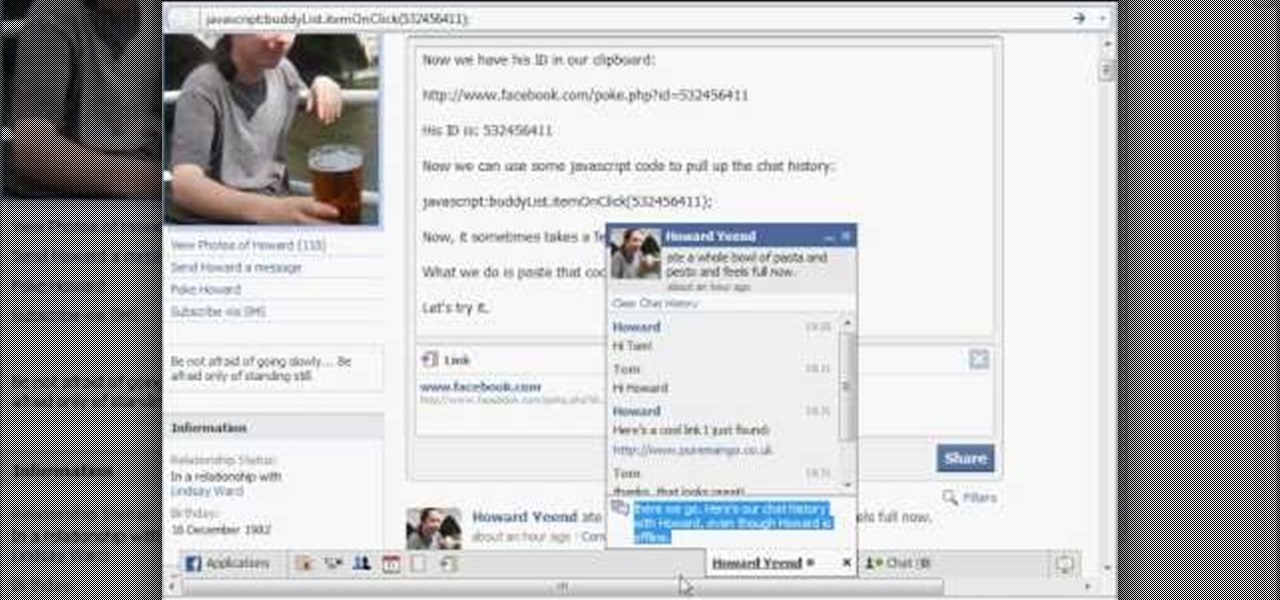
A Facebook profile page shows up explaining the steps on how to get chat history of a friend on Facebook. It explains that you need to go to the profile of the person you would like to find chat history with. It then explains steps on how you can copy there Facebook ID. Once you have accessed that he provides you with a JavaScript code to use to pull up chat history. He gives you step by step examples explaining how to set up the ID and apply it to the JavaScript coding. Once that has been es...

This video displays a 2010 Toyota 4Runner, modeled with seating for seven passengers. In the tutorial it shows a few of the basic adjustments that can be made to the seating. You can adjust the seat to recline to your comfort level and move to seat forward and backward. Unlike most 4Runner model this one comes with an additional back row of seating. This can be accessed simply by pulling the bottom lever of the backseat and pushing the seat forward.

In Access 2010 you can now create a navigation form (like a home page) for your database without writing a single piece of code or logic! Great for busy people who need to organize their database quickly, but who don't have code writing skills. It's just drag and drop. There are predefined layouts which help you design the form and then simply drag the information you want into the form. Reports can be added and accessed quickly from the navigation form so you can analyze the data simply and ...

In this video tutorial, Chris Pels will show how to share data in between JavaScript and server-side code by using a hidden field in an ASP.NET page. Next, learn how to use the RegisterHiddenField method in server-side code to programmatically create a hidden field on the client. In addition, see how to programmatically create a HiddenField server control for sharing data on an ASP.NET page. Finally, use the RegisterArrayDeclaration method to create a container in server code for storing mult...

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

NTFS? What is it? It stands for New Technology File System, but what does that mean? Well, it's the standard system for filing in Windows NT, including all later versions, up to the current Windows 7, but Mac users can take advantage of this file system, too. If you’re confused when it comes to your hard drive’s format, this guide will show you the way to get the most out of your system.

The purpose of this video is to show how to become a permanent resident in Canada. Some programs are federal and some are for Quebec. The first program is the skilled worker program. The applicant is accessed under a point system and is awarded points for education level, knowledge of English or French, work experience, age, confirmed job offer, and adaptability and you must have sufficient proof of funds. The next program is Family Class Sponsorship. A citizen or permanent resident can spons...

For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

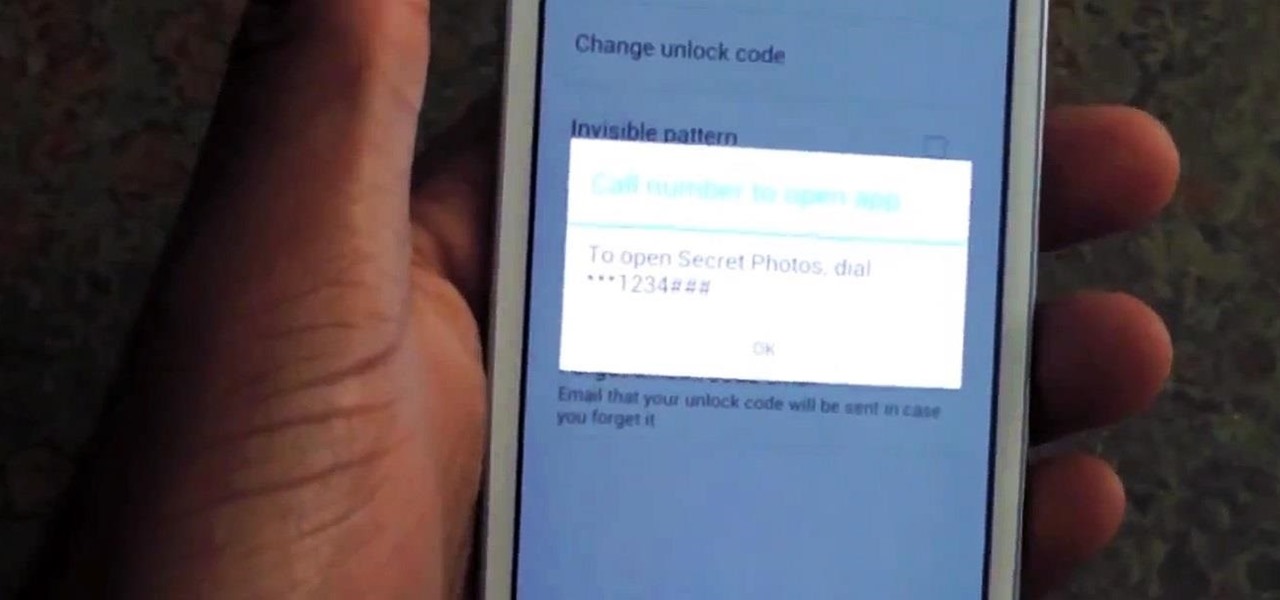
Whenever a friend borrows my Samsung Galaxy S3 to browse the web or make a quick call, I always pause to make sure there's nothing incriminating on it. I'm no superfreak, but some of my friends are, so I have more than a few photos on my device that I wouldn't wish upon anyone. I like to avoid these kinds of looks.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

In iOS, the Control Center is an easy way to toggle settings such as Wi-Fi, Do Not Disturb, and Low Power Mode. Its Android counterpart is called "Quick Settings," which provides much of the same functionality with a few bonuses. If you're curious about how this toggle menu works or miss having it before you made the switch from Android, you can test it out on your iPhone right now.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.